
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Browser ] Security vulnerabilities fixed in Firefox 52 https://www.mozilla.org/en-US/security/advisories/mfsa2017-05/
"Firefox 52 中修复的漏洞: https://t.co/BvMjhAptNu "
-

[ Challenges ] flAWS #aws #security challenges by @ 0xdabbad00 -> check it out. http://flaws.cloud/
" AWS 常见漏洞挑战赛: https://t.co/z44pzJjIXu"
-

[ Linux ] Security issue in Linux kernel (v4.5+) persistent memory enabling http://seclists.org/oss-sec/2017/q1/570
" Linux kernel (v4.5+) DAX mappings 存在安全问题可导致任意可读文件可被写入: https://t.co/P80rzocW5s"
-

[ MalwareAnalysis ] Analyzing PowerShell based attacks in PowerShell v5.0 with ScriptBlockLogging - http://blog.joesecurity.org/2017/03/powershell-scriptblocklogging-rocks.html?m=1 #blueteam
" 利用 ScriptBlockLogging 日志协助分析 Powershell 恶意软件: https://t.co/DjAl0KcvOU "
-

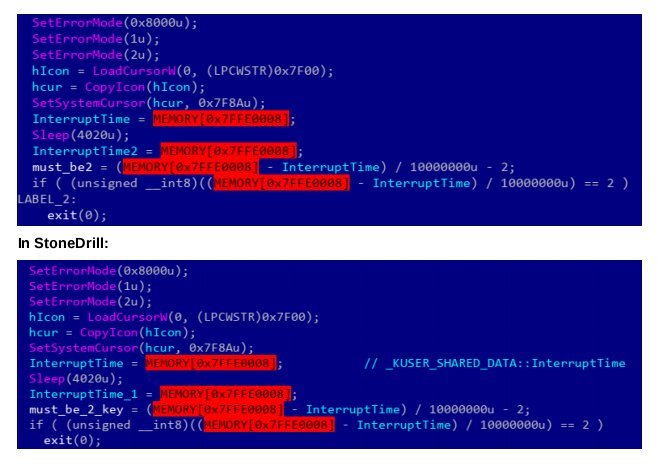
[ MalwareAnalysis ] Shamoon 2.0 / Stonedrill technical report : https://securelist.com/files/2017/03/Report_Shamoon_StoneDrill_final.pdf (pdf) https://t.co/x1rvdRZRPN
"Kaspersky 针对 Shamoon 2.0 及 Stonedrill 两款恶意软件的分析︰ https://t.co/Bxj75KMTXL "
-

[ Obfuscation ] Analyzing obfuscated scripts using nothing but a text editor http://blog.nviso.be/2017/03/07/analyzing-obfuscated-scripts-using-nothing-but-a-text-editor
"Analyzing obfuscated scripts using nothing but a text editor: https://t.co/hvn6rwjgDt "
-

[ Others ] [BLOG] How to Attack Common SSO Vulnerabilities - http://bit.ly/2lSRlyh - nice work Jem!
"基于 SAML 的单点登录(SSO)解决方案以及常见的漏洞:: https://t.co/0ReZdV4oS0"
-

[ Others ] How to securely sign .NET assemblies https://lowleveldesign.org/2017/03/07/how-to-securely-sign-dotnet-assemblies/
"如何安全的给 .NET 的字节码签名: https://t.co/EzMhLdldxU"
-

[ Pentest ] PSExec For Lateral Movement (How it works, including PowerShell variants) https://www.toshellandback.com/psexec
"PsExec 在渗透测试中的应用: https://t.co/CSERm6vlWm"
-

[ Popular Software ] #WesternDigital #MyCloud Multiples #RCE PoC Video https://www.youtube.com/watch?v=aKu_yWrIIFI https://www.exploitee.rs/index.php/Western_Digital_MyCloud #WD #infosec #NAS
"西部数码 MyCloud 系列 NAS 设备的固件安全性分析: https://t.co/Vc8AEhzbux PoC 视频: https://t.co/5JJJawFXO9 "
-

[ Programming ] awesome-safety-critical : Resources about programming practices for writing safety-critical software : https://github.com/stanislaw/awesome-safety-critical
"面向程序员的安全编码相关的资料收集︰ https://t.co/JNe1qHJiMi"
-

[ SecurityReport ] Analysing the use of outdated JavaScript libraries on the web https://blog.acolyer.org/2017/03/07/thou-shalt-not-depend-on-me-analysing-the-use-of-outdated-javascript-libraries-on-the-web/
"旧版本 (Outdated) JavaScript 库在互联网网站上的使用情况如何?根据 13.3 万网站的统计结果显示,其中 37% 的网站至少存在一个 JS 库的已知漏洞:: https://t.co/kVcDjmbLPP "
-

[ Tools ] What’s new in Visual Studio 2017 - https://www.visualstudio.com/en-us/news/releasenotes/vs2017-relnotes #VisualStudio2017
" Visual Studio 2017 发布: https://t.co/H8zKaxvl69 "
-

[ Tools ] Check-out info from @ChrisTruncer on Veil 3 including the latest update, evasion techniques, and release https://t.co/ZLFVOa7ax5 #Veil3
"免杀软件 Veil 3.0 发布: https://t.co/ZLFVOa7ax5 "
-

[ Tools ] The CIA have nice IOS exploits from GCHQ - MACHO parsing to defeat codesign, KASLR bypass OSKextCopyLoadedKextInfo https://t.co/PnY8LZoFFb
"维基解密曝光 CIA 的黑客工具 - Vault 7: https://wikileaks.org/ciav7p1/cms/index.html ,CIA 的 iOS 武器库列表: https://t.co/PnY8LZoFFb"
-

[ Tools ] Best way to integrate into @ blockadeio is the cloud node "/admin/add-indicators" call. Python script sample here - https://github.com/blockadeio/cloud_node/blob/master/test-scripts/add-indicators.py
"cloud_node -- Chrome 插件 Blockade 在本地部署的云节点: https://t.co/VkbLc3VoKC"
-

[ Tools ] Introducing BinSkim – a binary static analysis tool by Microsoft https://blogs.msdn.microsoft.com/secdevblog/2016/08/17/introducing-binskim/
"BinSkim -- microsoft 推出的一款二进制静态分析工具,用于扫描Windows PE 文件是否开启缓解措施: https://t.co/Gg7oBuLe4p "
-

[ Tools ] INTERLOCK release 2017.03.07: file creation feature, default-deny all resources in CSP, UI improvements. https://t.co/PPtUnFQe0B
"interlock -- file encryption front end: https://t.co/PPtUnFQe0B"
-

[ Windows ] Another post in the series: Windows Kernel Local Denial-of-Service #3: nt!NtDuplicateToken (Windows 7-8), http://j00ru.vexillium.org/?p=3187
"Windows 内核本地拒绝服务系列之三: nt!NtDuplicateToken (Windows 7-8): https://t.co/YHs8MYHrl9"
-

[ Windows ] Easy local Windows Kernel exploitation : https://media.blackhat.com/bh-us-12/Briefings/Cerrudo/BH_US_12_Cerrudo_Windows_Kernel_WP.pdf (pdf) #BHUSA12
" Windows 内核本地提权的三种方法:清空 ACL、获得特权、替换 Token,来自 IOActive 2012 年的总结︰ https://t.co/UjKfTbdUwC "
-

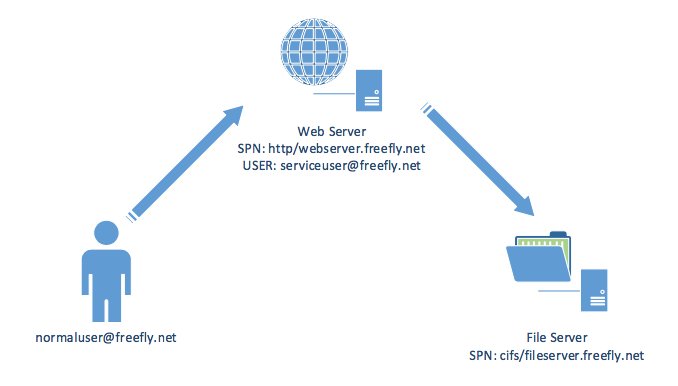
[ Windows ] New Core Labs blog "Kerberos Delegation, SPNs and More..." http://hubs.ly/H06zJPb0 by @ agsolino https://t.co/niz2ZjDH8m
"CoreSecurity 团队对 Windows 认证协议 Kerberos Delegation 特性和 SPN 的研究: https://t.co/niz2ZjDH8m "
-
[ Popular Software ] S2-045 原理初步分析(CVE-2017-5638): http://paper.seebug.org/241/ http://www.ijiandao.com/safe/cto/46798.html
 Xuanwu Spider via seebug & 爱尖刀
Xuanwu Spider via seebug & 爱尖刀