腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] Android Spyware Targets Security Job Seekers in Saudi Arabia https://blogs.mcafee.com/mcafee-labs/android-spyware-targets-security-job-seekers-in-saudi-arabia/
" 攻击目标为沙特阿拉伯安全岗位求职者的 Android 间谍软件,来自 McAfee Blog: https://t.co/9KxEgYhqga"
-

[ Attack ] North Korea Fingered In Swift Payments Systems Heists https://packetstormsecurity.com/news/view/26674/North-Korea-Fingered-In-Swift-Payments-Systems-Heists.html
"朝鲜被指与最近的 SWIFT 支付系统攻击事件有关: https://t.co/VcwerWM6L5"
-

[ Crypto ] If you’re looking for a comprehensive history of SSL/TLS and PKI, look no further: I built a detailed timeline https://www.feistyduck.com/ssl-tls-and-pki-timeline/
" 以时间轴的方式展示 SSL/TLS、PKI 的历史: https://t.co/6jyBJ1SKx4"
-

[ Defend ] XnR No-Execute-After-Read,Preventing Code Disclosure in Commodity Software - http://cs.unc.edu/~jjwerner/near-asiaccs.pdf code https://github.com/UNCSecLab/VMXXNR #VMM #XnR
" 这篇 Paper 中作者提出 XnR(Execute-no-Read)技术并不能有效地防御代码重用攻击,作者提出了一种新的 No-Execute-After-Read 技术解决这个问题: https://t.co/ti7jjLaNzq GitHub Repo: https://t.co/8EpIRcYDzB "
-

[ Exploit ] Writing my first shellcode - iptables -P INPUT ACCEPT : https://0day.work/writing-my-first-shellcode-iptables-p-input-accept/
" 作者写了一段 Shellcode,功能是执行 'iptables -P INPUT ACCEPT' 命令 ︰ https://t.co/9nfwtbGMZU"
-

[ IoTDevice ] Diagnosis of Embedded Devices (In Japanese) - http://io.cyberdefense.jp/entry/2016/05/09/%E7%B5%84%E8%BE%BC%E6%A9%9F%E5%99%A8%E3%81%AE%E8%A8%BA%E6%96%AD%E3%82%92%E7%B4%B9%E4%BB%8B_1/2 (Part 1) http://io.cyberdefense.jp/entry/2016/05/31/%E7%B5%84%E8%BE%BC%E6%A9%9F%E5%99%A8%E3%81%AE%E8%A8%BA%E6%96%AD%E3%82%92%E7%B4%B9%E4%BB%8B_2/2 (Part 2) Reminds me of my buddies
" 嵌入式设备分析(日文), Part 1: https://t.co/mBYd1B15yy Part 2: https://t.co/AX2rDdQhxB "
-

[ Language ] .@ gvanrossum announced (optional) static typing in #Python. #PyCon2016 #programming Slides: https://www.dropbox.com/s/efatwr0pozsargb/PyCon%20mypy%20talk%202016.pdf?dl=0 https://t.co/zinKI4l8kg
" Python 的静态类型支持,来自 PyCon 2016 会议 ︰ https://t.co/wQv2e69ITB https://t.co/zinKI4l8kg"
-

[ Linux ] Analysis of stack disclosure vulnerabilities in FreeBSD compatibility layers: http://cturt.github.io/compat-info-leaks.html
" FreeBSD 兼容层在处理 TIOCGSERIAL 命令时存在栈信息泄漏漏洞 ︰ https://t.co/JtdbqHNcyx"
-

[ Malware ] Locky Ransomware Shipping With a New Loader https://reaqta.com/2016/05/locky-ransomware-new-loader/
" Locky 勒索软件一直在发展和进化,近期又用了一个新的加载器: https://t.co/Gy1dvCpTiA"
-

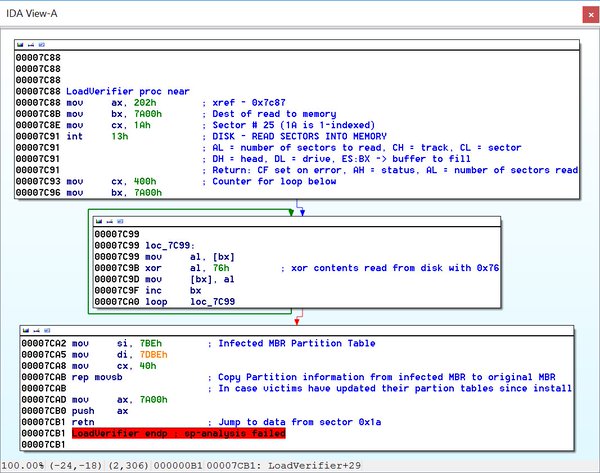
[ Malware ] An analysis of the MBR bootkit referred to as “HDRoot” : http://williamshowalter.com/a-universal-windows-bootkit/ https://t.co/0SM5h5130J
"HDRoot - Windows MBR bootkit 分析: https://t.co/dI0mldmxwI https://t.co/0SM5h5130J"
-

[ Malware ] Javascript Attachment executing a Payload http://neonprimetime.blogspot.com/2016/05/javascript-attachment-executing-payload.html
" 用 JavaScript 附件执行 Payload 的攻击邮件: https://t.co/VYZml3j3YZ"
-

[ OpenSourceProject ] Looking for XSS in PHP Source Code http://brutelogic.com.br/blog/looking-xss-php-source/
" 在 PHP 源码中找 XSS 漏洞: https://t.co/3h8HOzH1WQ "
-

[ Others ] Interesting read on Israeli surveillance vendor, 'Ability,' offering global mobile surveillance http://www.forbes.com/sites/thomasbrewster/2016/05/31/ability-unlimited-spy-system-ulin-ss7/#142723297595 by @ iblametom
" 以色列的一家尖端监控厂商表示,花 2000 万美金,他们可以监控地球上的任何一部手机,来自福布斯网站的报道: https://t.co/HjUNGO3UMq"
-

[ Others ] 这些年, 我们虐过的漏洞 - http://keenlab.tencent.com/zh/2016/05/25/CVEs-in-KeenLab/ By @ keen_lab Awesome stuff from them for last 10years.
"这些年, 我们虐过的漏洞,来自腾讯科恩实验室上周的一篇 Blog: https://t.co/jynSC4PTqJ"
-

[ Pentest ] OS X Office Macros with EmPyre http://www.harmj0y.net/blog/empyre/os-x-office-macros-with-empyre/
"用 EmPyre 攻击框架为 OS X Office 生成内嵌宏代码的文档: https://t.co/LGovODl3q9"
-

[ Pentest ] Wfuzz – Web Application Brute Forcer http://www.darknet.org.uk/2016/05/wfuzz/
"Wfuzz - Web 应用暴力破解工具: https://t.co/sXqt67C74e"
-

[ Popular Software ] [RT-SA-2016-004] Websockify: Remote Code Execution via Buffer Overflow http://goo.gl/fb/zztjtb #FullDisclosure
" Websockify 缓冲区溢出 RCE,来自 FullDisclosure 公告: https://t.co/Wj4kM93VXJ "
-

[ Popular Software ] Out-of-Box Exploitation : A Security Analysis of OEM Updaters : https://duo.com/assets/pdf/out-of-box-exploitation_oem-updaters.pdf (pdf)
" OEM 厂商的软件更新工具安全性分析,来自 Duo 团队的报告︰ https://t.co/Fw0JKgWBPA "
-

[ Tools ] w0w, Cisco just released ROPMEMU tool to analyze ROP chains! Powered by @ capstone_engine & @ unicorn_engine \O/ https://github.com/vrtadmin/ROPMEMU
" ROPMEMU - 用于分析 ROP 链的工具: https://t.co/2m2BA6XNhp 关于这个工具还有一篇 Paper: http://s3.eurecom.fr/docs/asiaccs16_graziano.pdf "
-

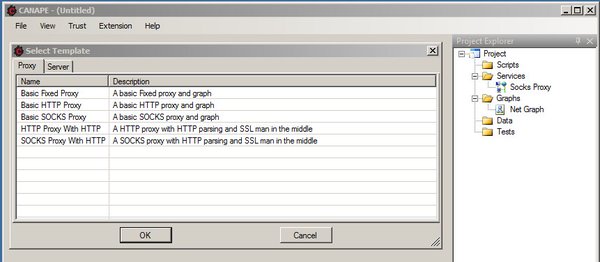
[ Tools ] Canape is a network testing tool for arbitrary protocols, specifically designed for binary http://www.contextis.com/services/research/canape/ https://t.co/yA2MJhb6d1
" Canape - 网络协议测试工具,支持任意协议,尤其是二进制协议,来自 Context 公司: https://t.co/2xsn6eMJgT https://t.co/yA2MJhb6d1"
-

[ Tools ] Knocked together some debugger detection in PowerShell - https://github.com/FuzzySecurity/PowerShell-Suite/blob/master/Detect-Debug.ps1 https://t.co/uuFJWZYKhC
" FuzzySecurity 写的 PowerShell 工具集昨天新加了一个用于检测调试器的模块: https://t.co/bI3oUzzsFN https://t.co/uuFJWZYKhC "
-

[ Tools ] I built KaliBrowser to run @ kalilinux in a @ Docker container with a full web gui. http://jerrygamblin.com/2016/05/31/kalibrowser/
" JGamblin 写了一个 KaliBrowser,为 Kali Docker 提供 Web UI 展示界面: https://t.co/dvXucoNWPy"
-

[ Tools ] Tracking Down Heap Overflows with rr https://sean.heelan.io/2016/05/31/tracking-down-heap-overflows-with-rr/ tl;dr https://github.com/mozilla/rr/wiki/Usage#reverse-execution
" 用 rr 调试器跟踪堆溢出: https://t.co/eex4dlNEYZ rr 调试器支持 record 和 replay,运行一次,多次回放调试。GitHub WiKi: https://t.co/IcgXobRrO6"
-

[ Tools ] Get all the Keystone source code, precompiled binaries for Windows & Python modules from our website at http://www.keystone-engine.org/download/
" 汇编引擎 Keystone 下载,包括源码和编译后的二进制文件: https://t.co/tu8mhZVKD7"
-

[ Web Security ] Web Storage: the lesser evil for session tokens? http://blog.portswigger.net/2016/05/web-storage-lesser-evil-for-session.html
" 都说 Web Storage 不适合存储会话 Token,作者却不这么认为,来自 PortSwigger Blog: https://t.co/OwlOyuMpVZ"
-

[ Windows ] Windows Zero Day Selling for $90,000: https://threatpost.com/windows-zero-day-selling-for-90000/118380/ via @ threatpost
" 有黑客在黑市上卖 Windows 0Day,售价 9 万美金。该 0Day 影响 Windows 2000 到 Windows 10 的所有版本,来自 ThreatPost 的报道: https://t.co/UZt8AMLKtm"
-

[ Windows ] [Blog Post] Comparing PowerShell Objects with CLIXML - http://bit.ly/1Z9eWc0
" 用 CLIXML 比较 PowerShell 对象: https://t.co/s7pmNLyAYj"