腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Analysis of CVE-2016-2414 - Out-of-Bound Write Denial of Service Vulnerability in Android Minikin Library http://blog.fortinet.com/post/analysis-of-cve-2016-2414-out-of-bound-write-denial-of-service-vulnerability-in-android-minikin-library-1
"Android Minikin 库越界写拒绝服务漏洞分析(CVE-2016-2414 ), 来自 Fortinet Blog: https://t.co/Yu9N8oGUWk "
-

[ Attack ] Join us for this webcast: The Attacker's Dictionary: Auditing Criminal Attacks #Rapid7 https://information.rapid7.com/the-attackers-dictionary-auditing-criminal-attacks-apac.html#.VxB90PGMeoU.twitter via @ rapid7
" 攻击者的字典 - Rapid7 通过蜜罐收集了 22 万条日志,包含攻击者使用过的密码信息,报告下载: https://t.co/bXchcqmLbS"
-

[ Attack ] RCMP obtained key to hack BlackBerry communications: report http://www.huffingtonpost.ca/2016/04/14/blackberry-decryption-key-rcp_n_9692680.html
"加拿大警察拥有 BlackBerry 手机的主加密 Key,可以解密 BlackBerry 的通信消息: https://t.co/ONej8ADBtS"
-

[ Attack ] w3c suffered a data breach: https://www.w3.org/wiki/AdvisoryCommittee/2016-04-data-breach
"w3c 遭到攻击,成员信息、部分邮件信息泄漏 ︰ https://t.co/2muenQBVnJ"
-

[ Browser ] #DailyBug bonus #Firefox 100% CPU usage https://bugzilla.mozilla.org/show_bug.cgi?id=1124835 <body onload='i=open("").Iterator;i.prototype.next=String;for(s in i(1));'>
"Firefox 迭代器拒绝服务漏洞, Bug 1124835: https://t.co/rMjDuWBWnk"
-

[ Browser ] Edge XSS filter bypass : http://blog.portswigger.net/2016/04/edge-xss-filter-bypass.html cc: @ garethheyes
"Edge 浏览器 XSS Filter Bypass, 来自 PortSwigger Blog ︰ https://t.co/DKkTLUVjRO "
-

[ Browser ] What is definition of a CSS hack http://www.sitepoint.com/what-is-the-definition-of-a-css-hack/ One of the things I’d add is a hack often takes advantage of parser bugs.
" 'CSS hack' 的定义是什么: https://t.co/HaZc8CcWUK "
-

[ Challenges ] My buddy, @ durchfall3n wrote the writeup for the challenge, "Worm" in XCTF http://www.vxsecurity.sg/2016/04/15/walkthrough-x-ctf-2016-worm/
"XCTF 2016 Worm 逆向题解题报告: https://t.co/hGIcDCECb5 "
-

[ Conference ] INFILTRATE 2016 speaker presentation slide decks are available online at http://infiltratecon.com/archives.html.
"INFILTRATE 2016 会议的所有 PPT 和视频: https://t.co/bL1FlBif0s。"
-

[ Defend ] Intel Tamper Protection Toolkit Helps Protect the Scrypt Encryption Utility against Reverse Engineering - https://software.intel.com/en-us/articles/intel-tamper-protection-toolkit-helps-protect-the-scrypt-encryption-utility-against-reverse
"Intel 防篡改套件包可以为关键代码和数据区提供防逆向和防篡改功能: https://t.co/s3Er8yKqLx 关于防篡改套件的其他文档: https://software.intel.com/en-us/tamper-protection/documentation "
-

[ Linux ] The Linux Scheduler: a Decade of Wasted Cores : http://www.ece.ubc.ca/~sasha/papers/eurosys16-final29.pdf (pdf)
"Linux 调度器的 Bug ︰ 那些年浪费的核: https://t.co/yCx9grXflF "
-

[ Linux ] Linux Troubleshooting Cheatsheet: strace, htop, lsof, tcpdump, iftop & sysdig : https://sysdig.com/blog/linux-troubleshooting-cheatsheet/
"Linux 问题排查手册︰ strace,htop,lsof,tcpdump,iftop & sysdig 工具的使用: https://t.co/ymuTWhvveT"
-

[ Malware ] Targeted Ransomware Activity https://blog.anomali.com/targeted-ransomware-activity
"定向勒索软件 SamSam 的近期动态: https://t.co/02oFOkzGFC"
-

[ Malware ] Widespread JBoss Backdoors a Major Threat http://blog.talosintel.com/2016/04/jboss-backdoor.html
"勒索软件利用 JBoss 漏洞在服务器安装后门, 目前发现有 1600 个 IP 已经被攻击,来自 Talos Blog: https://t.co/X0sey1zL3q"
-

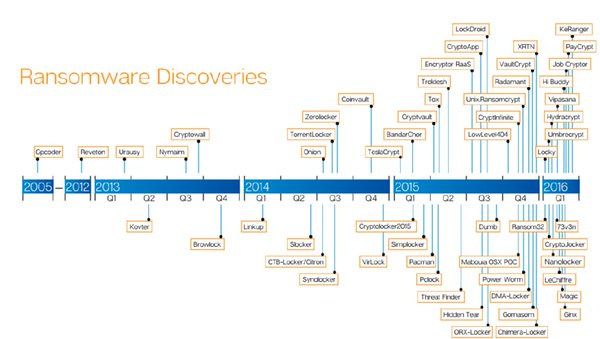
[ Malware ] Ransoware Discoveries https://t.co/bYLGDCmTDQ
"一张图展示勒索软件的发现历史: https://t.co/bYLGDCmTDQ"
-

[ Malware ] Meet GozNym Malware: The Banking Malware Offspring of Gozi ISFB and Nymaim : https://securityintelligence.com/meet-goznym-the-banking-malware-offspring-of-gozi-isfb-and-nymaim/ https://t.co/VI6yzCr2F8
"Security Intelligence 对 GozNym 恶意软件的分析: https://t.co/LdQPG4h8bs GozNym 是 Gozi ISFB 和 Nymaim 的后代 "
-

[ Mitigation ] @ HaifeiLi That range check failure is documented here: https://media.blackhat.com/bh-us-12/Briefings/M_Miller/BH_US_12_Miller_Exploit_Mitigation_Slides.pdf - Catches null byte writes out of bounds of a stack array
"Windows 8 在漏洞利用缓解技术方面的改进, 来自 BlackHat USA 2012 会议: https://t.co/fKhSQSJdxM "
-

[ NetworkDevice ] Cisco UCS servers can be hijacked with malicious HTTP request - Help Net Security http://ow.ly/4mIvbW
"发送一个恶意的 HTTP 请求就可以攻破思科 UCS 服务器(CVE-2016-1352), 来自 Help Net Security 的报道: https://t.co/qQcK3rtg2r"
-

[ Others ] Patch the VMware Client Integration Plugin asap: VMware issued a security update to fix a critical vulnerabili... http://saur0.tech/1V5HHb4
"VMware 客户端集成插件存在严重漏洞,可以通过中间人和 Web 会话劫持发起攻击,官方建议尽快升级。来自 SecurityAffairs 的报道: https://t.co/O0mWnJoSeZ"
-

[ Others ] Security Implications of DTD Attacks Against a Wide Range of XML Parsers : https://www.nds.rub.de/media/nds/arbeiten/2015/11/04/spaeth-dtd_attacks.pdf (pdf)
"各种 XML 解析器受 DTD 攻击的影响, 来自德国波鸿鲁尔大学的研究 Paper ︰ https://t.co/xNnU4ny5rf "
-

[ ReverseEngineering ] The Art of Unpacking : https://www.blackhat.com/presentations/bh-usa-07/Yason/Whitepaper/bh-usa-07-yason-WP.pdf (pdf) #b2b
"脱壳的艺术, 来自 BlackHat USA 2007 会议的演讲 ︰ https://t.co/RpTt3KUHIK "
-

[ SecurityProduct ] PfSense Community Edition Multiple Vulnerabilities http://goo.gl/fb/J9kufZ #FullDisclosure
"PfSense 社区版防火墙存在多个漏洞, 来自 FullDisclosure 公告: https://t.co/J2wyzl75cf "
-

[ ThreatIntelligence ] Beginners Guide to OSINT – Chapter 1 http://itgeekchronicles.co.uk/2016/04/15/beginners-guide-to-osint-chapter-1/
"OSINT(开源威胁情报)入门 第一章: https://t.co/OU8WQUPxx9 "
-

[ Tools ] Pafish : Several tech. to detect sandboxes: https://github.com/a0rtega/pafish ,al-khaser : Public malware tech. used in wild : https://github.com/LordNoteworthy/al-khaser
"Pafish - 采用多种技术探测沙箱环境的工具 ︰ https://t.co/86cRRmlG42 al-khaser - 野外恶意样本中使用的一些技术收集︰ https://t.co/j4hOExphJM"
-

[ Virtualization ] Slides for my Xenpwn talk from @ InfiltrateCon and @ SyScan: https://www.ernw.de/download/xenpwn.pdf, code + WP will be published soon™
"Xenpwn - 攻击半虚拟化(Paravirtualized)的设备,来自作者在 InfiltrateCon 和 SyScan 会议上的演讲:: https://t.co/2x1OvQ8e6i "
-

[ Windows ] An interesting bug in OLE found by my colleague, TLDR: StringCchCopyEx() is hard to understand even for MS ppl..https://blogs.mcafee.com/mcafee-labs/cve-2016-0153-microsoft-patches-possible-ole-typo
"微软修复了一个有趣的 OLE 漏洞(CVE-2016-0153), 漏洞存在于 ole32.dll 的 OleRegEnumVerbs() 中, 来自 McAfee Blog: https://t.co/8FgkJe0j4C 长话短说:甚至微软也很难真正理解 StringCchCopyEx()"