腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] BlackEnergy infected also Ukrainian Mining and Railway Systems http://securityaffairs.co/wordpress/44452/hacking/blackenergy-mining-and-railway-systems.html
"TrendMicro 发现 BlackEnergy 与最近的乌克兰矿业和铁路系统攻击事件有关, 来自 SecurityAffairs 的报道: https://t.co/gOPNK1nv8F TrendMicro 对样本 KillDisk 的分析: http://blog.trendmicro.com/trendlabs-security-intelligence/killdisk-and-blackenergy-are-not-just-energy-sector-threats/ "
-

[ Crypto ] A Gentle Introduction to Secure Computation : http://www.alexirpan.com/2016/02/11/secure-computation.html
"安全计算简介: https://t.co/pM36LpIN9v"
-

[ Debug ] How to isolate VBS or JScript malware with Visual Studio http://feedproxy.google.com/~r/eset/blog/~3/O8WiZ96Y8mQ/
"如何借助 Visual Studio 在一个可控的隔离环境中执行 VBS 和 JScript, 观察恶意软件的行为: https://t.co/2lpH6LQJUG "
-

[ Detect ] Detecting Offensive PowerShell Attack Tools : https://adsecurity.org/?p=2604
"从 Windows 7 开始 PowerShell 开始系统内置,同时它功能强大又灵活,深受攻击者的喜爱。 来自 AD Security 的这篇 Blog 谈 PowerShell 相关攻击工具的检测: https://t.co/kI4XAobsSO"
-

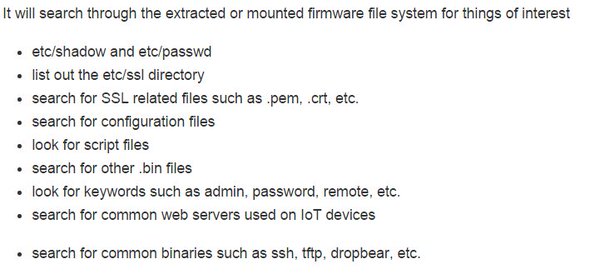
[ Firmware ] For ur #IoT sec research: firmwalker. a script for searching extracted/mounted firmware fs. https://github.com/craigz28/firmwalker https://t.co/dYD6qj8E1y
"firmwalker - 固件文件系统搜索工具,用于从已提取的固件文件目录中搜索有用的信息, 如 /etc/passwd、 SSL 相关的证书文件等: https://t.co/gtM06EkJ28 "
-

[ Fuzzing ] vUSBf:A KVM/QEMU based USB-fuzzing framework https://github.com/schumilo/vUSBf
"vUSBf - 一个基于 KVM/QEMU 的 USB Fuzz 框架, Github Repo: https://t.co/P8zfYXL4ns"
-

[ Hardware ] RE recent posts about GPU ISA reversing: I decided to put a post with links to open-source low-level GPU projects http://allsoftwaresucks.blogspot.ru/2016/01/on-gpu-isas-and-hacking.html
"与 GPU 有关的一些开源项目: https://t.co/g8wtzxeuCr"
-

[ iOS ] what. 64-bit iPhones and iPads get stuck in a loop when set to January 1, 1970 - http://arstechnica.com/apple/2016/02/64-bit-iphones-and-ipads-get-stuck-in-a-loop-when-set-to-january-1-1970/
"当把时间设置为 1970 年 1 月 1 日时, 64 位的 iPhone 和 iPad 陷入了死循环, 来自 ArsTechnica 报道: https://t.co/Yq3SCzgxJI"
-

[ Linux ] Linux System Call CheatSheet (Quick Reference) : http://www.digilife.be/quickreferences/qrc/linux%20system%20call%20quick%20reference.pdf ,Fascinating World of Linux System Calls : https://sysdig.com/fascinating-world-linux-system-calls/
"Linux 系统调用参考手册(PDF): https://t.co/S088chefrP Linux 系统调用的迷人世界, 来自 SysDig Blog: https://t.co/svcJcgGYqj"
-

[ Network ] Lots of interesting data sets in Geoff Huston's "Is #IPv6 Really Faster?": https://www.nanog.org/sites/default/files/Huston_Is_Ipv6.pdf [PDF] #nanog66 https://t.co/DwezE0VG53
"IPv6 真的更快吗? PDF: https://t.co/mlwj47JGf5 "
-

[ Others ] Presenting -"WMIKatz" - Executes Local File Mimikatz From WMI Provider https://gist.github.com/subTee/eeb18352321408bcee1e Memory Only Will Be Released @ WEareTROOPERS
" WMIKatz - 从 WMI Provider 中执行本地的 Mimikatz: https://t.co/zgIeJFkZz1"
-

[ Others ] New blog from me and @ teddyreedv about creating secure software where we release our @ NCCGroupplc pentest report: https://code.facebook.com/posts/226775617661196/in-pursuit-of-secure-open-source-software/
"努力构建一个安全的开源软件 - 来自 Facebook 的 Blog: https://t.co/tVeOxeo24T"
-

[ Others ] Vanessa Teague, The University of Melbourne, talks about security and vulnerability in e-voting. #enigma2016 https://goo.gl/bxcXbe
"墨尔本大学的 Vanessa 谈电子投票中的安全漏洞, Youtube 视频: https://t.co/L7X7B2VQQZ"
-

[ Pentest ] Dropping infected/weaponized files using a Human Interface Device : http://www.labofapenetrationtester.com/2015/01/dropping-weaponized-files-using-hid.html
"利用 HID 设备释放恶意样本, Blog: https://t.co/CaPU6QIgKL"
-

[ Pentest ] Easy Reverse Shells : http://www.labofapenetrationtester.com/2016/02/kautilya-easy-reverse-shells.html
"几个简单的反弹 Shell - TCP/UDP/ICMP/HTTP, Blog: https://t.co/EQBkqEfFxZ"
-

[ Tools ] JEB 2.2 demo - Debugging Android Dalvik and native code seamlessly, preview at https://www.youtube.com/watch?v=qfnvR7nA0wU
"JEB 2.2 支持无缝调试 Android Dalvik 和 Native 代码了, Youtube 演示视频: https://t.co/vGnzgkz3ik"
-

[ Windows ] New Blog post by Me @ R00tkitSMM : CVE-2016-0040 Story of uninitialized pointer ( local privilege escalation) http://goo.gl/HYvcp0
"CVE-2016-0040 未初始化指针的故事(MS16-014) - Windows 内核在处理 WMI 相关功能时存在漏洞,可以实现本地提权。 来自 R00tkitSMM Blog: https://t.co/auU334DAFU"
-

[ Windows ] What’s inside a PDB File? https://blogs.msdn.microsoft.com/vcblog/2016/02/08/whats-inside-a-pdb-file/
"调试器依赖 .pdb 文件, 那么 PDB 文件里到底有什么信息? 来自微软 VC++ Blog: https://t.co/X1629fEteu"