腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Reflecting on Recent iOS and Android Security Updates https://shar.es/14jQJz via @ sharethis
"对这个月 iOS 和 Android 安全更新的一些分析和思考, 来自 Zimperium Blog: https://t.co/JfYGqzTMjw"
-

[ Android ] Valentine's Day app downloads provide perfect opportunity for attacks http://www.symantec.com/connect/ko/blogs/valentines-day-app-downloads-provide-perfect-opportunity-attacks
"本月,情人节和约会相关的应用下载量增加,这对于攻击者来说是个绝佳的时机, 来自 Symantec Blog: https://t.co/kka7CsAIpw"
-

[ Android ] New blog post on Lobotomy #android #mobile #security https://twitter.com/lifeform_labs/status/698947286840303616
"Android 逆向分析框架 Lobotomy 的 surgicalAPI 介绍: https://t.co/fYV4dhy4uB"
-

[ Attack ] DeepEnd Research blog post: "Jan-Feb 2016 domains associated with "Admedia" Wordpress compromises (WP plugins)" http://www.deependresearch.org/2016/02/jan-feb-2016-domains-associated-with.html
"与 'Admedia' WordPress 攻击有关的域名, 来自 DeepEnd Research Blog: https://t.co/ipK5yziriY"
-

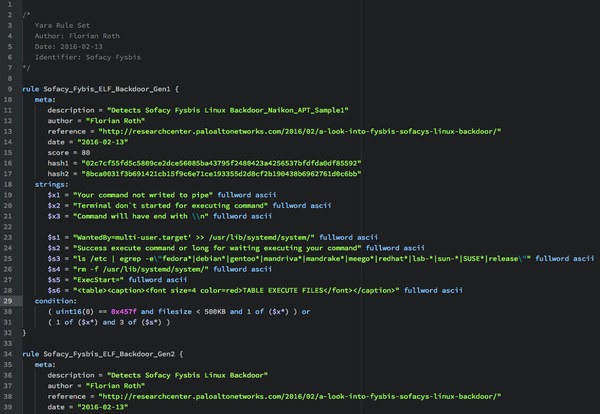
[ Attack ] #YARA rules for #Sofacy Fysbis ELF malware: https://github.com/Neo23x0/Loki/blob/master/signatures/apt_sofacy_fysbis.yar in addition to IOCs: http://researchcenter.paloaltonetworks.com/2016/02/a-look-into-fysbis-sofacys-linux-backdoor/ https://t.co/WYx2HW67GQ
"攻击组织 Sofacy 的 Linux 后门样本 Fysbis 分析: https://t.co/XnFSsQfxZo YARA 规则: https://t.co/WXwpJBJeA0 "
-

[ Crypto ] Padding oracles and the decline of CBC-mode cipher suites https://blog.cloudflare.com/padding-oracles-and-the-decline-of-cbc-mode-ciphersuites/
"Padding Oracle 与 CBC 模式密码套件的衰落, 来自 CloudFlare Blog: https://t.co/utUBkKPSoN "
-

[ Debug ] soswow64 : windbg extension for debugging 64-bit dumps of 32-bit .NET processes : https://github.com/poizan42/soswow64
"soswow64 - 用于调试 32 位 .NET 进程 64 位内存 Dump 的 Windbg 扩展工具: https://t.co/pZ4wEeWQUf"
-

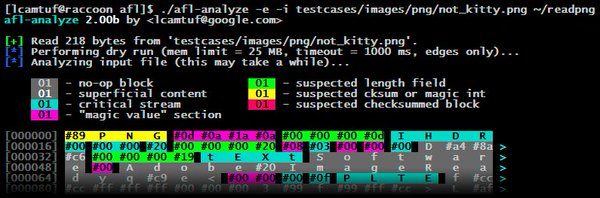
[ Fuzzing ] AFL-analyze: Inferring a file structure via fuzzing by @ lcamtuf https://lcamtuf.blogspot.com/2016/02/say-hello-to-afl-analyze.html https://t.co/Y3OI2S3OWX
"AFL-analyze - 新版本的 AFL 新添加的一个工具,该工具可以在 Fuzz 过程中自动化地推导文件结构: https://t.co/4gUC9zFXmg "
-

[ Hardware ] Lenovo's, batteries & Hacking ~Three Part series By Matt : http://www.zmatt.net/unlocking-my-lenovo-laptop-part-1/
"联想笔记本和电池的故事 - 作者新买了一块电池,安装上之后,BIOS 提示电池未通过认证,无法充电。于是作者开始尝试破解, Part 1: https://t.co/vnueQMM2aR Part 2: http://www.zmatt.net/unlocking-my-lenovo-laptop-part-2/ Part 3: http://www.zmatt.net/unlocking-my-lenovo-laptop-part-3/ "
-

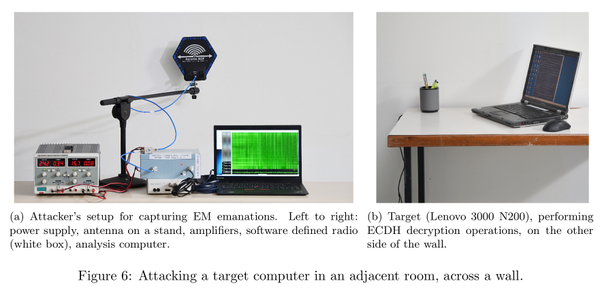
[ Hardware ] How to steal a GPG key from the next room: http://eprint.iacr.org/2016/129 By Eran Tromer (https://z.cash/team.html#scientists) et al. https://t.co/x9C1aTVsmF
"如何从隔壁房间窃取 GPG 密钥 - 通过低频电磁攻击提取密钥, 来自 IACR 的 Paper: https://t.co/DI68b3CWPr "
-

[ Linux ] #Tools to scan a #Linux server for #Malware & #Rootkit https://www.howtoforge.com/tutorial/how-to-scan-linux-for-malware-and-rootkits/ #MalwareMustDie #Tips https://t.co/owh6uK6E1C
"用于扫描 Linux 恶意软件、 Rootkit 的 3 款工具: Chkrootkit, Rkhunter and ISPProtect, 使用指南: https://t.co/nWU9v4PH2d "
-

[ Mac OS X ] New post: Toying around with Mac OS X malware and machine learning - Part 1 http://tbarabosch.de/2016/02/13/toying-part1.html
"通过机器学习的方法分析 OS X APP 的静态特征, 自动化地识别恶意软件: https://t.co/WD3atBnPho"
-

[ Mac OS X ] “Huge” number of Mac apps vulnerable to hijacking, and fix is elusive #infosec http://ow.ly/YhFDo @ arstechnica https://t.co/K7XTOhSPHH
"受第三方软件更新框架 Sparkle 的影响, 大量的 Mac OS X 应用存在中间人劫持漏洞: https://t.co/ZUwHSZ2mvy "
-

[ Mac OS X ] Extracting FileVault 2 keys with Volatility : https://tribalchicken.com.au/security/extracting-filevault-2-keys-with-volatility/ cc: @ tribalchickenAU
"用 Volatility 框架提取 OS X 磁盘加密工具 FileVault 2 的加密 Key: https://t.co/l2IB8OAQlq "
-

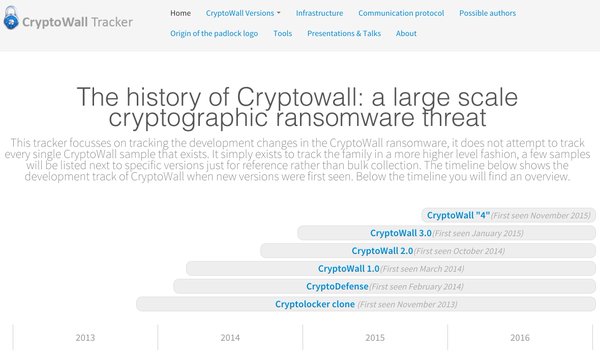
[ Malware ] Introducing the #CryptoWall tracker, a library of history, research and data on #CryptoWall: https://www.cryptowalltracker.org/ https://t.co/sb2hmUyCYg
"CryptoWall Tracker - CryptoWall 档案馆,记录了 CryptoWall 的发展史: https://t.co/NfMRgkqMZK https://t.co/sb2hmUyCYg"
-

[ NetworkDevice ] All Ubiquiti devices except EdgeOS have the same key and cert https://www.shodan.io/report/MXTZWxf0
"除 EdgeOS 外, 所有的 Ubiquiti 设备都使用相同的密钥和证书, 来自 Shodan 的统计信息: https://t.co/UDyFFctvRz"
-

[ NetworkDevice ] Ubiquiti Networks disclosed a bug submitted by 93c08539: https://hackerone.com/reports/73480 - Bounty: $18,000 #hackerone https://t.co/ekShxczMjC
"Ubiquiti AirMax 产品任意文件上传漏洞: https://hackerone.com/reports/73480 "
-

[ Pentest ] Using Problem Steps Recorder (PSR) Remotely with Metasploit https://cyberarms.wordpress.com/2016/02/13/using-problem-steps-recorder-psr-remotely-with-metasploit/
"通过 Metasploit Shell 远程调用 Windows 内置的问题步骤记录器, 获取用户操作的截屏和文字描述信息, 来自 Cyber Arms Blog: https://t.co/2PgMh7TvU6"
-

[ Tools ] #Python AST-based static analyzer from #OpenStack #Security Group https://github.com/openstack/bandit #infosec #audit #staticanalyzer
"Bandit - 基于抽象语法树的 Python 静态代码分析工具,用于扫描 Python 代码中的安全漏洞: https://t.co/ahNLglSVxt "
-

[ Tools ] Shellsploit: generate customized shellcodes, backdoors, injectors for different OS: https://github.com/b3mb4m/shellsploit-framework https://t.co/jAlBr2Amjm
"Shellsploit: 定制版 Shellcode、后门、Payload 生成器, 支持多种操作系统: https://t.co/5MVH2w5sLx "
-

[ Tools ] Put up a windbg script to do heap tracing and a moded version of villoc to visualise it with https://github.com/sam-b/windbg-plugins https://t.co/snv8zb1Uzj
"Windbg Heap Trace 脚本,可以输出可视化的 HTML 格式: https://t.co/N2NKUd1enJ https://t.co/snv8zb1Uzj "
-

[ Web Security ] An-Introduction-to-SQL-Injection-Attacks-for-Oracle-Developers : https://github.com/vinigomescunha/An-Introduction-to-SQL-Injection-Attacks-for-Oracle-Developers
"写给 Oracle 开发者的 SQL 注入攻击入门文章, 来自 Github: https://t.co/OoEYQ4Cw5u"
-

[ Windows ] Walkthrough & PoC for CVE-2014-1767: AFD.sys dangling pointer (MS14-040) - Windows 7, 32bit: http://ricklarabee.blogspot.in/2016/02/walkthough-and-poc-for-cve-2014-1767.html https://t.co/3MXTGJdcsI
"AFD.sys Double Free 漏洞 PoC 分析(CVE-2014-1767, MS14-040), Sebastian Apelt 利用这个漏洞在 Pwn2Own 2014 上实现了 System 提权: https://t.co/wELBySbF7J https://t.co/3MXTGJdcsI"
-

[ Windows ] What exactly is the "Windows internal POSIX fork clone capability" (https://msdn.microsoft.com/en-us/library/dn457825(v=vs.85).aspx)? [I thought Windows only had CreateProcess.]
"Windows 进程快照 - 利用 Windows 内部的 POSIX fork clone 特性可以为进程创建快照, 还支持将这个快照转储到文件, 来自 MSDN: https://t.co/NrnOm1NtHv "
-

[ Windows ] Defending Against Mimikatz https://jimshaver.net/2016/02/14/defending-against-mimikatz/
"如何阻止 Mimikatz 抓取 Windows 密码: https://t.co/YOkCvZ7wIw"