
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Browser ] 0patching another 0-day: Internet Explorer 11 Type Confusion (CVE-2017-0037) http://0patch.blogspot.com/2017/03/0patching-another-0-day-internet.html
"0patching 团队为前两周 IE HandleColumnBreakOnColumnSpanningElement 类型混淆漏洞(CVE-2017-0037)生成了一个第三方补丁:: https://t.co/8crPfJ967k"
-

[ Browser ] Chrome 57 security fixes https://chromereleases.googleblog.com/2017/03/stable-channel-update-for-desktop.html
"Chrome 发布 57 版本稳定版(57.0.2987.98),本次更新修复了多个漏洞: https://t.co/Ut2IWPsXD2"
-

[ Forensics ] AFAIK there are at least two KLEE forks with built-in taint analysis: http://repository.cmu.edu/cgi/viewcontent.cgi?article=1242&context=ece&sei-redir=1&referer=https%3A%2F%2Fscholar.google.com%2Fscholar%3Fq%3DKLEE%2B%2522taint%2Banalysis%2522%26btnG%3D%26hl%3Den%26as_sdt%3D0%252C33#search=%22KLEE%20taint%20analysis%22 and https://cs.famaf.unc.edu.ar/~rcorin/kleecrypto/icics.pdf : any others?
"KLEE 在污点分析中的实际应用: https://t.co/tp1ufhGmkl"
-

[ IoTDevice ] Multiple vulnerabilities discovered in ASUSWRT https://bierbaumer.net/security/asuswrt/
" ASUSWRT 无线路由器操作系统多个漏洞分析: https://t.co/uQiVAxacDP "
-

[ Malware ] How To Restore Your Computer From The UEFI Ransomware (Complete Removal Guide) http://bestsecuritysearch.com/restore-computer-uefi-ransomware-complete-removal-guide/
" 如何恢复受 UEFI 勒索软件影响的系统: https://t.co/icgAr69ZRP"
-

[ MalwareAnalysis ] Introduction to Reverse Engineering Cocoa Applications http://www.fireeye.com/blog/threat-research/2017/03/introduction_to_reve.html
"逆向分析 macOS 下恶意木马 Cocoa: https://t.co/HdSOAX33ma"
-

[ Network ] #KaitaiStruct is the fastest #Python binary parser among #Scapy #Construct #Hachoir in benchmark by Carolina Lucas:… https://t.co/lpOcxevZhq
-

[ Others ] J.Martin et al., "A Study of MAC Address Randomization in Mobile Devices and When it Fails" https://arxiv.org/abs/1703.02874
"移动设备的 MAC 地址随机化技术以及在具体实现中存在的问题: https://arxiv.org/pdf/1703.02874.pdf"
-

[ Pentest ] Introducing my new red teaming tool SessionGopher. Check out my post on the FireEye Threat Research Blog. https://t.co/1wIqgNk2fn
"渗透过程中,由于 Linux 系统没有入域的概念,发现和定位他们不太容易。FireEye 这篇 Blog 介绍了一个工具,这个工具用于从 Windows 系统的 WinSCP、PuTTY、SuperPuTTY、FileZilla 等常见应用中提取用户连接过的 Linux 机器信息: https://t.co/1wIqgNk2fn Github: https://github.com/fireeye/SessionGopher"
-

[ Popular Software ] Very cool Google Maps XSS https://medium.com/@ marin_m/how-i-found-a-5-000-google-maps-xss-by-fiddling-with-protobuf-963ee0d9caff#.o2rm7fh0g #XSS #BugBounty #vulnerability #GoogleMaps
"我是如何挖掘到价值 5000 美元的 Google Maps XSS 漏洞的: https://t.co/IDA3CxQCuL "
-

[ Popular Software ] Notepad++ release v7.3.3 - Fix CIA Hacking Issue : https://notepad-plus-plus.org/news/notepad-7.3.3-fix-cia-hacking-issue.html , Notepad++ DLL Hijack (Vault7 / CIA) : https://wikileaks.org/ciav7p1/cms/page_26968090.html
"Notepad + + 发布 v7.3.3 版本,修复了 CIA 文档中暴露的问题︰ https://t.co/Eoq8iuyr2a Notepad + + DLL 劫持 (Vault7 / CIA): https://t.co/goITr24qOu"
-

[ Programming ] Vulnerability Spotlight: R - PDF LoadEncoding Code Execution Vulnerability http://blog.talosintelligence.com/2017/03/r-pdf-vuln.html
"R-PDF LoadEncoding 代码执行漏洞(CVE-2016-8714): https://t.co/IlmlJHkYVF"
-

[ Programming ] Git Internals: http://opcode.org/peepcode-git.pdf (pdf)
"针对 Git 爱好者的 Git 学习手册︰ https://t.co/fEx8ztcz3j "
-

[ Programming ] An In-Depth Study of > 10 Yrs of Java Exploitation : https://testlab.sit.fraunhofer.de/downloads/publications/holzinger2016java.pdf (pdf)
"通过 87 个公开的 Java 漏洞,对 Java 安全架构进行深度研究︰ https://t.co/jEsQetSd6x "
-

[ Tools ] HighTouch-WPS-Breaker #Bash script to extract the #WPS pin of many #vulnerable #routers and get the password https://t.co/kNgNLoU5tG
"HT-WPS-Breaker: 高性能WPS破解工具: https://t.co/kNgNLoU5tG"
-

[ Tools ] PoC to show why HttpOnly flag isn't a complete protection against session hijacking via XSS.… https://t.co/CPZI4UbZjl
"HttpPwnly -- XSS 后渗透工具,用于大规模的控制浏览器: https://github.com/Danladi/HttpPwnly"
-

[ Tools ] Many new and updated MISP expansion modules available in misp-modules including @ ThreatMiner https://github.com/MISP/misp-modules/ #ThreatIntel
"misp-modules -- MISP扩展服务模块: https://t.co/4GgBZ8ga54 "
-

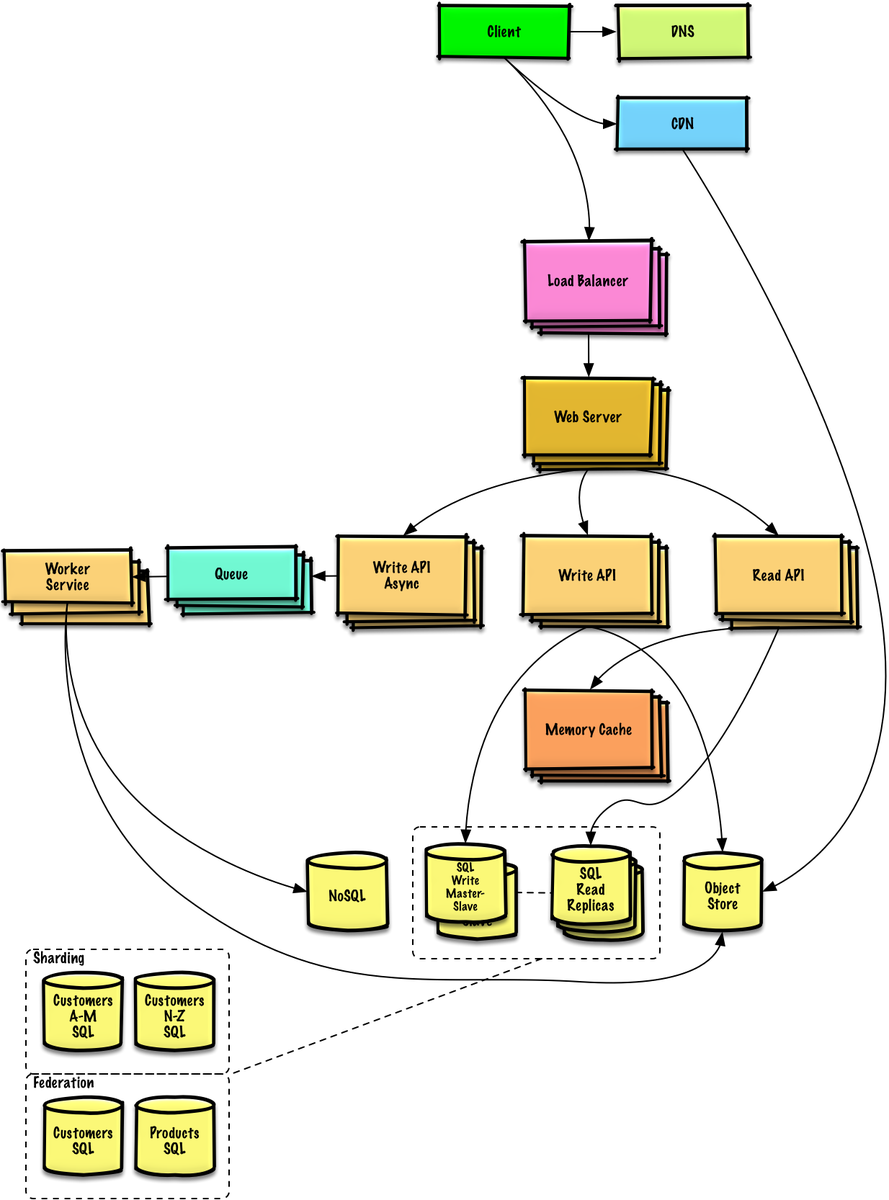
[ Tools ] The System Design Primer : https://github.com/donnemartin/system-design-primer https://t.co/0yLmB5ZMAE
"如何设计一个规模较大的系统︰ https://t.co/GaFMZI82Oc "
-

[ Windows ] [New Post] Various Privilege Escalation Methods via Unquoted Service Path https://pentestlab.blog/2017/03/09/unquoted-service-path/ #pentestlab #pentest #privilegeescalation
"未用引号包含的服务路径可导致本地权限提升漏洞: https://t.co/Sgkq5726KO "
-

[ Windows ] New code injection detection features in #WDATP creators update. Lots of case studies https://blogs.technet.microsoft.com/mmpc/2017/03/08/uncovering-cross-process-injection-with-windows-defender-atp/
"Windows Defender 高级威胁防护(ATP)方案是如何发现跨进程注入行为的: https://t.co/lZ6J5BUZRb"
 Xuanwu Spider via seebug
Xuanwu Spider via seebug