腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] 百脑虫之HOOK技术分析 - http://blogs.360.cn/360mobile/2016/04/25/analysis_of_bainaochong_hook/ by 360 Mobile Security Team
"百脑虫之 HOOK 技术分析, 来自 360 移动安全团队: https://t.co/IYFnhH1qtC "
-

[ Android ] RuMMS: The Latest Family of Android Malware Attacking Users in Russia Via SMS Phishing https://www.fireeye.com/blog/threat-research/2016/04/rumms-android-malware.html
"RuMMS - 通过短信钓鱼攻击俄罗斯用户的 Android 恶意软件: https://t.co/jboVYJNhFG"
-

[ Attack ] Massive security breach at German Nuclear power plant ~ http://www.express.co.uk/news/world/664868/German-nuclear-plant-security-breach-fears-cyber-hackers-gain-access-atomic-site
"德国核电站的计算机中发现了大量的病毒, 这些病毒可以让攻击者控制移动放射性燃料棒的设备: https://t.co/DkMj8RFWiQ"
-

[ Attack ] 冒充最高检网络电信诈骗之追溯 - http://bobao.360.cn/learning/detail/2851.html
"冒充最高检网络电信诈骗之追溯 - https://t.co/99wmcVYM3G"
-

[ Attack ] Oh man: vulnerability in huge dark web marketplace leaves private messages exposed; containing orders, addresses etc https://motherboard.vice.com/read/vulnerability-in-huge-dark-web-marketplace-exposes-private-messages-alphabay-reddit
"AlphaBay,当前最大的黑市,本周被爆出其 API 中存在 Bug,可以泄露订单和地址信息: https://t.co/jco0GwBbBo"
-

[ Attack ] Repackaging Open Source #BeEF Browser Exploitation Framework for #APT campaigns https://securelist.com/blog/software/74503/freezer-paper-around-free-meat/
"伊朗的一家网站被攻击者嵌入了 BeEF(浏览器漏洞利用框架): https://t.co/lxtShWXTDx "
-

[ Backdoor ] #Tuto4PC #scareware backdoors millions of computers-@ Cisco Talos report: https://threatpost.com/tuto4pc-utilities-silently-install-12m-backdoors-cisco/117704/ via @ threatpost
"Tuto4PC 公司的软件给 1200 万用户静默安装后门, 来自 ThreatPost 的报道: https://t.co/XkQvk6iGeJ 来自 Talos 的分析报告: http://blog.talosintel.com/2016/04/the-wizzards-of-adware.html "
-

[ Browser ] Debug Microsoft Edge from VS Code with the new Edge Diagnostics Adapter. https://blogs.windows.com/msedgedev/2016/04/27/introducing-edge-diagnostics-adapter/ https://t.co/rMV43Tp5mh
"基于 Edge 的诊断适配器, 用 VS Code 或 Sublime Text 调试 Edge 浏览器: https://t.co/NLecZ7wKIO https://t.co/rMV43Tp5mh"
-

[ Browser ] CVE-2016-1779 技术分析及其背后的故事 - http://xlab.tencent.com/cn/2016/04/19/CVE-2016-1779/ by @ XuanwuLab
"CVE-2016-1779 技术分析及其背后的故事, 来自玄武实验室 xisigr: https://t.co/Wdo7pRkrxx "
-

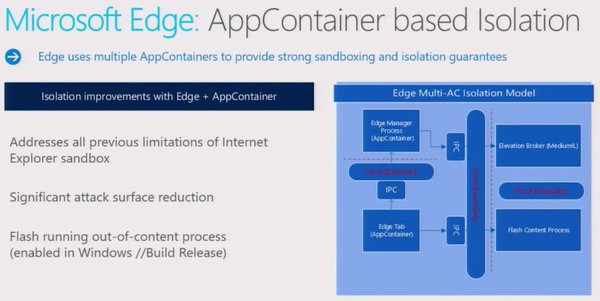
[ Browser ] Insight into security mechanisms within the MSFT Edge Browser. Worth a watch! http://bit.ly/1qM5kbO #DFIR https://t.co/657cRY2NkN
"《The Cutting Edge of Browser Security》, 视频, 介绍微软在 Edge 浏览器的安全性方面做出过哪些努力: https://t.co/hiHAza9Rc1 https://t.co/657cRY2NkN"
-

[ Browser ] Firefox 46 Patches Critical Memory Vulnerabilities: https://threatpost.com/firefox-46-patches-critical-memory-vulnerabilities/117698/ via @ threatpost
"Firefox 浏览器更新 46 版本, 本次更新共修复了 10 个漏洞, 其中一个为严重级别: https://t.co/JI1j4AfVTN"
-

[ Browser ] Extracting page contents with CSS injection via OTF+SVG & XEE https://gist.github.com/cure53/1501bcb6aa6608b2af38fcafd68af219
" 通过 CSS 注入提取页面内容(基于 OTF+SVG & XEE), GitHub Repo: https://t.co/aviTd5cQeR"
-

[ Browser ] Firefox release 46.0 gets enabled W^X for JIT-code: https://www.mozilla.org/en-US/firefox/46.0/releasenotes/, http://jandemooij.nl/blog/2015/12/29/wx-jit-code-enabled-in-firefox/
"Firefox 46.0 版本开始启用 JIT 代码可写、可执行互斥机制, 更新日志︰ https://t.co/qkc1YwxBjs https://t.co/DVwJ9NE8ft"
-

[ Detect ] Passive DNS for Threat Hunting on the network https://www.endgame.com/blog/hunting-cheap-part-1-architecture
"低成本的威胁检测 Part 1:基于被动 DNS 的威胁检测架构: https://t.co/UieAM8s1rF"
-

[ Linux ] Linux KASLR memory randomization moving to PATCH stage http://comments.gmane.org/gmane.linux.kernel/2206880
"Linux 内核 KASLR 内存随机化进入 Patch 阶段: https://t.co/SdmzHU4ULE"
-

[ Mac OS X ] SyScan360 Singapore 2016 slides and exploit code https://reverse.put.as/2016/04/27/syscan360-singapore-2016-slides-and-exploit-code/
" Pedro Vilaça 在 SyScan360 上的演讲《Memory corruption is for wussies》: https://t.co/Mds2I5Sjm3 之前推送过 Slides, 这次作者放出了 CVE-2016-1757 的利用代码: https://github.com/gdbinit/mach_race "
-

[ Malware ] Malware Takes Advantage of Windows ‘God Mode’ https://blogs.mcafee.com/mcafee-labs/malware-takes-advantage-of-windows-god-mode/
"从 Vista 版本开始, Windows 就有一个彩蛋,允许创建一个特殊命名的文件夹,这个文件夹会作为指向【控制面板】、【我的电脑】的快捷方式。 McAfee 最近捕获的恶意样本就利用了这个特性: https://t.co/O0rL3siD2v"
-

[ Malware ] New #malware variant combines high-level obfuscation techniques & several layers of evasion http://intel.ly/1pDLnD7 https://t.co/mdgVVdZ0UX
"新的宏病毒变种采用高级混淆技术逃逸检测, 来自 McAfee Blog: https://t.co/ObsbMC7Off https://t.co/mdgVVdZ0UX "
-

[ Mitigation ] AMD Memory Encryption- http://amd-dev.wpengine.netdna-cdn.com/wordpress/media/2013/12/AMD_Memory_Encryption_Whitepaper_v7-Public.pdf #SEV #SME
"AMD 内存加密技术, 来自 2013 年的一篇 Paper: https://t.co/gb0xzHQCMv "
-

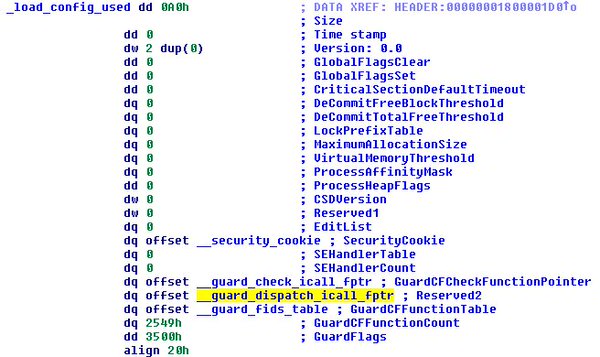
[ Mitigation ] Changes in CFG: 'Reserved2' field of LOAD_CONFIG_DIRECTORY now points to new func ntdll!LdrpDispatchUserCallTarget https://t.co/0y6PKLfNue
"CFG 的新变化︰ LOAD_CONFIG_DIRECTORY 结构体的 'Reserved2' 域指向了一个新函数: ntdll !LdrpDispatchUserCallTarget https://t.co/0y6PKLfNue"
-

[ OpenSourceProject ] Re: CVE Request: Out-of-bands write issue found in qemu: +-- On Wed, 27 Apr 2016, 李强 wrote --+ | The qemu has... http://bit.ly/235peL7
"Qemu uart_write() 内存越界写: https://t.co/gr89Epr7IZ"
-

[ OpenSourceProject ] Vulnerability Spotlight: Further NTPD Vulnerabilities http://feedproxy.google.com/~r/Vrt/~3/YoDCJSvJV-Y/vulnerability-spotlight-further-ntpd_27.html
"Cisco 在 NTPD 中发现了 6 个漏洞: http://blog.talosintel.com/2016/04/vulnerability-spotlight-further-ntpd_27.html "
-

[ Others ] Some Java Deserialization Security FAQ - https://christian-schneider.net/JavaDeserializationSecurityFAQ.html#main to answer dev questions about #JavaDeser - feedback welcome
"关于 Java 反序列化问题的 FAQ: https://t.co/lxEm5caoEv "
-

[ Others ] vulny : Vulnerable Linux socket game for educational purposes : https://github.com/vix597/vulny
"vulny - 以教学为目的、存在漏洞的 Linux socket 游戏 ︰ https://t.co/DF9VBxzDDi"
-

[ Others ] 7 million unsalted MD5 passwords leaked by Minecraft community Lifeboat http://arstechnica.com/security/2016/04/minecraft-community-lifeboat-fails-remedial-password-security/
"700 万的 Lifeboat(救生艇) 游戏玩家账户密码泄露, 泄露的密码是没有加 Salt 的 MD5 Hash: https://t.co/RBCNe3sTUj"
-

[ Pentest ] 书安第七期 - http://down.jdsec.com/secbook-7/%E4%B9%A6%E5%AE%89-%E7%AC%AC%E4%B8%83%E6%9C%9F.pdf
"书安第七期 - https://t.co/06ETPovlGg"
-

[ Pentest ] 书安第六期 - http://down.jdsec.com/secbook-6/%E7%AC%AC%E5%85%AD%E6%9C%9F.pdf
"书安第六期 - https://t.co/fTpu1cPFgA"
-

[ Pentest ] IntruderPayloads : A collection of Burpsuite Intruder payloads : https://github.com/1N3/IntruderPayloads
"IntruderPayloads - 渗透和 Fuzz 中使用的 Burpsuite Payloads 收集︰ https://t.co/DlnquV2i8a"
-

[ Pentest ] Faster Blind MySQL Injection Using Bit Shifting : https://www.exploit-db.com/papers/17073/
" 利用移位实现更快的 MySQL 盲注, 来自 Exploit DB ︰ https://t.co/aOgqxYdTxO"
-

[ Pentest ] Did you know we have official OSX installers for the open source Metasploit Framework? https://github.com/rapid7/metasploit-framework/wiki/Nightly-Installers
" Metasploit 框架在各系统中的安装包工具: https://t.co/becWTGNbLc"
-

[ Tools ] Mosh : the mobile shell (SSH replacement) : https://mosh.mit.edu/ (For Android,Mac OS X,FreeBSD,GNU/Linux) ,PDF : https://mosh.mit.edu/mosh-paper.pdf
"Mosh - 手机版的 Shell(用于替代 SSH)︰ https://t.co/LKCNeR97T7 该工具为手机定制,支持网络间断性连接、支持智能本地 echo,支持 Android、Mac OS X、Linux 等, Paper: https://t.co/AlDWYddXQk"
-

[ Tools ] PowerShell for Docker Available for Early Testing http://windowsitpro.com/powershell/powershell-docker-available-early-testing
"PowerShell for Docker - 微软开源的 Docker 引擎的 PowerShell 模块,作为 Docker 客户端的替代品: https://t.co/suPCyAfeeb GitHub Repo: https://github.com/Microsoft/Docker-PowerShell "
-

[ Web Security ] Binary Webshell Through OPcache in PHP 7 http://blog.gosecure.ca/2016/04/27/binary-webshell-through-opcache-in-php-7/
"基于 PHP 7 OPcache 的二进制格式 Webshell: https://t.co/22Onmtt2A9 "
-

[ Web Security ] Office 365 authentication bypass disclosure and write-up: http://www.economyofmechanism.com/office365-authbypass.html #SAML https://t.co/mckGzrqBev
"Office 365 身份验证绕过漏洞披露, 来自 Blog 《通往地狱的路铺满了 SAML 断言》︰ https://t.co/8v39qznmyu https://t.co/mckGzrqBev"
-

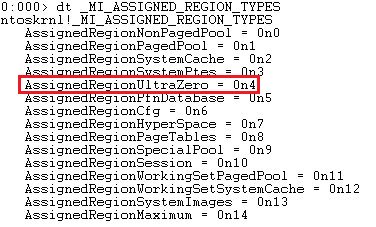
[ Windows ] MiAssignTopLevelRanges brings full KASLR to Windows 10, at last. ULTRAZERO. https://t.co/3hNCidVEws
"MiAssignTopLevelRanges 使 Windows 10 内核完全地随机化: https://t.co/3hNCidVEws"
-

[ Windows ] CVE-2016-0018: DLL Planting Leads to a Remote Code Execution Vulnerability https://blogs.mcafee.com/mcafee-labs/cve-2016-0018-dll-planting-leads-to-a-remote-code-execution-vulnerability/
"CVE-2016-0018: DLL 劫持导致的远程代码执行漏洞, 来自 McAfee Blog: https://t.co/SLAvvmz6Kr"
-

[ Windows ] [Experimenting] JavaScript - Generate and Enroll Certificate Chain - COM+ Scriptlets https://gist.github.com/subTee/9b90e64808b477b2b92a37dbfad9d898
" 用 JavaScript 实现证书的生成和注册, 来自 Casey Smith 的 GitHub Repo: https://t.co/i0flYGKJbm "
-

[ Windows ] Windows Server 2016 Technical Preview 5 - with Shielded VM's and Host Guardian Service - https://www.microsoft.com/en-us/evalcenter/evaluate-windows-server-technical-preview interesting
"Windows Server 2016 Technical Preview 5 下载: https://t.co/h0TPhKWBGl "
-

[ Windows ] NCC Group Blog: Adventures in Windows Driver Development: Part 1 - https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2016/april/adventures-in-windows-driver-development-part-1/
"Windows 驱动程序开发中遇到的一些小问题 Part 1, 来自 NCC Group Blog: https://t.co/WNZSxHXXLZ"
-

[ Windows ] Windows RS1 14332, no changes in UAC except redesigned window (in 14328). Would be interesting to see if sysprep will be fixed before rtm.
"Windows RS1 14332 版本的 UAC 除了重新设计的一个新窗口外,没什么变化"
-

[ Windows ] Redstone Build 14332 now adds MiRebaseDynamicRelocationRegions, and fully dynamic PTE/PDE/PXE base, with a call to SecureKernel/VSM.
"Windows 10 Build 14332 增加了一个 API MiRebaseDynamicRelocationRegions, PTE/PDE/PXE 的基址完全随机化"