
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Writeup on cadmium - Exploit targeting sboot, the exynos android bootloader cc @ _kamino_ @ nitayart https://wikileaks.org/ciav7p1/cms/files/cadmium.pdf #Vault7
"WikiLeaks 公开的 CIA 对 Exynos Android Bootloader 漏洞的分析和利用细节,成功利用该漏洞可以实现加载未签名的 Android Image 镜像: https://t.co/BxuULz29NF "
-

[ Android ] [CVE-2017-0510] Critical #Vulnerability: Attacking #Nexus 9 with Malicious Headphones #android #netsec https://t.co/QXnbBZ07oT
"3 月份的 Android 漏洞补丁修复了一个可以通过耳机触发的 Nexus 9 漏洞,成功利用该漏洞可以实现泄露栈上 Cookie、Bypass ASLR、恢复手机出厂设置等等: https://t.co/QXnbBZ07oT "
-

[ Android ] TrustZone TEEs An Attacker’s Perspective https://microsoftrnd.co.il/Press%20Kit/BlueHat%20IL%20Decks/GalBeniamini.pdf
"攻击者眼中的TrustZone TEEs(可信执行环境): https://t.co/UxfBPzbJWr"
-

[ Browser ] Here are the release notes for today’s Safari Technology Preview release 25 update. https://webkit.org/blog/7432/release-notes-for-safari-technology-preview-25/ https://t.co/LpAlZA6G6Y
" Safari 技术预览版25发布报告: https://t.co/uL5RD4G7MS "
-

[ Crypto ] Cryptography and Network Security Principles and Practices (4rth Edition) : http://www.inf.ufsc.br/~bosco.sobral/ensino/ine5680/material-cripto-seg/2014-1/Stallings/Stallings_Cryptography_and_Network_Security.pdf (pdf)
"2005 年出版的一本《密码编码学与网络安全(第四版)》︰ https://t.co/tmDiH2zcuh"
-

[ IoTDevice ] 0day vulnerabilities found in GoAhead and in Wireless IP (P2P) cameras (pre-auth RCE as root) #0day #IoT #Cloud https://t.co/pWq7tbzLRg
"基于 P2P 协议的无线摄像头多个安全漏洞分析: https://t.co/pWq7tbzLRg"
-

[ Linux ] Linux kernel: CVE-2017-2636: local privilege escalation flaw in n_hdlc http://seclists.org/oss-sec/2017/q1/569
"Linux 内核驱动 n_hdlc 存在条件竞争漏洞,可导致本地权限提升(CVE-2017-2636): https://t.co/uL3fh13sDl"
-

[ MalwareAnalysis ] Crypt0l0cker (TorrentLocker): Old Dog, New Tricks http://blog.talosintelligence.com/2017/03/crypt0l0cker-torrentlocker-old-dog-new.html
"近几年,勒索软件就像瘟疫一样蔓延,Talos 这篇 Blog 是对其中一款 Crypt0l0cker 勒索软件的分析: https://t.co/oTaBrf38v2"
-

[ Others ] Art of Anti Detection 3 – https://pentest.blog/art-of-anti-detection-3-shellcode-alchemy/ ,Part 2 (PE Backdoor Manufacturing): https://pentest.blog/art-of-anti-detection-2-pe-backdoor-manufacturing/ ,P1… https://twitter.com/i/web/status/839374930340900864
" 免杀的艺术 3 - Shellcode炼金术: https://t.co/rXJ2D8SREv 免杀的艺术 2 - PE后门制造︰ https://t.co/7FPL15kwzb 免杀的艺术 1 - 绕过杀软检测、内存加载: https://t.co/59wJ34Eenq"
-

[ Popular Software ] Ambionics Security team found critical RCE vulnerability in Drupal Services module. Details and exploit: https://t.co/wMSvhZkRjj
"DRUPAL 7.X 服务模块存在反序列化漏洞导致远程代码执行漏洞的分析,来自 Ambionics team︰ https://t.co/wMSvhZkRjj"
-

[ Popular Software ] [TECHNICAL ADVISORY] Shell Injection in #MacVim mvim URI handler…by @ dan_crowley https://www.nccgroup.trust/us/about-us/newsroom-and-events/blog/2017/february/technical-advisory-shell-injection-in-macvim-mvim-uri-handler/
" MacVim 在处理 mvim URI 时存在 Shell 注入: https://t.co/N0p6hwh23X "
-

[ Tools ] Wow, a brand new framework uses Intel's Branch-Trace-Store for transparent runtime code tracing! #CapstoneInside… https://t.co/t7YEuzWq49
"BranchMonitoringProject -- 进程监视器解决方案: https://github.com/marcusbotacin/BranchMonitoringProject"
-

[ Tools ] Unicorn v2.6 released. Adds obfuscation to the HTA attack vector. Now much harder to detect. Misc bug fixes. https://t.co/FhGQkzfiPd
" PowerShell 降级攻击框架 Unicorn v2.6 版本发布: https://t.co/FhGQkzfiPd"
-

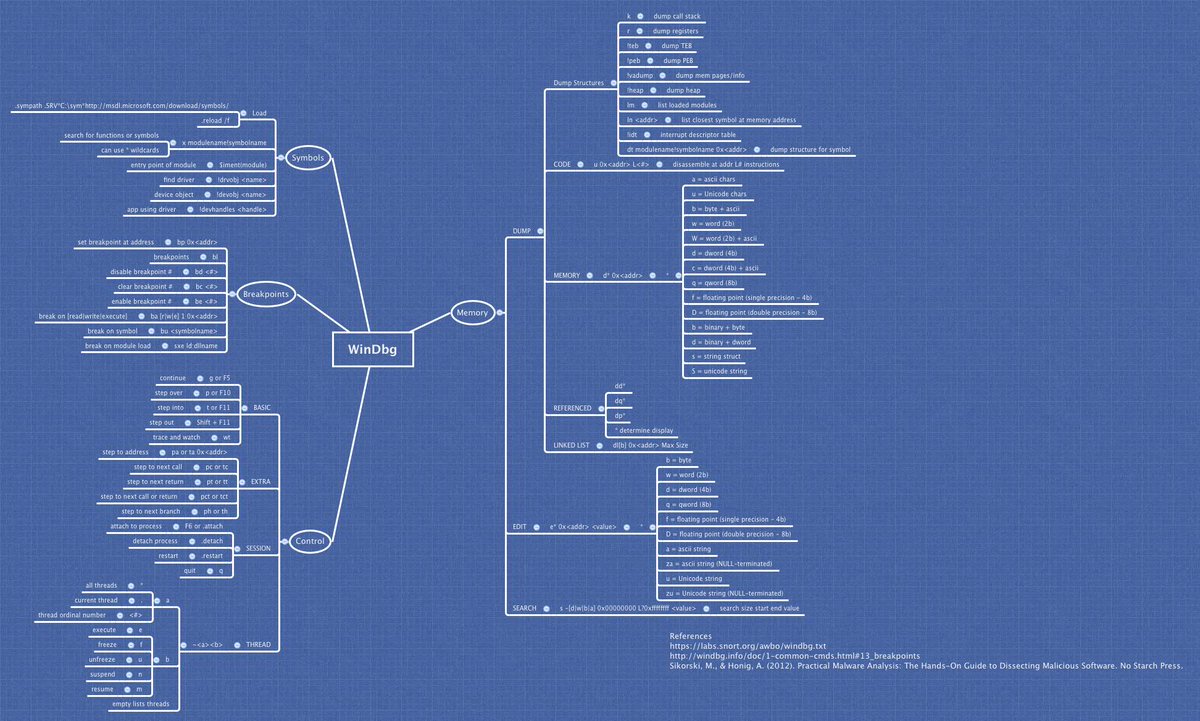
[ Tools ] A Windows Debugger WDB cheat-sheet reference curtesy of the CIA https://wikileaks.org/ciav7p1/cms/page_13762778.html https://t.co/LOwAUwhcZ2
"CIA 帮我们总结的 WinDbg 调试常用命令: https://t.co/KWCkGqUNKF https://t.co/LOwAUwhcZ2 "
-

[ Tools ] SJCL – Stanford JavaScript Crypto Library : https://github.com/bitwiseshiftleft/sjcl
"SJCL —— Stanford Javascript Crypto Library︰ https://t.co/yMTnEYoTWr"
-

[ Tools ] I wrote a ptrace based assembly repl for x86, armv7, amd64. Useful for quickly playing with unknown instructions. https://t.co/QQCLOS83F8
"rappel -- 一款交互式的汇编解释器,支持 x86、amd64 和 armv7: https://t.co/QQCLOS83F8"
-

[ Virtualization ] Hyper-V Top Level Functional Specification v5.0 - docs on Virtual Secure Mode VTL and Nested Virtualization - https://github.com/Microsoft/Virtualization-Documentation/blob/live/tlfs/Hypervisor%20Top%20Level%20Functional%20Specification%20v5.0.pdf
"微软公开的《虚拟机监控程序规范》: https://t.co/SYMLDOclbP"
-

[ Web Security ] When Bypassing JSON Encoding, XSS Filter, WAF, CSP, and Auditor turns into 8 Vulnerabilities on @Airbnb w/@bbuerhaus https://t.co/A9H7lDbG2J
"研究员 Brett Buerhaus 发现了 Airbnb 的一个跨站脚本漏洞,而且最后利用该漏洞实现了 Bypass JSON encoding, XSS filter, WAF, CSP ,同时可以 Bypass Chrome 的 XSS Auditor : https://t.co/A9H7lDbG2J"
-

[ Windows ] USBPcap (USBPcap.sys) NULL Pointer Dereference EOP Exploit https://www.exploit-db.com/exploits/41542/ (bundled with WireShark 2.2.5) #0day
" USBPcap 空指针引用可导致本地权限提升: https://t.co/ZdTgsFrlp8 "
-
[ Others ] 趋势科技研究员从漏洞、漏洞利用、Fuzz、利用缓解四个方面总结的一张脑图(Vulnerability-Exploit-Fuzz-Mitigation-v1.3.jpeg): https://pan.baidu.com/s/1pKVFsoV

 Xuanwu Spider via 游戏安全实验室
Xuanwu Spider via 游戏安全实验室