腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Source Code For #GMBot Android Banking Malware Leaked: https://threatpost.com/source-code-for-android-banking-malware-leaked/116380/ via @ threatpost
"Android 银行恶意软件 GM Bot 的源码泄露了, 接下来一段时间将会出现大量 GM Bot 的变种: https://t.co/aG9Qu6IP7o"
-

[ Android ] How does Dalvik handle 'this' registers? - http://buff.ly/20Qpw7m
"Dalvik 虚拟机是如何处理 'this' 寄存器的? https://t.co/JrS5l3Xp2d"
-

[ Attack ] Admedia attacks now rely also on Joomla to serve ransomware http://securityaffairs.co/wordpress/44693/cyber-crime/admedia-attacks-joomla.html
"Admedia 攻击者现在正在将宿主目标转移至 Joomla, 来自 SecurityAffairs 的报道: https://t.co/ioGZZX5nz5"
-

[ Attack ] Japan targeted with regionalized malicious spam campaigns http://www.symantec.com/connect/ko/blogs/japan-targeted-regionalized-malicious-spam-campaigns
"最近,日本被区域化的恶意邮件行动盯上了, 来自 Symantec Blog: https://t.co/Nv1y8Pn3a7"
-

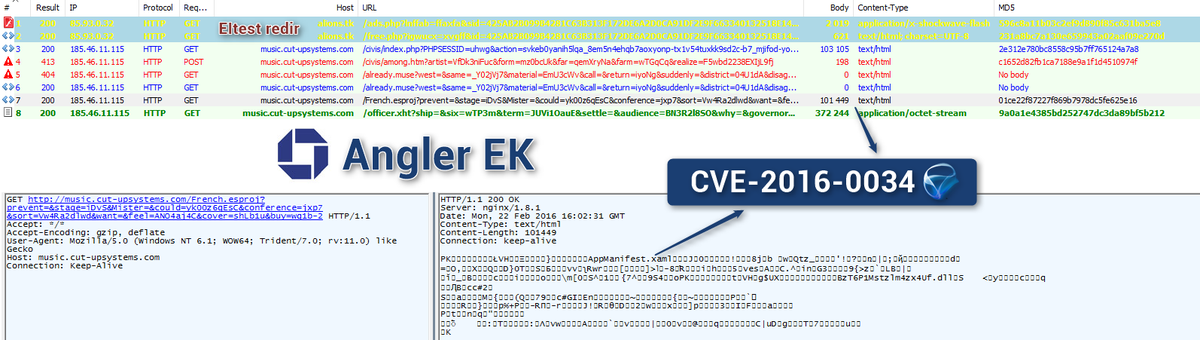
[ Attack ] Angler EK is now exploiting Silverlight up to 5.1.41105.0 (CVE-2016-0034 ? ) http://malware.dontneedcoffee.com/2016/02/cve-2016-0034.html https://t.co/zAaNRaAPeX
"Angler Exploit Kit 开始攻击 Silverlight 5.1.41105.0 CVE-2016-0034 漏洞, 该漏洞由 Kaspersky 研究员发现,最早在 HackingTeam 泄露的邮件中被提及: https://t.co/yPoYYku9Ny https://t.co/zAaNRaAPeX"
-

[ Detect ] Cool powershell script to automatically scan your system and report VirusTotal positives: http://blogs.technet.com/b/pfesweplat/archive/2016/02/20/powershell-malware-detection-and-tracking-of-new-autoruns.aspx
"Verify-Autoruns.ps1 - 恶意代码检测 PowerShell 脚本,可以扫描系统开机启动程序、验证签名、自动关联 VirusTotal 扫描结果,最终可以生成检测报告。 来自微软 TechNet Blog: https://t.co/jsmOawav9n"
-

[ Detect ] [/dev/random] Incident Handling with Docker Containers https://blog.rootshell.be/?p=30083
"应急响应中常用的几个恶意代码检测 Docker 容器, 来自 RootShell Blog: https://t.co/QfGw6bMmSG"
-

[ iOS ] IOActive researcher says invasive hardware attack or power analysis could unlock iPhone 5c. https://threatpost.com/delicate-hardware-hacks-could-unlock-shooters-iphone/116388/
"IOActive 研究员称:美国情报机构可以通过侵入型的硬件芯片攻击解锁 iPhone 5c, 来自 ThreatPost 的报道: https://t.co/u8ifEmy5EU"
-

[ Linux ] CVE-2016-2384 arbitrary code execution due to a double-free in the usb-midi linux kernel driver - https://xairy.github.io/blog/2016/cve-2016-2384 bonus: SMEP bypass
"Linux 内核 USB MIDI 驱动程序 Double Free 漏洞(CVE-2016-2384),利用这个漏洞实现任意代码执行,作者提供了可以绕过 SMEP 的 PoC。Blog: https://t.co/QfhW4oOecp "
-

[ Malware ] Necurs.P2P - A New Hybrid Peer-to-Peer Botnet http://www.malwaretech.com/2016/02/necursp2p-hybrid-peer-to-peer-necurs.html
"Necurs.P2P - 一个新的混合型 P2P Botnet, 来自 MalwareTech 的分析: https://t.co/E8guw9YybY"
-

[ Network ] PoC for getting remote HTTP Server date using gzip compressed HTTP Response : https://github.com/jcarlosn/gzip-http-time , Details : http://jcarlosnorte.com/security/2016/02/21/date-leak-gzip-tor.html
"从 GZIP 压缩的 HTTP Response 中提取服务器的日期信息, PoC : https://t.co/lENacwP0JP Blog : https://t.co/l3ot3m8kL5"
-

[ NetworkDevice ] Synology NAS DSM 5.2 Remote Code Execution (RCE) http://rileykidd.com/2016/01/12/synology-nas-dsm-5-2-remote-code-execution-rce/
"Synology NAS DSM 5.2 (NAS 存储设备)远程代码执行漏洞: https://t.co/BtABw6iuA2"
-

[ Others ] Reverse engineering the ARM1 processor's microinstructions : http://www.righto.com/2016/02/reverse-engineering-arm1-processors.html cc: @ kenshirriff https://t.co/mhnDHSRCji
"逆向 ARM1 处理器的微指令, 来自 Righto Blog: https://t.co/y8QqTOnt4l "
-

[ Others ] OpenLibra : The largest Internet platform for downloading free scientific ,technical ,Programming & security books: https://openlibra.com/en/collection/search/category/security_books
"OpenLibra : 科学、 技术、 编程与安全方面的电子书下载网站(免费): https://t.co/SZVQygK0l5"
-

[ Others ] #Unit42 finds pirated #iOS app store’s client successfully evaded Apple iOS code review http://bit.ly/1RgXxLI @ Unit42_Intel
"盗版的 iOS App Store 客户端(名叫 开心日常英语)成功地绕过了 Apple iOS 代码审查: https://t.co/hRYbXkHSIz "
-

[ Pentest ] Abusing Exchange Web Service - Part 1 http://www.shellntel.com/blog/2016/2/13/abusing-exchange-web-service
"滥用 Exchange Web 服务 - Part 1, 通过暴力穷举等手段获取密码凭据信息: https://t.co/iwAEXsxomS"
-

[ Tools ] IDA v6.9 service pack released! Multiple bug fixes include decompiler. Let's patch your IDA ;) https://www.hex-rays.com/products/ida/6.9/index.shtml#160222 #REhints
"IDA v6.9 Service Pack 发布! 修复了多个 Bug, 详细的更新说明: https://t.co/4K2wdoM6uM "
-

[ Tools ] Using an optimizing decompiler to reverse engineer an obfuscated program http://zneak.github.io/fcd/2016/02/21/csaw-wyvern.html
"fcd 编译器支持伪 C 代码输出前对代码做简化,而这个特性对于还原混淆后的程序很有用。 这篇 Blog 就是利用 fcd 的这个特性反混淆一个 CSAW Wyvern CTF 赛题程序: https://t.co/Bd5lzvWN9j"
-

[ Tools ] Free Online Tools for Looking up Potentially Malicious Websites https://zeltser.com/lookup-malicious-websites/
"潜在恶意网站/URL 检测、检查工具(在线版,全部免费): https://t.co/izmNVRwyv3 "
-

[ Web Security ] BlackBerry Enterprise Service 12 Self-Service - SQLi and Reflected XSS http://goo.gl/fb/OgdoK1 #FullDisclosure
"BlackBerry Enterprise Service 12 Self-Service - SQLi and Reflected XSS, 来自 FullDisclosure 的公告: https://t.co/8C8v2FmPhb "
-

[ Web Security ] Added #145 "XSS without User Interaction from passive Elements" to #H5SC. More variations welcome, it's a WIP. https://html5sec.org/#145
"HTML5 安全手册新添加了一个 '基于被动元素的无需用户交互的 XSS 测试用例', 来自 HTML5Sec Blog: https://t.co/UTFLLSnqVd"