腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Android security :) (Source) https://conference.hitb.org/hitbsecconf2016ams/materials/D1T2%20-%20Tim%20Xia%20-%20Adaptive%20Android%20Kernel%20Live%20Patching.pdf https://t.co/sXF0BMojyH
" 自适应地 Android 内核运行时 Patch 技术,来自百度 XLab 研究员在 HITB 会议的演讲: https://t.co/DlTyiZBkZi https://t.co/sXF0BMojyH"
-

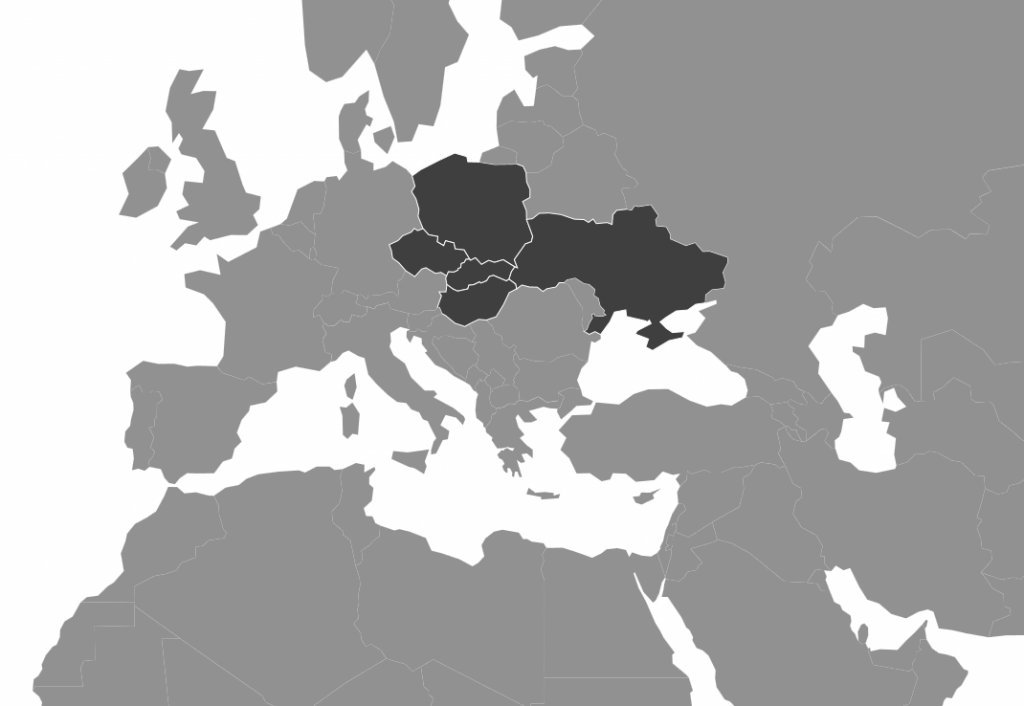
[ Android ] The Latest Android Overlay Malware Spreading via SMS Phishing in Europe https://www.fireeye.com/blog/threat-research/2016/06/latest-android-overlay-malware-spreading-in-europe.html
"RuMMS - 通过短信传播的 Android 视图覆盖恶意软件,来自 FireEye Blog: https://t.co/7Py2UfTh1C"
-

[ Attack ] Myspace database leak dump http://myspace.thecthulhu.com
"Myspace 数据库泄漏,下载地址: https://t.co/z40SzQnEqY"
-

[ Detect ] DOUBLETAKE: Fast and Precise Error Detection via Evidence-Based Dynamic Analysis http://arxiv.org/pdf/1601.07962.pdf
"DOUBLETAKE - 以线索为基础的动态分析,实现快速精确的异常检测: https://t.co/8InkBTFzNq"
-

[ Linux ] Preventing malicious attacks by diversifying Linux shell commands : http://ceur-ws.org/Vol-1525/paper-15.pdf
" 通过改变 Linux Bash Shell 的名字,对抗恶意软件,攻击者再也不知道哪个才是正确的命令︰ https://t.co/IwKQ5jQT6N"
-

[ Linux ] Since this is public now, here's the netfilter target_offset Ubuntu 16.04 local root exploit https://cyseclabs.com/exploits/target_offset_vnik.zip
" Ubuntu 16.04 netfilter target_offset 本地 Root 提权 PoC 下载: https://t.co/0t0Zz681tv"
-

[ Linux ] Paper on: Exploiting ELF `$ORIGIN` expansion in IllumOS/Solaris: http://backtrace.io/blog/blog/2016/06/29/exploiting-elf-expansion-variables/
" IllumOS 内核在加载 ELF 代码时存在 '$ORIGIN' 变量扩展的漏洞︰ https://t.co/sbwuCBJWlp"
-

[ Malware ] Espionage toolkit targeting Central and Eastern Europe uncovered: http://www.welivesecurity.com/2016/07/01/espionage-toolkit-targeting-central-eastern-europe-uncovered/ via @ ESET https://t.co/COorJm9Mb8
"SBDH toolkit - 针对欧洲和中东的间谍活动的攻击工具包: https://t.co/COorJm9Mb8 https://t.co/UmjnywIHvH"
-

[ Malware ] Cracking Locky’s New Anti-Sandbox Technique http://blog.fortinet.com/2016/06/30/cracking-locky-s-new-anti-sandbox-technique
"破解 Locky 勒索软件的沙盒对抗技术: https://t.co/FxEmI2n788"
-

[ Network ] LizardStresser IoT Botnet Part of 400Gbps DDoS Attacks https://threatpost.com/lizardstresser-iot-botnet-part-of-400gbps-ddos-attacks/119006/
"Arbor 安全团队发布报告称 400Gbps IoT DDoS 攻击的背后是 Lizard Squad 组织: https://t.co/72LGcz9qi0 "
-

[ OpenSourceProject ] A nice uptodate ptmalloc reference by @ SpamAndHex teammate GyM: https://github.com/gymgit/glibc-2.23-tmp/blob/master/slides/heap_going.pdf - very handy for CTF!
" glibc 库中的内存分配的实现︰ https://t.co/oqN65TfulI "
-

[ Others ] CDitter – CD-ROM drive based data exfiltration : https://www.anfractuosity.com/projects/cditter/ , Github : https://github.com/anfractuosity/cditter/
"CDitter — 基于 CD-ROM 驱动器的数据渗透技术︰ https://t.co/zIqGLJpFgh GitHub: https://t.co/hclitaiR87"
-

[ Others ] Phoenix Exploit Kit Remote Code Execution https://packetstormsecurity.com/files/137728/phoenix-exec.txt
" Phoenix Exploit Kit 存在一个 Web PHP 代码执行漏洞,PoC: https://t.co/qC89bJCh6P"
-

[ Others ] SIemens patched something it calls a password reconstruction vulnerability in some of its software this week - http://ow.ly/cCQl301QBtL
" 安全研究员发现了西门子输配电能源控制系统 SICAM PAS 的两个漏洞,目前其中一个已修复,来自 ThreatPost 的报道: https://t.co/wgg9A4svjI 来自 SecurityAffairs 的报道: http://securityaffairs.co/wordpress/48922/security/siemens-sicam-pas-flaws.html "
-

[ Pentest ] Shell No! Adversary Web Shell Trends and Mitigations (Part I) https://www.recordedfuture.com/web-shell-analysis-part-1/
" WebShell 的发展趋势和防护策略: https://t.co/wVqEraED5n"
-

[ Popular Software ] Jenkins Remoting RCE II – The return of the ysoserial https://www.insinuator.net/2016/07/jenkins-remoting-rce-ii-the-return-of-the-ysoserial/
" Jenkins Remoting RCE II – The return of the ysoserial: https://t.co/a6oQQtYBNU"
-

[ Tools ] My good friend @ GaborSzappanos did this awesome write up on Office exploit generators, https://www.sophos.com/en-us/medialibrary/PDFs/technical%20papers/sophos-office-exploit-generators-szappanos.pdf [link to PDF]
" Sophos 团队对主流 Office Exploit 生成器的研究: https://t.co/H6a4pCQdcY "
-

[ Web Security ] My #AppSecEu slides for "From Facepalm to Brain Bender: Exploring Client-Side XSS" are available at https://ben-stock.de/wp-content/uploads/2016/06/owasp2016.pdf
" Ben Stock 在 AppSec 会议关于客户端 XSS 的演讲: https://t.co/dlUddvhZaC"
-

[ Web Security ] Slides of "Making CSP great again!" presented at #AppSecEU: https://speakerdeck.com/mikispag/making-csp-great-again-michele-spagnuolo-and-lukas-weichselbaum - introducing #strictdynamic and a new way of doing CSP.
" Making CSP great again,来自 AppSecEU 会议: https://t.co/4HbwhVqVEK "
-

[ Web Security ] Magento – Account Hijacking Vulnerabilities : http://netanelrub.in/2016/07/01/magento-re-installation-account-hijacking-vulnerabilities/
"Magento 电商系统重安装与帐户劫持漏洞︰ https://t.co/vACklzt3gN"
-

[ Windows ] SLIDES: From zero to SYSTEM on full disk encrypted windows system #MS16-072 #MS16-014 http://www.slideshare.net/NabeelAhmed7/from-zero-to-system-on-full-disk-encrypted-windows-system @ hackinparis @ tgilis
"在全磁盘加密的 Windows 系统中实现从零到 SYSTEM: https://t.co/A94AQxBJv3 "
-

[ Windows ] Project Zero blog: "A year of Windows kernel font fuzzing #2: the techniques" by @ j00ru - https://goo.gl/QXfhSK
" Windows 内核字体 Fuzz 这一年的技术总结,来自 Project Zero Blog: https://t.co/8v3ZXTBkHd"