
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] I updated by targeted threats tracker, with latest reports and indicators of compromise https://github.com/botherder/targetedthreats
" 定向威胁攻击中的 IOC 收集,也包括处理好的 Snort 规则: https://t.co/Ue0NZ1BMyo"
-

[ Browser ] Fingerprinting Firefox users with cached intermediate CA certificates. #fiprinca https://shiftordie.de/blog/2017/02/21/fingerprinting-firefox-users-with-cached-intermediate-ca-certificates-fiprinca/ https://t.co/LfRKAu3tbI
"利用缓存的中间 CA 证书为 Firefox 用户建立指纹信息: https://t.co/6FQlN4ANlT https://t.co/LfRKAu3tbI"
-

[ Browser ] BeEF now supports persistent hooking in IE 11 using an invisible HTMLFile ActiveX object https://github.com/beefproject/beef/pull/1364 @ beefproject @ MagicMac2000
"浏览器利用框架 BeEF 支持利用不可见的 HTMLFile ActiveX 对象 Hook IE 11 了: https://t.co/aR2oIBqAqi "
-

[ Conference ] RSA 2017 Videos Playlist https://www.youtube.com/playlist?list=PLeUGLKUYzh_j1Q75yeae8upX-T1FLmZWf
"RSA 2017 会议的视频集: https://t.co/LcWGbW4qHK"
-

[ Defend ] Hardware Supported Process Isolation – An introduction - http://www.kerneldrivers.com/hardware-supported-process-isolation-introduction/
"硬件支持的进程隔离方法介绍: https://t.co/eHHcdwoWZm"
-

[ IoTDevice ] Reversing Internet of Things from Mobile applications (PDF) http://area41.io/downloads/slides/area41_16_apvrille_mobileiot.pdf
" 分析 IoT 设备安全性时可以先从手机 APP 入手: https://t.co/IMa77osHvy"
-

[ Malware ] PlugX + Poison Ivy = PlugIvy? ― PlugX Integrating Poison Ivy’s Code http://blog.jpcert.or.jp/2017/02/plugx-poison-iv-919a.html by @ jpcert_en
"PlugX 中嵌有 PlugIvy 的代码,来自日本 CERT: https://t.co/Imu8pTjkCl "
-

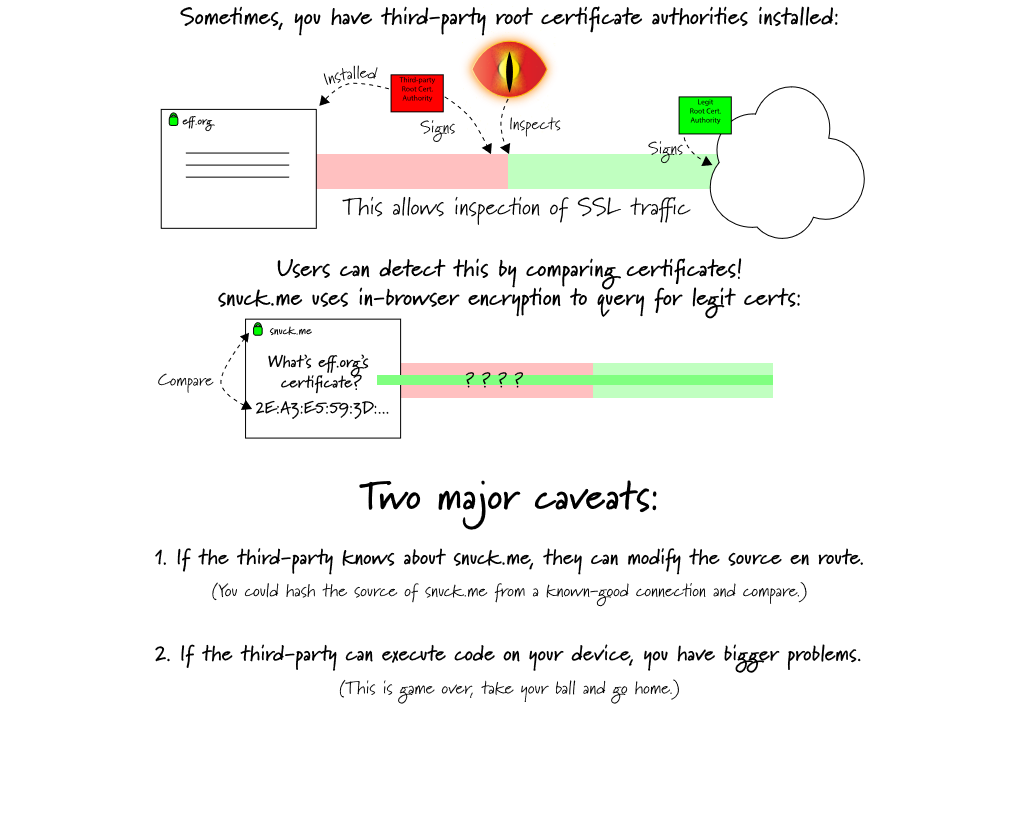
[ Network ] snuck.me : a service detecting SSL man-in-the-middle : https://jlospinoso.github.io/node/javascript/security/cryptography/privacy/2017/02/20/snuckme-cert-query.html https://t.co/7pbbqvO6aj
"snuck.me︰ 检测 SSL 中间人的服务︰ https://t.co/HYboAVEyHp https://t.co/7pbbqvO6aj"
-

[ Tools ] Puppy RAT a Python cross platform RAT https://github.com/n1nj4sec/pupy
" Puppy RAT - Python 语言编写的跨平台的远控工具: https://t.co/6JTHTGWIRf"
-

[ Tools ] Another option for file sharing https://security.googleblog.com/2017/02/another-option-for-file-sharing.html
" Google 公开了一个工具 Upspin 用于文件共享: https://t.co/11SNMuvkEr"
-

[ Tools ] Offline Digital Forensics Tool for Binary Files: ByteForce https://n0where.net/offline-digital-forensics-tool-byteforce/ #InfoSec #CyberSecurity
"二进制文件的离线数字取证工具︰ ByteForce https://t.co/sEb01EUrJi "
-

[ Tools ] iOSkextdump is a new tool to dump kernel extension information from iOS kernel cache. #CapstoneInside https://t.co/PUHDj2Qba3
"iOSkextdump - 从 iOS 内核缓存中 Dump 内核扩展信息的工具: https://t.co/PUHDj2Qba3"
-

[ Tools ] Lighthouse (https://github.com/gaasedelen/lighthouse) pulling input from DynamoRio's code coverage tool into IDA Pro. Clean UI, clean code. Nice work.
" Lighthouse - IDA Pro 的一款插件,用于分析代码覆盖率: https://github.com/gaasedelen/lighthouse "
-

[ Web Security ] Same-Origin Policy, CSRF and Cross-Origin Resource Sharing (CORS) https://mo.github.io/2017/02/20/cross-origin-resource-sharing.html
"同源策略、 CSRF 和跨域资源共享 (CORS): https://t.co/8rrKeo5wdD"
-

[ Web Security ] Privilege Escalation in Amazon Web Services. https://blog.cloudsploit.com/privilege-escalation-in-amazon-web-services-cb4837365958#.6y1uzyxlq
" 亚马逊 Web 服务中的提权: https://t.co/xrj4x90kpJ"
-

[ Windows ] @ _samdb_ code is all at https://github.com/sam-b/windows_kernel_address_leaks
" 从用户态泄漏 Windows 内核地址信息的多个实例代码: https://t.co/SEWLEXNsn8"
-

[ Windows ] Did a blag - 'Revisiting Windows Security Hardening Through Kernel Address Protection' https://samdb.xyz/revisiting-windows-security-hardening-through-kernel-address-protection/
" 从内核针对地址的保护看 Windows 的安全性加固措施: https://t.co/iSxUTuNcb5"
-

[ Windows ] Windows driver signature bypass by derusbi - http://www.sekoia.fr/blog/windows-driver-signing-bypass-by-derusbi/ Driver Signature Enforcement (by @ j00ru) - http://j00ru.vexillium.org/?p=377
" Windows 内核驱动的签名检查绕过(2015): https://t.co/KhlyT6qO4B j00ru 对 Windows 的驱动签名检查增强机制的分析: https://t.co/nNjIU7R9Qu "
-

[ WirelessSecurity ] Hacking exposed wireless:Wireless security secrets & solution second edition (PDF) http://dl.finebook.ir/book/4b/14104.pdf https://t.co/uYkbSoQRrx
"黑客大曝光-无线渗透 (PDF): https://t.co/fKtYgNDzTW "
-
[ Android ] Android 源代码情景分析法,了解罗老师是怎么分析 Android 源代码(视频): http://0xcc0xcd.com/p/videos/analyse-aosp.php
-
[ Windows ] 微软的 Microsoft Ignite China 2016 会议: https://channel9.msdn.com/Events/Ignite/Microsoft-Ignite-China-2016?sort=status&direction=desc 其中有张银奎老师关于 Windows 内核的演讲《Windows 内核揭秘》: https://channel9.msdn.com/Events/Ignite/Microsoft-Ignite-China-2016/WIN-B301
-
[ Windows ] 32 位程序对 64 位进程的远程注入实现:http://www.4hou.com/technology/3426.html

 Xuanwu Spider via 罗升阳
Xuanwu Spider via 罗升阳