腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Android Dynamic Binary Instrumentation tool for tracing Android native layer: http://ow.ly/Y4zUD
"ADBI - Android Native 层动态二进制插桩工具, Github Repo: https://t.co/H9kH9acqeS"
-

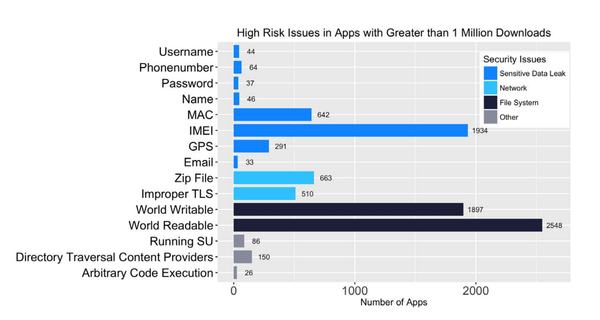
[ Android ] 2016 @ NowSecureMobile Mobile Security Report - [PDF] https://info.nowsecure.com/rs/201-XEW-873/images/2016-NowSecure-mobile-security-report.pdf https://t.co/vIXF8pD9kX
"来自 NowSecureMobile 的 2016 手机安全报告(PDF): https://t.co/K1NzSz8w6H https://t.co/vIXF8pD9kX"
-

[ Android ] User Beware: Rooting Malware Found in 3rd Party App Stores http://blog.trendmicro.com/trendlabs-security-intelligence/user-beware-rooting-malware-found-in-3rd-party-app-stores/
"Android 用户要小心第三方应用市场中的 Root 恶意软件, 来自 TrendMicro Blog: https://t.co/URAkkAJksE"
-

[ Android ] Unlocking the Motorola Bootloader with a TrustZone exploit : http://bits-please.blogspot.in/2016/02/unlocking-motorola-bootloader.html https://t.co/5qMW9VjEGs
"通过一个 TrustZone Exploit 解锁 Motorola Bootloader, 来自 Bits-Please Blog: https://t.co/k0X7pBsTTD https://t.co/5qMW9VjEGs"
-

[ Attack ] Poseidon Group: a Targeted Attack Boutique specializing in global cyber-espionage https://securelist.com/blog/research/73673/poseidon-group-a-targeted-attack-boutique-specializing-in-global-cyber-espionage/
"Poseidon - 一个专门从事全球网络间谍定向攻击行动的组织, 来自 Kaspersky Blog: https://t.co/Ivtj0axqcF"
-

[ Browser ] ZDI-16-165: Microsoft Edge Text Node Type Confusion Remote Code Execution Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-165/
"ZDI-16-165: Edge 浏览器 Text Node 类型混淆 RCE 漏洞, 来自 ZDI 的公告: https://t.co/ck1WbLcp9H"
-

[ Conference ] Major changes in Pwn2Own 2016: http://pastebin.com/Yt387wEn #Pwn2Own
"Pwn2Own 2016 的主要变化: https://t.co/3dy9sN2iPz #Pwn2Own"
-

[ Crypto ] On the conceit that any one nation can outlaw strong encryption or mandate exceptional access backdoors to software: https://www.schneier.com/cryptography/paperfiles/worldwide-survey-of-encryption-products.pdf
"从全球收集的 865 个软硬件加密产品的调查报告, 来自 Schneier: https://t.co/WUEMIvk7Z0"
-

[ Defend ] [White Paper] Learn how to rank your readiness in each of your core capabilities http://bddy.me/1QtUTix #DFIR https://t.co/M9guuQRnoO
"FireEye Mandiant 的报告 - 如何为应急响应做准备: https://t.co/AXLvFin6QC #DFIR https://t.co/M9guuQRnoO "
-

[ Exploit ] Post-Exploitation JavaScript -> Shellcode Exec POC Evade Whitelisting, AV and EMET http://subt0x10.blogspot.com/2016/02/javascript-office-shellcode-execution.html Feedback? Useful?Crazy?Just Dumb?
"Office Shellcode 执行的一段 JavaScript 脚本,可以逃逸白名单和杀软的检测: https://t.co/mCtoGHKKyU "
-

[ MalwareAnalysis ] njRat Trojan Alive and Kicking. A Cool Overview Into its Day to Day Operations https://www.threatstream.com/blog/njrat-trojan-alive-and-kicking.-a-cool-overview-into-its-day-to-day-operations#When:13:00:00Z
"njRat - ThreatStream 从地域、版本、时间的角度对最近遇到的 njRat 木马样本的分析: https://t.co/PMwNmnND7a"
-

[ MalwareAnalysis ] Angler EK leads to fileless Gootkit http://www.cyphort.com/angler-ek-leads-to-fileless-gootkit/
"Angler EK 分发无文件型 Gootkit 恶意软件, 详细的感染过程: https://t.co/H90ZUO7FUp"
-

[ MalwareAnalysis ] Hydracrypt Ransomware https://reaqta.com/2016/02/hydracrypt-ransomware/
"Hydracrypt 勒索软件分析, 来自 REAQTA Blog: https://t.co/fA6bAZaeTw "
-

[ Network ] Securing a DNS server with Snort IDS http://www.theseus.fi/bitstream/handle/10024/98458/Drozdova_Thesis%20work.pdf?sequence=1
"用 Snort IDS 加固 DNS 服务器, Paper: https://t.co/PsoO8ESMpv"
-

[ Network ] If you are following along with our talk at #sas2016, here's our example on Turla SSL certificate chains. http://blog.passivetotal.org/harnessing-ssl-certificates-using-infrastructure-chaining/
"通过基础设施链关系加固 SSL 证书, 来自 PassiveTotal Blog: https://t.co/m47iTfsFMT"
-

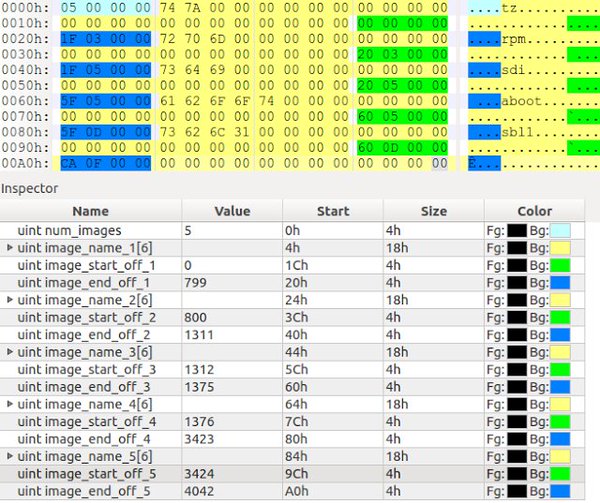
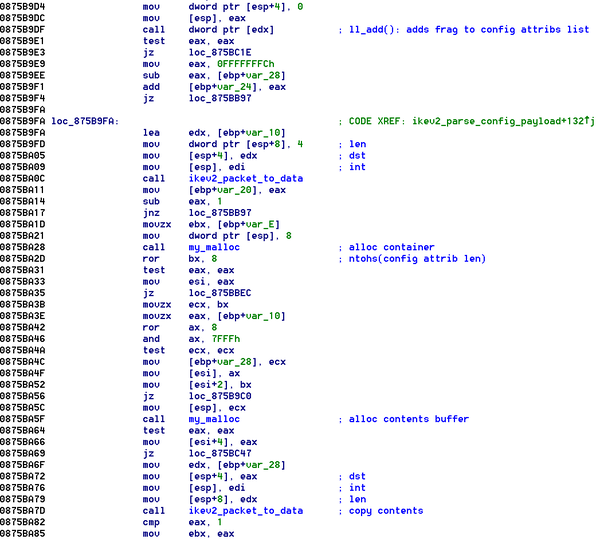
[ NetworkDevice ] Technical writeup of CVE-2016-1287 [Cisco ASA Software IKEv1 & IKEv2 Buffer Overflow Vuln] : https://blog.exodusintel.com/2016/01/26/firewall-hacking/ https://t.co/nWpHzBigul
"CVE-2016-1287 Cisco ASA IKEv1 & IKEv2 缓冲区溢出漏洞利用 - Execute My Packet, 来自 ExodusIntel Blog: https://t.co/YZMkBxNcCm https://t.co/nWpHzBigul"
-

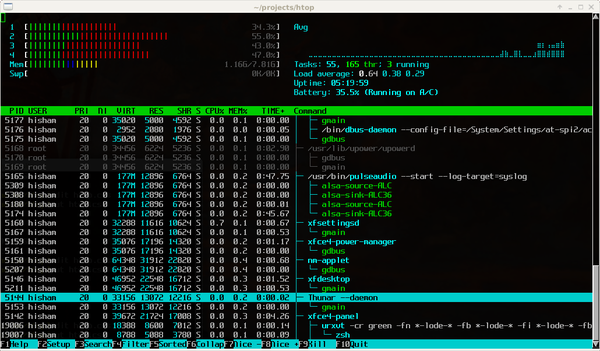
[ Others ] htop - an interactive process viewer for Linux, FreeBSD, OpenBSD and Mac OS X : http://hisham.hm/htop/ https://t.co/by9c47aYrA
"htop - 交互式进程查看器, 支持 Linux,FreeBSD,OpenBSD 和 Mac OS X: https://t.co/Kyaq0jzNDg https://t.co/by9c47aYrA"
-

[ Tools ] Network Minor 2.0 released ~SMB/CIFS parser now supports file extraction from SMB write operations. http://www.netresec.com/?page=Blog&month=2016-02&post=NetworkMiner-2-0-Released
"Network Minor 2.0 版本开始支持从 SMB 写操作中提取文件了: https://t.co/rbokeEteSr"
-

[ Vulnerability ] Understanding IE 11 CVE-2015-2419 Exploitation : http://blog.checkpoint.com/2016/02/10/too-much-freedom-is-dangerous-understanding-ie-11-cve-2015-2419-exploitation/
"过多的自由是一种危险 - IE11 CVE-2015-2419 漏洞利用分析, 来自 CheckPoint Blog: https://t.co/EhQBpggAnQ"
-

[ Web Security ] The Most Forgotten Web Vulnerabilities : https://www.exploit-db.com/docs/39434.pdf (pdf)
"那些最容易被遗忘的 Web 漏洞, 来自 Exploit-DB 的 Paper: https://t.co/3VJvgGskSK "
-

[ Windows ] [POC-Writeup] Defeating FDE (BitLocker) through Windows Authentication Bypass http://bgcd.co/1TVsYh9 by @ tgilis https://t.co/1zTFjgFbWH
"在一个全盘加密的系统中从 0 到 SYSTEM, Blog: https://t.co/2pS2YiTec8 "
-

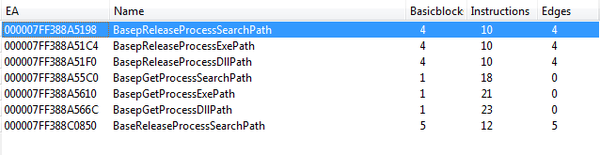
[ Windows ] Kernelbase.dll 6.1.7601.19131 from MS16-014 adds new DLL Loading Security #infosec #RE #PatchTuesday https://t.co/QmPkDzqT7p
"Kernelbase.dll 6.1.7601.19131 在 MS16-014 补丁中新添加了一个 DLL 加载安全特性, 相关的 API 如下图"