腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Secure Containers in #Android: the Samsung KNOX Case Study https://arxiv.org/pdf/1605.08567v1.pdf
" 三星 KNOX 安全容器案例研究,来自以色列特拉维夫大学: https://t.co/HaZK4X70sY"
-

[ Attack ] There is no barrier to developing malware. Even ISIS managed to produce custom malware for a targeted attack! https://citizenlab.org/2014/12/malware-attack-targeting-syrian-isis-critics/
" 针对叙利亚 ISIS 批评者的恶意软件攻击行动,来自 Citizen Lab 2014 年的一篇 Blog: https://t.co/8GfwFAVUp5 "
-

[ Browser ] Text to speech in Edge with Speech synthesis API https://blogs.windows.com/msedgedev/2016/06/01/introducing-speech-synthesis-api/
" Edge 浏览器将通过语音合成 API 支持文本到语音的转换,来自 Edge 开发者 Blog: https://t.co/I4avJ7fKs9"
-

[ Browser ] Interesting new feature in Chrome 53 https://chromium.googlesource.com/chromium/src/+/e14e5ad593f4b86b03ba71357117bf2ec1bf29c8/third_party/WebKit/LayoutTests/presentation/resources/embedded-smoke-tests.html#52 new PresentationRequest('https://example.com'); p.start()
" 从 Chrome 53 版本的代码库里看到的一个有趣的新特性: PresentationRequest() : https://t.co/OtvzRJVGFt "
-

[ Browser ] Exploiting Browser-based timing attacks : http://www.slideshare.net/phdays/ss-62583382 (Slides)
" Exploiting Browser-based Timing Attacks,来自 PHDays 会议 ︰ https://t.co/50H6GmnC3H PHDays 2016 会议的全部 Slides: http://www.slideshare.net/phdays/presentations "
-

[ Browser ] Scalable and Effective Fuzzing of Google Chrome Browser : http://www.slideshare.net/phdays/google-chrome-62582929 (Slides)
" 大规模、高效地 Fuzz Google Chrome 浏览器,来自 PHDays 会议 ︰ https://t.co/L4lASbkU8l "
-

[ Conference ] SSTIC keynote slides by spender: https://grsecurity.net/SSTIC2016.pdf
"SSTIC 2016 会议 Keynote,来自 GrSecurity ︰ https://t.co/8QYa7D5M2P"
-

[ Debug ] Very Mighty eXtension for debugging : http://www.slideshare.net/phdays/ss-62582252 (Slides)
" 基于 VMX 的调试技术,来自 PHDays 会议︰ https://t.co/PtdTkUTfzN "
-

[ Detect ] Exploiting Redundancy Properties of Malicious Infrastructure for Incident Detection : http://www.slideshare.net/phdays/exploiting-redundancy-properties-of-malicious-infrastructure-for-incident-detection (Slides)
" 攻击恶意软件基础设施的冗余特性,来自 PHDays 会议︰ https://t.co/vQOJkl60Ni "
-

[ Forensics ] New Blog Post: Expanding Skype Forensics With OSINT: IP Addresses | Automating OSINT Blog http://bit.ly/1VwiMwY #osint #dfir
" Skype 取证分析 - 提取 IP 地址和地理位置信息,在地图上展示呼叫的位置: https://t.co/YGGmtPvKDt "
-

[ Industry News ] Kaspersky Lab Assists in Russia’s Largest Cybercriminal Arrest: The Hackers Who Stole $45 Million http://www.kaspersky.com/about/news/virus/2016/The-Hackers-Who-Stole-45-Million-Dollars via @ kaspersky
" 卡巴斯基协助俄罗斯警方逮捕罪犯 - 那个盗取银行 4500 万美元的黑客: https://t.co/hzn7FNK9fL"
-

[ Malware ] Decodes, Downloads and Disguises: Three New Methods for Distributing Malware Using Windows Internal Tools. http://www.invincea.com/2016/05/decodes-downloads-and-disguises-three-new-methods-for-distributing-malware-using-windows-internal-tools/
" 解码、下载与伪装 - 利用 Windows 自带工具实现恶意软件分发的 3 个新方法,来自 Invincea Blog: https://t.co/ymQeoxE1Ko"
-

[ MalwareAnalysis ] Using Python to Decrypt Dispind.A and Helminth HTTP Beacons : https://breakpoint-labs.com/using-python-to-decrypt-dispind-a-and-helminth-http-beacons/
"用 Python 解密 Dispind.A 和 Helminth 的 HTTP 握手信息: https://t.co/g9Ad9iHFPW"
-

[ MalwareAnalysis ] Polichombr :Collaborative malware analysis framework : https://github.com/ANSSI-FR/polichombr
"Polichombr - 协同型恶意软件分析框架, GitHub Repo︰ https://t.co/0esurMm8CF"
-

[ Network ] Monitoring Reflective DDoS with Honeypots : http://www.slideshare.net/phdays/building-digita-ddosl-threat-intelligence-programs-ru-autosaved (Slides)
" 通过蜜罐监控反射式 DDoS 攻击,来自 PHDays 会议: https://t.co/y2GpAuurxR "
-

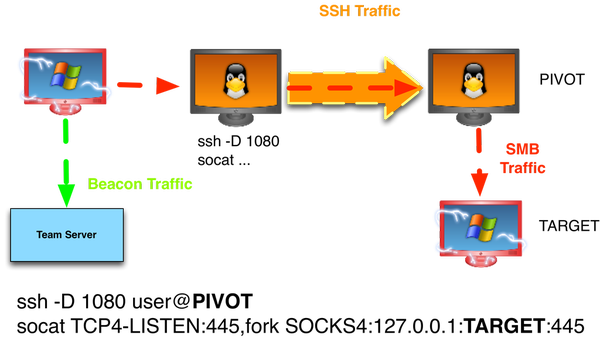
[ Network ] HOWTO: Port Forwards through a SOCKS proxy http://blog.cobaltstrike.com/2016/06/01/howto-port-forwards-through-a-socks-proxy https://t.co/lFvaIL1DuW
" 基于 SOCKS 代理的端口转发: https://t.co/mJXwOQRSKy https://t.co/lFvaIL1DuW"
-

[ NetworkDevice ] Cisco Guide to Harden IOS XR Devices http://www.cisco.com/c/en/us/about/security-center/increase-security-ios-xr-devices.html
"Cisco IOS XR 设备安全加固指南,来自 Cisco 官网: https://t.co/BZP31rX8Ws "
-

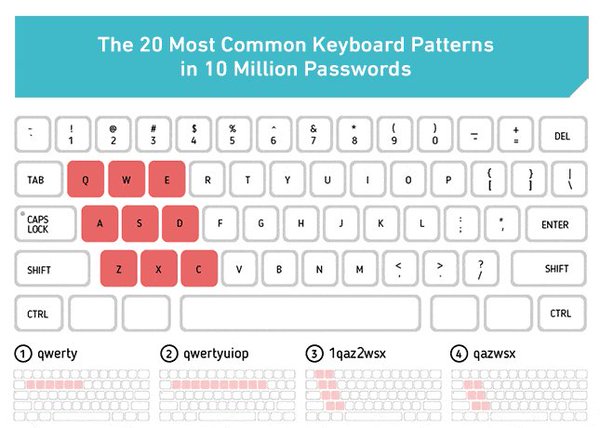
[ Others ] Analysis of 10 Million Passwords: http://wpengine.com/unmasked/?SSAID=392587 https://t.co/i93PSgH7Cq
"1000 万密码的统计分析 ︰ https://t.co/FVH9Hkyvjk https://t.co/i93PSgH7Cq"
-

[ Pentest ] Discovering Subdomains : https://blog.bugcrowd.com/discovering-subdomains
"子域名探测工具和方法,来自 BugCrowd Blog︰ https://t.co/nZb4IMHus2"
-

[ Popular Software ] Critical flaw in KeePass automatic update (over HTTP ?!?!) feature - allows MiTM and push bad updates (RCE). https://bogner.sh/2016/03/mitm-attack-against-keepass-2s-update-check/
"KeePass 自动更新存在中间人劫持漏洞(CVE-2016-5119): https://t.co/Kfw0pcNvNX KeePass 是一款流行的密码管理软件"
-

[ Popular Software ] Tcpdump crash in 4.5.1 https://www.exploit-db.com/exploits/39875/
"TCPDump 4.5.1 Crash PoC: https://t.co/oBOWFXFfZ9"
-

[ Programming ] Beyond Memory Safety With Types : https://insanitybit.github.io/2016/05/30/beyond-memory-safety-with-types
" Rust 编程语言的类型系统使用户可以安全地使用内存 ︰ https://t.co/y8V32QN2Wc"
-

[ ReverseEngineering ] Reversing C++ (Pt. 3) – Objects: The Basics : http://cybersmash.io/reversing-c-pt-3-objects-the-basics/ , Pt 2 : http://cybersmash.io/reversing-c-pt-2-switch-statement/ ,Pt 1 : http://cybersmash.io/reversing-c-pt-1-function-overloading-and-function-templates/
" C++ 逆向 Part 3 – 对象 : https://t.co/eovDEkssZo Part 2 - switch 表达式 : https://t.co/OXMVfub03D Part 1 - 函数重载和函数模板: https://t.co/MEoJnE9jVE"
-

[ Tools ] Research Spotlight: ROPMEMU – A Framework for the Analysis of Complex Code Reuse Attacks http://blogs.cisco.com/security/talos/ropmemu
" 昨天推送过 ROPMEMU,这是个用于分析 ROP 攻击的工具,昨天晚些时候 Talos Blog 写了一篇 Blog 专门介绍该工具: https://t.co/o4hr57hvdL "
-

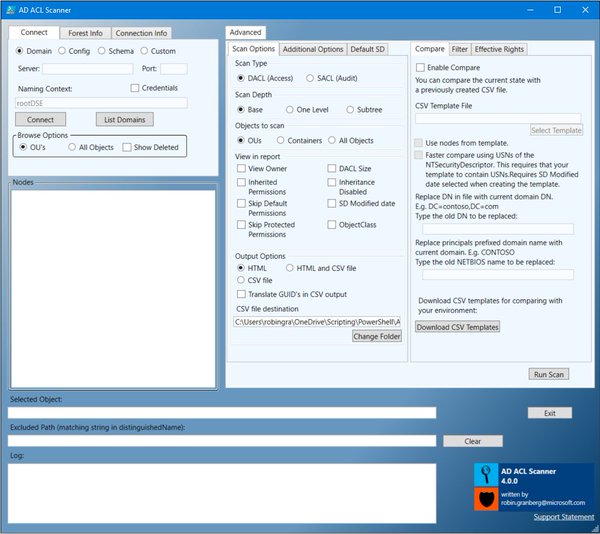
[ Tools ] AD ACL Scanner #PowerShell tool to create reports of DACLs & SACLs in AD via @ h0ng10 https://adaclscan.codeplex.com/ https://t.co/2uFsRPR6AG
" adaclscan - AD 域 ACL 扫描器,可以生成关于 DACLs 和 SACLs 的报告: https://t.co/Tg6cfrN5JP https://t.co/2uFsRPR6AG"
-

[ Tools ] gunpack - a generic tool for unpacking malware https://bitbucket.org/iwseclabs/gunpack/
"gunpack - 恶意软件通用脱壳工具: https://t.co/dsBzYvAwxy "
-

[ Virtualization ] Abusing Privileged and Unprivileged Linux Containers https://www.nccgroup.trust/us/our-research/abusing-privileged-and-unprivileged-linux-containers/
"特权级和非特权级 Linux 容器的滥用,来自 NCC Group: https://t.co/hTdkTPl7HF"
-

[ Web Security ] Joomla SecurityCheck extension - Multiple vulnerabilities http://goo.gl/fb/n9WMSk #FullDisclosure
"Joomla SecurityCheck 扩展 2.8.9 版本存在存储型 XSS 和 SQL 注入漏洞,来自 FullDisclosure 的公告: https://t.co/mHTgbjOQ81 "
-

[ Web Security ] Over a million #WordPress sites at risk due to XSS #vulnerability: http://bit.ly/280PWcZ #cybersecurity
" 超过 100 万 WordPress 网站受 Jetpack 插件 XSS 漏洞的影响,来自 TrendMicro Blog ︰ https://t.co/CYHoMfG9pA "
-

[ Web Security ] Discuz X系列门户文章功能SSRF漏洞挖掘与分析 - http://bobao.360.cn/learning/detail/2889.html by 360's 0kee team
"Discuz X 系列门户文章功能 SSRF 漏洞挖掘与分析,来自 360 0kee 团队: https://t.co/Dw8FjevLsU "
-

[ Web Security ] Taking over Heroku accounts : http://esevece.github.io/2016/06/01/taking-over-heroku-accounts.html
" 接管 Heroku 帐户 ︰ https://t.co/Zh582d3pSf"
-

[ Web Security ] Web Application Firewall Bypassing : http://www.slideshare.net/phdays/ss-62570233 (Slides)
"Web 应用防火墙绕过技术,来自 PHDays 会议︰ https://t.co/sBeLUsdYT8 "
-

[ Windows ] Relevance of Windows EventIDs in Investigation http://resources.infosecinstitute.com/relevance-of-windows-eventids-in-investigation/
"Windows EventID 在入侵调查方面的关联分析,来自 InfoSec Blog: https://t.co/25Q1CBGYiD "
-

[ Windows ] Chaining MS16-032 with Excel DDE to get macro-less command exec in a phishing payload https://sensepost.com/blog/2016/powershell-c-sharp-and-dde-the-power-within/ by @ Saif_Sherei
" 基于 C# 的 DLL 函数导入以及基于 Excel DDE 的命令执行技术: https://t.co/loEvLj7Imr "
-

[ Windows ] Spread the word…the May-June issue of The NT Insider is available: http://bit.ly/1TJHW6y https://t.co/F3POXvIUzg
"关于 NT 内核的杂志 《The NT Insider》发布 2016 5-6 月版︰ https://t.co/vr43RanIGe https://t.co/F3POXvIUzg"