腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Android Security Report: 29 Percent of Active Devices Not Up To Patch Levels: https://threatpost.com/android-security-report-29-percent-of-active-devices-not-up-to-patch-levels/117511/ via @ threatpost
"Google 发布 Android 安全年度报告(2015), 来自 ThreatPost 的报道: https://t.co/DxsRTGnBIE 报告下载: http://source.android.com/security/reports/Google_Android_Security_2015_Report_Final.pdf "
-

[ Android ] Fun! Open sourced CVE-2015-1805 for some Android devices (mainly Sony) https://github.com/dosomder/iovyroot
"iovyroot - 基于 CVE-2015-1805 漏洞的 Android Root 工具: https://t.co/M5svW17mGu"
-

[ Android ] Booting Android: bootloaders, fastboot and boot images - http://www.slideshare.net/chrissimmonds/android-bootslides20
"Android 系统的引导过程︰ bootloaders, fastboot, boot images: https://t.co/f19jk42xAb"
-

[ Attack ] IBM warns a spike in the number of PHP C99 Webshell Attacks http://securityaffairs.co/wordpress/46449/hacking/c99-webshell-attacks.html
"IBM 警告称 PHP C99 Webshell 变种攻击数量出现顶峰: https://t.co/duai93RkPU "
-

[ Attack ] APT Targeting Tibetans Packs Four Vulnerabilities in One Compromise: https://threatpost.com/apt-targeting-tibetans-packs-four-vulnerabilities-in-one-compromise/117493/ via @ threatpost
"据 Arbor Networks 发现, 在针对藏._族的 APT 攻击行动中, 攻击者一次使用了 4 个 RTF 的漏洞(CVE-2012-0158, CVE-2012-1856, CVE-2015-1641, CVE-2015-1770), 来自 ThreatPost 的报道: https://t.co/SsIFwAwcYk 来自 Arbor 的报告: https://www.arbornetworks.com/blog/asert/wp-content/uploads/2016/04/ASERT-Threat-Intelligence-Report-2016-03-The-Four-Element-Sword-Engagement.pdf "
-

[ Browser ] Chrome XSS Bypass http://brutelogic.com.br/blog/chrome-xss-bypass/
"Chrome XSS Auditor Bypass,来自 Brutelogic Blog: https://t.co/KGY6mTebN8"
-

[ Browser ] Bypassing Browser Memory Protections : https://www.trailofbits.com/resources/bypassing_browser_memory_protections_vista_paper.pdf (pdf)
"绕过浏览器的内存保护机制,来自 08 年的一篇总结性 Paper,作者为 Alexander Sotirov 和 Mark Dowd ︰ https://t.co/mRli4O7JR6 "
-

[ Challenges ] My v8 exploit for #plaidctf's js_sandbox challenge: https://gist.github.com/sroettger/d077d3907999aaa0f89d11d956b438ea
"plaidctf 的 js_sandbox 题的 Exploit ︰ https://t.co/M8vFlooGCg"
-

[ Debug ] New post from @ _samdb_ on WinDbg scripting with python and Windows heap tracing https://labs.mwrinfosecurity.com/blog/heap-tracing-with-windbg-and-python/ https://t.co/8pcxzepzJX
"如何通过 WinDbg 的 Python 扩展(pykd)跟踪 Windows 进程堆的使用: https://t.co/msqJ775MbI https://t.co/8pcxzepzJX "
-

[ Exploit ] I made a new SMEP bypass for DSE bypass lib, now it works fine from Hyper-V partition: https://github.com/Cr4sh/fwexpl/commit/a170ca27baf666dd7799b7c3f39a373119ec7f31 https://twitter.com/d_olex/status/696126803820175360
"固件漏洞利用框架 fwexpl 新添加了一个 SMEP Bypass 技巧, 可以绕过 DSE(驱动签名强制检查)︰ https://t.co/ISZrOEKVB0 https://t.co/BpHqtbusJt"
-

[ Hardware ] X1 Carbon 4th gen has a hidden new feature: a case intrusion detection switch with BIOS hooks to clear TPM keys. https://t.co/KnH9b0ydfT
"ThinkPad X1 Carbon 第 4 代笔记本有一个隐藏的新功能︰ 有一个入侵检测开关,可以清空 TPM 密钥: https://t.co/KnH9b0ydfT"
-

[ Industry News ] FireEye extends Threat Analytics Platform capabilities to @ awscloud Lambda service http://bddy.me/1XGo5Z2 #cloudsecurity #infosec
"FireEye 与 亚马逊云 Lambda 服务平台合作,提供公有云上的高级威胁检测分析: https://t.co/cd9Tsbo4nS "
-

[ iOS ] Uploaded my iOS of Sauron: How iOS Tracks Everything You Do presentation from @ BSidesNOLA https://github.com/mac4n6/Presentations/blob/master/iOS%20of%20Sauron%20-%20How%20iOS%20Tracks%20Everything%20You%20Do/iOS_of_Sauron_04162016.pdf #mac4n6 #DFIR
"iOS 是如何跟踪你做的每一件事的,来自 BSidesNOLA 会议: https://t.co/J9TPsk7xN3 "
-

[ Linux ] Detecting the use of "curl | bash" server side : https://www.idontplaydarts.com/2016/04/detecting-curl-pipe-bash-server-side/
"检测服务器上 'curl | bash' 管道传递 Payload 命令的使用 ︰ https://t.co/sDmnQojC2F"
-

[ Malware ] Drive-by Ransomware Infection in the Wild http://www.cyphort.com/drive-by-ransomware-infection-in-the-wild/
"Cyphort 最近监测到一些受 Angler EK 攻击的网站会传播勒索软件: https://t.co/MT8F6LdtGo"
-

[ Malware ] Let's Analyze: Dridex (Part 2) http://www.malwaretech.com/2016/04/lets-analyze-dridex-part-2.html
"MalwareTech Blog 对 Dridex 的分析 (Part 2): https://t.co/dNmwn8Fjvg"
-

[ Malware ] #Unit42 discovers #Python-based malware #PWOBot targeting European organizations http://bit.ly/1rdOaoi
"Palo Alto 最近捕获到了一个纯 Python 编写的恶意代码家族样本 - PWOBot, 该家族的攻击目标为欧洲的一些组织: https://t.co/o9iuHgQy9J"
-

[ Malware ] Kovter Ad Fraud Trojan Evolves Into Ransomware | http://SecurityWeek.Com http://ow.ly/4mQAWj
"Kovter 广告欺诈软件演变成勒索软件, 来自 SecurityWeek 的报道: https://t.co/hL4kPemmTi 来自 CheckPoint 的分析: http://blog.checkpoint.com/2016/04/15/kovter-ransomware-the-evolution-from-police-scareware-to-click-frauds-and-then-to-ransomware/ "
-

[ Malware ] Godzilla Loader | A tiny loader that uses the ATL control hosting API to download a payload http://www.kernelmode.info/forum/viewtopic.php?f=16&t=4327 #Malware #GodzillaLoader
"Godzilla 恶意软件下载器分析,来自 KernelMode 论坛: https://t.co/oEIPD5qtpD "
-

[ Network ] How To Prepare For A DDoS Attack: 10 Steps http://ow.ly/4mQ4ti
"为一次 DDoS 攻击做防御准备的 10 个步骤(10 张图): https://t.co/JrzMOlBPj9"
-

[ Network ] I've released Assetnote for the bug bounty community to assist in the monitoring of passive DNS data - more here: https://github.com/infosec-au/assetnote
"assetnote - 被动 DNS 数据监控通知推送工具, 可以监控新域名的出现 ︰ https://t.co/mR5wW36g8P"
-

[ Network ] How to trick traffic sensors - Securelist http://ow.ly/4mQATg
"如何欺骗交通流量传感器, 来自 Kaspersky Blog: https://t.co/bdRj98Oma0"
-

[ Obfuscation ] Combining learning with fuzzing for software deobfuscation [PDF, masters thesis] http://repository.tudelft.nl/assets/uuid:6282cd05-6ae3-4f39-adc7-1a45efe1ccce/thesis-combining-learning-with-fuzzing-for-software-deobfuscation.pdf
"软件 Fuzz 与代码混淆, 来自荷兰一所大学的 Paper: https://t.co/o20jEGufAk"
-

[ Others ] JavaScript-toting spam emails: What should you know and how to avoid them? https://blogs.technet.microsoft.com/mmpc/2016/04/18/javascript-toting-spam-emails-what-should-you-know-and-how-to-avoid-them/
"携带 JavaScript 附件的垃圾邮件, 你应该了解的事儿以及如何防御, 来自微软 Blog: https://t.co/S44Gg4DJG3"
-

[ Others ] Hyper-V bugs details released -- https://bugs.chromium.org/p/project-zero/issues/detail?id=688 https://bugs.chromium.org/p/project-zero/issues/detail?id=689 https://bugs.chromium.org/p/project-zero/issues/detail?id=690
"Hyper-V 可以从 Guest 影响 Host 机的 3 个漏洞, Project Issue 688: https://t.co/lU4zEBJXQA Issue 689: https://t.co/mcgcZAUHcD Issue 690: https://t.co/LAeBRAhFXH"
-

[ Others ] Creating a JVM language (a series of 11 blogposts): http://jakubdziworski.github.io/categories.html#Enkel-ref
"《构建 JVM 语言》系列文章(共 11 篇)︰ https://t.co/OtAF4NIoE4"
-

[ Others ] Towards Vulnerability Discovery Using Staged Program Analysis http://arxiv.org/abs/1508.04627
"以漏洞挖掘为目的的分阶段程序分析, Paper: https://t.co/zYDLuI3FXM"
-

[ Others ] Fuzzing @ capstone_engine with LibFuzzer detected this issue in x86_64 affecting 3.0.4 https://github.com/aquynh/capstone/commit/6b88d1d51eadf7175a8f8a11b690684443b11359
"LibFuzzer 在 Fuzz capstone_engine 反汇编引擎时发现了一个 x86_64 指令处理的 Bug, 影响 3.0.4 版本: https://t.co/gFd00m4SdN"
-

[ Pentest ] Recon-ng – Web Reconnaissance Framework http://www.darknet.org.uk/2016/04/recon-ng-web-reconnaissance-framework/
"Recon-ng — Web 信息探测框架: https://t.co/w77T923Bpd"
-

[ SecurityProduct ] Escaping The Avast Sandbox Using A Single IOCTL CVE-2016-4025 https://www.nettitude.co.uk/escaping-avast-sandbox-using-single-ioctl-cve-2016-4025/
"仅用一个简单的 IOCTL 漏洞逃逸 Avast 的沙盒保护(CVE-2016-4025): https://t.co/EtNghMfztE"
-

[ Tools ] Multiple RCE in Veil-Evasion RPC https://blog.cylance.com/veil-evasion-vulnerability-discovered-by-cylance
"Veil-Evasion 是一个用于逃逸传统杀软的 Payload 生成器, Cylance 的研究员在 Veil-Evasion 框架本身发现了多个 RCE 漏洞: https://t.co/LFxBXrFrkR"
-

[ Web Security ] $5k for a bug that a scanner can easily find... https://hackerone.com/reports/122475
"Imgur 奖励一个路径穿越漏洞(../../) 5k 刀: https://t.co/JwC5eCGe4H "
-

[ Windows ] Proof Of Concept #PowerShell Server / JavaScript Reverse HTTP Shell https://gist.github.com/subTee/24c7d8e1ff0f5602092f58cbb3f7d302#file-jsrat-ps1 Rough Draft. Take it for a spin. Feedback?
"PowerShell Server + JavaScript HTTP 反弹 Shell 的 PoC 代码,作者为 subTee: https://t.co/s2rY99Lj1R "
-

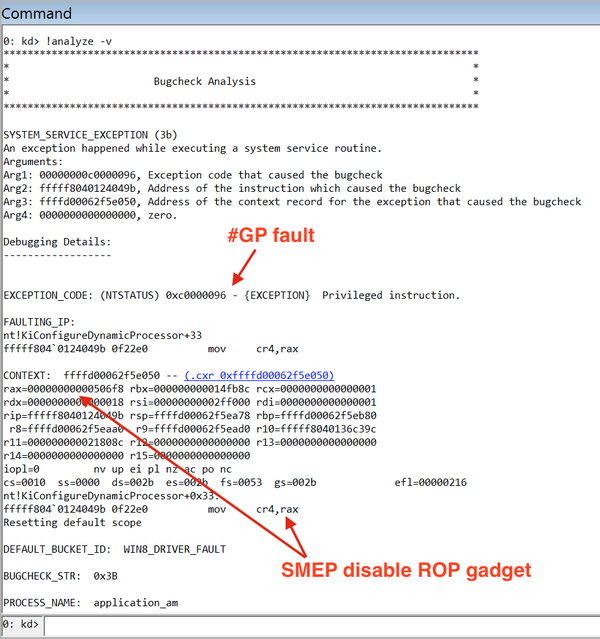
[ Windows ] Interesting: you can’t disable SMEP on Windows 10 with hyper-v because it protects CR4 register of root partition https://t.co/Gyfu5P2xsL
"Windows 10 系统无法在 Hyper-V 中禁用 SMEP,因为它保护了根分区的 CR4 寄存器: https://t.co/Gyfu5P2xsL"