腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

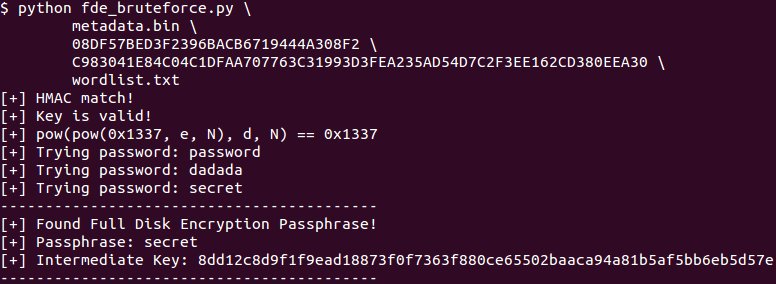
[ Android ] New blog post: https://bits-please.blogspot.com/2016/06/extracting-qualcomms-keymaster-keys.html Extracting Qualcomm's KeyMaster Keys - Breaking Android Full Disk Encryption! https://t.co/fE5Bc6ndUJ
" 提取高通的 KeyMaster 密钥,破坏 Android 全盘加密︰ https://t.co/Ni9RdLWwIp https://t.co/fE5Bc6ndUJ 相关的代码: https://github.com/laginimaineb/ExtractKeyMaster https://github.com/laginimaineb/android_fde_bruteforce "
-

[ Attack ] The inner workings of Pacifier APT. http://download.bitdefender.com/resources/files/News/CaseStudies/study/115/Bitdefender-Whitepaper-PAC-A4-en-EN1.pdf
" Pacifier(奶嘴) APT 攻击行动分析报告,来自 BitDefender: https://t.co/Wnl0xKqLT1"
-

[ Attack ] 2 million-person terror database leaked online https://thestack.com/security/2016/06/29/2-million-person-terror-database-leaked-online/
"200 万的可疑恐怖分子数据库泄漏: https://t.co/zJ1VLuFyxX"
-

[ Browser ] The history of HTML styling https://eager.io/blog/the-languages-which-almost-were-css/
" HTML 样式语言的历史 - 一门差点成为 CSS 的语言: https://t.co/Pg0Ba6iomx"
-

[ Crypto ] [BLOG] A brief survey of Fully Homomorphic Encryption, computing on encrypted data http://blog.quarkslab.com/a-brief-survey-of-fully-homomorphic-encryption-computing-on-encrypted-data.html
" 全同态加密的简短分析,来自 QuarksLab Blog: https://t.co/sADT0Glvgx"
-

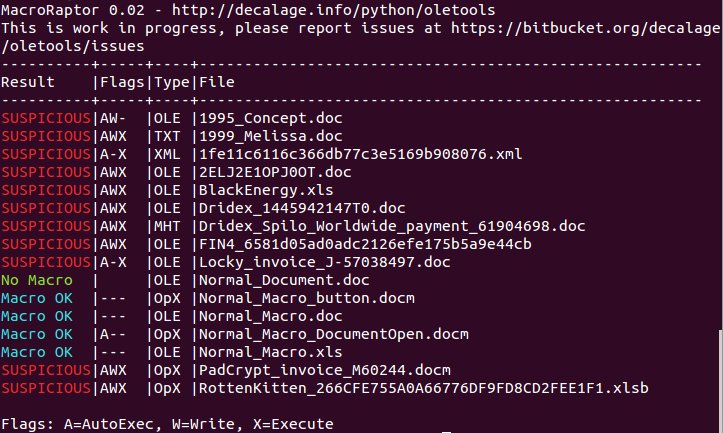
[ Detect ] How to detect most malicious macros without an antivirus (part 1): http://decalage.info/mraptor https://t.co/BeIGUgdIEz
" 不依赖杀软,检测大部分的恶意宏代码(利用 mraptor 工具)︰ https://t.co/bOI7jeuRx0 https://t.co/BeIGUgdIEz"
-

[ Malware ] KSN Report: Mobile ransomware in 2014-2016 https://securelist.com/analysis/publications/75183/ksn-report-mobile-ransomware-in-2014-2016/
"2014~2016 手机勒索软件发展趋势报告,来自 Kaspersky: https://t.co/udbURJUaBE "
-

[ Malware ] Getting a #PlugX builder http://blog.airbuscybersecurity.com/post/2016/06/Getting-a-PlugX-builder
" 寻找 PlugX 远控工具的生成器: https://t.co/VQfDCScBfI"
-

[ Malware ] Related attackers? @ PaloAltoNtwks #Unit42 connects past and recent #MNKit activity: http://bit.ly/2961qGM
" MNKit(CVE-2012-0158 Exploit 生成器)最近的活动情况,来自 Palo Alto Blog︰ https://t.co/nZXMTYUs7z"
-

[ Malware ] New Blog Post - Asruex: Malware Infecting through Shortcut Files ^ST http://blog.jpcert.or.jp/2016/06/asruex-malware-infecting-through-shortcut-files.html
" 基于快捷方式的恶意代码感染技术,来自日本 CERT: https://t.co/1fdbOUuf3U"
-

[ Malware ] Hummer Android trojan: 18 root methods, 1.4m infected devices daily at peak, pushes games, silent pr*n install http://www.cmcm.com/blog/en/security/2016-06-29/995.html
" 猎豹移动安全实验室发现了一个叫做悍马(Hummer)的手机木马,木马来自中国,该木马有 18 种 ROOT 方法,高峰时每天感染 140 万设备,日赚 50 万美元: https://t.co/r6x6a9a97e"
-

[ Malware ] #Facebook #malware tricks users into thinking a friend has tagged them https://kas.pr/k7Fk via @ Securelist
" 攻击 Facebook 用户的恶意软件 - 有能耐你给我打个标签,来自 Kaspersky Blog: https://t.co/8IOuW6v7pX"
-

[ Others ] New post: Brazilians Migrate to Telegram, Cybercriminals Follow Suit http://bit.ly/29fuX1k @ TrendMicro
" 巴西用户抛弃 WhatsApp,转投 Telegram,网络犯罪分子也开始跟风: https://t.co/ST6DSL8qyg "
-

[ Others ] Introducing Worldwide SMS Messaging from Amazon SNS : https://mobile.awsblog.com/post/TxSP0HUNM8FQ1Y/Introducing-Worldwide-SMS-Messaging https://t.co/vx6V6S6tnW
"亚马逊的全球短消息发送服务︰ https://t.co/taQDpLuACC https://t.co/vx6V6S6tnW"
-

[ Others ] Slides from "How Do I Crack Satellite and Cable Pay TV?" at #reconmtl: https://www.dropbox.com/s/6fkpn97x3119m74/REcon%202016%20-%20How%20Do%20I%20Crack%20Satellite%20and%20Cable%20Pay%20TV.pdf?dl=0 (12MB PDF) @ reconmtl https://t.co/bHqWtv9irT
" 我是如何黑掉卫星和有线付费电视的,来自 RECon 会议的 PPT︰ https://t.co/6UUlz6N8Oh https://t.co/bHqWtv9irT"
-

[ Others ] Step Change in Security with Modern Devices and Architecture - https://blogs.technet.microsoft.com/windowsitpro/2016/06/29/step-change-in-security-with-modern-devices-and-architecture/
" 现代设备与体系架构在安全上的巨大变化,来自微软 Blog: https://t.co/4gd8SY42f3"
-

[ Popular Software ] Foxit patched 12 vulns in its PDF reader - all which could be used for #RCE -http://ow.ly/K5pl301Ok5U
"Foxit 阅读器更新 8.0 版本,本次更新修复了 12 个漏洞,来自 ThreatPost 的报道: https://t.co/aAu1gZ6uWR 官方的公告: https://www.foxitsoftware.com/support/security-bulletins.php#content-2016 "
-

[ Popular Software ] [blog] "A Case Study in Attacking KeePass" http://www.harmj0y.net/blog/redteaming/a-case-study-in-attacking-keepass/
" 针对密码管理软件 KeePass 的攻击案例研究: https://t.co/df2pAhDldt"
-

[ Popular Software ] ZDI-16-393: Foxit Reader Pattern Uninitialized Pointer Remote Code Execution Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-393/
" 福昕阅读器在处理 PDF Pattern 时存在一个未初始化指针 RCE 漏洞,来自 ZDI 的公告: https://t.co/LRQEziEeKK"
-

[ Popular Software ] ZDI-16-394: Foxit Reader FlateDecode Use-After-Free Remote Code Execution Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-394/
" 福昕阅读器 FlateDecode UAF,来自 ZDI 公告 ZDI-16-394: https://t.co/viSVF8W5Cv Adobe Reader 也有过一个类似的: http://www.zerodayinitiative.com/advisories/ZDI-16-359/ "
-

[ ReverseEngineering ] I just published “Researching protection and recovering Namco System ES1 arcades” https://medium.com/p/researching-protection-and-recovering-namco-system-es1-arcades-1f8423fdeb3b
" Namco System ES1 游戏系统的防护和还原机制研究: https://t.co/84RX9Uv5WU"
-

[ SecurityProduct ] Very critical 0day. https://github.com/cuckoosandbox/cuckoo/issues/984
" Cuckoo 沙盒 agent.py 通过 XMLRPC 可以触发的一个提权漏洞: https://t.co/OR9RLGOwsY"
-

[ Windows ] How to Bypass Application Whitelisting http://buff.ly/2995IwK #windows #hacking https://t.co/TM6VNzRYrJ
" Bypass 应用白名单: https://t.co/jrzfccQwbO https://t.co/TM6VNzRYrJ"
-

[ Windows ] [Blog Post] What you probably didn't know about regsvr32.exe http://subt0x10.blogspot.com/2016/06/what-you-probably-didnt-know-about.html Feedback Welcome.
" 关于 regsvr32.exe,你可能不知道的事儿: https://t.co/W79HkPGoec 在 regsvr32 进程中执行 Mimikatz: https://gist.github.com/subTee/c3d5030bb99aa3f96bfa507c1c184504 "
-

[ Windows ] [local] - Windows 7 SP1 x86 - Privilege Escalation (MS16-014) https://www.exploit-db.com/exploits/40039/
" Windows MS16-014 提权漏洞的 PoC(Windows 7 SP1 x86 提权),来自 ExploitDB,页面上的 CVE-2016-0400 写错了,应该是 CVE-2016-0040: https://t.co/JniUivuWPY"