腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Just published 3 chs. of "Mobile #IncidentResponse for #Android & #iOS” via @ NowSecureMobile http://ow.ly/YLjlP https://t.co/yWH2B5LTl6
"来自 NowSecure 的 《Android iOS 安全应急响应》(书), 也可以在线浏览: https://t.co/LrebDfVW9H https://t.co/yWH2B5LTl6"
-

[ Android ] Appie v3 - Android Pentesting Portable Integrated… http://goo.gl/V0zEUD #Androguard #Android #AndroidPentesting https://t.co/u3vaoV1X1B
"Appie v3 - Windows 平台 Android 便携式渗透测试框架: https://t.co/dZIA6klOob https://t.co/u3vaoV1X1B "
-

[ Android ] Ransomware and SMS-Sending Trojans: Top Threats in Bitdefender Android H2 2015 Report https://labs.bitdefender.com/2016/02/ransomware-and-sms-sending-trojans-top-threats-in-bitdefender-android-h2-2015-report/
"Bitdefender 2015 下半年 Android 威胁报告, 报告中指出, 勒索软件和短信木马仍然是 Android 平台最主要的威胁: https://t.co/whpWN8OgLt "
-

[ Attack ] From Seoul To Sony https://www.bluecoat.com/security-blog/2016-02-24/seoul-sony
"从首尔到索尼, BlueCoat Blog 讨论索尼被黑事件与一些恶意软件家族的关联: https://t.co/1DRInH1FUI"
-

[ Attack ] [Report] The 7th edition of #MTrends is now available! http://bddy.me/1R4yoRP #DFIR #infosec https://t.co/vn5SNwWpSA
"FireEye M-Trends 2016 报告, 该报告总结回顾了 2015 年高级威胁的发展变化情况: https://t.co/8tp2qVHjDe https://t.co/vn5SNwWpSA"
-

[ Attack ] Attacks on social media, cloud apps exploit trust in popular free services http://phishme.com/attacks-on-social-media-cloud-apps-exploit-trust-in-popular-free-services/
"越来越多的钓鱼攻击开始转向社交媒体(如 Facebook、Twiiter) 和一些免费的云应用(如 Office 365、Dropbox): https://t.co/JjXNARzjzx"
-

[ Browser ] Go everyone test ur browser if it has the obvious dangerous (but easy to fix) #0day vulnerability. #Edge #Chrome https://dl.dropboxusercontent.com/u/14747595/auto_download_test/test.html
"浏览器 'Auto-Download' 漏洞测试页面: https://t.co/oMEnkwK4S7"
-

[ Defend ] Counteracting Data-only Malware with Code Pointer Examination : https://www.sec.in.tum.de/assets/Uploads/kittelraid2015.pdf (pdf)
"通过代码指针检查打击纯数据型恶意软件, Paper: https://t.co/J0Yg68MUtW "
-

[ Firmware ] firmadyne : Towards Automated Dynamic Analysis for Linux-based Embedded Firmware : https://github.com/firmadyne/firmadyne/blob/master/paper/paper.pdf (pdf) , https://github.com/firmadyne/firmadyne
"firmadyne - 嵌入式固件自动化分析工具,可以动态分析基于 Linux 的嵌入式固件, Paper: https://t.co/ohru3ZJJmj Github Repo: https://t.co/TtPMkaAUk5"
-

[ Fuzzing ] HTMLFuzzer https://github.com/jackmasa/HTMLFuzzer
"HTMLFuzzer, Github Repo: https://t.co/fB8zCFsH8F"
-

[ Malware ] New post: FighterPOS Gets Worm Routine http://bit.ly/1LfH8aY @ TrendMicro
"TrendMicro 发现新版本的 FighterPOS 恶意软件增加了局域网蠕虫传播功能, Blog: https://t.co/QmEcl7y8Ac "
-

[ MalwareAnalysis ] The DGA of Qakbot.T https://johannesbader.ch/2016/02/the-dga-of-qakbot/
"银行木马 Qakbot 的 DGA(域名生成算法)分析, Blog: https://t.co/AcR8TIlw5G"
-

[ MalwareAnalysis ] 说说那些偷鸡不成蚀把米的事儿 http://blogs.360.cn/360safe/2016/02/25/pay_for_your_greedy/
"说说那些偷鸡不成蚀把米的事儿, 来自 360 Blog: https://t.co/pM9Pe62Zkk"
-

[ Obfuscation ] Experiments In JS Obfuscation & Deobfuscation For Hacking Html5 Apps And Malware Analysis http://damilarefagbemi.com/experiments-in-js-obfuscation-deobfuscation-for-hacking-html5-apps-and-malware-analysis/ #malware
"几种常见的 JavaScript 混淆和反混淆工具分析实战, Blog: https://t.co/RYUnCee0gt "
-

[ Others ] Details of the IDA Pro Floating Licence Server remote exploit: https://www.securifera.com/advisories/cve-2015-8277/
"Flexera FlexNet Publisher 栈缓冲区溢出 RCE(CVE-2015-8277): https://t.co/Rv6un6LKrv 还有一篇文章参考: http://securitymumblings.blogspot.com/2016/02/cve-2015-8277.html "
-

[ Others ] Practical Black-Box Attacks against Deep Learning Systems using Adversarial Examples http://arxiv.org/abs/1602.02697
"使用对抗型样本黑盒攻击深度学习系统, Paper: https://t.co/GQ3Rj7KpgX"
-

[ Others ] Malicious Forums Turn Amateur Hackers Into Cybercriminals https://blogs.mcafee.com/mcafee-labs/malicious-forums-turn-amateur-hackers-into-cybercriminals/
"一些提供恶意代码下载的论坛将业余黑客培养成了网络罪犯, 来自 McAfee Blog: https://t.co/pwI3YdT8w2"
-

[ Others ] Qualcomm Adreno GPU driver "perfcounter query" heap overflow: https://code.google.com/p/google-security-research/issues/detail?id=734
"高通 Adreno GPU MSM 驱动堆溢出漏洞,在查询性能计数器时,有符号数、无符号数转换触发整数溢出,继而触发堆溢出。 来自 Project Zero Issue 734: https://t.co/dHnQhKUbqz"
-

[ Others ] ARM Assembly Language : http://www.googoolia.com/micro/lecture/arm_assembly.pdf (pdf)
"伊斯法罕大学的 ARM 汇编语言课件, PDF: https://t.co/b86caDlKOd "
-

[ Pentest ] Building an Effective Active Directory Lab Environment for Testing : https://adsecurity.org/?p=2653
"搭建一个 Active Directory 渗透测试实验环境, 来自 AD Security Blog: https://t.co/1FI2OrzlB7"
-

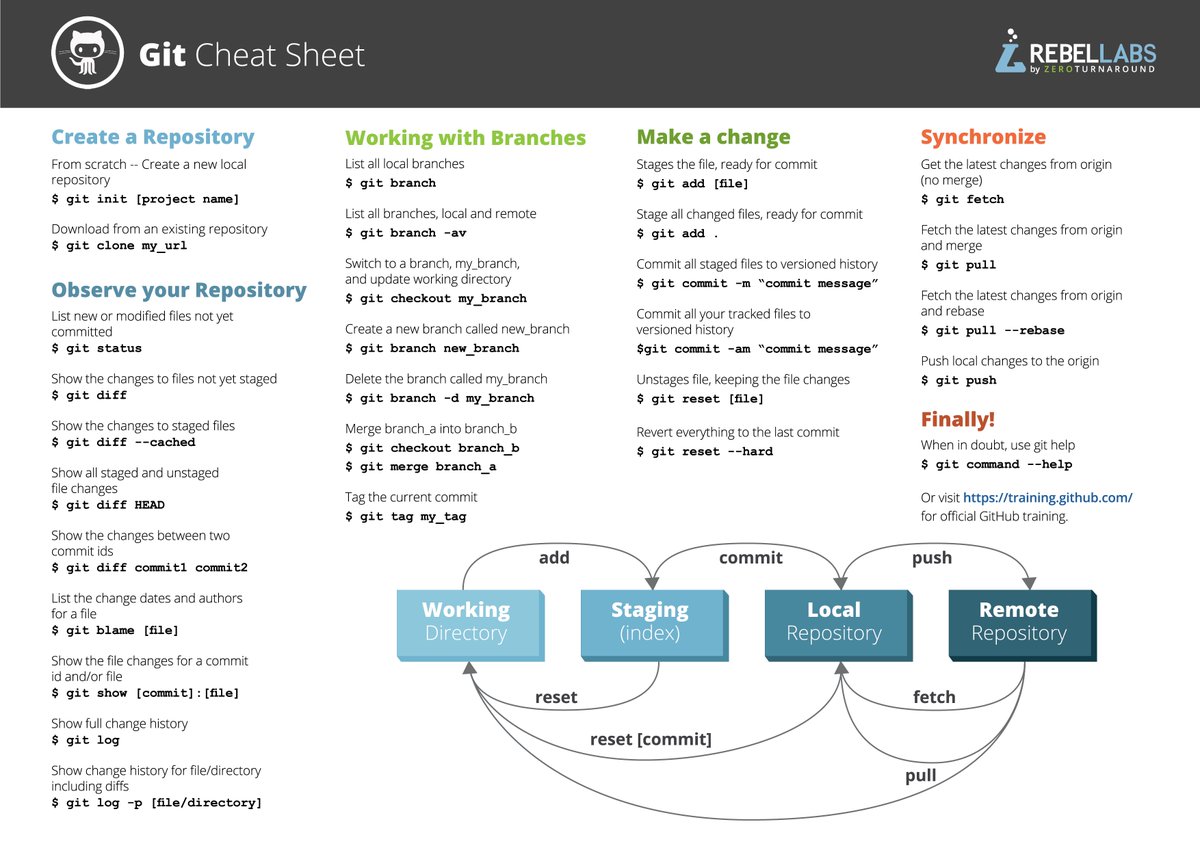
[ Tools ] Git CheatSheet : http://zeroturnaround.com/rebellabs/git-commands-and-best-practices-cheat-sheet/ https://t.co/YQ4aPYX20E
"Git 命令手册: https://t.co/JCP8WDkzxo https://t.co/YQ4aPYX20E"
-

[ Tools ] A tool from @ jpcert_en to visualize "APT campaign information and to visualize relations of IOC" https://github.com/S03D4-164/Hiryu
"Hiryu - 威胁分析可视化工具,用于整理 APT 行动信息和可视化地关联 IOC 信息, Github Repo: https://t.co/OJ9Ddnm3mY"
-

[ Tools ] Firmware Test Suite (FWTS) 16.02.00 released, now with many ACPI updates. https://wiki.ubuntu.com/FirmwareTestSuite/ReleaseNotes/16.02.00
"FirmwareTestSuite 是一个由 Ubuntu 官方维护的固件测试工具: https://wiki.ubuntu.com/FirmwareTestSuite/ 现以更新到 16.02.00 版本, 该版本增加了许多关于 ACPI 的更新: https://t.co/hMoRdeKPsO"
-

[ Tools ] Sandbox for semi-automatic Javascript malware analysis and payload extraction. https://github.com/HynekPetrak/malware-jail #malware
"malware-jail - 基于 Node.js 的半自动 Javascript 恶意代码分析沙盒,也支持导出动态生成的 Payload : https://t.co/LTybGsG9j3"
-

[ Tools ] Jalangi - A Dynamic Analysis Framework for JavaScript http://www.eecs.berkeley.edu/~gongliang13/jalangi_ff/#about #malware
"Jalangi - JavaScript 动态分析框架,通过 Hook,该框架能够监控 JS 执行过程中的每一个动作,该工具以 Firefox 扩展的形式存在: https://t.co/kfNEaVT5ih "