腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

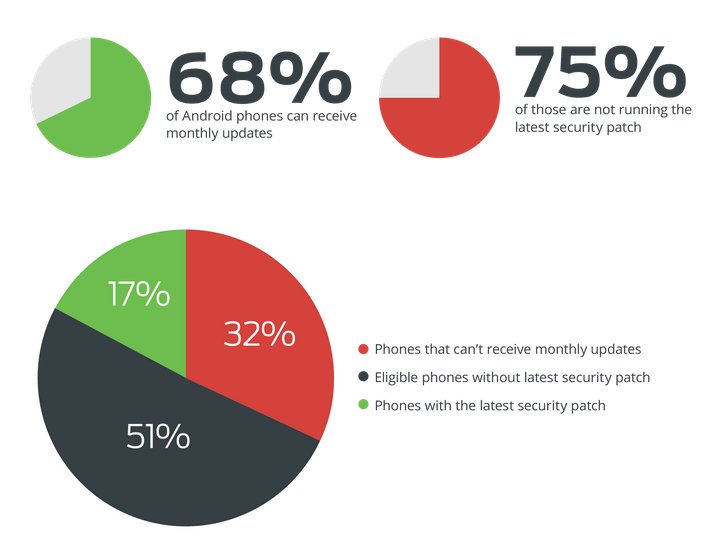
[ Android ] Huawei Is the Best OEM at Applying Android Security Updates http://twib.in/l/aAE9kRp7Rx4A https://t.co/rukU8iZP44
" Duo Security 统计数据表明,在应用 Android 安全更新的及时性方面,华为是最优秀的 OEM 厂商: https://t.co/YmtRaP7eg1 https://t.co/rukU8iZP44"
-

[ Attack ] Threat Update: Nigerian Cybercriminals Target High-Impact Industries in India via Pony https://blog.cylance.com/threat-update-nigerian-cybercriminals-target-high-impact-indian-industries-via-pony
" 尼日利亚黑客攻击印度重要行业的多个公司,来自 Cylance Blog: https://t.co/Cv7WpRQzfg"
-

[ Attack ] SecureWorks, bruteforcing bit.ly links, concludes HRC/DNC campaign seniors were spearphished https://www.secureworks.com/research/threat-group-4127-targets-hillary-clinton-presidential-campaign https://t.co/iSoDustILB
" 攻击组织 4127 发起与希拉里·克林顿竞选有关的黑客攻击行动,来自 SecureWorks Blog: https://t.co/sFPt833eTh https://t.co/iSoDustILB"
-

[ Conference ] 2016 Kcon西部 - https://drive.google.com/folderview?id=0B_thUFNIy8TdYmYyWFFqbzBua0U&usp=sharing
"2016 Kcon 西部会议的 PPT 下载: https://t.co/W83jrRnale"
-

[ Firmware ] Exploring and exploiting Lenovo firmware secrets http://blog.cr4.sh/2016/06/exploring-and-exploiting-lenovo.html
" 探索联想固件的秘密(借助一个 0Day 绕过 Flash 写保护、禁用 UEFI 安全启动、绕过 Windows 10 企业版的虚拟安全模式和密钥保护机制): https://t.co/IDzNitkPIg 作者公开的相关利用代码: https://github.com/Cr4sh/ThinkPwn "
-

[ Fuzzing ] A simple concolic execution tool for exploring the input space of a binary executable program based in Triton https://github.com/CIFASIS/nosy-newt
" Nosy Newt - 一个具体执行(Concolic Execution)工具,用于发现二进制可执行程序的输入空间,基于 Triton: https://t.co/hfJHPdN0oU "
-

[ Hardware ] Reverse Engineering Quadcopter Protocols http://hackaday.com/2016/06/28/reverse-engineering-quadcopter-protocols/
" 四轴飞行器协议逆向: https://t.co/G4MojYA8XY"
-

[ IoTDevice ] .@ _jsoo_ Found it. https://drive.google.com/file/d/0B_thUFNIy8TdVktDSlVnWkdoYzA/view?usp=sharing
" 《揭秘家用路由器0day漏洞挖掘技术》电子版下载: https://t.co/vWci1Amibv"
-

[ Linux ] Two exploitable vulnerabilities in the #linux #kernel that can lead to privilege escalation or denial of service https://twitter.com/nixcraft/status/746744760442851328
" Linux 内核在处理 setsockopt 时的两个漏洞,一个本地提权(CVE-2016-4997),一个拒绝服务(CVE-2016-4998): http://www.openwall.com/lists/oss-security/2016/06/24/5 "
-

[ Malware ] Neutrino EK: fingerprinting in a Flash https://blog.malwarebytes.com/cybercrime/exploits/2016/06/neutrino-ek-fingerprinting-in-a-flash/
" Flash 中的指纹识别,来自 MalwareBytes Blog: https://t.co/OPWSkdldrD"
-

[ Malware ] Satana ransomware – threat coming soon? https://blog.malwarebytes.com/threat-analysis/2016/06/satana-ransomware/
" Satana - 目前还处于 '开发中' 状态的勒索软件,来自 MalwareBytes Blog: https://t.co/4EaBugp2pK"
-

[ Network ] WireGuard : Next generation fast,modern,secure in-kernel modern VPN (alt. to IPSec & OpenVPN) : https://www.wireguard.io/
"WireGuard - 下一代高速、安全的内核态 VPN 实现︰ https://t.co/xKYmVRf4Ho"
-

[ OpenSourceProject ] new post - Apache Xerces XML parser Use-After-Free (fix pending) - https://marcograss.github.io/security/2016/06/29/xerces-xml-uaf.html kudos to Gustavo Grieco who found it first!
" Apache Xerces-C++ XML 解析库的 UAF 漏洞: https://t.co/CzxVo0AiGc "
-

[ OpenSourceProject ] All Github repos (commits and code, 3TB, 145M commits, 162M files) are now queryable using BigQuery in seconds: https://github.com/blog/2201-making-open-source-data-more-available
" GitHub 官方 Blog 表示,280 万的代码库、超过 3TB 的数据集现在支持秒级搜索了: https://t.co/DEe8qsxZC9"
-

[ Others ] Blog post: “memcpy (and friends) with NULL pointers” https://www.imperialviolet.org/2016/06/26/nonnull.html
" 如果传递给 memcpy 的实参是 NULL 指针会出现什么情况: https://t.co/2vHfX8RzaU"
-

[ Others ] (Deep)Learning to Break Semantic Image CAPTCHAs : http://www.cs.columbia.edu/~polakis/papers/sivakorn_eurosp16.pdf (pdf)
" 通过深度学习对抗语义型图形验证码,来自哥伦比亚大学的 Paper︰ https://t.co/aRRSTVFWoC "
-

[ Pentest ] Want to simulate data exfil over a variety of protocols, or malware in your network? Egress-Assess can do it - https://github.com/ChrisTruncer/Egress-Assess
" Egress-Assess - 通过多种协议模拟数据渗透的一个工具: https://t.co/80PRC0DFVc"
-

[ Pentest ] Detecting DNS Data Exfiltration http://blogs.cisco.com/security/talos/detecting-dns-data-exfiltration
"检测基于 DNS 的数据渗透行为,来自 Talos Blog: https://t.co/BSCmqJkFgT"
-

[ Pentest ] Here follow my slides from the presentation "Perform effective command injection attacks like Mr.Robot" @ BSidesAth - https://www.dropbox.com/s/om4yttb6nfix2hk/BSidesAth16_Perform_Effective_Command_Injection_Attacks_Like_Mr.Robot_Final.pdf
" 像 Mr.Robot 一样的命令注入攻击,来自 BSides 会议: https://t.co/N2IKyEIer3"
-

[ Pentest ] 渗透测试中的技巧 - https://drive.google.com/file/d/0B_thUFNIy8Tdd0FWV1JCNEliaEU/view?usp=sharing
"渗透测试中的技巧 PPT 下载: https://t.co/9E8YtRKhOJ"
-

[ Popular Software ] Foxit Reader ConvertToPDF TIFF SamplesPerPixel Parsing Heap Buffer Overflow Remote Code Execution Vulnerability http://srcincite.io/advisories/src-2016-23/
"福昕阅读器 ConvertToPDF 插件堆溢出 RCE 漏洞(CVE-2016-3740),构造的 TIFF 图片如果有一个超大的 SamplesPerPixel 值就会触发堆溢出,来自 Source Incite 公告: https://t.co/DbpQHu2b9V"
-

[ Tools ] How to quickly perform fuzzing and a customized automated scan using Burp's cookie jar: http://intel.ly/291BEn2 https://t.co/2FvWPsOxyo
" 利用 Burp 的 Cookie Jar 快速高效地测试 Web 应用,来自 McAfee Blog ︰ https://t.co/8aRRgzMKuT https://t.co/2FvWPsOxyo"
-

[ Tools ] Hashcat v3.00 released, the fusion of hashcat and oclHashcat into one project. Tons of updates and improvements: https://hashcat.net/forum/thread-5559.html
"Hashcat v3.00 版本发布︰ https://t.co/Al1NgPLex3"
-

[ Tools ] This is a VERY cool library. https://www.nuget.org/packages/UnmanagedExports .NET & Unmanaged dll's Hybrid #DFIR Ever seen this? https://t.co/kX5mYFaML5
" Unmanaged Exports - DllExport for .Net,从托管代码(.NET)中导出函数给 Native 代码调用: https://t.co/2PWj7vfASR.NET "
-

[ Web Security ] The Genesis of an XSS Worm – Part II : http://brutelogic.com.br/blog/genesis-xss-worm-part-ii/ ,Part I : http://brutelogic.com.br/blog/genesis-xss-worm-part-i/ cc @ brutelogic
"XSS 蠕虫的成因 Part 2 ︰ https://t.co/oDdLskIvaX 之前推送过的 Part 1︰ https://t.co/nyMfAb06JR "
-

[ Windows ] [Blog Post] Unlock PowerShell ConstrainedLanguage Mode with InstallUtil.exe http://subt0x10.blogspot.com/2016/06/unlock-powershell-constrainedlanguage.html Feedback Welcome
" 通过 InstallUtil.exe 解锁 PowerShell 的约束语言模式: https://t.co/4oHg2ySpzF "