
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

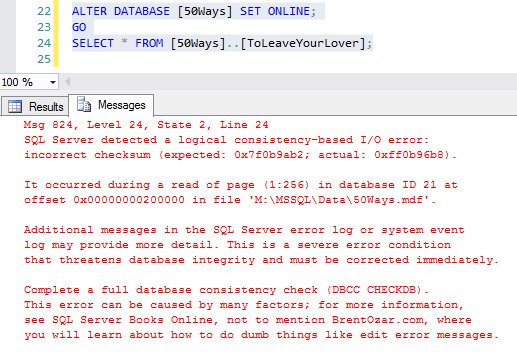
[ Attack ] Let’s Corrupt a SQL Server Database Together (Part 1: Clustered Indexes) : https://www.brentozar.com/archive/2017/02/lets-corrupt-sql-server-database-together/ https://t.co/j9xZPq7GI5
"SQL Server 大破坏(Part 1: Clustered Indexes),在 SQL Server 未开启 PAGE_VERIFY 的情况下可以任意篡改数据库文件: https://t.co/hySjsrgMq9 https://t.co/j9xZPq7GI5"
-

[ Browser ] Edge adds the option for mandatory code signing enforcement and blocking of new executable pages. Killer with cfg. https://t.co/jcMKdehjGw
"微软安全团队在缓解 Edge浏览器 Native 代码执行方面是如何考虑及实施的: https://t.co/jcMKdehjGw"
-

[ Browser ] Microsoft Edge and IE: Type confusion in HandleColumnBreakOnColumnSpanningElement https://bugs.chromium.org/p/project-zero/issues/detail?id=1011
"Microsoft Edge 及 IE 浏览器 HandleColumnBreakOnColumnSpanningElement 中存在类型混淆漏洞(CVE-2017-0037): https://t.co/Wxy5Ua11Nh"
-

[ Conference ] Satellite Based IP Content Delivery Network : https://recon.cx/2017/brussels/resources/slides/RECON-BRX-2017-Reverse_Engineering_Satellite_Based_IP_Content_Distribution.pdf (Slides)
"基于卫星的 IP 内容传输网络,来自 RECON BRX 2017 大会︰ https://t.co/H0Ghu1U2Gb "
-

[ MalwareAnalysis ] Dissecting the Qadars Banking Trojan https://info.phishlabs.com/blog/dissecting-the-qadars-banking-trojan
"Qadars 银行木马分析: https://t.co/zB6hovCP6Y"
-

[ MalwareAnalysis ] In-depth Analysis of Disttrack Malware : https://www.cylance.com/en_us/blog/threat-spotlight-disttrack-malware.html https://t.co/eHwrIs0iR2
"深入分析 Disttrack 恶意软件︰ https://t.co/S40jL8u1Nv https://t.co/eHwrIs0iR2"
-

[ Tools ] Let’s Build a Compiler : http://www.stack.nl/~marcov/compiler.pdf (pdf)
"编译器编写教程︰ https://t.co/dLlJ6ILzyb"
-

[ Tools ] Super excited to release Unicorn Emulator v1.0, with lots of bug fixes, new APIs & 3 more bindings added! Plz RT https://t.co/azGQreLr4f
"Unicorn Emulator v1.0 发布: https://t.co/azGQreLr4f"
-

[ Tools ] Shell Factory is a framework for compiling shellcodes from a C++ source for multiple systems and architectures: https://t.co/KFoTmGBiGZ
"shell-factory -- 一个用于将 C++ 代码编译支持成多平台多系统的shellcode 的框架︰ https://t.co/KFoTmGBiGZ"
-

[ Tools ] Hardentools is an experimental utility in beta to harden certain Windows features. Looking for testing and code. https://t.co/3DQL5MVfgW
"Hardentool -- 用于禁用操作系统和部分应用程序中的一些功能,旨在减少计算机的攻击面: https://t.co/3DQL5MVfgW"
-

[ Tools ] Here's a basic POC on how to extend the Windows Script Host to load your dll. https://github.com/subTee/WindowsScriptHostExtension I find it interesting.
"WindowsScriptHostExtension -- WSH扩展组件: https://t.co/PK3Zae0pFj"
-

[ Vulnerability ] #CloudBleed cloudflare: Cloudflare Reverse Proxies are Dumping Uninitialized Memory https://bugs.chromium.org/p/project-zero/issues/detail?id=1139 https://t.co/VYHXIDMzcf
"cloudflare 服务器在解析文档时存在一个内存泄露漏洞,攻击者可以通过该漏洞泄露其他客户的敏感信息,包括加密密钥、cookie等: https://t.co/SlHsEUYkWd 漏洞细节: https://blog.cloudflare.com/incident-report-on-memory-leak-caused-by-cloudflare-parser-bug/?utm_content=buffere476a&;utm_medium=social&utm_source=twitter.com&utm_campaign=buffer"
-

[ Web Security ] Web Service Hacking https://www.soapui.org/soap-and-wsdl/tips---tricks/web-service-hacking.html
"10 个测试 Web Service 登录的技巧: https://t.co/OFfokrqlKE"
-

[ Web Security ] Using Burp Macros and Sqlmap to exploit SQL injection with CSRF protection https://www.cyberis.co.uk/burp_macros.html
"为 BurpSuite 创建宏的教程,结合 BurpSuite 宏与 Sqlmap 来对存在 CSRF 防御的 SQL 注入漏洞进行利用: https://t.co/Xeoc4bnsOG"
-

[ Windows ] [BLOG] Analysis of MS16-104: .URL files Security Feature Bypass (CVE-2016-3353) http://blog.quarkslab.com/analysis-of-ms16-104-url-files-security-feature-bypass-cve-2016-3353.html by @ fdfalcon & @ RichardLeDe
"MS16-104漏洞分析: .URL 文件安全特性绕过 (CVE-2016-3353): https://t.co/OXOKeaeWZE "
-
[ APT ] 中部的熊 - 针对民主党委员会的入侵, 来自 CrowdStrike 2016 年 6 月的分析报告: https://www.crowdstrike.com/blog/bears-midst-intrusion-democratic-national-committee/
-
[ Crypto ] 密码学大事件!研究人员公布第一例SHA-1哈希碰撞实例: https://zhuanlan.zhihu.com/p/25401383 Google 的原始链接: https://security.googleblog.com/2017/02/announcing-first-sha1-collision.html

 Xuanwu Spider via CrowdStrike
Xuanwu Spider via CrowdStrike