腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

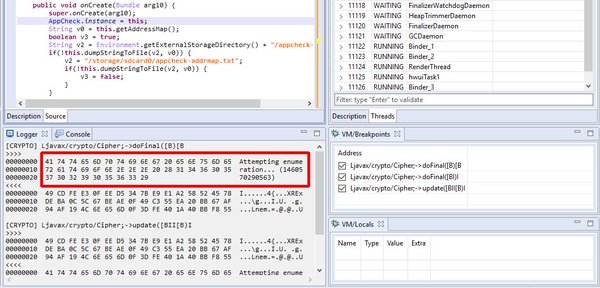
[ Android ] Crypto hooking on Android using the JEB debuggers API, demo plugin at https://www.pnfsoftware.com/blog/crypto-monitoring-android-debuggers-api/ https://t.co/O7z3SLZ9vl
"利用 Android JEB 调试器 API Hook 加密流程,提取输入输出参数: https://t.co/rOK6MijleT 示例代码: https://github.com/pnfsoftware/jeb2-samplecode/tree/master/src/com/pnf/andhook "
-

[ Android ] #Unit42 finds #MobileOrder #trojan targeting #Android users w/ pro-terrorism lures via social networks http://bit.ly/264kNEw
"MobileOrder Android 木马通过社交网络攻击亲恐怖主义的土耳其用户, 来自 Palo Alto Blog: https://t.co/S84CNRko8D"
-

[ Attack ] New post: US and European companies Top Targets of CEO Fraud http://bit.ly/263mlPg @ TrendMicro
"FBI 发布警告称: CEO 邮件诈骗攻击的数量在上升, 来自 TrendMicro Blog: https://t.co/UAAcpdWAjl "
-

[ Attack ] Estonia’s intelligence services report for 2015 is a must read if you’re interested in espionage, Russia or policy. https://www.kapo.ee/sites/default/files/public/content_page/Annual%20Review%202015.pdf
"爱沙尼亚的 2015 情报服务报告: https://t.co/7ZkCeFdTC8"
-

[ Browser ] Latest #Chrome Update Addresses Two High-Severity Vulnerabilities: https://threatpost.com/latest-chrome-update-addresses-two-high-severity-vulnerabilities/117400/ via @ threatpost
"Chrome 浏览器发布 50.0.2662.75 版本, 本次更新修复了 20 个漏洞,其中含两个高危漏洞, 来自 ThreatPost 的报道: https://t.co/iTvEIbHJUy Chrome 官方 Blog: http://googlechromereleases.blogspot.com/2016/04/stable-channel-update_13.html "
-

[ Browser ] UXSS Vulnerability in Comodo Dragon Browser (Write Up) http://blog.evanricafort.com/2016/04/11/universal-xss-vulnerability-in-comodo-dragon-browser-version-29-1-0-0-write-up/ #infosec #hacking #security #vulnerability #uxss #comodo
"Comodo Dragon 浏览器 UXSS 漏洞 PoC: https://t.co/oGiwriniLt "
-

[ Conference ] CanSecWest 2016 Slides Download: http://www.slideshare.net/CanSecWest/presentations https://t.co/YDlINExbml
"CanSecWest 2016 会议 Slides 下载 ︰ https://t.co/15kauNxCT4 https://t.co/YDlINExbml"
-

[ Defend ] DynaGuard : Armoring Canary-based Protections against Brute-force Attacks : https://www3.cs.stonybrook.edu/~mikepo/papers/dynaguard.acsac15.pdf (pdf)
"DynaGuard - 基于 Canary 的 Stack Cookie 保护技术被广泛部署在现代操作系统中,但对于进程 Fork 型程序(如 Ngnix),却可以通过逐字节穷举的方法猜出 Cookie 的值,使保护方法失效。这篇 Paper 作者提出了 DynaGuard,是对现有 Canary 保护的增强 ︰ https://t.co/XQely6MS4W "
-

[ Defend ] Readactor: Practical Code Randomization Resilient to Memory Disclosure https://www.ics.uci.edu/~sjcrane/papers/sjcrane15_readactor.pdf
"Readactor︰ 目前的内存缓解措施都不能对抗信息泄露+ROP, 这篇 Paper 尝试提出一种能够对抗信息泄露的代码随机化技术: https://t.co/NBMsQxiCw0"
-

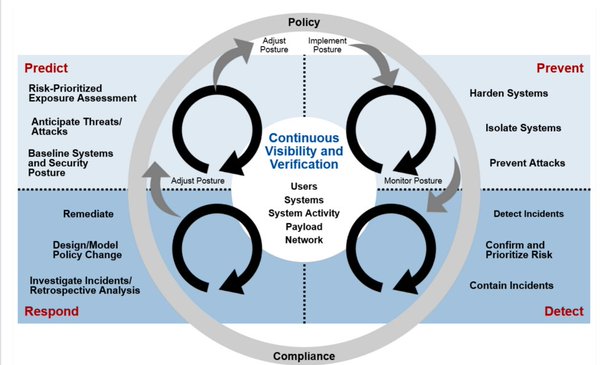
[ Defend ] [@ Gartner_inc Report] Gain tactics that'll help your org's prevention, detection & response http://bddy.me/1VsqPM8 https://t.co/SwYsLsEQMf
" 保护中端企业市场免遭高级威胁攻击的安全战略, 来自 Gartner 报告: https://t.co/r4MgJN7B2F https://t.co/SwYsLsEQMf"
-

[ Detect ] Nice set of posts on a threat hunting reference model proposal http://blog.sqrrl.com/the-cyber-hunting-maturity-model http://blog.sqrrl.com/the-threat-hunting-reference-model-part-2-the-hunting-loop http://blog.sqrrl.com/the-threat-hunting-reference-model-part-3-the-hunt-matrix
"来自 Sqrrl 的威胁检测参考模型, Part 1: https://t.co/8e5zcPnGNA Part 2: https://t.co/O62oLdQj6c Part 3: https://t.co/CXUzCLcsTR"
-

[ iOS ] We’ve just open-sourced some sweet iOS tools to help you easily find and fix memory leaks. https://code.facebook.com/posts/583946315094347 #f8 #f82016
"Facebook 开源了一套自动化检测 iOS 内存泄露的工具, 来自 Facebook Blog: https://t.co/g2yTITIm8r"
-

[ iOS ] iOS date bug could be triggered over Wi-Fi spoofing an NTP server http://securityaffairs.co/wordpress/46305/hacking/ios-date-bug.html
"在 Wi-Fi 环境欺骗 NTP 服务器可以触发 iOS 的日期 Bug,使 iPhone 永久成砖, 来自 SecurityAffairs 的报道: https://t.co/KngjdpDnP6"
-

[ MalwareAnalysis ] DRAKVUF :Agentless dynamic malware analysis sys built on Xen,LibVMI, Volatility & Rekall : http://drakvuf.com/ ,http://www.slideshare.net/tklengyel/drakvuf
"DRAKVUF - 无 Agent 的恶意软件动态分析系统,基于 Xen、 LibVMI、Volatility、Rekall, 官网: https://t.co/g7ESid3ety 会议演讲的 Slides: https://t.co/SC1WUg3h2c"
-

[ Others ] DIMVA paper on Flush+Flush Cache Side Channels by @ BloodyTangerine and @ lavados https://cmaurice.fr/pdf/dimva16_gruss_flush.pdf
"Flush+Flush - 一个快速、隐蔽的缓存攻击: https://t.co/iMwTMcrWGg "
-

[ Others ] row hammer with memcpy/memset & Non-Temporal instructions: http://seclab.cs.sunysb.edu/seclab/pubs/host16.pdf
"基于 memcpy 和 memset 的 Row hammer 攻击, Paper︰ https://t.co/3kaUPMRT0t"
-

[ Others ] Iron-filings: An offline brute-force attack against Node.js authentication tokens (Iron, hapi-cookie-auth, Yar). https://github.com/tkeetch/iron-filings
"Iron-filings - Node.js 认证 tokens 离线爆破工具: https://t.co/ggY7moQPZW"
-

[ Others ] Deep learning materials (french and english) 2016 slides/videos from the lectures and seminars by @ ylecun https://drive.google.com/folderview?id=0BxKBnD5y2M8NclFWSXNxa0JlZTg&usp=drive_web
"从 2016 年多个会议收集的深度学习相关的资料, 部分资料为法语, Google Drive: https://t.co/k1QnIMJXWN"
-

[ Others ] Apple deprecates QuickTime for Windows. No patch coming for ZDI-16-241 and ZDI-16-242. http://zerodayinitiative.com/advisories/ZDI-16-241 http://zerodayinitiative.com/advisories/ZDI-16-242
"苹果不再维护 Windows 版 QuickTime, 因此 ZDI-16-241 和 ZDI-16-242 这两个 RCE 漏洞将不会被修复: https://t.co/0OYJ1T7137 https://t.co/emfPibMizS"
-

[ Pentest ] [New Blog Post] Setting Up A Homestead In the Enterprise with JavaScript. http://subt0x10.blogspot.com/2016/04/setting-up-homestead-in-enterprise-with.html Feedback Welcome. This is fun!
" JavaScript Post-Exploitation 与 .SCT 文件, 来自 subTee Blog: https://t.co/BhFy8iCzZX "
-

[ ThirdParty ] Django CMS v3.2.3 - Filter Bypass & Persistent Vulnerability http://goo.gl/fb/P0rV7O #FullDisclosure
"Django CMS v3.2.3 过滤器绕过 & 永久性注入漏洞: https://t.co/0yMWjVdjdA "
-

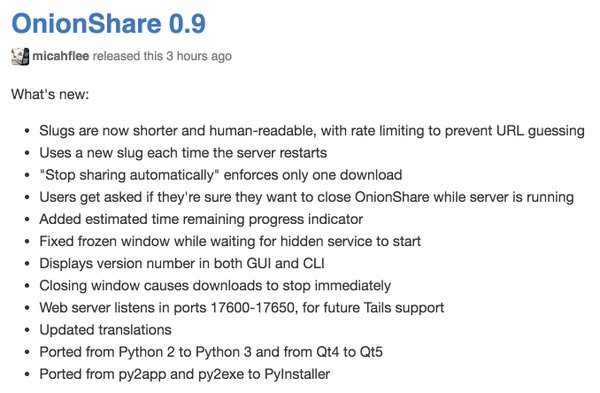
[ Tools ] I've just released OnionShare 0.9, with a slew of new features. Check it out https://onionshare.org/ https://t.co/pffxeSroaR
"OnionShare 0.9 版本发布, OnionShare 是个匿名文件共享工具: https://t.co/2jH0FuYsBU https://t.co/pffxeSroaR"
-

[ Web Security ] Brute-force short URLs to privately-shared files. #oops https://twitter.com/princetoncitp/status/720576680851542016
"通过暴力枚举短域名服务,可以发现一些云服务中分享的私有敏感文件, 如微软 OneDrive: https://t.co/CvmjbcK5Vd 去年还推送过另外一篇文章: http://shubh.am/exploiting-url-shortners-to-discover-sensitive-resources-2/ "
-

[ Web Security ] Cross-Site Script Inclusion - A Fameless but Widespread Web Vulnerability Class http://www.scip.ch/en/?labs.20160414
"跨站脚本执行 - 一个名气不大但传播广泛的 Web 漏洞类型: https://t.co/tqkRxdnL9e "
-

[ Web Security ] As serious as #BadLock: https://sadlock.org, http://notoken.pl
"继 BadLock、 Sadlock 后, 又有人发现了一个 WordPress 的严重漏洞, 并将其命名为 'BadCSRF NoToken' Bug, 也专门建了一个网站, 这个漏洞将于今年 7 月 15 号披露︰ https://t.co/ovAeGodLBR https://t.co/a34pXX4BPA"
-

[ Windows ] Excellent documentation on the Registry file format: https://github.com/msuhanov/regf/blob/master/Windows%20registry%20file%20format%20specification.md
"Windows 注册表文件格式规范, 来自 Github Repo ︰ https://t.co/IUrAbXMXL9"
-

[ Windows ] Windows Kernel ATMFD.DLL NamedEscape 0x2511 Out-Of-Bounds Read https://packetstormsecurity.com/files/136688 #exploit
"Windows Kernel ATMFD.DLL NamedEscape 0x2511 越界读漏洞, 微软认为这个漏洞无法利用,所以目前该漏洞的状态是 WontFix, 来自 Project Zero Issue 781: https://bugs.chromium.org/p/project-zero/issues/detail?id=781 "