腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] . @ IBM analyzes market for #Android malware, in particular overlay malware which steal credentials. https://threatpost.com/scourge-of-android-overlay-malware-on-rise/117720/
"地下市场上 Android 恶意攻击者之间的竞争越来越激烈, 来自 ThreatPost 的报道: https://t.co/AShtt8ufRx"
-

[ Attack ] Qatar National Bank 1.5 Gb archive leaked online http://securityaffairs.co/wordpress/46764/data-breach/qatar-national-bank-data-leak.html
"卡塔尔国家银行 1.5 GB 文档泄露: https://t.co/mEzM35Ob5S"
-

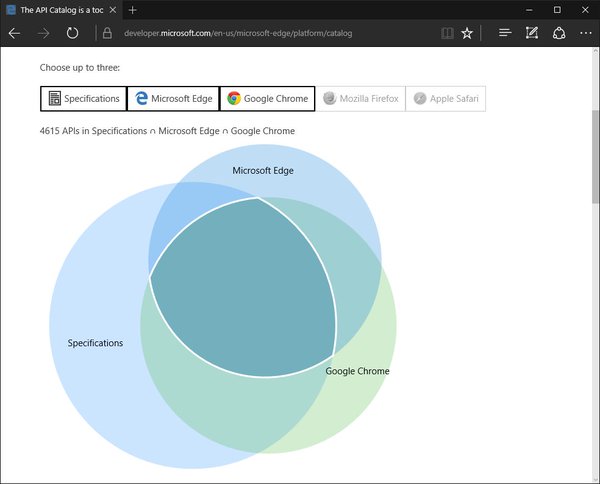
[ Browser ] Compare browser type systems with the new API Catalog tool https://blogs.windows.com/msedgedev/2016/04/28/introducing-api-catalog/ https://t.co/TV9xCtz0UL
"微软推出了一个称为 'API Catalog' 的工具,该工具可以在多个浏览器之间比较 API 支持的差异性,也可以和规格文档比较: https://t.co/wOmonDVr9k https://t.co/TV9xCtz0UL"
-

[ Defend ] Defend against @ subTee's AppLocker Bypass technique using EMET's ASR https://github.com/iadgov/Secure-Host-Baseline/tree/master/EMET#blocking-the-regsvr32-application-whitelisting-bypass-technique … #squiblydoo
" 用 EMET ASR 防御技术检测 subTee 的 AppLocker Bypass: https://t.co/Bufu7ttkiX 来自 GitHub Repo : https://github.com/iadgov/Secure-Host-Baseline 该项目用于实现 Windows 10 自动化部署"
-

[ Exploit ] Hidden Bind Shell : Keep your shellcode hidden from scans : http://www.shelliscoming.com/2014/03/hidden-bind-shell-keep-your-shellcode.html , Demo : https://www.youtube.com/watch?v=xYBuaVNQjGA
"如何隐藏你的 Bind Shell - 在 Shellcode 中对 Socket 连接请求直接回复 RST : https://t.co/qIgfXxNde6 Youtube Demo : https://t.co/h1WXc7DR9M"
-

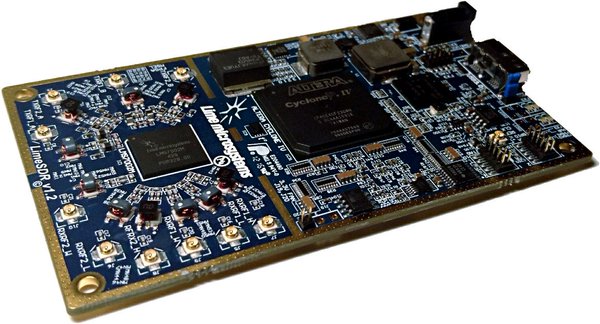
[ Hardware ] LimeSDR is now open source hardware! https://myriadrf.org/blog/limesdr-now-open-source-hardware/ #OSHW #FOSS #OpenSource #SDR https://t.co/8qJBx2i8R3
"LimeSDR 开源了, LimeSDR 是一个低成本的 SDR 硬件实现: https://t.co/pC5XG40dnr GitHub Repo: https://github.com/myriadrf/LimeSDR-USB "
-

[ iOS ] Riskware "ImgNaix" repackaged into Wechat, abused private API and affected non-jailbroken iOS device: http://drops.wooyun.org/mobile/15406 by @ SparkZheng
" 微信双开还是微信定时炸弹?- 关于非越狱iOS上微信分身高危插件ImgNaix的分析, 来自 Wooyun Drops: https://t.co/YgzekaUfGw"
-

[ Malware ] TeslaCrypt 4.2 Released with quite a few Modifications http://ow.ly/4nbvpM
" TeslaCrypt 勒索软件 4.2 版本的一些变化: https://t.co/oGUtTVudlb "
-

[ Malware ] #Afraidgate: Major Exploit Kit campaign swaps #Locky ransomware for #CryptXXX http://bit.ly/21hQqqE #Unit42
"Afraidgate 攻击行动开始用 Nuclear EK 安装 Locky 勒索软件, 最近已经切换为用 Angler EK 安装 CryptXXX 了。 来自 Palo Alto 的分析: https://t.co/FuQkEylGzn "
-

[ Others ] PHP 7.x Heap Overflow https://packetstormsecurity.com/files/136843/php7-overflow.txt
"PHP 7.x 版本在读取 zip 文件时存在整数溢出导致的堆溢出漏洞,影响 7.0.6 之前版本: https://t.co/4li2JorMA2"
-

[ Others ] Flaw allowed anyone to modify & take control over ANY .as domain https://isecguy.wordpress.com/2016/04/25/flaw-allowed-anyone-to-modify-take-control-over-any-as-domain/
"美国 .as 域域名注册商(nic.as) 存在漏洞,攻击者可以篡改并控制任何的 .as 域名: https://t.co/iGWyTvtjAi"
-

[ Others ] New Paper. How It Works: Steganography Hides Malware in Image Files https://www.virusbulletin.com/virusbulletin/2016/04/how-it-works-steganography-hides-malware-image-files/ https://t.co/Aev6TcQjzU
" 恶意软件图片文件中的隐写是如何实现的, 来自 VirusBulletin Blog: https://t.co/q6NL3zWoos https://t.co/Aev6TcQjzU"
-

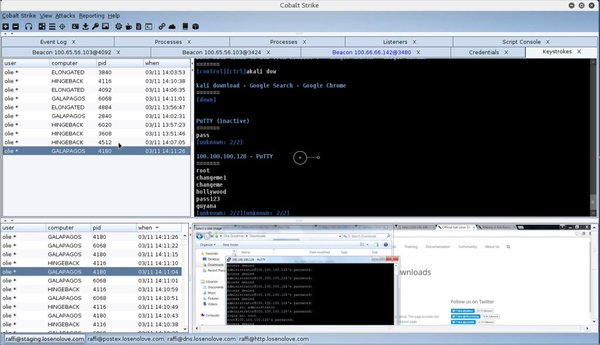
[ Pentest ] User Exploitation at Scale http://blog.cobaltstrike.com/2016/04/28/user-exploitation-at-scale https://t.co/68AzKuEyYh
"Cobalt Strike 3.0 版本支持批量用户的管理: https://t.co/jTkVihhobU https://t.co/68AzKuEyYh"
-

[ Programming ] AMD64 Architecture Programmer’s Manual (Vol - II : System Programming) : http://support.amd.com/TechDocs/24593.pdf (pdf)
"AMD64 架构编程手册 第二卷:系统编程: https://t.co/KtKLtYtZok "
-

[ Sandbox ] detux : Analyze linux malwares on x86, x86-64,ARM,MIPS ,MIPSEL cpu architecture - The Multiplatform Linux Sandbox : https://github.com/detuxsandbox/detux
"detux ︰ 分析 Linux 恶意软件流量的沙盒系统,支持 x86、x86-64、ARM、MIPS、MIPSEL 架构 ︰ https://t.co/TMQZcmCUb4"
-

[ Tools ] We just uploaded a new tool created by @ ukstufus for rapid @ OpenVPN certificate & configuration deployment https://labs.mwrinfosecurity.com/tools/rapid-openvpn-certificate-and-configuration-deployment/
" OpenVPN 配置工具,一键生成并部署证书和配置文件,来自 MWR Labs: https://t.co/RezIJJjbLb"
-

[ Tools ] We've published a video blog about the Noise Protocol Framework http://noiseprotocol.org/ at https://cryptoservices.github.io/cryptography/protocols/2016/04/27/noise-protocol.html by @ lyon01_david
"Noise 是一个用于构建加密协议的框架: https://t.co/za1ljrvS2F 视频: https://t.co/tWksgCQUy5 "
-

[ Tools ] Python script to speed up analysis of newer MS office docs. Uses officedissector library, dumps macros https://github.com/infoassure/officefileinfo @ Info_Assure
"用于分析 MS Office X 格式的 Python 脚本,基于 officedissector 库, GitHub Repo: https://t.co/Axljt8FDpR "
-

[ Tools ] Just published Sysinternals updates, including Sysmon v4 with enhanced filtering, Procdump v8 and Sigcheck v2.51. https://blogs.technet.microsoft.com/sysinternals/2016/04/28/update-sysmon-v4-procdump-v8-sigcheck-v2-51/
"Sysinternals 工具集更新,本次更新了 Sysmon、Procdump 和 Sigcheck: https://t.co/ncAWfBpF1d"
-

[ Web Security ] D2 Elliot 1.5 is available with new exploits and tools. Bonus for this release: #0day for #joomla 1.5.26 and #vBSEO. http://d2sec.com/updates/d2_elliot_1.5.html
"D2 Elliot Web 漏洞利用框架更新 1.5 版本,本次更新增加了 joomla 1.5.26 和 vBSEO 的 0Day。 这是个付费的工具: https://t.co/3DNIVnuMzt"
-

[ Windows ] COM Object hijacking: the discreet way of persistence https://blog.gdatasoftware.com/2014/10/23941-com-object-hijacking-the-discreet-way-of-persistence #DFIR
"COM 对象劫持 - 一种比较隐蔽的持久控制方式, 来自 GData 2014 年的一篇 Blog: https://t.co/MAnzHF2CY8"
-

[ Windows ] Microsoft Windows Kernel win32k.sys TTF Processing Pool Corruption https://packetstormsecurity.com/files/136844/GS20160428155107.tgz
"Windows 内核 win32k.sys 在处理 TTF 字体文件时的内存池破坏漏洞(CVE-2016-0145): https://bugs.chromium.org/p/project-zero/issues/detail?id=684 "