腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Likely the last Android Census update, now has 572 devices, SELECT your way to lolworthy bugs. https://census.tsyrklevich.net
"Android 手机设备统计信息汇总: https://t.co/GcAuYJisT2 https://androiddevice.info/"
-

[ Android ] Having fun with secure messengers and Android Wear (and Android Auto) : http://www.slideshare.net/CanSecWest/csw2016-chaykin-havingfunwithsecuremessengersandandroidwear (Slides)
"Android 几款通讯应用、Android Wear 与 PendingIntent 相关的攻击面 ︰ https://t.co/xEZLRUw17x "
-

[ Android ] Checkout @ anarcheuz poc for CVE-2014-0196 - https://github.com/anarcheuz/Android-PoCs/tree/master/CVE-2014-0196
"Android tty_insert_flip_string_fixed_flag 条件竞争漏洞(CVE-2014-0196) PoC: https://t.co/TPbilKY9sG"
-

[ Attack ] Very interesting writeup (spanish) describing how HackingTeam was hacked (opsec tips included): http://pastebin.com/raw/GPSHF04A
"Hacking Team 是如何被黑的,西班牙语版 ︰ https://t.co/Dm9WRsKLBn 英文版: https://ghostbin.com/paste/2w26u 还有一篇 MotherBoard 的报道文章: https://motherboard.vice.com/read/the-vigilante-who-hacked-hacking-team-explains-how-he-did-it "
-

[ Browser ] Microsoft Internet Explorer 11 MSHTML.DLL Remote Binary Planting… http://goo.gl/fb/Gs4QTt #FullDisclosure
"IE 11 MSHTML.DLL 引用了系统中多个不存在的 DLL 文件,攻击者如果可以植入这些 DLL,就可以实现 DLL 劫持, 来自 Full Disclosure 的公告: https://t.co/aF6uN4p0ac "
-

[ Crypto ] Why TLS 1.3 is a major leap forward for #cryptographic protocols. #swsec https://www.cigital.com/blog/tls-1-3/ via @ cigital
"TLS 1.3 与加密协议的未来, 来自 Cigital Blog: https://t.co/7cMDIDNVy0"
-

[ Exploit ] Bypassing Different Defense Schemes via Crash-Resistant Probing of Address Space : http://www.slideshare.net/CanSecWest/csw2016-gawlik-bypassingdifferentdefenseschemes (Slides)
"通过地址空间的 Crash 弹性探测技术绕过不同的防御, 来自 CanSecWest 2016 会议: https://t.co/4UAgv6cKaw "
-

[ Exploit ] Automatic Exploit Generation - an Odyssey : http://www.slideshare.net/CanSecWest/csw2016-d-antoineautomaticexploitgeneration (Slides)
"Exploit 自动生成之旅, 来自 CanSecWest 2016 会议︰ https://t.co/2CMTs9cMaA "
-

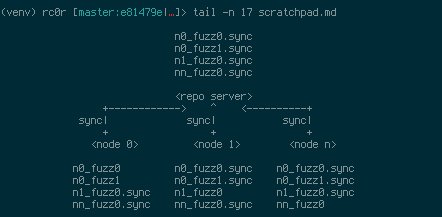
[ Fuzzing ] afl-utils v1.27a comes with yet another new tool: afl-sync! https://github.com/rc0r/afl-utils Happy syncing! #AmericanFuzzyLop https://t.co/URyF5vohH5
"afl-fuzz 的辅助工具集 afl-utils 更新 v1.27a,本次新添加了一个工具 afl-sync,用于多个 fuzz 实例之间的同步、备份、重建: https://t.co/voN2191yw5 https://t.co/URyF5vohH5"
-

[ Fuzzing ] "Reducers are Fuzzers" http://blog.regehr.org/archives/1284 by @ johnregehr
"Reducers are Fuzzers, Reducer 指用于精简样本的工具: https://t.co/VnaVoj5Tzj"
-

[ Fuzzing ] I just created a Docker image for Nightmare (https://github.com/joxeankoret/nightmare). Just use: $ docker pull joxean/nightmare
"Nightmare - 分布式 Fuzz 框架的 Docker 镜像版: https://t.co/UZqujxONQO "
-

[ Hardware ] HARDSPLOIT : Framework for Hardware Security Audit - a bridge between hardware & a software pentester : http://www.slideshare.net/CanSecWest/csw2016-julien-moinardhardsploit (Slides)
"HARDSPLOIT - 硬件安全审计框架,连接软件渗透测试工程师和硬件之间的桥梁,来自 CanSecWest 2016 会议: https://t.co/9YQ3jV6my8 "
-

[ IoTDevice ] Attacking Smart locks w/ a smart Phone : http://www.slideshare.net/CanSecWest/csw2016-song-lismartwars (Slides)
"用智能手机攻击 kevo 蓝牙智能锁, 来自 CanSecWest 2016 会议 ︰ https://t.co/DPm1BuczVZ "
-

[ Linux ] KASLR memory randomization proposal for Linux kernel http://permalink.gmane.org/gmane.linux.kernel.hardened.devel/2181
"Linux 内核 KASLR 内存随机化加固建议: https://t.co/amNjDdjQWp "
-

[ MachineLearning ] Tensorflow - Play with neural networks : https://github.com/tensorflow/playground , Whitepaper : http://download.tensorflow.org/paper/whitepaper2015.pdf
"Google 的第二代机器学习引擎 Tensorflow - 把玩神经网络 : https://t.co/vSmstgd7k4 Tensorflow Paper : https://t.co/JJY5zZURrh"
-

[ MachineLearning ] Understanding Machine Learning : From Theory to Algorithms : http://www.cs.huji.ac.il/~shais/UnderstandingMachineLearning/understanding-machine-learning-theory-algorithms.pdf (pdf)
"剑桥大学出版社 2014 年出版的一本书:《深入理解机器学习︰从理论到算法》 ︰ https://t.co/sVlw7m4fG5 "
-

[ Malware ] Neutrino Exploit Kit Analysis and Threat Indicators https://www.sans.org/reading-room/whitepapers/malicious/neutrino-exploit-kit-analysis-threat-indicators-36892
"SANS 发表的《 Neutrino Exploit Kit 分析白皮书》: https://t.co/nfS9lMQTS8"
-

[ Network ] Today I learned about https://dnshistory.org/ - look up historical DNS records for many, many domain names. Now on #dnsdist :-)
"DNS 变更历史记录查询工具(在线版): https://t.co/Zw46KG3U2F "
-

[ NetworkDevice ] A Systematic Analysis of the Juniper Dual EC Incident : http://eprint.iacr.org/2016/376.pdf (pdf)
"Juniper ScreenOS Dual EC 伪随机数生成器漏洞整体分析, Paper ︰ https://t.co/VtP36BuHWn "
-

[ NetworkDevice ] Execute My Packet : http://www.slideshare.net/CanSecWest/csw2016-wheeler-barksdalegruskovnjakexecutemypacket (Slides)
"Execute My Packet - Exodus 的研究员在 CanSecWest 2016 会议讲 Cisco 网络设备漏洞利用(CVE-2016-1287) ︰ https://t.co/RXAMa2aYgb 之前推送过 Exodus 在 Blog 上发表的一篇同名文章: https://blog.exodusintel.com/2016/01/26/firewall-hacking/ "
-

[ OpenSourceProject ] ZDI-16-243: Google Chrome Pdfium JPEG2000 Out-Of-Bounds Read Information Disclosure Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-243/
" Google Chrome Pdfium JPEG2000 越界读信息泄露漏洞, ZDI-16-243 公告: https://t.co/xSnv0GM65h"
-

[ Others ] Awesome CPUs : Manuals/documentation & Datasheets for CPU & MCU : https://github.com/larsbrinkhoff/awesome-cpus
"Awesome CPUs - 各种 CPU/ MCU(微控制器) 的文档收集, Github Repo ︰ https://t.co/F4Wp9Q1hQn"
-

[ Others ] Docker Escape Technology : http://www.slideshare.net/CanSecWest/csw2016-wang-dockerescapetechnology (Slides)
"Docker 逃逸技术,来自 CanSecWest 2016 会议 ︰ https://t.co/tu2d4hZayM "
-

[ Others ] Here are the slides for @ evan_pena2003 and my talk at @ bsidesnash on Persistence Techniques Seen in the Wild - http://www.slideshare.net/CTruncer/ever-present-persistence-established-footholds-seen-in-the-wild
"野外样本中看到的持久控制技术, 来自 Bsides 会议: https://t.co/IQ5CIUNFJh"
-

[ Pentest ] XSSProxy https://github.com/jackmasa/XSSProxy
"XSSProxy - XSS 攻击内网代理工具,Github Repo: https://t.co/I5G0cCCmND"
-

[ ReverseEngineering ] Rockey 4 USB dongle: Unknown algo deduction using black-box input/output pairs & Z3 SMT solver http://blog.yurichev.com/node/71 cc: @ RolfRolles @ seanhn
"Rockey 4 USB 加密狗 ︰ 仅依赖输入输出组合和 Z3 SMT 求解器,推倒未知算法: http://t.co/1J0ttjJ3 "
-

[ Tools ] RoP Hooks : http://www.slideshare.net/CanSecWest/csw2016-macaulay-ehtracerophooks (Slides)
"RoP Hooks - Trace ROP 的执行过程, 来自 CanSecWest 2016 会议 ︰ https://t.co/dZENErC00b "
-

[ Tools ] IPGeoLocation – Retrieve IP Geolocation Information http://www.darknet.org.uk/2016/04/ipgeolocation-retrieve-ip-geolocation-information/
"IPGeoLocation - 检索 IP 地址地理位置信息的工具: https://t.co/zYPdIgBYAl"
-

[ Tools ] Uploaded Symex on github — simple tool which resolves symbols (uses dbghelp): https://github.com/ax330d/Symex
"Symex - 调试符号解析工具,指定目标进程 PID、模块名、偏移(或地址),该工具会自动下载符号并且解析出对应的符号名字(如某个函数): https://t.co/3MSGQw0aIn"
-

[ Windows ] New post up on @ WhitehattersA exploiting a bunch more of the @ HackSysTeam driver vulns https://www.whitehatters.academy/intro-to-windows-kernel-exploitation-more-of-the-hacksys-driver/
"以 HackSys 驱动的几类漏洞为示例谈 Windows 内核漏洞利用: https://t.co/EsXyCWXLsB "
-

[ Windows ] Bypassing application whitelisting in critical infrastructures : http://www.slideshare.net/CanSecWest/csw2016-freingruber-bypassingapplicationwhitelisting (Slides)
"关键基础设施应用白名单保护绕过, 来自 CanSecWest 2016 会议 ︰ https://t.co/oo7p1DISTB "
-

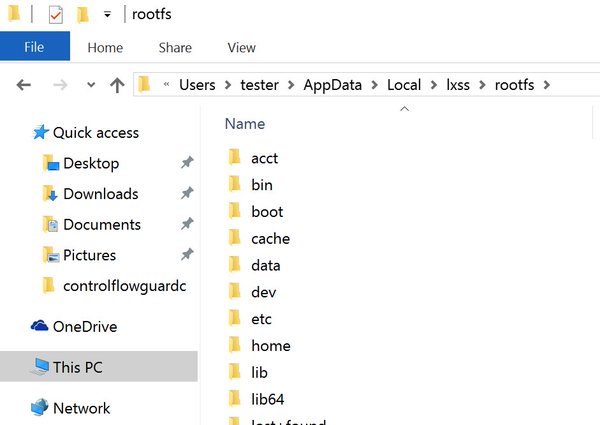
[ Windows ] OK! The win10 linux files are at ...\AppData\Local\lxss\rootfs\ Defender excludes rootfs from active protection. https://t.co/wditNRkOBg
"Win10 Linux 子系统位于 \AppData\Local\lxss ootfs\ 该路径在 Defender 的主动防御排除项: https://t.co/wditNRkOBg"
-

[ Windows ] Masquerading as a Windows System Binary Using Digital Signatures : https://labs.mwrinfosecurity.com/blog/masquerading-as-a-windows-system-binary-using-digital-signatures/ https://t.co/8hxI8LqYaU
"构建自己的 CA,将此 CA 根证书安装到目标机器,然后用此 CA 签名的文件伪装成 Windows 系统文件 ︰ https://t.co/GGuCYfxmPg https://t.co/8hxI8LqYaU"