腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] ESET paper on the evolution of Android ransomware is a good read. http://www.welivesecurity.com/wp-content/uploads/2017/02/ESET_Trends_2017_in_Android_Ransomware.pdf
"Android 勒索软件的的演变: https://t.co/CYII96rg3l"
-

[ Android ] Hacking an Android phone. How deep the rabbit hole goes: https://medium.com/@ kayrus/hacking-android-phone-how-deep-the-rabbit-hole-goes-18b62ad65727
" Hacking Android phone - 兔子洞能有多深?︰ https://t.co/7i9VSuY0AR"
-

[ Attack ] Financial cyberthreats in 2016 https://securelist.com/analysis/publications/77623/financial-cyberthreats-in-2016/
"2016 年金融领域的网络威胁报告,来自卡巴斯基: https://t.co/Msgd3OpUFC"
-

[ Browser ] Google Chrome: out-of-bound read in layout https://bugs.chromium.org/p/project-zero/issues/detail?id=1024
"Chrome 浏览器 layout 过程中的一个越界读漏洞: https://t.co/wT6EkKwPEc"
-

[ Browser ] Apple WebKit: UXSS via Frame::setDocument https://bugs.chromium.org/p/project-zero/issues/detail?id=1057
" WebKit Frame::setDocument UXSS(CVE-2017-2365): https://t.co/Hh7zR95X6B"
-

[ Browser ] Apple WebKit: Bypass pop-up blocker via cross-origin or sandboxed iframe. https://bugs.chromium.org/p/project-zero/issues/detail?id=1050
" 通过跨域或者 sandboxed iframe 绕过 WebKit 的弹框屏蔽器(pop-up blocker)(CVE-2017-2371),漏洞发现者为 lokihardt: https://t.co/5bCgxdcJKm"
-

[ Browser ] Apple WebKit: UXSS via FrameLoader::clear https://bugs.chromium.org/p/project-zero/issues/detail?id=1049
" WebKit FrameLoader::clear UXSS(CVE-2017-2363): https://t.co/tJMkB8yx83"
-

[ Challenges ] The sourcecode and deployment files for all of our @ BSidesSF #CTF challenges: https://github.com/BSidesSF/ctf-2017-release
" BSidesSF 会议 CTF 比赛相关的源码和文件︰ https://t.co/OA3cxAyeXe"
-

[ Crypto ] SSLyze - An SSL/TLS scanner ( detects various issues bad certificates, dangerous cipher suites ) : https://nabla-c0d3.github.io/blog/2017/02/08/sslyze-1-0-0-released/ cc @ nabla_c0d3
"SSLyze - SSL/TLS 扫描器,可以用于检测危险加密套件、不合法证书等问题︰ https://t.co/AqwthFBVE9 FreeBuf 之前也有过介绍这个工具的文章: http://www.freebuf.com/sectool/107967.html "
-

[ Exploit ] Teaching Old Shellcode New Tricks https://recon.cx/2017/brussels/resources/slides/RECON-BRX-2017-Teaching_Old_Shellcode_New_Tricks.pdf #ExploitDev #InfoSec https://t.co/UUGPuUHDYt
" 给旧 Shellcode 添加新技能: https://t.co/XW6pUWqkxN https://t.co/UUGPuUHDYt"
-

[ Firmware ] Slides from our "New vulnerabilities in Coreboot and UEFI based firmware" talk at @ reconbrx : http://www.intelsecurity.com/advanced-threat-research/content/data/REConBrussels2017_BARing_the_system.pdf [pdf]
" Coreboot 与基于 UEFI 的固件的新漏洞,来自 RECON 会议: https://t.co/i4cmlqLNNt "
-

[ Hardware ] Leaking (a lot of) Data from Air-Gapped Computers via (small) Hard Drive LED : http://cyber.bgu.ac.il/advanced-cyber/system/files/LED-it-GO_0.pdf (pdf) Demo : https://www.youtube.com/watch?v=4vIu8ld68fc
" 利用硬盘指示灯,从物理隔离的计算机泄漏数据︰ https://t.co/jKg3GeGv6w https://t.co/tFTA1IWGWb"
-

[ Linux ] Linux kernel: CVE-2017-6074: DCCP double-free vulnerability (local root) http://seclists.org/oss-sec/2017/q1/471
"Linux 内核 DCCP Double Free 代码执行漏洞(CVE-2017-6074),可以实现本地 ROOT: https://t.co/ZqKHNXB40S"
-

[ Malware ] These attacks combine TeamViewer’s VPN tool with a keylogger. https://threatpost.com/data-stealing-malware-teamspy-resurfaces-in-spam-campaign/123820/ via @ threatpost
" TeamSpy 恶意软件再次被发现,这次是在 TeamViewer 的 VPN 捆绑 Keylogger: https://t.co/hitlySOas3"
-

[ Network ] HOW TO USE WIRESHARK A PACKET SNIFFER TO ANALYZE NETWORK TRAFFIC https://www.custompcreview.com/articles/tutorial-wireshark-packet-sniffer-guide-analyze-network-traffic/38446/
" 用 WIRESHARK 分析网络流量的教程(基础版): https://t.co/NWv9O54552"
-

[ Others ] LuaJIT Hacking: Getting next() out of the NYI list https://blog.cloudflare.com/luajit-hacking-getting-next-out-of-the-nyi-list/
" LuaJIT Hacking: https://t.co/vId4hvr3mx "
-

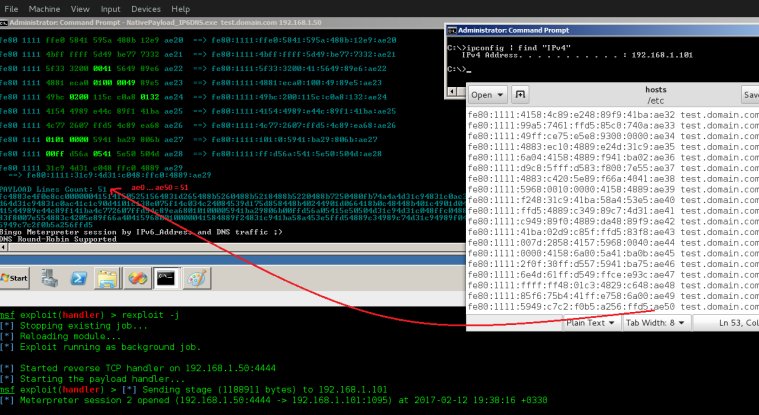
[ Pentest ] Transferring Backdoor Payloads by DNS AAAA records and IPv6 Address : https://www.peerlyst.com/posts/transferring-backdoor-payloads-by-dns-aaaa-records-and-ipv6-address-damon-mohammadbagher cc @ _Damon_M_ https://t.co/mBQTx0Q4Cm
"通过 DNS AAAA 记录和 IPv6 地址传递后门 Payload︰ https://t.co/dwJw8GJx1h https://t.co/mBQTx0Q4Cm"
-

[ Popular Software ] EasyCom PHP API Stack Buffer Overflow https://goo.gl/fb/jsiGlJ #FullDisclosure
"EasyCom 中间件 PHP API 堆栈缓冲区溢出漏洞(CVE-2017-5358): https://t.co/A1GgZzupv0 "
-

[ Popular Software ] Vulnerability Spoltlight: Multiple Vulnerabilities in the Aerospike NoSQL Database Server http://blogs.cisco.com/security/talos/aerospike-vulnerabilities-2
" Aerospike NoSQL Database Server 被发现多个漏洞: https://t.co/fas8oIiBgX "
-

[ ReverseEngineering ] Finding The Lost Vikings – Reversing a Virtual Machine https://ryiron.wordpress.com/2017/02/01/finding-the-lost-vikings-reversing-a-virtual-machine/
"逆向 Vikings(维京传奇)游戏的虚拟机: https://ryiron.wordpress.com/2017/02/01/finding-the-lost-vikings-reversing-a-virtual-machine/ "
-

[ Tools ] Unicorn v2.4.3 released. Adds improved macro injection. obfuscation, and evasion. http://github.com/trustedsec/unicorn #TrustedSec
" PowerShell 降级攻击框架 Unicorn 更新 2.4.3 版本: https://t.co/FhGQkzfiPd "
-

[ Tools ] Lilu is a new MacOS kernel extension & framework to support patching kext, library & process. #CapstoneInside https://t.co/FtKPGeqsUO
" Lilu - macOS 平台用于 Patch 内核扩展、进程的框架: https://t.co/FtKPGeqsUO "
-

[ Tools ] mongoaudit - A Powerful MongoDB Auditing and Pentesting Tool http://www.kitploit.com/2017/02/mongoaudit-powerful-mongodb-auditing.html
"mongoaudit -- 一个强大的 MongoDB 审计与渗透测试工具 : https://t.co/WurOpwSw6I"
-

[ Tools ] Updated the Shodan 3D interface with URL hashing and fixed some bugs: https://simple.shodan.io/#query=category%3Amalware #threejs
" Shodan 搜索开始支持 3D 角度展示了︰ https://t.co/XfuTJ1kGUG "
-

[ Web Security ] How I could Steal Your Google Bug Hunter Account with Two Clicks in IE : http://ngailong.com/how-i-could-steal-your-google-bug-hunter-account-with-two-clicks-in-ie/ cc @ ngalongc
"通过 IE 浏览器的两次点击,我就可以偷到你 Google Bug Hunter 的账户信息︰ https://t.co/MWwMPuKePX "
-

[ Windows ] New blog post: Windows Kernel Local Denial-of-Service #1: win32k!NtUserThunkedMenuItemInfo (Windows 7-10), http://j00ru.vexillium.org/?p=3101
" Windows 内核本地拒绝服务 #1: win32k!NtUserThunkedMenuItemInfo,影响 Windows 7-10,作者为 j00ru: https://t.co/jAh4pQV7Ik"