腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Announcing cargo-apk - cross compiling to android just got significantly easier! https://users.rust-lang.org/t/announcing-cargo-apk/5501
"cargo-apk - 从 Rust 交叉编译成 APK: https://t.co/BH5beFpQZ8"
-

[ Attack ] Lottery security director hacked random-number generator to rig lotteries http://securityaffairs.co/wordpress/46400/cyber-crime/security-director-hacked-lottery.html
"彩票安全主管黑掉随机数生成器操纵彩票: https://t.co/VpuVxyMFDq"
-

[ Browser ] Using a Braun Shaver to Bypass XSS Audit and WAF https://blog.bugcrowd.com/guest-blog-using-a-braun-shaver-to-bypass-xss-audit-and-waf-by-frans-rosen-detectify
"通过 Amazon 上的智能剃须刀链接,构造特殊的 URL,绕过 XSS Auditor 和 WAF: https://t.co/G7otdb0qrr "
-

[ Debug ] PwnDbg by @ ebeip90 is now using Unicorn inside for code emulation! https://github.com/zachriggle/pwndbg
"PwnDbg - 优化 GDB 调试的体验, 有很多与 PEDA 相似的功能: https://t.co/jylNfDtBMP"
-

[ Detect ] MIT builds Artificial Intelligence system that can detect 85% of Cyber Attacks ~ http://thehackernews.com/2016/04/artificial-intelligence-cyber-security.html #Security
"MIT 开发了一套人工智能系统,该系统可以检测到 85% 的网络攻击: https://t.co/Nfj7C2K9ZZ "
-

[ Detect ] Another interesting #malware tracker: http://tracker.h3x.eu/
"Malware Tracker - 一个跟踪恶意软件的网站︰ https://t.co/uYsNMZdHhh"
-

[ Detect ] Blocking #ransomware POC using mini-filter driver & honeyTokens https://github.com/ofercas/ransomware_begone
"ransomware_begone - 勒索软件阻断工具,基于 Mini-filter 和 honeyTokens,在勒索软件尝试加密文件的早期阶段阻断它, Github Repo: https://t.co/h2qggNyJZI"
-

[ Fuzzing ] PyExZ3 - symbolic execution engine for Python, now using the Z3 theorem prover https://github.com/thomasjball/PyExZ3/ Paper http://research.microsoft.com/pubs/233035/dse.pdf
"PyExZ3 - 基于 Z3 的符号执行引擎: https://t.co/QLU1HTObaj 来自微软的 Paper: https://t.co/ZFYA8BHoWV"
-

[ IoTDevice ] Jailbreaking the Microsoft fitness band http://www.b0n0n.com/2016/04/20/ms-jailbreak/
"越狱微软的健身手环: https://t.co/1DRV9j5Cjt"
-

[ Mac OS X ] Happy 4/20! New tool aims for generic ransomware detection: https://objective-see.com/products/ransomwhere.html. In-depth technical/R&D details: https://objective-see.com/blog/blog_0x0F.html
"RansomWhere - OS X 勒索软件通用检测工具︰ https://t.co/9knYTKLTky 深入的技术分析 ︰ https://t.co/iv3vsBgvh6"
-

[ Malware ] Dissecting a spammer’s spam script, spammers abuse known flaws https://jelleraaijmakers.nl/2016/04/dissecting-spammers-spam-script
"剖析一段用于发送垃圾邮件的 PHP 脚本: https://t.co/wqvLmyQ110"
-

[ Malware ] Writeup on TeslaCrypt Propagation, Evasion, Encryption, and Persistence Techniques https://www.endgame.com/blog/your-package-has-been-successfully-encrypted-teslacrypt-41a-and-malware-attack-chain
"TeslaCrypt 勒索软件 4.1A 版本的传播、逃逸、加密过程分析: https://t.co/1AvFWpn5Ox "
-

[ Malware ] Threat Spotlight: Exploit Kit Goes International Hits 150+ Countries http://blog.talosintel.com/2016/04/nuclear-exposed.html
"Exploit Kits 走国际化路线, 150+ 个国家受到它的攻击, 来自 Talos Blog: https://t.co/hdwUFWI1cJ"
-

[ Malware ] Ransomware Overview : Names, extensions, patterns, decryptors list along w/ screenshots : https://docs.google.com/spreadsheets/d/1TWS238xacAto-fLKh1n5uTsdijWdCEsGIM0Y0Hvmc5g/edit#gid=0
"知名勒索软件概览︰包括名称、 扩展名、 扩展名正则模式、 解密工具,有的还有截屏,来自 Google Drive ︰ https://t.co/2krftHe9Aa"
-

[ Malware ] Nemucod meets 7-Zip to launch #ransomware attacks: https://rqt.io/1i https://t.co/bb7phL63cT
"Nemucod JavaScript 下载器下载伪装成 7-Zip 的勒索软件︰ https://t.co/897BN0PzmS https://t.co/bb7phL63cT"
-

[ Malware ] PoS Malware Steals Credit Card Numbers via DNS Requests http://ow.ly/4mU5kZ
"PoS 恶意软件通过 DNS 请求向攻击者发送偷来的信用卡信息: https://t.co/WXvGzl4N04 来自 FireEye 的分析中,将此 POS 恶意软件家族称为 MULTIGRAIN,详细的分析报告: https://www.fireeye.com/blog/threat-research/2016/04/multigrain_pointo.html "
-

[ Malware ] New Thanatos Trojan Can Delete Competing Malware from the Infected Target http://news.softpedia.com/news/new-thanatos-trojan-can-delete-competing-malware-from-the-infected-target-503163.shtml
"新木马 Thanatos 会删掉受感染电脑上的其他恶意软件: https://t.co/z3v5EutHde 据报道这类黑吃黑恶意软件的数量在上升: http://venturebeat.com/2016/04/16/rise-of-the-malware-hunting-malware/ "
-

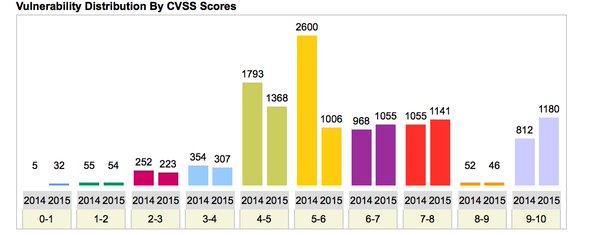
[ Others ] Using the National Vulnerability Database to Reveal Trends - A guest blog by @ realinfosec: https://community.rapid7.com/community/infosec/blog/2016/04/20/using-the-national-vunerability-database-to-reveal-vulnerability-trends-over-time https://t.co/PmjYZx0gbw
"利用 NVD 漏洞库总结漏洞发展趋势, 来自 Rapid7 Blog ︰ https://t.co/M422JwhRHK https://t.co/PmjYZx0gbw"
-

[ Others ] Viber adds End-to-End Encryption and PIN protected Hidden Chats features http://ow.ly/4mSW2i
"即时通讯工具 Viber 加入端到端加密支持, 以及 PIN 保护的隐藏式聊天功能: https://t.co/i3ScQBtz5Y"
-

[ Others ] Emulating a USB Mouse with mbed to Cheat at CookieClicker · http://jcjc-dev.com/2014/01/10/emulating-a-USB-mouse-with-mbed-to-cheat-at-cookieclicker/
"基于 mbed IoT 开发平台,模拟 USB 鼠标设备,在 CookieClicker 游戏中作弊: https://t.co/0Y6JF6tMer"
-

[ Others ] 136 vulns patched in Oracle update. Remote exec across product line: JVM, Java SE, database, core middleware, ERP… http://www.oracle.com/technetwork/security-advisory/cpuapr2016v3-2985753.html
" Oracle 发布 4 月份补丁更新,本次共修复了 136 个漏洞: https://t.co/eBTHbYXBJT"
-

[ Others ] Secure boot checkup utility - http://apps.insyde.com/sbutil.html plus an interesting base intro on uefi and secure boot
"Windows 8 UEFI 安全启动特性状态检查工具: https://t.co/20yFtQrAW9 "
-

[ Others ] ARM Architecture Reference Manual : https://www.scss.tcd.ie/~waldroj/3d1/arm_arm.pdf (pdf)
"ARM 体系结构参考手册 ︰ https://t.co/XGEgEuS4Yj "
-

[ Others ] Build Your Own Botnet : https://www.sans.org/reading-room/whitepapers/threats/byob-build-botnet-33729 (pdf)
"构建属于你自己的僵尸网络 (PDF)︰ https://t.co/DGfOaDnDag "
-

[ Others ] Understanding and Hardening Linux Containers by @ NCCGroupInfosec https://www.nccgroup.trust/globalassets/our-research/us/whitepapers/2016/april/ncc_group_understanding_hardening_linux_containers-10pdf/ (122 pages of container security)
"了解并加固 Linux Containers, 来自 NCC Group: https://t.co/qCzNUI2itX "
-

[ Others ] How I hunted the most odd ruby bug : http://blog.arkency.com/2016/04/how-i-hunted-the-most-odd-ruby-bug/
"我是如何找到 Ruby 最古怪的这个 Bug 的: https://t.co/bgPmzf0Y1Q"
-

[ Pentest ] My pentesting war story from @ NCCGroupplc #NCCcon to get domain creds from @ albinowax web app Excel export tricks http://www.exploresecurity.com/from-csv-to-cmd-to-qwerty/
"关于渗透的一个小故事: 从 CSV 到 CMD 命令行, 再从 CMD 到键盘: https://t.co/H0P1UoUvQw"
-

[ Popular Software ] Oracle OIT Image Export SDK libvs_pdf XRef Index Code Execution Vulnerability http://blog.talosintel.com/2016/04/oracle-oit-image-export-sdk-libvspdf.html
"Oracle OIT 图像导出 SDK 在解析 PDF 文档时存在代码执行漏洞, 来自 Talos Blog: https://t.co/cHCRw49kbB"
-

[ ReverseEngineering ] Reversing a Finite Field Multiplication Optimization http://blog.quarkslab.com/reversing-a-finite-field-multiplication-optimization.html
"逆向有限域乘法优化: https://t.co/d0A04zc0IL"
-

[ SecurityProduct ] Symantec Messaging Gateway Flaws Let Local Users Obtain and Decrypt Passwords and Execute Arbitrary Shell Commands.. http://www.securitytracker.com/id/1035609
"Symantec 消息网关 10.6.0-7 之前版本存在两个漏洞,本地用户可以获取并解密目标系统的密码,而且可以执行任意 Shell 命令: https://t.co/2tHkaauqqq"
-

[ Tools ] TLS-Attacker : A Java-based framework for analyzing TLS libraries : https://github.com/RUB-NDS/TLS-Attacker
"TLS-Attacker - 用于分析 TLS 库安全性的 Java 框架 ︰ https://t.co/7ahmcWcuEf"
-

[ Tools ] sk3wldbg : Debugger plugin for IDA Pro backed by the Unicorn Engine : https://github.com/cseagle/sk3wldbg
"sk3wldbg: IDA Pro 的调试器插件, 基于 Unicorn 反汇编引擎 ︰ https://t.co/ux0LEPhsFW"
-

[ Windows ] Windows Kernel DrawMenuBarTemp Wild Write https://packetstormsecurity.com/files/136738/GS20160419233516.tgz
"Windows 内核 DrawMenuBarTemp 未映射内存写漏洞(x64), 在 32 位 Windows 7 可以触发空指针读操作。 来自 Project Zero Issue 707: https://bugs.chromium.org/p/project-zero/issues/detail?id=707 "
-

[ Windows ] Blog @ sjenninglinux "Running Fedora on Windows 10 using WSL" https://www.variantweb.net/blog/running-fedora-on-windows-10-using-wsl/ https://youtu.be/YHfQgEuMzfI
"在 Windows 10 系统上运行 Fedora: https://t.co/8N1SfcF1fN Youtube 视频: https://t.co/Dohapdtoyk"
-

[ Windows ] Looking Caves in Windows Executables http://marcoramilli.blogspot.com/2016/04/looking-caves-in-windows-executables.html
"在 Windows 可执行文件中找 Code Caves(代码空白区): https://t.co/y0xmxLgijR "