腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] ReDex is an Android bytecode optimizer originally developed at Facebook http://fbredex.com/
"ReDex - Facebook 开发的 Android 字节码优化工具: https://t.co/n9CBQCafJj "
-

[ Android ] 通过BT种子传播到安卓手机的下载者 - http://blogs.360.cn/360safe/2016/04/12/bt_android_downloader/
"通过BT种子传播到安卓手机的下载者, 来自 360 Blog: https://t.co/tMgxxTS9Fl"
-

[ Attack ] New @ DeepEndResearch post: "JBoss exploits - View from a Victim" - http://www.deependresearch.org/2016/04/jboss-exploits-view-from-victim.html
"从被攻击者的角度看 JBoss Exploits: https://t.co/cecP7enlPT"
-

[ Attack ] [White Paper] Learn why cyber attackers are targeting higher education. http://bddy.me/1XvfU1v #highereducation https://t.co/RJN1Xtnffm
"为什么攻击者如此青睐高等教育机构, FireEye 评估了 100 所高校的网络,发现全部存在漏洞: https://t.co/Rgg7EdI78o https://t.co/RJN1Xtnffm"
-

[ Browser ] H.264/AVC is coming to RTC in Edge. Also available in Firefox & behind flag in Chrome https://blogs.windows.com/msedgedev/2016/04/13/roadmap-update-for-real-time-communications-in-microsoft-edge/#.Vw59t3IzVxs.twitter
"微软 Edge 浏览器将在 RTC(网页实时通信)中支持 H.264/AVC: https://t.co/gkuzCcwDzw"
-

[ Crypto ] Very interesting EUROCRYPT 2016 paper on defects in the OpenSSL PRNG by Falko Strenzke (former colleague): https://eprint.iacr.org/2016/367.pdf
"OpenSSL 随机数生成器缺陷分析, Paper ︰ https://t.co/9WEJFT57OM"
-

[ Defend ] Preventing malicious attacks by diversifying Linux shell commands http://ceur-ws.org/Vol-1525/paper-15.pdf
"通过使 Linux shell 命令多样化,对抗恶意软件攻击, Paper: https://t.co/vldkD4Z9pN"
-

[ Exploit ] Part 3 of Exploitation Demystified covers heap based #exploits http://bit.ly/1Q7wjDx
"Palo Alto 漏洞利用揭秘之基于堆的漏洞利用: https://t.co/vObtV9aQjz"
-

[ Forensics ] Smartphone Forensics to Detect Distraction https://www.schneier.com/blog/archives/2016/04/smartphone_fore.html
"Cellebrite 公司正在开发一款智能手机取证设备,这个设备可以判断用户在某个时间点是否在使用手机。这个可用于判断交通事故中驾驶员当时是否在玩手机: https://t.co/9oXJU4z9Bf"
-

[ Hardware ] Ethernet Connected Remote Wifi Sniffing Station with an ESP8266 Module : http://phasenoise.livejournal.com/4003.html , Github : https://github.com/cnlohr/espthernet
"以太网连接的远程 WiFi Sniffer 设备(基于 ESP8266 芯片) : https://t.co/FRdLdp6PkU Github Repo : https://t.co/E8JAtbJPHJ"
-

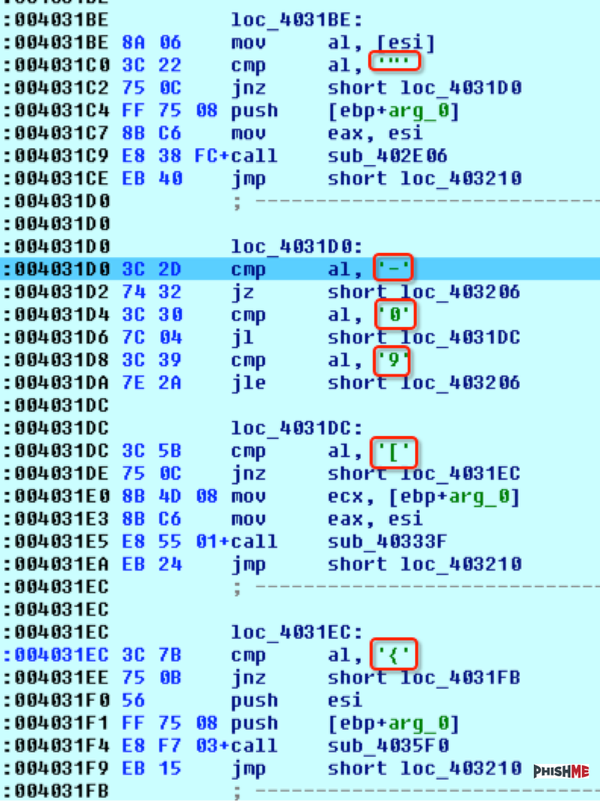
[ Malware ] RockLoader : New Upatre-like Downloader Pushed by Dridex, Downloads all the Malwares : http://phishme.com/rockloader-new-upatre-like-downloader-pushed-dridex-downloads-malwares/ https://t.co/OZO4JQMFD6
"RockLoader ︰ 靠 Dridex 推广的一个下载器,来自 PhishMe Blog ︰ https://t.co/ZNzRuXErR7 https://t.co/OZO4JQMFD6"
-

[ Malware ] We'd like to introduce the 1st of our “Ghosts in the Endpoint” series on malicious #software http://bddy.me/1VoRFEO https://t.co/YM1eGevrJw
" FireEye 《终端中的幽灵》系列文章第一篇: https://t.co/rq2Up2HQIR FireEye 将会在这个系列的文章中分析一些基于 Signature 无法检测到的恶意软件,被分析的样本都是在 VirusTotal 上检测率为 0。有时还会分析一些 VirusTotal 上检测率很低但绕过技术很有趣的样本"
-

[ Malware ] Qbot Malware Morphs Quickly to Evade Detection https://threatpost.com/qbot-malware-morphs-quickly-to-evade-detection/117377/
"Qbot 恶意软件变种轻松逃逸检测, 来自 ThreatPost 的报道: https://t.co/uLCHqxcylf 来自 BAE System 的报告《 Qbot 归来》: https://resources.baesystems.com/pages/view.php?ref=39115&search=&offset=0&order_by=relevance&sort=DESC&archive=0&thumbs=show&k=46713a20f9& "
-

[ Malware ] 黑暗幽灵(DCM)木马详细分析 - http://drops.wooyun.org/tips/14911
"黑暗幽灵(DCM)木马详细分析, 来自 Wooyun Drops: https://t.co/YogIE67lMX"
-

[ MalwareAnalysis ] RT @ viql: Published the DGA of the banking trojan Qadars 3.0.0.0 - active since mid March it seems https://johannesbader.ch/2016/04/the-dga-of-qadars/
"银行木马 Qadars 3.0.0.0 DGA(动态域名算法)分析: https://t.co/UoaV8hUkeG"
-

[ Operating System ] Writing an OS in Rust : Kernel Heap : http://os.phil-opp.com/kernel-heap.html //Series cont'd
"用 Rust 语言写操作系统系列文章之内核堆 ︰ https://t.co/zbMrkhmvdb "
-

[ Others ] Automated Root Cause Identification for Crashing Executions by @ seanhn https://docs.google.com/presentation/d/1vvl34hw0pAyFeNo-oqJnMUg8zsKIVNj0NHOKxdW-UEs/edit#slide=id.p
" 自动化地定位 Fuzz 过程中 Crash 的根本原因: https://t.co/RkHa6zly1t "
-

[ Others ] Go 1.6.1 and 1.5.4 are released to address two security issues. Info: https://groups.google.com/d/msg/golang-announce/9eqIHqaWvck/kXsfO0ogLAAJ Download: https://golang.org/dl/ #golang
"Go 发布 1.6.1 和 1.5.4 版本,修复了两个安全漏洞,一个是 DLL 加载时的劫持问题,另一个是加密时参数不正确导致的超长运算问题(有可能拒绝服务), 漏洞公告︰ https://t.co/nSRDm4Ivwt 新版本下载 ︰ https://t.co/StazJXrC1k "
-

[ Others ] https://www.sadlock.org.
"Badlock 漏洞昨天披露后,今天又有人为 Badlock 漏洞建了一个网站,名叫 Sadlock: https://t.co/KTKLgEEM2m"
-

[ Others ] ZDI-16-234: Microsoft .NET Framework mscoreei DLL Planting Remote Code Execution Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-234/
"ZDI-16-234: Microsoft.NET 框架 mscoreei DLL 劫持漏洞, 来自 ZDI 的公告: https://t.co/thH0KQviJK"
-

[ Others ] ZDI-16-235: Adobe Creative Cloud Node.js Remote Code Execution Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-235/
"ZDI-16-235: Adobe Creative Node.js 远程代码执行漏洞, 来自 ZDI 的公告: https://t.co/u6NCerRuQu"
-

[ Pentest ] WhatsPwn : Linux tool used to extract sensitive data, inject backdoor or drop remote shells on android devices : https://github.com/jlrodriguezf/WhatsPwn
"WhatsPwn: 用于在 Android 设备上提取敏感信息、注入后门、释放远程 Shell 的工具, Github Repo︰ https://t.co/qWw6RImfYU"
-

[ Tools ] UniHook - Intercept arbitrary functions at run-time, without knowing their typedefs https://github.com/stevemk14ebr/UniHook
"UniHook - 函数 Hook 框架,可以在运行时劫持任意函数,而且无需知道函数的原型定义: https://t.co/5O2f9jyiWL"
-

[ Tools ] gapstone - gapstone is a Go binding for the capstone disassembly library https://github.com/bnagy/gapstone
"gapstone - Capstone 反汇编引擎的 Go 语言 Binding: https://t.co/Nzn66wYiip"
-

[ Tools ] RDP Replay Code Release http://contextis.com/resources/blog/rdp-replay-code-release/
"RDP Replay - RDP 流量重放工具, 来自 Context 公司: https://t.co/KVPl1xtCLl"
-

[ Tools ] lesser known commercial RCE tools: http://www.hopperapp.com/ https://www.relyze.com/ https://binary.ninja/
"鲜有人知的商业 RCE 攻击工具︰ Hopper: https://t.co/lteenQoLEO Relyze: https://t.co/YBPrEES9lt Ninja 逆向平台: https://t.co/KezL5KeZSL"
-

[ Virtualization ] HyperBone - Minimalistic VT-X hypervisor with hooks https://github.com/DarthTon/HyperBone
"HyperBone - 简约型 VT-X Hypervisor,支持内核 Inline Hooks,MSR Hooks,IDT Hooks 等, Github Repo: https://t.co/AXJK9MbggK"
-

[ Virtualization ] Stealthy monitoring with Xen altp2m https://blog.xenproject.org/2016/04/13/stealthy-monitoring-with-xen-altp2m/
"基于 Xen Hypervisor altp2m 实现对 Guest 机隐蔽的监控, 来自 Xen Blog: https://t.co/y3VFvvjXhW"
-

[ Vulnerability ] I just discovered another article by Ruhai Zhang on the same topic, with some additional info: https://www.virusbulletin.com/virusbulletin/2013/05/cat-and-mouse-game-cve-2012-0158#id4230804
"CVE-2012-0158(Office 漏洞)的猫鼠游戏, 来自 VirusBulletin 2013 年的一篇 Blog ︰ https://t.co/PUDkgQbexE"
-

[ Vulnerability ] New post: How bad is Badlock (CVE-2016-0128/ CVE-2016-2118)? http://bit.ly/1qPpy4T @ TrendMicro
"Badlock 漏洞到底有多严重 (CVE-2016-0128/ CVE-2016-2118) , 来自 TrendMicro Blog: https://t.co/gIayA44gV9"
-

[ Vulnerability ] New advisory and POC for MS16-042 at https://smsecurity.net/microsoft-office-excel-out-of-bounds-read-remote-code-execution/
"MS16-042(CVE-2016-0122) Office 越界读 RCE 漏洞 PoC: https://t.co/Ep10ZXM4m8"
-

[ Web Security ] Google Account Recovery XSS (worth a bug bounty of $12.5k ) : https://sites.google.com/site/bughunteruniversity/best-reports/account-recovery-xss
"Google 账户找回功能 XSS( Google 给了 12.5k 的 Bounty 奖金): https://t.co/HlUXnU4UXD"
-

[ Web Security ] GitHub's CSP journey (Content Security Policy) http://githubengineering.com/githubs-csp-journey/
"GitHub 的 CSP 之旅(内容安全策略): https://t.co/Cly2Yi2udF"
-

[ Windows ] Our articles about a malicious RTF (CVE-2015-1641) in collaboration with @ decalage2: http://www.sekoia.fr/blog/ms-office-exploit-analysis-cve-2015-1641/ and http://www.decalage.info/rtf_tricks
"MS Office CVE-2015-1641 恶意 Exploit 样本分析, 来自 Sekoia Blog︰ https://t.co/z61WgvTWr9 武器级 RTF 分析对抗技巧: https://t.co/YQsEaJgACM"
-

[ Windows ] Windows 10 RS1 14316 UAC again broken, and yet again with help of sysprep and dumbest way of whitelisting inside appinfo.dll
"Windows 10 RS1 14316 UAC 又出问题了,在 sysprep 和 appinfo.dll 内的白名单的帮助下可以再次绕过 UAC"
-

[ Windows ] Windows Kernel-Mode Drivers written in Rust https://github.com/pravic/winapi-kmd-rs
" Rust 语言写 Windows 内核态驱动, Github Repo: https://t.co/ee5wICPajo "