腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] How I hacked my hospital https://kas.pr/g3in by @ 61ack1ynx #TheSAS2016
"我是如何黑掉我的医院的 - Youtube 视频: https://t.co/rTbhRS88Xw "
-

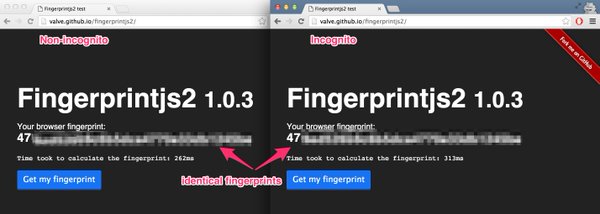
[ Browser ] Browser fingerprinting - take that Incognito Mode. https://github.com/Valve/fingerprintjs2 https://t.co/b5BDLSORou
"fingerprintjs2 - 浏览器指纹库: https://t.co/3CRj3VhBmI https://t.co/b5BDLSORou"
-

[ Browser ] Firefox 44.0.2 security fixes: https://www.mozilla.org/en-US/security/known-vulnerabilities/firefox/#firefox44.0.2
"Firefox 44.0.2 修复了一个同源策略相关的严重漏洞, Mozilla 公告: https://t.co/3UrtfF6wQl"
-

[ Cloud ] Deep Packet Inspection in Cloud Containers http://goo.gl/k17BVw #CloudComputing #ApplicationDataSecurity #NetworkSecurity
"云容器环境下的深度数据包检测, 来自 InfoSec Blog: https://t.co/mlbe5d0WF9 "
-

[ Conference ] Pwn2Own 2016 Rules http://zerodayinitiative.com/Pwn2Own2016Rules.html
"Pwn2Own 2016 比赛规则, 来自 ZDI: https://t.co/jXItAHks8e"
-

[ Defend ] Just saw a PANW blog post talking about #BadWinmail http://researchcenter.paloaltonetworks.com/2016/01/use-traps-to-protect-against-badwinmail-cve-2015-6172, remember: Flash is just 1 of the vulnerable OLE objects.
"Palo Alto 介绍如何通过自己的下一代防火墙组件 Traps 对抗 BadWinmail 攻击: https://t.co/m1MmbDJQ6A Haifei Li 表示: Flash 只是受影响的 OLE 对象中的一个"
-

[ Detect ] Greater Visibility Through PowerShell Logging http://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html
"如何启用更详细的 PowerShell 日志功能,便于观察恶意 PowerShell 脚本的行为, 来自 FireEye Blog: https://t.co/hM2CyoheC7"
-

[ Exploit ] The best resources for learning exploit development : https://www.peerlyst.com/posts/the-best-resources-for-learning-exploit-development @ Fabiothebest89 || @ ClausHoumann
"漏洞利用开发相关的一些资源链接, 来自 PeerLyst: https://t.co/Yvb2Nl2PYc "
-

[ IoTDevice ] KL-001-2016-001 : Arris DG1670A Cable Modem Remote Command Execution http://goo.gl/fb/ud0hPI #FullDisclosure
"Arris DG1670A 有线调制解调器远程命令执行漏洞, 来自 FullDisclosure: https://t.co/yQhj0brL0l "
-

[ Linux ] Linux kernel bug delivers corrupt TCP/IP data to Mesos, Kubernetes, Docker containers - https://medium.com/vijay-pandurangan/linux-kernel-bug-delivers-corrupt-tcp-ip-data-to-mesos-kubernetes-docker-containers-4986f88f7a19#.ap6wf48vm
"Linux 内核中的 Bug 导致使用 veth 网卡设备的容器(如 Docker)将损坏的 TCP/IP 数据传递给应用层: https://t.co/z55Z729yre"
-

[ Malware ] HackSpy-Trojan-Exploit : Creates almost undetectabe trojan virus to exploit windows machine : https://github.com/ratty3697/HackSpy-Trojan-Exploit
"HackSpy-Trojan-Exploit - 创建一个几乎无法检测的木马病毒(Windows), Github Repo: https://t.co/a67grIGjzo"
-

[ MalwareAnalysis ] HydraCrypt Another Variant of Ransomware Created With Angler Exploit Kit https://blogs.mcafee.com/mcafee-labs/hydracrypt-another-variant-of-ransomware-created-with-angler-exploit-kit/
"HydraCrypt - 通过 Angler EK 分发的勒索软件变种, 来自 McAfee Blog: https://t.co/y8fwAZynQr"
-

[ Others ] [Blog] Chrooting @ nginx ,php-fpm and @ MySQL using @ bitnami http://blog.dornea.nu/2016/02/12/chrooting-nginx-php-fpm-and-mysql-using-bitnami/ #security #infosec
"借助 bitnami 工具为 Nginx、php-fpm、MySQL 搭建一个 Chroot 环境: https://t.co/YQH3M7IHHx "
-

[ Popular Software ] Cracking PHP rand() : http://www.sjoerdlangkemper.nl/2016/02/11/cracking-php-rand/
"破解 PHP 随机数函数 rand(): https://t.co/NKNdI1xYAr"
-

[ Programming ] Java Security Guide http://goo.gl/cChjzy #SecureCodingJava
"Java 安全编码指南, 来自 InfoSec Blog: https://t.co/uTwk1TMWE8 "
-

[ Virtualization ] How Malware Detects Virtualized Environment, and its Countermeasures –An Overview http://resources.infosecinstitute.com/how-malware-detects-virtualized-environment-and-its-countermeasures-an-overview/
"恶意软件对虚拟化环境的检测以及相应的对策, 来自 InfoSec Blog: https://t.co/RKtkL4bH7o"
-

[ Web Security ] How I got a shell on one of the #Google Acquisitions ? | Blog - 0daylabs https://goo.gl/2XDjTN #bugbounty #infosec #0daylabs
"如何在 Google 收购的公司中获取一个 Shell: https://t.co/cYYLn1oZuV "
-

[ Web Security ] Compromising US Banks with Third-party JavaScript https://blog.gaborszathmari.me/2016/02/11/compromising-us-banks-third-party-code/
"通过第三方 JavaScript 脚本攻击银行用户: https://t.co/ncqWUJBlZg "
-

[ Web Security ] dvws : Damn Vulnerable Web Services (vulnerable testing environment) : https://github.com/snoopythesecuritydog/dvws https://t.co/yHtsrn6SIm
"dvws: Web 服务漏洞训练场, Github Repo: https://t.co/QK0eMniSLc "
-

[ Windows ] Deconstructing the Microsoft TLS Session Resumption bug : https://blog.cloudflare.com/microsoft-tls-downgrade-schannel-bug/
"剖析微软 TLS 会话恢复机制的 Bug, 来自 CloudFlare Blog: https://t.co/uxnEkf5Wc4"