腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] LG Smartphones Affected by Two Severe Vulnerabilities http://ow.ly/6Rrr300Iz9J
" 在这两天的 LayerOne 安全会议上,来自 CheckPoint 的两位研究员直接公开了他们发现的两个 LG 手机的漏洞,之前并没有通知 LG 官方: https://t.co/5qxFU76ROu"
-

[ Android ] Android 6.0 Marshmallow permission-granting model is under attack http://securityaffairs.co/wordpress/47865/malware/android-marshmallow.html
" 多个恶意软件作者盯上了 Android 6.0 版本的权限授予模型: https://t.co/WKIEJhXApt "
-

[ Android ] Interacting with Samsung radio layer from unprivileged applications http://roberto.greyhats.it/2016/05/samsung-access-rild.html (“stealth call” video: https://twitter.com/rpaleari/status/701780929791008768)
" 非特权 APP 滥用一个未公开漏洞,直接与 Radio 层交互,悄悄地拨打电话: https://t.co/6TzariA5MK https://t.co/JeaDlWTn6M "
-

[ Android ] A reference guide that shows private notes of @ doriancussen about Android Security: https://github.com/doridori/Android-Security-Reference
" Android 安全概览手册,来自作者 doridori 的个人总结和资料收集 ︰ https://t.co/CE32XOxXH3"
-

[ Attack ] Hackers Stole 68 Million Passwords From Tumblr, New Analysis Reveals https://motherboard.vice.com/read/hackers-stole-68-million-passwords-from-tumblr-new-analysis-reveals
"黑客从 Tumblr 窃取 6800 万用户密码: https://t.co/LkxB9YwzH7"
-

[ Attack ] Awesome report published by @ citizenlab on Stealth Falcon. Infra indicators are available inside of @ PassiveTotal. https://citizenlab.org/2016/05/stealth-falcon/
" 暗处的猎鹰(Stealth Falcon) - 针对阿联酋异见者的间谍攻击行动,来自 CitizenLab: https://t.co/2faOtfirRU"
-

[ Browser ] A fun old MSc thesis (ca. 2009) that deals with heap corruptions, SpiderMonkey v1.7, infoleak construction etc.: https://drive.google.com/file/d/0B5hBKwgSgYFaalNIYVc3OXdrQW8/view?usp=sharing
" Web 2.0 时代,经典的浏览器内存破坏类漏洞攻击,来自一篇 2009 年的 Paper,其中有对 Mozilla SpiderMonkey 引擎的分析︰ https://t.co/FYvV1WgyXb "
-

[ Browser ] Microsoft Internet Explorer 8 Divide By Zero Proof Of Concept https://packetstormsecurity.com/files/137217/ie8xpsp3-divide-crash-poc.zip
" IE8 浏览器的一个除零漏洞 PoC: https://t.co/9YiAbR6jUx"
-

[ Crypto ] How to Generate Secure Random Numbers (in Various Programming Languages) https://paragonie.com/blog/2016/05/how-generate-secure-random-numbers-in-various-programming-languages
" 在不同编程语言中,如何安全地生成随机数: https://t.co/ZjibPZBSzj"
-

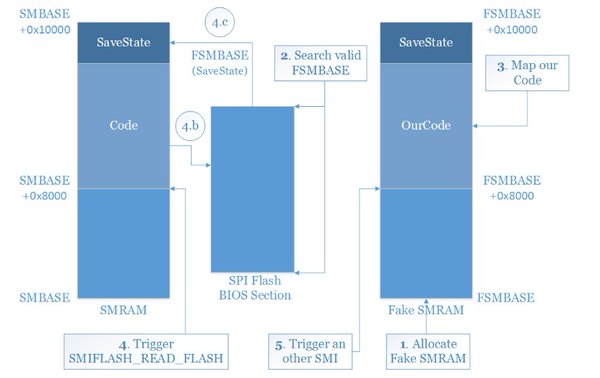
[ Firmware ] SMM unchecked pointer vulnerability : http://esec-lab.sogeti.com/posts/2016/05/30/smm-unchecked-pointer-vulnerability.html cc @ BrunoPujos https://t.co/7C44kChzQg
"SMM 未检查指针漏洞的利用,来自 Sogeti ESEC Lab Blog ︰ https://t.co/kXYPmX5857 https://t.co/7C44kChzQg"
-

[ IoTDevice ] Hacking an IP camera (Grandstream GXV3611_HD) : http://boredhackerblog.blogspot.in/2016/05/hacking-ip-camera-grandstream-gxv3611hd.html (No cache for URL,for few URL may not work) https://t.co/4HJ25d3s9z
"Hacking an IP camera (Grandstream GXV3611_HD): https://t.co/XmAswfnS4p https://t.co/4HJ25d3s9z"
-

[ Obfuscation ] Protecting Software through Obfuscation: Can It Keep Pace with Progress in Code Analysis? http://www.cs.rhul.ac.uk/home/kinder/papers/csur16-obfuscation.pdf
" 通过混淆的方式保护软件 - 这种方法能够跟上代码分析发展的步伐吗: https://t.co/DRxtN0LBen"
-

[ Others ] Process Hollowing http://marcoramilli.blogspot.com/2016/05/process-hollowing.html
" Process Hollowing - 恶意软件常常利用这种技术在进程创建的早期将其替换为自身: https://t.co/6jCp8erZsE"
-

[ Others ] Environmental Systems Corporation (ESC) 8832 Data Controller, remotely exploitable, no patch/update -mitigate only: https://ics-cert.us-cert.gov/advisories/ICSA-16-147-01
"环境系统公司 (ESC) 8832 数据控制器存在漏洞,可以远程攻击,暂时无补丁更新,来自 ICS-CERT ︰ https://t.co/l7OK260ttQ"
-

[ Others ] TCP Timing Attacks: Practical Web App attacks using "Nanown" presented at back hat ~ https://www.blackhat.com/docs/us-15/materials/us-15-Morgan-Web-Timing-Attacks-Made-Practical.pdf&ved=0ahUKEwiCsp7GvYDNAhUGSlIKHTwYByoQFggdMAE&usg=AFQjCNHfJ5yap96vOANXx3y6vmjFWOXjNg&sig2=Gd_eiqnFG-Vou0cz_675Ow https://github.com/ecbftw/nanown
" Web Timing Attack 实战(基于工具 Nanown),来自 BlackHat USA 2015 会议的一篇演讲: https://t.co/KdEcoXvDT5 https://t.co/Pdt6tFllfi"
-

[ Others ] Wired Mobile Charging – Is it Safe? https://securelist.com/blog/mobile/74804/wired-mobile-charging-is-it-safe/ via @ Securelist
" 手机 USB 有线充电安全不安全(隐私泄露、远程控制): https://t.co/K3xcICX3QG"
-

[ Others ] Hijacking Bitcoin: Large-scale Network Attacks on Crypto-currencies ~ Maria Apostolaki ~ http://arxiv.org/abs/1605.07524
"劫持比特币 - 针对加密货币的大规模网络攻击, Paper: https://t.co/Zq1W8ruAhT"
-

[ Popular Software ] The 0day by niubl of Knownsec 404 Security Team has been killed http://blog.knownsec.com/2016/05/imagemagick-popen-remote-command-execution-vulnerability/
" 昨天推送过,ImageMagick 在处理文件名时如果遇到管道符,部分文件名会被当作命令执行。知道创宇的研究员也发现了这个漏洞,他们对该漏洞的分析: https://t.co/V3US6R7uYQ"
-

[ Popular Software ] Boot & Crypto Analysis of Sophos SafeGuard Enterprise https://www.logicista.com/2016/sophosboot
" Sophos SafeGuard 企业版磁盘加密产品的启动过程分析,来自 Logicista Blog: https://t.co/oZxE7iZgu5"
-

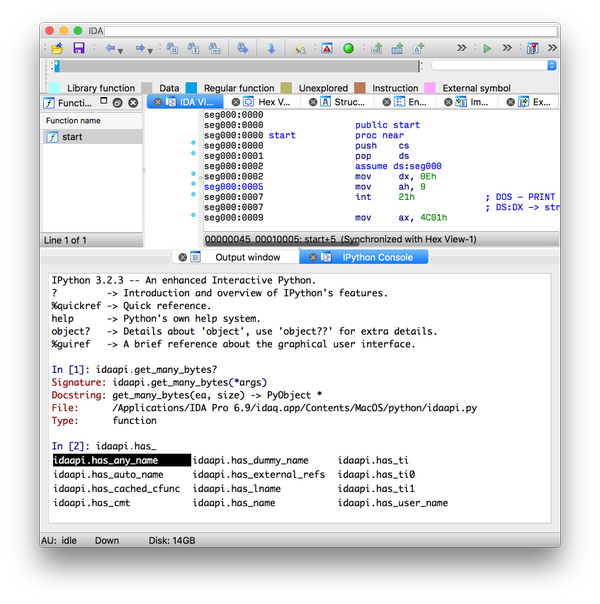
[ ReverseEngineering ] Good morning. I've fixed the IDA Pro console for everyone. Have a look: https://github.com/eset/ipyida https://t.co/Y7snSUQyG4
" 在 IDA Pro 上下文环境使用 IPython Console︰ https://t.co/wHtrETqESS https://t.co/Y7snSUQyG4"
-

[ Tools ] Email Reconnaissance and Phishing Template Generation Made Simple http://cybersyndicates.com/2016/05/email-reconnaissance-phishing-template-generation-made-simple/
" 钓鱼邮件生成器模板工具: https://t.co/BMssY8kgNb"
-

[ Web Security ] wpDiscuz Supercharged native comments 3.1.4 Reflected #XSS http://security.szurek.pl/wpdiscuz-supercharged-native-comments-314-reflected-xss.html #WordPress
" WordPress wpDiscuz 插件 3.1.4 版本反射式 XSS 漏洞: https://t.co/t8Uy9eIMIy "
-

[ Windows ] Duqu 2.0 kernel exploitation technique analysis (part 1 of 2) - https://blogs.technet.microsoft.com/mmpc/2016/05/29/%E2%80%8Bduqu-2-0-kernel-exploitation-technique-analysis-part-1-of-2-2/
"Duqu 2.0 内核漏洞利用技术分析,这篇 Blog 发布之后不久就被微软删除了: https://t.co/Yq8buFWy3L 好在 Google 已经缓存下来了: https://webcache.googleusercontent.com/search?q=cache:g0ulRtD1Wf0J:https://blogs.technet.microsoft.com/mmpc/2016/05/29/%25E2%2580%258Bduqu-2-0-kernel-exploitation-technique-analysis-part-1-of-2-3/+&cd=1&hl=zh-CN&ct=clnk&gl=cn "