腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

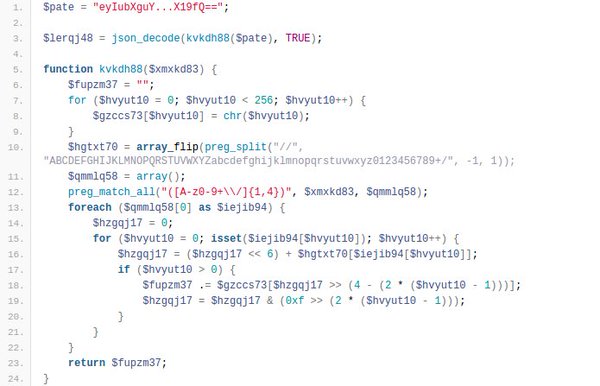
[ Android ] How I defeated an obfuscated and anti-tamper APK with some Python and a home-made Smali emulator : https://www.evilsocket.net/2016/04/18/how-i-defeated-an-obfuscated-and-anti-tamper-apk-with-some-python-and-a-home-made-smali-emulator/
"怎样用 Python 和自制 Smali 模拟器搞定一个加混淆、防篡改的 APK︰ https://t.co/WIKtZpCATz"
-

[ Attack ] New post: “Operation C-Major” Actors Also Used Android, BlackBerry Mobile Spyware Against Targets http://bit.ly/1Wb4EbY @ TrendMicro
" 在针对印度的 'C-Major' 信息窃取行动中,攻击者也会通过手机端窃密,包括使用 Android 和 BlackBerry 间谍软件: https://t.co/fr0hdIdw8y "
-

[ Attack ] Over the last year Google detected nearly 800,000 compromised websites. #big #number https://security.googleblog.com/2016/04/helping-webmasters-re-secure-their-sites.html
"在过去一年中,Google 检测到了 80 万个被入侵的网站: https://t.co/49GjP68oV3"
-

[ Attack ] How I hacked my local ISP and some general advice/learnings. https://blog.harshillodhi.co.in/how-i-hacked-into-my-isp-and-what-i-learnt-in-the-process/
"我是如何黑掉我的 ISP 的: https://t.co/JO95mVdFGf"
-

[ Attack ] Between Hong Kong and Burma: Tracking UP007 and SLServer Espionage Campaigns https://citizenlab.org/2016/04/between-hong-kong-and-burma/
"攻击香港民主人士的两大恶意软件家族: UP007 和 SLServer, 来自 CitizenLab 的分析文章: https://t.co/0EkX3w0quZ"
-

[ Exploit ] Dynamic or live demonstration of classical exploitation techniques of typical memory corruption vulnerabilities https://github.com/NoviceLive/bintut
"二进制漏洞利用学习工具,包括一些经典的内存破坏漏洞的利用: https://t.co/BmDxNgUkIr "
-

[ Hardware ] #GSM "Hacking as Transgressive Infrastructuring": Interesting paper about #Osmocom and other GSM hacks around #CCC http://mkorn.binaervarianz.de/pub/korn-cscw2016.pdf
"一篇关于 GSM Hacking 的 Paper: 《移动手机网络与德国混沌计算机俱乐部》: https://t.co/nfPedDC9jE"
-

[ iOS ] su-a-cyder - An Home-Brewed iOS Malware PoC Generator https://github.com/Mi3Security/su-a-cyder
"su-a-cyder - iOS 恶意软件 PoC 生成器, 作者在 BlackHat Asia 2016 会议上讲过这个工具: https://t.co/r7EjXqQU5F 会议 Slides: https://www.blackhat.com/docs/asia-16/materials/asia-16-Tamir-Su-A-Cyder-Homebrewing-Malware-For-iOS-Like-A-B0SS.pdf "
-

[ Mac OS X ] Remote code execution, git, and OS X http://rachelbythebay.com/w/2016/04/17/unprotected/
" Mac OS X 系统的 Git 2.6.4 存在远程代码执行漏洞(CVE-2016-2324/ CVE-2016-2315): https://t.co/i64Nkrconj"
-

[ Malware ] MMD-0053-2016 - A bit about ELF/STD IRC Bot: x00's CBack aka xxx.pokemon(.)inc http://blog.malwaremustdie.org/2016/04/mmd-0053-2016-bit-about-elfstd-irc-bot.html
"MMD-0053-2016 - MalwareMustDie Blog 一篇关于 ELF/STD IRC Bot 的分析: https://t.co/OuOzzbr7ko"
-

[ Malware ] Dissection of an obfuscated PHP script used for spamming : https://jelleraaijmakers.nl/2016/04/dissecting-spammers-spam-script https://t.co/TnU4KOqUxP
"剖析一段混淆后的、用于发送垃圾邮件的 PHP 脚本 ︰ https://t.co/lxwrlmlPZA https://t.co/TnU4KOqUxP"
-

[ Malware ] Powershell - A boon or Curse : Malware Created with Microsoft PowerShell Is on the Rise : https://www.carbonblack.com/wp-content/uploads/2016/04/Cb-Powershell-Deep-Dive-A-United-Threat-Research-Report-1.pdf (pdf)
"既想感谢又想诅咒的 PowerShell︰恶意软件是如何使用 PowerShell 的, 来自 Carbon Black 的研究报告 ︰ https://t.co/OEjeYSKZmr "
-

[ OpenSourceProject ] [SuggestedReading] Bypassing password authentication of users that have 2FA enabled http://ift.tt/1NxBXz6
"Gitlab 双因素认证用户的密码认证绕过 PoC: https://t.co/UW6VpW5vmA"
-

[ Others ] 60 Minutes overtime footage of our phone hacking: http://www.cbsnews.com/news/60-minutes-overtime-how-strangers-can-hack-the-phone-in-your-pocket/
"陌生人是如何黑掉你口袋里的手机的(视频) ︰ https://t.co/2aKW26n5BE http://www.cbsnews.com/news/60-minutes-hacking-your-phone/ "
-

[ Others ] WhatsApp vs Telegram | Fortinet Blog http://ow.ly/4mOITU
"从安全性方面比较 WhatsApp 和 Telegram: https://t.co/nGaxxiO3do"
-

[ Others ] On the SS7 network, probably worth revisiting @ DonAndrewBailey & @ nickdepetrillo's 2010 We Found Carmen San Diego https://infocon.org/cons/SOURCE/SOURCE%20Boston%202010/Presentation%20Slides/carmen.pdf
"关于 7 号信令系统(SS7), 这有一篇 2010 年的 Slides: https://t.co/jKHdPWfr7E"
-

[ Others ] Seeing a lot of traffic around an Android app deobfuscation blog post compels me to remind everyone about https://github.com/CalebFenton/simplify
"Simplify - 通用型 Android 反混淆工具: https://t.co/tIEWv4dGBb"
-

[ Others ] Securely Implementing (De)Serialization in PHP https://paragonie.com/blog/2016/04/securely-implementing-de-serialization-in-php
" PHP 反序列化的安全实现: https://t.co/Dn7Gg1vrtm"
-

[ Others ] Understanding ysoserial's CommonsCollections1 exploit http://gursevkalra.blogspot.gr/2016/01/ysoserial-commonscollections1-exploit.html
"ysoserial - Java 反序列工具,可以生成多种对象的序列化实例: https://github.com/frohoff/ysoserial 这篇 Blog 介绍其中的 CommonsCollections1 : https://t.co/tZuV0hTs9T"
-

[ Others ] Finding security bugs in web applications using domain-specific static analysis https://dspace.mit.edu/handle/1721.1/99841#files-area
"通过领域特定语言的静态分析,挖掘 Web 应用的安全漏洞,来自 MIT 的 Paper: https://t.co/ioSaYOulhP "
-

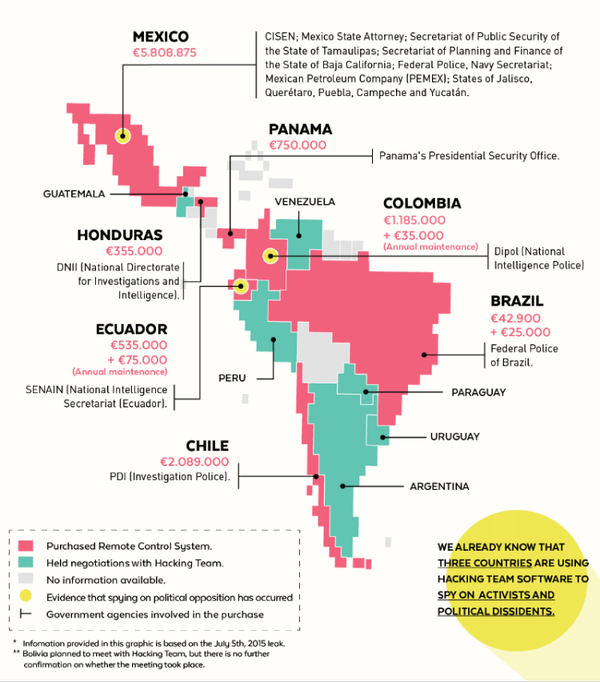
[ Others ] A look inside Hacking Team's Latin American empire. https://motherboard.vice.com/read/hacking-team-illegal-latin-american-empire https://t.co/lUNfa01rhP
"Hacking Team 的拉丁美洲帝国: https://t.co/CbUVo51eEC https://t.co/lUNfa01rhP"
-

[ Tools ] Just pushed my Rust bindings for @ unicorn_engine on crates.io : https://crates.io/crates/unicorn https://github.com/ekse/unicorn-rs
" Unicorn CPU 模拟器的 Rust 语言 Bindings: https://t.co/gPd6pvMwkh https://t.co/1COGoLa7xJ"
-

[ Tools ] New @ MIT scanner finds web app flaws in a minute - http://ow.ly/4mPwOI
"MIT 开发了一套 Web 应用分析工具,名叫 Space,该工具在 50 个热门 Web 应用中找到了 23 个新漏洞: https://t.co/Iu1ASjmsVn"
-

[ Web Security ] Wordpress Plugins jQuery Html5 File Upload https://cxsecurity.com/issue/WLB-2016040121
"Wordpress 插件 jQuery Html5 文件上传漏洞: https://t.co/LNXhmreC68"
-

[ Web Security ] Experts discovered a number of flaws in the Avactis PHP Shopping Cart http://securityaffairs.co/wordpress/46431/hacking/avactis-php-shopping-cart-flaws.html
"开源电商购物车组件 PHP Avactis 被发现多个漏洞, 来自 SecurityAffairs 的报道: https://t.co/alqDsKPEA9"
-

[ Web Security ] Oooh. http://bugs.chromium.org has deployed Content Security Policy with an experimental 'unsafe-dynamic' expression. https://w3c.github.io/webappsec-csp/#unsafe-dynamic-usage
" bugs.chromium.org 网站已经部署了实验性的 'unsafe-dynamic' 表达式, W3C 对该特性的介绍: https://t.co/4GoabLEMv6"
-

[ Windows ] Passwords for zip archives opened with Windows Explorer in Win8.x/10 are automatically cached. #facepalm http://goo.gl/4WXTQc
"Win 8.x/10 系统资源管理器在打开 ZIP 压缩文件时会缓存密码: https://t.co/jl4Sp5a6ac"