腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Mobile malware evolution 2015 | Securelist https://securelist.com/analysis/kaspersky-security-bulletin/73839/mobile-malware-evolution-2015/ https://t.co/URJRCsg4Jp
"2015 年手机恶意软件发展情况报告, 来自 Kaspersky Blog: https://t.co/Yb49Bc414c https://t.co/URJRCsg4Jp"
-

[ Android ] The Evolution of Acecard https://securelist.com/blog/research/73777/the-evolution-of-acecard/
"Android 银行木马家族 Acecard 的演进, 来自 Kaspersky Blog: https://t.co/9wiNe7IpXA Kaspersky 发现, 最近澳大利亚成为银行木马攻击活动的主要国家,经过调查分析,这些攻击的背后就是 Acecard 木马家族"
-

[ Android ] Highly recommend "Android Application Secure Design/Secure Coding Guidebook" by @ jssec_org to Android developers: https://www.jssec.org/dl/android_securecoding_en.pdf
"强烈推荐 《 Android 应用程序安全设计/安全编码指南 》, 来自 JSSec(日本智能手机安全协会) 的出版书, PDF: https://t.co/c3oj5RQB7z"
-

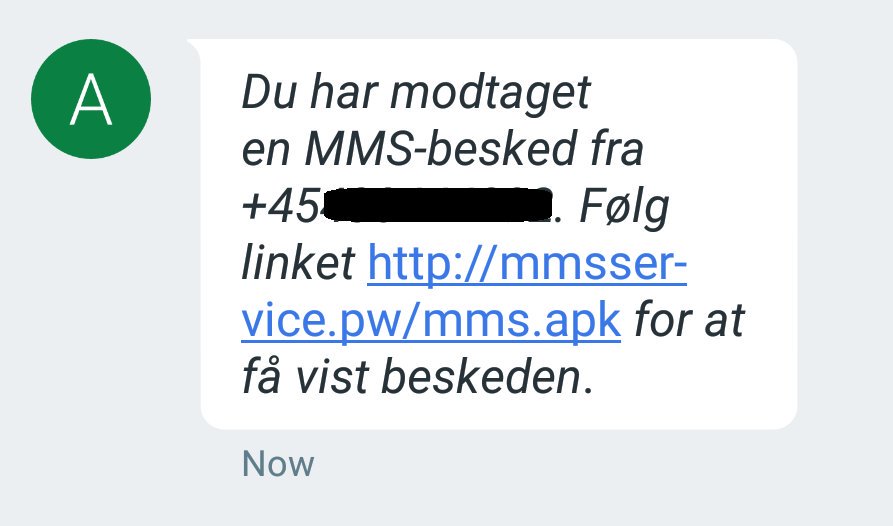
[ Android ] New MazarBot targeting the MobilePay can lock and erase your device http://b0n1.blogspot.com/2016/02/recent-mazarbot-targeting-mobilepay-can.html #MazarBOT #Android https://t.co/ltm0M5WIbj
"最近的 Android MazarBot 开始用钓鱼方式攻击手机支付, 而且可以锁定和清空手机: https://t.co/cXj9tV8Pt6 https://t.co/ltm0M5WIbj"
-

[ Attack ] Ratopak Trojan – Russian banks under attack http://securityaffairs.co/wordpress/44706/cyber-crime/ratopak-trojan-russian-banks.html
"Ratopak 木马攻击俄罗斯银行, 来自 SecurityAffairs 的报道: https://t.co/ON6sfR2bpi"
-

[ Crypto ] Eurocrypt 2016 papers http://ist.ac.at/eurocrypt2016/accepted.html
"Eurocrypt 2016 会议接受的 Papers: https://t.co/4jlSCVQoRr"
-

[ Detect ] Bro plugin to detect Meterpreter traffic, including XOR-encoded traffic https://github.com/ncsa/bro_meterpreter?platform=hootsuite #DFIR #infosec
"用于检测 Meterpreter 流量的 Bro 插件,也支持检测 XOR 编码的流量, Github Repo: https://t.co/KSiPfLuSwv "
-

[ Hardware ] Wireless mice, keyboards vulnerable to injection attacks from 100 meters away. #mousejack https://threatpost.com/mousejack-attacks-abuse-vulnerable-wireless-keyboard-mouse-dongles/116402/ via @ threatpost
"包括罗技、戴尔、联想等 7 个厂商的无线键盘、鼠标存在注入攻击漏洞,可以在 100 米内向无线键盘、鼠标设备发起注入攻击, 来自 ThreatPost 的报道: https://t.co/xiGtf9BOKi"
-

[ Linux ] “USB hub malformed packets causes null pointer dereference - Linux” or “in out, in out, shake it all about: b00m!” http://www.spinics.net/lists/linux-usb/msg132311.html
""USB Hub 畸形数据包触发 Linux 内核空指针解引用, 来自 Spinics 邮件列表: https://t.co/VI9b1ZghoA"
-

[ MalwareAnalysis ] The Rise of Locky: Dridex Crew Bets on Ransomware https://www.invincea.com/2016/02/dridex-crew-bets-on-ransomware/
"Locky 的崛起与 Dridex 团伙对勒索软件的押注, 来自 Invincea Blog: https://t.co/iMgGobkYXh "
-

[ MalwareAnalysis ] Locky Ransomware http://www.webroot.com/blog/2016/02/22/locky-ransomware/
"WebRoot 对 Locky 勒索软件的分析: https://t.co/krgWCjgsDJ"
-

[ MalwareAnalysis ] PoS Malware: All You Need to Know http://resources.infosecinstitute.com/pos-malwareall-you-need-to-know/
"关于 POS 恶意软件, 你需要了解的一切, 来自 InfoSec Blog: https://t.co/XhAQ4RHako "
-

[ Mitigation ] Disabling EMET protection by calling EMET unload func. Triggered by calling emet.dll's DllMain w/DLL_PROCESS_DETACH https://www.fireeye.com/blog/threat-research/2016/02/using_emet_to_disabl.html
"FireEye 的文章 《用 EMET 禁用 EMET》,这篇文章介绍了通过调用 EMET 卸载函数来禁用 EMET 保护的方法,调用 DllMain (GetModuleHandleW("EMET.dll") , DLL_PROCESS_DETACH , NULL); 禁用保护: https://t.co/4cbSNKKM3r "
-

[ Operating System ] With datacenter OSs and virtualization, Unikernels become possible and eliminate underlying OS attack surface: https://raw.githubusercontent.com/hioa-cs/IncludeOS/master/doc/papers/IncludeOS_IEEE_CloudCom2015_PREPRINT.pdf
"为云计算环境定制的操作系统内核 IncludeOS, Paper: https://t.co/eADJEcAT3I"
-

[ Others ] Microsoft Enterprise #Cloud Red Teaming https://azure.microsoft.com/en-us/documentation/articles/azure-security-enterprise-cloud-red-teaming/ <updated today, now with a link to downloadable version [PDF] #Security
"微软企业云渗透测试团队介绍: https://t.co/z5RwiSSkV0 从攻和防两方面了解微软企业云安全团队所做的工作"
-

[ Popular Software ] Compromising Symantec Endpoint Protection 11.x http://codewhitesec.blogspot.gr/2016/02/symantec-endpoint-protection-legacy-edition.html
"Symantec SEP(终端保护) 11.x 版本存在多个漏洞,包括 SQL 注入、命令执行、二进制注入等漏洞, 来自 CodeWiteSec Blog: https://t.co/TapdsXzqV7 去年 7 月份,作者还写过一篇文章,分析 Symantec SEP 12.1 版本的多个漏洞: http://codewhitesec.blogspot.com/2015/07/symantec-endpoint-protection.html "
-

[ Popular Software ] Using 'Free' SSL/TLS Certificates from Lets Encrypt with NGINX https://www.nginx.com/blog/free-certificates-lets-encrypt-and-nginx/
"用 Lets Encrypt 的方案在 NGINX 服务器上启用 SSL/TLS 免费证书, 来自 Nginx Blog: https://t.co/eQjYBbKh7P"
-

[ ReverseEngineering ] Reverse engineering the wheel of fortune NES game http://buff.ly/1Wrynva https://t.co/mxt43FtS4b
"逆向财富之轮游戏: https://t.co/chrLVbT7Xs https://t.co/mxt43FtS4b"
-

[ Tools ] Nextkey : Free KeyLogger for Kali Linux ,Ubuntu & Debian : https://github.com/misteriouser/NextKey
"Nextkey - 开源 KeyLogger, 支持 Linux、Ubuntu 和 Debian, Github Repo: https://t.co/DFokBJRDiN"
-

[ Tools ] block-parser : Parser for Windows PowerShell script block logs : https://github.com/matthewdunwoody/block-parser
"block-parser - Windows PowerShell 脚本执行日志解析器,PowerShell 代码的执行过程系统以事件日志的格式存储,block-parser 可以解析这种日志格式,转化成人易读的格式,方便取证分析。 Github Repo: https://t.co/qmak5zH2OD"
-

[ Tools ] VirusShare-Search : Downloads VirusShare hashes and searches them for specified MD5 hashes : https://github.com/AdamGreenhill/VirusShare-Search
"VirusShare 是一个病毒 Hash 库,存有大量病毒样本的 Hash,VirusShare-Search 工具提供了样本搜索和比对的功能, Github Repo: https://t.co/a57s6dcFIz"
-

[ Tools ] Internetwache RE60 Writeup: Symbolic Execution Tramples CTF Challenge - https://github.com/praetorian-inc/ctf-writeups/tree/master/internetwache-2015
"用符号执行的方法解 Internetwache RE60 CTF 题, Github Repo: https://t.co/BAkMUMjxUC Blog: https://www.praetorian.com/blog/internetwache-re60-writeup-symbolic-execution-tramples-ctf-challenge "
-

[ Windows ] Reversing PowerPoint and Custom Actions in Attacks : http://phishme.com/powerpoint-and-custom-actions/
"PhishMe 团队从最近捕获的 PowerPoint 钓鱼攻击中发现, 攻击者不再使用宏触发恶意 Payload, 而是通过 PowerPoint 自定义动作来触发 Payload 的执行: https://t.co/ICBKMpvUe4"
-

[ WirelessSecurity ] Receiving C-Band AERO Signals http://www.rtl-sdr.com/c-band-aero-signals/
"接收 C 波段航空信号, 来自 RTL-SDR Blog: https://t.co/MAm1DTZzlj"