腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] For a given Android vulnerability (i.e. #Stagefright), @ opensignal's fragmentation data is helpful to gauge risk: http://opensignal.com/reports/2015/08/android-fragmentation/.
"如果想评估一个 Android 漏洞的影响, OpenSignal 公司的这些 Android 数据可以帮助你 ︰ https://t.co/KrW6V0ZbE4。"
-

[ Android ] LG officially opens the European LG G5 H850 bootloader http://forum.xda-developers.com/lg-g5/development/official-european-lg-g5-h850-bootloader-t3363040
"LG 官方发布解锁 G5 H850 手机 Bootloader 的工具: https://t.co/MADc3WOXbr"
-

[ Attack ] Fake Social Button Plugin Redirects to Angler EK | Malwarebytes Labs http://ow.ly/4mWn7Q
"假社交网络插件会将用户重定向到 Angler EK 网站, 来自 Malwarebytes Blog: https://t.co/8Gp5iQGmVq"
-

[ Browser ] Malware - Analysing and Repurposing Spartan's CVE-2015-7645 http://vulnerablespace.blogspot.co.uk/2016/04/malware-analysing-and-repurposing.html
"Spartan CVE-2015-7645 漏洞分析和再利用: https://t.co/HEKJPENYBM"
-

[ Detect ] The problem with conflating #APT indicators of compromise with observables - new @ threatpost Op-Ed: https://threatpost.com/misunderstanding-indicators-of-compromise/117560/ via
"对 IOC 的误解, 来自 ThreatPost Blog: https://t.co/76lialxOs4"
-

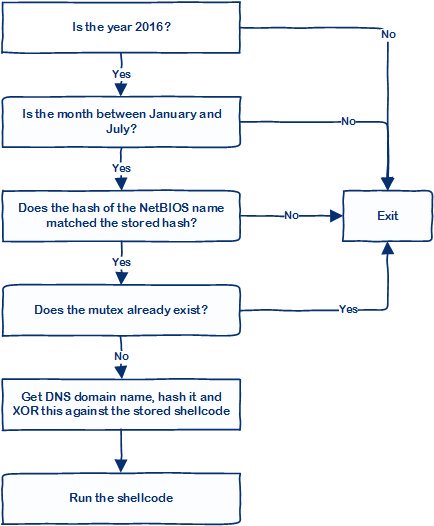
[ Exploit ] New post from @ ukstufus on creating safer implants with environmentally keyed shellcode https://labs.mwrinfosecurity.com/blog/safer-shellcode-implants/ https://t.co/q5Vv8naAdE
"为远控植入的 Shellcode 代码添加环境检查功能,包括:是否第一次执行、是否在指定机器上运行、某个时间点后是否运行过等,来自 MWR Labs: https://t.co/oeUazgeDaA https://t.co/q5Vv8naAdE ; "
-

[ Firmware ] Intel Releases the Arduino 101 Source Code : https://blog.arduino.cc/2016/04/21/intel-releases-the-arduino-101-firmware-source-code/ ; Download : https://downloadcenter.intel.com/download/25832
"英特尔发布了 Arduino 101 开发板的固件源码, Blog ︰ https://t.co/isITk0IbQj 源码下载︰ https://t.co/9iMWYXvtE0"
-

[ Hardware ] JTAGulator ($200) vs. JTAGenum ($3)... Hardware Hacking Tools for Identifying JTAG Pins in #IoT Devices https://www.praetorian.com/blog/jtagulator-vs-jtagenum-tools-for-identifying-jtag-pins-in-iot-devices
"JTAGulator vs JTAGenum - 用于识别 JTAG 引脚的工具: https://t.co/Or1K4vj7Sf "
-

[ Hardware ] #rowhammer 3.0 w/o CLFLUSH via popular libraries like glibc http://arstechnica.com/security/2016/04/dram-bitflipping-exploits-that-hijack-computers-just-got-easier/ [see paper https://twitter.com/daniel_bilar/status/720897816453849088 ]
"rowhammer 3.0: 不依赖 CLFLUSH 在流行的代码库(如 glibc)中实现位反转, 来自 ArsTechnica 的报道: https://t.co/SzGalgtFi3 Paper: https://t.co/2r7b832PIE https://t.co/lYl8eHrWlz http://t.co/2jfnJbTIZA "
-

[ Industry News ] #SpyEye creators sentenced to 24 years in prison: http://bit.ly/1r8OZi2 #infosec #malware https://t.co/DmzW0F76mD
"SpyEye 的作者被判处有期徒刑 24 年︰ https://t.co/qIic0KfFx1 https://t.co/DmzW0F76mD"
-

[ Linux ] NGS : Next generation UNIX shell : https://github.com/ilyash/ngs/
"NGS ︰ 下一代 UNIX Shell ︰ https://t.co/QPxouhvh1D"
-

[ Malware ] Panda Banker: New Banking Trojan Hits the Market | Proofpoint http://ow.ly/4mWoGl
"新款银行木马 Panda 分析, 来自 Proofpoint Blog: https://t.co/QcCqX35wNT"
-

[ MalwareAnalysis ] New Blog Post out: Nymaim - evading Sandboxes with API hammering: http://joe4security.blogspot.ch/2016/04/nymaim-evading-sandboxes-with-api.html #DFIR #ANTISANDBOX https://t.co/TDttZE6Yai
"Nymaim 家族样本通过 API Hammering 方式绕过沙盒检测, API Hammering 指:通过在循环中不断调用正常 API,消耗大量资源,造成沙箱检测的超时︰ https://t.co/qAdYC2Smih https://t.co/TDttZE6Yai"
-

[ MalwareAnalysis ] r2-ropstats - A set of tools based on radare2 for analysis of ROP gadgets and payloads.. https://github.com/shaded-enmity/r2-ropstats
"r2-ropstats - 基于 radare2 框架、用于分析 ROP Gadgets 和 Payloads 的工具: https://t.co/tuOpNgK1JE"
-

[ MalwareAnalysis ] Obfuscation code localization based on CFG generation of malware http://www.jaist.ac.jp/~mizuhito/papers/conference/FPS15.pdf
"基于恶意软件的控制流图(CFG),定位混淆代码,越南胡志明市大学与日本高级科学技术研究所合作研究的 Paper: https://t.co/elRbm9tVXY "
-

[ OpenSourceProject ] CVE-2016-3074: libgd: signedness vulnerability http://goo.gl/fb/rGtkwc #FullDisclosure
"CVE-2016-3074: 开源图像库 libgd 整数符号处理时存在漏洞: https://t.co/9lYmbrtFyr "
-

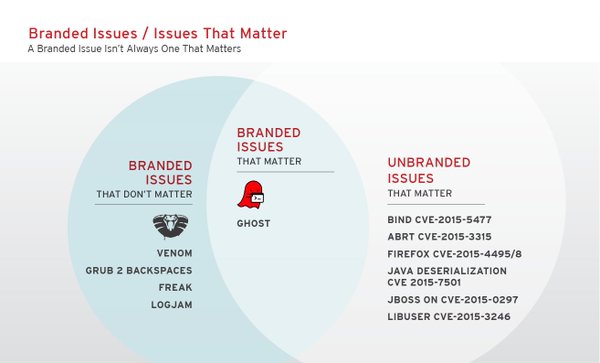
[ Others ] "Red Hat Product Security Risk Report: 2015” https://access.redhat.com/blogs/766093/posts/2262281 Good take: branded issues / issues that matter. https://t.co/NLhuiEJszw
"Red Hat 产品安全风险报告(2015): https://t.co/dVDaHYCwTq https://t.co/NLhuiEJszw"
-

[ Others ] I just came across this 7 yo work, a backdoored pci Ethernet card, I presented at LaCon'09 #hardware #hacking http://www.slideshare.net/wintercorelabs/meth-man-in-the-middle-ethernet
"M-ETH - 以太网卡中的中间人攻击, 来自 2009 年的演讲: https://t.co/fLCMkGaHk7"
-

[ Others ] Follow The Money: Dissecting the Operations of the Cyber Crime Group FIN6 « Threat Research Blog | FireEye Inc http://ow.ly/4mWo2V
"跟着钱走 - 网络犯罪组织 FIN6 追踪分析: https://t.co/jAWLHUh5AI"
-

[ Pentest ] 千呼萬喚始出來XD How I Hacked Facebook, and Found Someone's Backdoor Script 再找個 Google 的 RCE 就可以把各大公司的 RCE 系列給蒐集全了XD http://blog.orange.tw/2016/04/bug-bounty-how-i-hacked-facebook-and-found-someones-backdoor-script.html
"我是如何黑掉 Facebook 并在其中发现其他人的后门脚本的: https://t.co/5Hq6t4Ku1U 中文版: http://devco.re/blog/2016/04/21/how-I-hacked-facebook-and-found-someones-backdoor-script/ "
-

[ Pentest ] Check out "Teaching an old RAT new tricks" http://bit.ly/1QqbJOI. Researchers analyzed a new memory-only deployment method, very stealthy
"纯内存执行、不创建文件的 RAT 远控技巧: https://t.co/HHmxJkojlc "
-

[ Popular Software ] Lansweeper 5 SQL injection and weak credential storage lead to domain-admin password recovery! http://blog.gosecure.ca/2016/04/21/your-credentials-at-risk-with-lansweeper-5/
"Lansweeper 5 存在 SQL 注入和弱密码存储漏洞,可以还原管理员密码: https://t.co/npfqTpEhqI"
-

[ ReverseEngineering ] Reversing the Pepakura File Format https://github.com/daeken/PepakuraReverse
"逆向 Pepakura 3 文件格式, Pepakura 是个将 3D 模型转换成可打印文本的工具: https://t.co/94GrfnyIDx"
-

[ ReverseEngineering ] Slides: "Python Arsenal for Reverse Engineering" http://dsec.ru/upload/medialibrary/7d5/7d5e8a49b25b285b37800480a41583f8.pdf
"逆向工程 Python 兵器库: https://t.co/ReGPRJyeqa"
-

[ ReverseEngineering ] Pyflirt is a nice tool using Capstone & FLIRT signatures to detect lib functions in OllyDbg: https://github.com/mokhdzanifaeq/pyflirt https://t.co/tWUOBZl15I
"Pyflirt - 基于 Capstone 引擎和 FLIRT 规则,识别 Ollydbg 中的库函数调用 ︰ https://t.co/nxhoNFmn1y https://t.co/tWUOBZl15I"
-

[ Tools ] w0w Roper, a new exciting exploitation tool for ROP gadgets using genetic programming & Unicorn emulator inside! https://github.com/oblivia-simplex/roper
"Roper - 基于遗传算法,提取 ROP Gadgets,构造攻击链的工具: https://t.co/GJYmK4RRQI"
-

[ Web Security ] Adobe Patches DOM-XSS Flaw in Analytics AppMeasurement for Flash Library: https://threatpost.com/adobe-patches-dom-xss-flaw-in-analytics-appmeasurement-for-flash-library/117591/ via @ threatpost
"Adobe 修复了 Flash Analytics AppMeasurement 产品的一个 DOM-XSS 漏洞,来自 ThreatPost 的报道: https://t.co/jJsKZZc4k6"
-

[ Web Security ] #NoScript, script context. <script>alert//.%0D(1)</script> #fixed #bypass #XSS //cc @ma1
"NoScript 被修复的 XSS Bypass"
-

[ Web Security ] Wordpress iThemes Security (Better WP Security) Insecure Backup/Logfile… http://goo.gl/fb/K5ShOI #FullDisclosure
"Wordpress iThemes 插件存在漏洞,攻击者可以访问备份、日志文件, 来自 FullDisclosure 的公告: https://t.co/RXvUm4JssA "
-

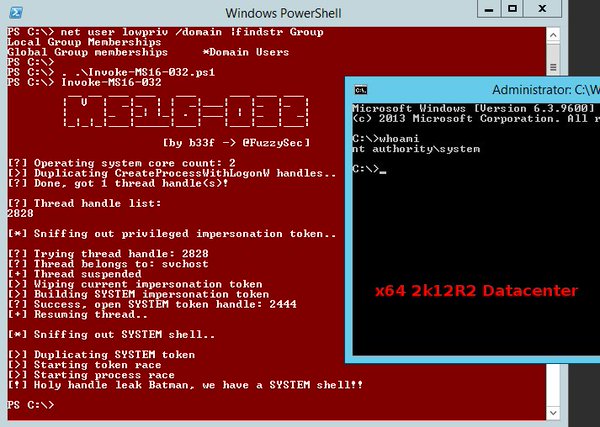
[ Windows ] #PowerShell exploit for MS16-032 Win7-Win10 & 2k8-2k12 (x32/x64) (CC @ tiraniddo ty!) - https://github.com/FuzzySecurity/PowerShell-Suite/blob/master/Invoke-MS16-032.ps1 https://t.co/IpZnQCZU8O
"MS16-032 PowerShell 版 Exploit,支持 Win7~Win10、2008~2012(x32/x64) 版本: https://t.co/IpmozhciXG 关于这个漏洞, James Forshaw 也写过一篇 Blog: https://googleprojectzero.blogspot.co.uk/2016/03/exploiting-leaked-thread-handle.html "
-

[ Windows ] [Blog Post] Bypass Application Whitelisting Script Protections - Regsvr32.exe & COM Scriptlets (.sct files) http://subt0x10.blogspot.com/2016/04/bypass-application-whitelisting-script.html :-)
"利用 Regsvr32.exe 和 .sct 文件绕过应用白名单脚本保护策略: https://t.co/yLdxMxSBXS "