腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] First post in the new zero-to-TrustZone series is up! Exploring QSEE - Qualcomm's Secure Execution Environment. http://bits-please.blogspot.com/2016/04/exploring-qualcomms-secure-execution.html
"从 0 到 TrustZone 系列文章: 第一篇 探究高通的 SEE(安全可执行环境),来自 Bits, Please Blog: https://t.co/3jfGwnfNpF"
-

[ Attack ] The hacker group Armada Collective, is threatening VPN providers with DDOS attacks http://www.digitaltrends.com/computing/blackvpn-armada-collective-ddos-threats-ransom-demands/ via @ DigitalTrends
"V.P.N 提供商 BlackV.P.N 因为拒绝 Armada 黑客组织的勒索请求,遭到 DDoS 攻击威胁: https://t.co/M3c8R5O0kg"
-

[ Attack ] Our latest blog digs deep into the PLATINUM APT group: http://ow.ly/4n5SNc
"深度挖掘 Platinum(白金) APT 组织, 来自微软 Blog ︰ https://t.co/etQzAdOd6x"
-

[ Attack ] Forcepoint Security Labs Publishes 2016 Global Threat Report: Forcepoint™ Security Labs™… http://j.mp/1SHopFF https://t.co/zl4z4ERFwt
"Forcepoint 发布 《2016 年全球威胁报告》,报告分为 5 章节:内部威胁、高级威胁、Web 和邮件威胁、云上的威胁、专家访谈: https://t.co/NFeos8CqeH https://t.co/zl4z4ERFwt"
-

[ Attack ] 2016 VZN data breach report is out. Top hits: old bugs, outdated Flash, unpatched Joomla/Wordpress 3rd party plugins http://www.verizonenterprise.com/resources/reports/rp_DBIR_2016_Report_Insiders_en_xg.pdf
"Verizon 发布 2016 年数据泄露调查报告(如果无法访问,请用 Prox.y): https://t.co/cUyMeYb0sH 上个月发过另一篇报告: http://www.verizonenterprise.com/resources/reports/rp_data-breach-digest_xg_en.pdf "
-

[ Attack ] Time Is Money: GozNym Launches Redirection Attacks in Poland http://ow.ly/4n7cF6
"时间就是金钱︰ GozNym 在攻击完北美的银行之后,立即开始投入新目标 - 波兰的银行: https://t.co/3i0R0wZuQU"
-

[ Challenges ] H5SC Mini-Challenge "XSS Metaphor" 5 - The Write-Up https://github.com/cure53/XSSChallengeWiki/wiki/H5SC-Mini-Challenge-5 #beta
"H5SC 迷你挑战 "XSS Metaphor" 5 解题笔记: https://t.co/61gceSEVpX #beta"
-

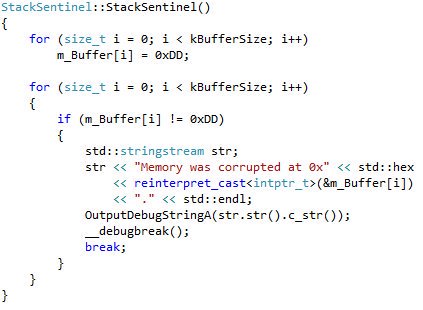
[ Debug ] Debugging memory corruption : http://blogs.unity3d.com/2016/04/25/debugging-memory-corruption-who-the-hell-writes-2-into-my-stack-2/ https://t.co/4auyvnA7ad
"Unity3D 内存破坏 Bug 调试 - 到底是谁向栈上写了个 2: https://t.co/prxcTKFOT1 https://t.co/4auyvnA7ad"
-

[ Forensics ] Google Rapid Response (GRR ) – Remote Live Forensics For Incident Response http://www.darknet.org.uk/2016/04/google-rapid-response-grr-remote-live-forensics-for-incident-response/
"GRR - Google 应急响应远程实时取证分析框架: https://t.co/0eq5MJoXcE"
-

[ Fuzzing ] Fuzzing Language Interpreters Using Regression Tests http://sean.heelan.ie/2016/04/26/fuzzing-language-interpreters-using-regression-tests/
"用回归测试的方法 Fuzz 语言解释器: https://t.co/1zEt7P8bjX"
-

[ Hardware ] Malware and non-malware ways for #ATM #jackpotting https://securelist.com/analysis/publications/74533/malware-and-non-malware-ways-for-atm-jackpotting-extended-cut/
"1967 年, 第一台 ATM 机在伦敦开始使用,现在全世界每天都在使用 ATM 机存款、取款,但银行和厂商对 ATM 机的安全关注却不够。 Kaspersky 这篇 Blog 介绍 ATM 机到底是如何工作的: https://t.co/QN60hAxib2 的"
-

[ Hardware ] Roundup of community-backed x86 hacker SBCs http://hackerboards.com/roundup-of-x86-hacker-sbcs/
"第一个由社区支持的 x86 hacker SBCs(单板计算机): https://t.co/TSIF4zrM5c"
-

[ Linux ] New Linux random number generator is coming http://www.chronox.de/lrng/doc/lrng.pdf According to comments https://news.ycombinator.com/item?id=11561340 it's crap.
"Linux 新的随机数生成器: https://t.co/9xtiXKSyDi 评论: https://t.co/13Pb1ZMGvO "
-

[ Linux ] UAF in Linux kernel 4.4 if "unprivileged_bpf_disabled" is not set (default): http://git.kernel.org/cgit/linux/kernel/git/davem/net.git/commit/?id=8358b02bf67d3a5d8a825070e1aa73f25fb2e4c7 grsec still requires CAP_SYS_ADMIN
" Linux 内核 4.4 replace_map_fd_with_map_ptr() UAF, Git Patch ︰ https://t.co/41PZ6vpnPw "
-

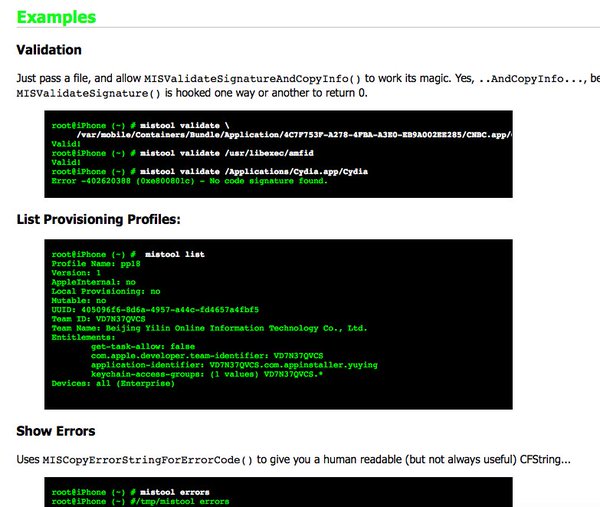
[ Mac OS X ] MISTool:query #iOS libmis(#signature/profile validation)+reversed #headers. http://newosxbook.com/tools/mistool.html open src #MOXiI https://t.co/Rq0MIgpGOn
"MISTool︰ 找出 libmis.dylib 中遗漏的部分: https://t.co/hNKd38NX1X https://t.co/Rq0MIgpGOn"
-

[ Malware ] How #Ransomware and Malware use Microsoft Windows’ Known Binaries | Check Point Blog http://blog.checkpoint.com/2016/04/26/how-ransomware-and-malware-use-microsoft-windows-known-binaries/
"恶意软件经常会伪装成 Windows 自身的系统进程(如 svchost.exe、explorer.exe 等),以此来躲避检测, 来自 CheckPoint Blog: https://t.co/bOgq1FoSbm"
-

[ Malware ] Ransomware in your inbox: the rise of malicious JavaScript attachments http://feedproxy.google.com/~r/nakedsecurity/~3/0ViimWsBitQ/
"收件箱中的勒索软件 ︰ 邮件附件中内嵌恶意 JavaScript 的数量持续上升,来自 Naked Security: https://t.co/jLT1WUEs3V "
-

[ Malware ] Uncovering a ransomware distribution operation (Part 2 ) : https://reaqta.com/2016/04/uncovering-ransomware-distribution-operation-part-2/ , Part 1 : https://reaqta.com/2016/04/uncovering-a-ransomware-distribution-operation/
"揭秘 Crypt0L0cker 勒索软件传播行动 - Part 2 感染过程的技术细节 : https://t.co/vd99bxpSQx Part 1 整体的传播情况及受影响的国家: https://t.co/ziBDoUfmrF"
-

[ Malware ] #CIH Virus aka #Chernobyl source code https://github.com/onx/CIH
"CIH 病毒的源码: https://t.co/R5b4eMDjXg"
-

[ Malware ] New Decryptor Unlocks CryptXXX Ransomware https://threatpost.com/new-decryptor-unlocks-cryptxxx-ransomware/117668/
"Kaspersky 研究员公开了一个 CryptXXX 勒索软件的解密工具, 来自 ThreatPost 的报道: https://t.co/dKzLl5KdI3 Kaspersky Blog: https://blog.kaspersky.com/cryptxxx-ransomware/11939/ "
-

[ Others ] Breaking #Steam client crypto with padding oracle attacks https://steamdb.info/blog/breaking-steam-client-cryptography/
"旧版本的 Steam 游戏客户端建立的加密连接可被 Padding Oracle 方式攻击,泄露敏感信息: https://t.co/hxBNLf2rPs"
-

[ Others ] A vendor perspective on crowd sourced penetration tests: https://blogs.adobe.com/security/2016/04/a-vendor-perspective-on-crowd-sourced-penetration-tests.html via @ peleusuhley
"从厂商的角度看 Bug Bounty, 来自 Adobe Blog: https://t.co/YYPPpWNmaS"
-

[ Others ] Great writeup of the Tor deanonymization tool used by the FBI. Similar to Metasploit Decloak, but different codebase https://twitter.com/csoghoian/status/725066035427201025
" 对 FBI 去 Tor 匿名化工具的分析: https://t.co/s2wDQXzw49 https://assets.documentcloud.org/documents/2124281/fbi-tor-busting-227-1.pdf "
-

[ Others ] Metamorphic Code Generator based on bytecode of LLVM IR http://scholarworks.sjsu.edu/cgi/viewcontent.cgi?article=1437&context=etd_projects
"基于 LLVM IR 字节码的变形代码生成器, Paper: https://t.co/mKQFBIiRGE "
-

[ Others ] @ fdfalcon FYI: we discussed precisely this bug type in our 2009 "Attacking Interoperability" paper: http://hustlelabs.com/stuff/bh2009_dowd_smith_dewey.pdf (~pg 67)
" 攻击互操作性 - 来自 Mark Dowd 2009 年在 BlackHat 的演讲 ︰ https://t.co/AcjfL9u5P1 "
-

[ Others ] My brief notes on "Automatic generation of hybrid data structure signatures from binary code executions": http://argp.github.io/2016/04/26/artiste/
" 从二进制代码的执行过程自动生成混合数据结构的签名, Paper: https://t.co/SLkACOdzJB"
-

[ ReverseEngineering ] Defusing a binary bomb with gdb (Part 4) : http://blog.carlosgaldino.com/2016/04/25/defusing-a-binary-bomb-with-gdb-part-4.html , Part 3 : http://blog.carlosgaldino.com/2015/12/03/defusing-a-binary-bomb-with-gdb-part-3.html, Part 2 : http://blog.carlosgaldino.com/2015/11/19/defusing-a-binary-bomb-with-gdb-part-2.html
"GDB 逆向一个 ELF 二进制文件 Part 4: https://t.co/PxLPwJODX6 Part 3 : https://t.co/4FJtujxbL3, Part 2 : https://t.co/DLZYp5HA8L Part 1: http://blog.carlosgaldino.com/2015/11/12/defusing-a-binary-bomb-with-gdb-part-1.html "
-

[ SecurityProduct ] How a spamfilter can help you to drop a shell https://forsec.nl/2016/04/how-a-spamfilter-can-help-you-phish/
"McAfee 邮件网关可以 '帮' 你释放一个恶意 Shell: https://t.co/ivi78uf0J9"
-

[ Tools ] Anti-Sandbox and Anti-Virtual Machine Tool, Sems https://goo.gl/mjDD8z
"sems - 用于探测各种沙盒、虚拟机环境的工具: https://t.co/uewhqxAul5 "
-

[ Tools ] Writing a dynamic x86_64 assembler in Scala : https://github.com/guillaumebort/scasm
"用 Scala 语言写的一个简单的 x86_64 汇编器 ︰ https://t.co/Iv4D2SZtZZ"
-

[ Virtualization ] Hypervisor Top Level Functional Specification v4.0 on github - https://github.com/Microsoft/Virtualization-Documentation/blob/master/tlfs/Hypervisor%20Top%20Level%20Functional%20Specification%20v4.0.pdf read as hyper-v top-level internals documented
"微软 Windows Server 2012 R2 Hypervisor 顶层功能性规范: https://t.co/veLgywwvD6 "
-

[ Web Security ] Trend Micro (Account) - Email Spoofing Web Vulnerability http://goo.gl/fb/XK6mrK #FullDisclosure
"趋势科技邮件欺骗 Web 漏洞,来自 FullDisclosure 的公告: https://t.co/W5eX2np6rk "
-

[ Windows ] Now published: PowerShell Remoting Security Considerations - https://msdn.microsoft.com/en-us/powershell/scripting/topic/winrmsecurity
"PowerShell Remoting 安全注意事项, 来自 MSDN: https://t.co/BoXHoWZ4FW"
-

[ Windows ] The side effect of removing the VDM by default on Windows 8 to solve the kernel NPD problem, Session 0 access :-) https://bugs.chromium.org/p/project-zero/issues/detail?id=692
"CSRSS BaseSrvCheckVDM Session 0 Process Creation EoP: https://t.co/ZXWyFPb6QQ Windows 8 默认移除 VDM 的副作用"