腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] The largest malicious campaign on Google Play: Trojan porn clicker http://www.welivesecurity.com/2016/02/24/porn-clicker-trojans-google-play-analysis/ #Android #Malware https://t.co/uWIhb58vme
"Google Play 上出现了大量的色情点击木马, 这些木马伪装成 '地铁跑酷' 或者 'GTA' 游戏, 来自 WeLiveSecurity 的分析: https://t.co/Q2Ye3GyvfG https://t.co/uWIhb58vme"
-

[ Android ] Improving dynamic analysis coverage in Android with DroidBot | The Honeynet Project https://honeynet.org/node/1317
"Honeynet 项目 DroidBot, 该工具可以有效地提高 Android 恶意软件动态分析时的覆盖率: https://t.co/sGwEBc0iU1"
-

[ Attack ] Operation Dust Storm : https://www.cylance.com/hubfs/2015_cylance_website/assets/operation-dust-storm/Op_Dust_Storm_Report.pdf?t=1456259131512 (pdf) #backdoor
"Cylance 揭露 Dust Storm(沙尘暴)攻击行动, 该攻击行动针对多个行业, 涉及日本、美国、韩国、欧洲、南亚部分国家: https://t.co/RnyIPmOQKa "
-

[ Attack ] Behind the Malware – Botnet Analysis https://blog.sucuri.net/2016/02/behind-the-malware-botnet-analysis.html
"在分析防火墙日志时,Sucuri Labs 发现了一个针对 WordPress 幻灯片插件 RevSlider 历史漏洞的攻击行为, 这篇 Blog 分析这次攻击过程中的 Botnet: https://t.co/P2gsjyO1o0"
-

[ Attack ] Operation Blockbuster revealed: A glimpse at the spider web of the Lazarus Group APT campaigns https://securelist.com/blog/incidents/73914/operation-blockbuster-revealed/
"Blockbuster 攻击行动揭秘 - 瞟一眼 Lazarus 组织的 APT 攻击行动蜘蛛网, 来自 Kaspersky Blog: https://t.co/DQDJfHwyrw"
-

[ Backdoor ] Backdooring Binary Objects : http://phrack.org/issues/56/9.html #b2b #Phrack
"Phrack 2000 年的一篇文章, 谈如何优雅地将二进制文件后门化: https://t.co/W3jitUCJrk "
-

[ Crypto ] How to perform SSL striping. https://avicoder.me/2016/02/22/SSLstrip-for-newbies/
"SSL Strip 教程: https://t.co/GiMhrIsuM2"
-

[ Defend ] Suhosin for PHP7 progress: transparent cookie encryption, some input filtering and disable display_errors #suhosin7 https://github.com/sektioneins/suhosin7
"Suhosin - PHP 安全防护扩展组件,现在更新对 PHP7 的支持,支持透明 cookie 加密、输入过滤和错误回显禁用等功能, Github Repo: https://t.co/PGayek1Wr1"
-

[ Detect ] Detecting Advanced Threats with Sysmon, WEF and ElasticSearch http://joshuadlewis.blogspot.com/2014/10/advanced-threat-detection-with-sysmon_74.html
"基于 Sysmon、 WEF 和 ElasticSearch 工具的高级威胁检测方案, 2014 年的一篇 Blog: https://t.co/8KzxbA5qAO "
-

[ Firmware ] New blog post: Exploiting SMM callout vulnerabilities in Lenovo firmware http://blog.cr4.sh/2016/02/exploiting-smm-callout-vulnerabilities.html Sources: http://github.com/Cr4sh/fwexpl
"联想 UEFI 固件 SMM 驱动 SMI Handler 漏洞的利用, Blog: https://t.co/Yx868H6mnZ Github Repo: https://t.co/Hiy3fVmeOU"
-

[ Hardware ] Ghost in the Machine: “MouseJack” Wireless Mouse and Keyboard Injection Vulnerability http://www.tenable.com/blog/ghost-in-the-machine-mousejack-wireless-mouse-and-keyboard-injection-vulnerability #infosec
"机器中的幽灵 - Tenable 对 'MouseJack' 无线鼠标和键盘注入漏洞的分析文章: https://t.co/Y7sWrJsDkS "
-

[ Hardware ] Introduction to Microcontrollers (Part 1 - 14) : http://www.embeddedrelated.com/showarticle/453.php
"了解微控制器 (Part 1 - 14): https://t.co/Ed3hYnczpq"
-

[ Hardware ] Controlling vehicle features of Nissan LEAFs across the globe via vulnerable APIs : http://www.troyhunt.com/2016/02/controlling-vehicle-features-of-nissan.html
"通过有漏洞的 API 跨越全球控制 Nissan LEAFs, Nissan LEAFs 是一款 Nissan 产的两厢纯电动汽车: https://t.co/gcK3cR0lu7"
-

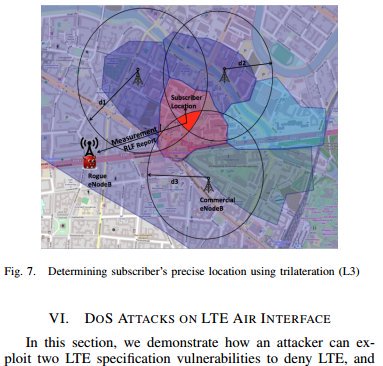
[ Hardware ] Practical Attacks Against Privacy and Availability in 4G/LTE Mobile Communication Systems https://www.internetsociety.org/sites/default/files/blogs-media/practical-attacks-against-privacy-availability-4g-lte-mobile-communication-systems.pdf https://t.co/VczdmzAeWZ
"4G/LTE 移动通信系统的隐私性和可用性攻击实战, 来自德国柏林工业大学的 Paper: https://t.co/Q1pt05xVEr https://t.co/VczdmzAeWZ"
-

[ Industry News ] #XamarinJoinsMicrosoft to delight developers everywhere: http://xmn.io/21rpOUp https://t.co/EkQpDCJAmd
"微软收购了 Xamarin, Xamarin 是一家从事手机应用开发的公司: https://t.co/4sDK0wMpnJ https://t.co/EkQpDCJAmd"
-

[ iOS ] Open List of Requested iOS Security Improvements http://www.zdziarski.com/blog/?p=5741
"iOS 安全改进心愿单, 来自 Zdziarski Blog: https://t.co/ZkPUVuwqjM"
-

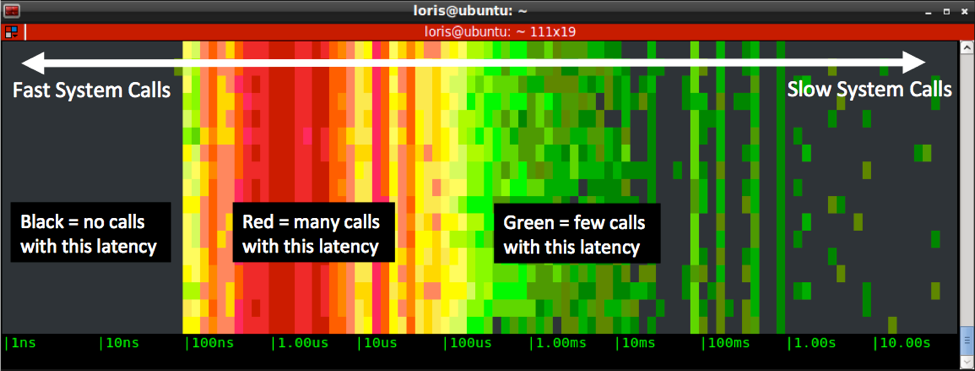
[ Linux ] 50 Shades of System Calls https://sysdig.com/50-shades-of-system-calls/ https://t.co/8cKgn9oCKo
"系统调用的 50 个色调, 根据调用次数不同,划分成不同的色调。 来自 SysDig Blog: https://t.co/uNXb9XbhMz https://t.co/8cKgn9oCKo"
-

[ Linux ] My presentation slides from today's @ sectalks_MEL are up! "Escape from SHELLcatraz" available here: https://speakerdeck.com/knaps/escape-from-shellcatraz-breaking-out-of-restricted-unix-shells #infosec #unix
"从受限的 Unix Shell 中逃逸: https://t.co/2ePzRKcheJ "
-

[ Linux ] Linux 64-bit io_submit L2TP sendmsg integer overflow: https://code.google.com/p/google-security-research/issues/detail?id=735
"Linux 64-bit 内核 io_submit L2TP sendmsg 整数溢出漏洞, 成功利用该漏洞可以实现本地提权。 来自 Project Zero Issue 735: https://t.co/MvFt5x2Uj5"
-

[ MalwareAnalysis ] A new blog investigates Nivdort, a #Trojan that downloads dangerous #malware. See how it works: https://blogs.mcafee.com/mcafee-labs/nivdort-data-stealing-trojan-arrives-via-spam/?utm_source=twitter&utm_campaign=Labs
"McAfee 对数据窃取木马 Nivdort 的分析, 该木马通过垃圾邮件传播: https://t.co/7u07NK9YcT"
-

[ MalwareAnalysis ] Analyzis of a Malicious .lnk File with an Embedded Payload, (Wed, Feb 24th) https://isc.sans.edu/diary.html?storyid=20763&rss
"SANS Blog 对一个钓鱼邮件中的 .lnk 样本的分析: https://t.co/f341Gakgab"
-

[ Others ] CESG white paper about Quantum Key Distribution is available on our website: https://www.cesg.gov.uk/content/files/protected_files/guidance_files/Quantum%20Key%20Distrubution%20-%20CESG%20White%20Paper.pdf #CESGguidance
"CESG Paper: 量子密钥分发: https://t.co/r4qtmNwS0G "
-

[ Others ] In-depth analysis & reversing of Locky malware. Word payload, AV evasion & OSINT on the C&Cs https://www.sensepost.com/blog/2016/understanding-locky/ by @ v1ad_o & @ dcuthbert
"SensePost 对 Locky 勒索软件的深度分析,包括 Word Payload、AV 逃逸技巧、C&C: https://t.co/IUjInQBrq9 "
-

[ Others ] Windows Mobile Application Security Testing - Part 4 http://anandsecurity.blogspot.com.tr/2016/02/windows-mobile-application-security_24.html by @ anandtiwarics
"Windows Mobile 应用程序安全测试 Part 4: https://t.co/HEq5vw04bd Part 3: http://anandsecurity.blogspot.com.tr/2016/02/windows-mobile-application-security_95.html Part 2: http://anandsecurity.blogspot.com.tr/2016/02/windows-mobile-application-security_22.html Part 1: http://anandsecurity.blogspot.com.tr/2016/02/windows-mobile-application-security.html "
-

[ Others ] LPC13xx Bootloader Analysis https://domenpk.github.io/lpc13xx_boot_analysis/
"NXP lpc1313/lpc1343 Bootloader 分析, 来自 domenpk Blog: https://t.co/L3ptWRHFMB"
-

[ Pentest ] Directory Traversal, File Inclusion, and The Proc File System https://blog.netspi.com/directory-traversal-file-inclusion-proc-file-system/
"目录遍历、 本地文件包含漏洞的攻击中,攻击者往往直接读取 /etc/passwd 文件,泄露密码信息。 而这篇文章提到,攻击者还可以通过读取 /proc 文件系统获取一些有意思的信息: https://t.co/2S8Tchmllt"
-

[ Popular Software ] Available for download: @ NCCsecurityUS’s Public Report of the Ricochet Security Assessment funded by @ OpenTechFund http://bit.ly/1QelYKE
"NCC Group 对匿名通信应用 Ricochet 的安全评估报告: https://t.co/An7CxaheD8 "
-

[ Popular Software ] New report: "Baidu’s and Don’ts: #Privacy and Security Issues in #Baidu Browser" https://citizenlab.org/2016/02/privacy-security-issues-baidu-browser/
-

[ Sandbox ] EMET has a global variable to on/off protections: https://www.fireeye.com/blog/threat-research/2016/02/using_emet_to_disabl.html. Flash Player has it for its sandbox also: http://reversingonwindows.blogspot.sg/2012/10/flash-player-enables-sandbox-via-global.html
"EMET 由一个全局变量控制保护功能的开启和关闭(昨天推送过的 FireEye 的文章): https://t.co/Nrynzh9fYb Flash Player Sandbox 也有一个全局变量开关, 来自一篇 2012 年的 Blog: https://t.co/BIeyrRujoK"
-

[ Tools ] [Press Release] Rapid7 releases disruptive new security incident detection and response solution, InsightIDR: http://www.rapid7.com/company/news/press-releases/2016/rapid7-launches-new-security-incident-detection-and-response-solution.jsp
"Rapid7 推出了一款检测和应急响应解决方案 - InsightIDR: https://t.co/PVEPJx4gwN"
-

[ Tools ] bettercap v1.4.4 released! https://www.bettercap.org/changelog/ https://t.co/2FshO1Uqef
"中间人攻击框架 bettercap v1.4.4 版本发布, changelog: https://t.co/CjDxHq3mVe https://t.co/2FshO1Uqef"
-

[ Tools ] x86 Emulator running Windows 98 in the browser (also try Archlinux, Kolibri, OpenBSD) : http://copy.sh/v86/
"Virtual x86 - 运行在浏览器里的 x86 模拟器,支持运行 Windows 98,也支持 Archlinux,Kolibri,OpenBSD 等操作系统, 来自 copy.sh : https://t.co/aGv5dYHD6t 这个模拟器还是开源的: https://github.com/copy/v86 "
-

[ Tools ] Cash : a cross-platform implementation of Unix shell commands in JavaScript : https://github.com/dthree/cash/ https://t.co/L2OS5M7YKx
"Cash - 跨平台的 Unix Shell 命令行工具, Github Repo: https://t.co/r4ySOxr8f3 https://t.co/L2OS5M7YKx"
-

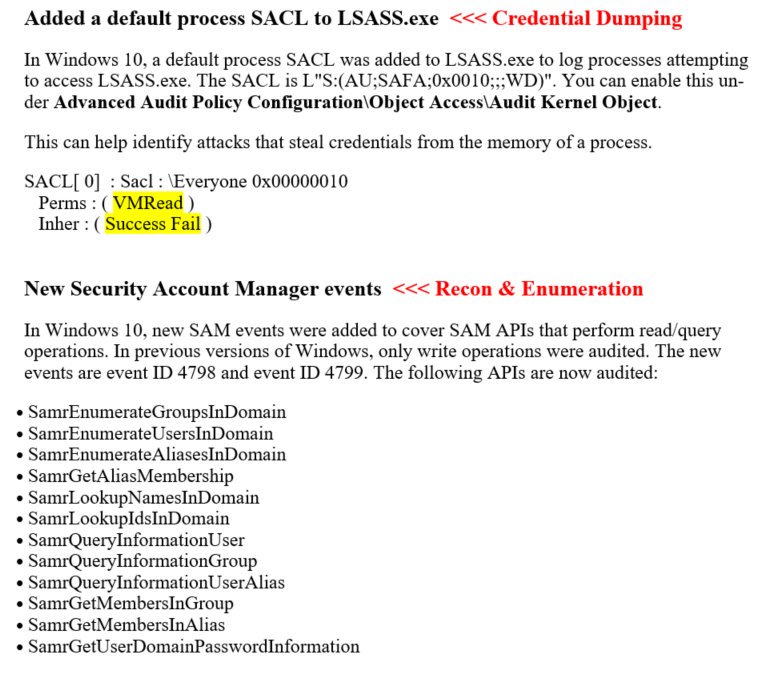
[ Windows ] Defenders, new logging in Win10 to help detect credential dumping and enumeration. #mimikatz https://technet.microsoft.com/en-us/library/mt431757(v=vs.85).aspx#BKMK_LSASS https://t.co/GO1qyrVawX
"Windows 10 在安全审计方面的新特性: https://t.co/zKHI1WZdRR 其中新添加了一个针对 lsass.exe 进程访问的日志记录功能,该功能有助于检测密钥凭据信息转储和枚举的攻击行为"
-

[ WirelessSecurity ] When Whales Fly – Building a Wireless Pentest Environment using Docker http://foxglovesecurity.com/2016/02/24/when-whales-fly-building-a-wireless-pentest-environment-using-docker/
"当鲸鱼飞起来的时候 — 搭建一个基于 Docker 的无线渗透测试环境, Blog: https://t.co/PXQlibCqyy"
-

[ WirelessSecurity ] MouseJack : Injecting Keystrokes into Wireless mouse : https://github.com/RFStorm/mousejack/blob/master/doc/pdf/MouseJack-whitepaper-v1.1.pdf (pdf)
"MouseJack - 昨天推送过一篇 ThreatPost 关于无线键盘鼠标注入攻击的报道,今天作者放入了一篇 Paper 《无线鼠标击键注入攻击》, PDF: https://t.co/7DPaaCjVyV Github Repo: https://github.com/RFStorm/mousejack/ "