腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] Just released! The 2016 Symantec Internet Security Threat Report. The details: http://symc.ly/1XsTQVc #SymantecISTR https://t.co/fpg8MeO7AV
"赛门铁克发布 《2016 年互联网安全威胁报告》 ︰ https://t.co/lFtwX2AFxZ https://t.co/fpg8MeO7AV"
-

[ Attack ] 2013 DDoS Attacks on US Banking Sector Used Sweden's Military Servers http://ow.ly/10z8QZ
"据瑞典的《每日新闻》报道,瑞典军队的一批 Web 服务器遭劫持和攻击,参与了 2013 年针对美国银行的 DDoS 攻击: https://t.co/Nle8pAdsDi"
-

[ Browser ] Microsoft Edge supports an early version of the Web Authentication spec. Log in with your face or finger! Read more https://blogs.windows.com/msedgedev/2016/04/12/a-world-without-passwords-windows-hello-in-microsoft-edge/
"微软 Edge 支持无密码登陆,可以刷脸或指纹登陆, 来自 Edge Blog: https://t.co/raYZlXXxEJ"
-

[ Defend ] Intel® Software Guard Extensions SDK for Linux* Availability Update: Whenever I talk with developers about Int... http://intel.ly/23qiOMa
"Intel SGX 保护扩展 Linux 平台 SDK 可以下载了: https://t.co/sKelYKJxXs"
-

[ iOS ] Just updated #libirecovery to support iPhone SE and iPad Pro (9.7 inch) https://github.com/libimobiledevice/libirecovery.git
"libirecovery - 通过 USB 与 iOS 设备通信的工具, 是个扩平台的协议库实现,支持 Windows、Linux 和 OS X: https://t.co/ozdt9L12Ij 官网: http://www.libimobiledevice.org/ "
-

[ Malware ] Rokku Ransomware shows possible link with Chimera : https://blog.malwarebytes.org/threat-analysis/2016/04/rokku-ransomware/ cc: @ hasherezade || @ Malwarebytes https://t.co/d3NafG9KQv
"Rokku 勒索软件与 Chimera 有很多的相似性, 来自 MalwareBytes Blog︰ https://t.co/ewI9L5m3nz https://t.co/d3NafG9KQv"
-

[ Malware ] New post: ATM Malware on the Rise http://bit.ly/1T1iECo @ TrendMicro
"ATM 恶意软件数量上升, 来自 TrendMicro Blog: https://t.co/quskET7He0 "
-

[ Malware ] C&C Flaw Offers Glimpse into Dridex Operations | http://SecurityWeek.Com http://ow.ly/10xifI
" Buguroo 公司的研究员利用 Dridex 银行木马的漏洞,获取了 Dridex 的 C&C 控制界面访问权限,看到了有多少人的信息被盗取, 来自 SecurityWeek 的报道: https://t.co/jeNdaEi9gy 来自 Buguroo 的分析报告: https://buguroo.com/wp-content/uploads/2016/04/dridex_report_20160407.pdf "
-

[ Malware ] Manamecrypt – a ransomware that takes a different route https://blog.gdatasoftware.com/2016/04/28234-manamecrypt-a-ransomware-that-takes-a-different-route
"Manamecrypt(也叫 CryptoHost) — 另辟蹊径的一款勒索软件, 来自 GData Blog: https://t.co/ZNV8FGd6KG "
-

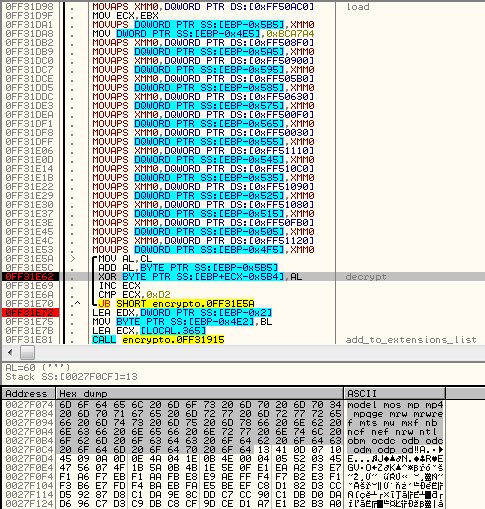
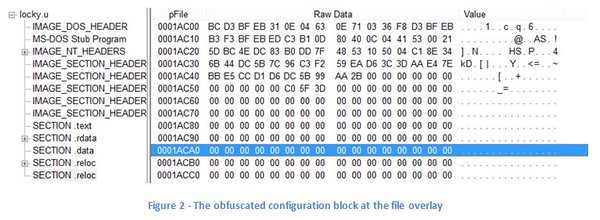
[ Malware ] New Locky Variant Implements Evasion Techniques : http://blog.checkpoint.com/2016/04/11/new-locky-variant-implements-evasion-techniques/ https://t.co/PAudFTxiOV
"Locky 勒索软件的新变种实现了新的检测逃逸技术, 来自 CheckPoint Blog ︰ https://t.co/48TuNhywFB https://t.co/PAudFTxiOV 前天推送了一篇 Palo Alto 对该逃逸技术的分析: http://researchcenter.paloaltonetworks.com/2016/04/unit42-ransomware-locky-teslacrypt-other-malware-families-use-new-tool-to-evade-detection/ "
-

[ Malware ] A great summary of Android Ransomware techniques and ecosystem by my ex-colleague Qing Dong: http://blogs.360.cn/360mobile/2016/04/12/analysis_of_mobile_ransomware/ (in Chinese)
"Android 勒索软件研究报告, 来自 360 移动安全团队: https://t.co/OvQZHalnci"
-

[ Malware ] ZeuS banking Trojan resurfaces as #Atmos variant - https://threatpost.com/zeus-banking-trojan-resurfaces-as-atmos-variant/117344/
"宙斯银行木马再次以 Atmos 变种出现, 来自 ThreatPost 的报道: https://t.co/N9J25XuoMu"
-

[ MalwareAnalysis ] Using reverse engineering techniques to see how a common malware packer works https://labs.detectify.com/2016/04/12/using-reverse-engineering-techniques-to-see-how-a-common-malware-packer-works/
"通过逆向看看常见的恶意软件壳是如何工作的, 来自 Detectify Labs: https://t.co/5WirhwvMsD"
-

[ Network ] Clandestine DNS lookups with gdns http://rud.is/b/2016/04/11/clandestine-dns-lookups-with-gdns/
"Google 最近推出 DNS-over-HTTPS API, 支持端到端认证的 DNS 查询, 这篇 Blog 基于 Gdns 实现隐蔽的 DNS 查询: https://t.co/Z1sO1fUUHh "
-

[ Others ] Static Identification of Program Behavior using Sequences of API Calls - https://insights.sei.cmu.edu/sei_blog/2016/04/static-identification-of-program-behavior-using-sequences-of-api-calls.html
"通过 API 调用序列静态识别程序的行为, 来自卡内基梅隆大学: https://t.co/8UDu4vxgs5"
-

[ Others ] Control Flow Hardening with Program Counter Encoding for ARM® Processor Architecture http://www.inase.org/library/2015/crete/COCI.pdf#page=32
"通过编码程序计数器保护控制流, 来自 CC/CSSP 2015 年的会议论文集: https://t.co/7ImfS3jfic"
-

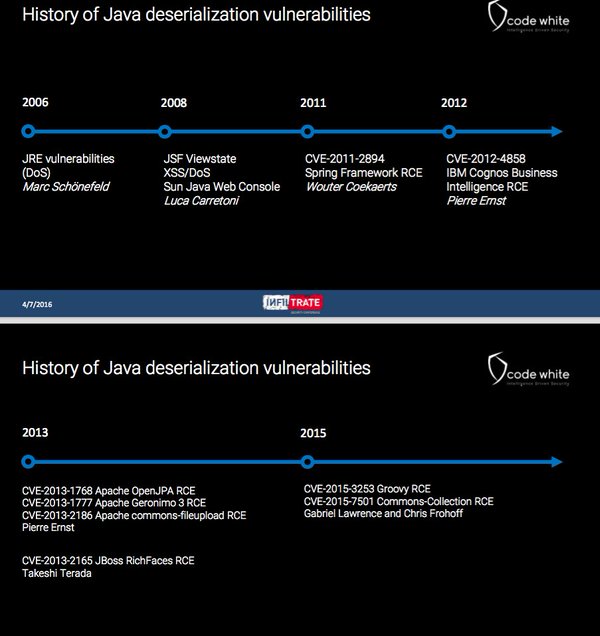
[ Others ] #infiltrate Java deserialization vuls by @ matthias_kaiser http://www.slideshare.net/codewhitesec/java-deserialization-vulnerabilities-the-forgotten-bug-class [tragedy in 4 acts, more to come] https://t.co/BS6nj8cBSM
"Java 反序列化漏洞的历史 - 被遗忘的 Bug 类型, 来自 InfiltrateCon 会议: https://t.co/qJ4ysMrPzn https://t.co/BS6nj8cBSM"
-

[ Others ] Exploiting PHP Serialization/Object Injection Vulnerabilities : https://crowdshield.com/blog.php?name=exploiting-php-serialization-object-injection-vulnerabilities cc: @ crowdshield
"PHP 序列化/对象注入漏洞的利用,来自 CrowdShield Blog ︰ https://t.co/A7XkfYBzfn "
-

[ Others ] Why MAC Address Randomization is not Enough : An Analysis of Wi-Fi Network Discovery Mechanisms : http://papers.mathyvanhoef.com/asiaccs2016.pdf (pdf)
"为什么 MAC 地址随机化还不够 - Wi-Fi 网络发现机制分析, Paper︰ https://t.co/OldgLJoFQU "
-

[ Pentest ] Getting the goods with CrackMapExec (Part 1) : https://byt3bl33d3r.github.io/getting-the-goods-with-crackmapexec-part-1.html cc: @ byt3bl33d3r
" CrackMapExec 实战 Part 1: https://t.co/5bi8RCo07y "
-

[ Popular Software ] Links to my @ InfiltrateCon and @ SyScan360 slide decks about Pwning Adobe Reader with XFA are now online on our blog http://siberas.blogspot.de
"滥用 Adobe Reader 内嵌的 XFA 引擎实现稳定的漏洞利用, XFA 指 Adobe 的 XML 表单架构, 来自 siberas 在 InfiltrateCon 和 SyScan 360 会议的演讲: https://t.co/ZYeqVvFyVZ"
-

[ Popular Software ] [SE-2012-01] Yet another broken security fix in IBM Java 7/8 http://goo.gl/fb/aoA1kv #FullDisclosure
"Broken security fix in IBM Java 7/8(CVE-2013-5456), 来自 FullDisclosure 公告 https://t.co/ifLembj4m0 "
-

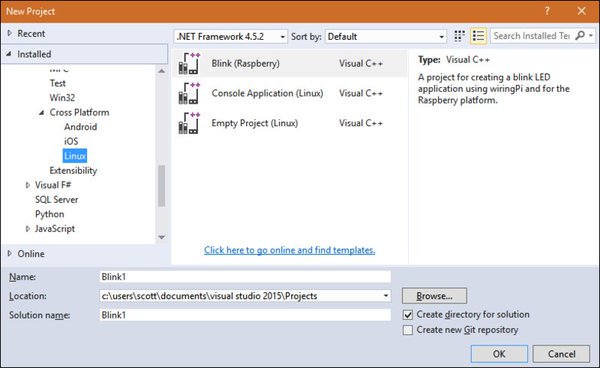
[ Programming ] Visual C++ for Linux and Raspberry Pi Development via @ shanselman http://bit.ly/1VeF9Hm @ shanselman #vs2015 https://t.co/dEn73nYGYM
"用 Visual Studio 为 Linux 和 树莓 Pi 开发程序: https://t.co/g55OkCOuGu https://t.co/dEn73nYGYM"
-

[ ReverseEngineering ] Reverse of a Mifair Laundry card system (github) https://github.com/LesMargoulins/Margoulineur2000
"洗衣机卡余额查询设备逆向(Margoulineur2000), Github Repo: https://t.co/GgJYQwTaMC"
-

[ Tools ] GEF - Multi-Architecture GDB Enhanced Features for Exploiters & Reverse-Engineers http://bit.ly/1qJAgtQ #infosec #hacking #pentest #tech
"GEF - 逆向增强版的 GDB 调试器, Python 语言编写,支持多种架构, Github Repo: https://t.co/HZfHTiXoDA "
-

[ Tools ] A new Metasploit module from @ ukstufus for generating CSV org charts from AD https://github.com/rapid7/metasploit-framework/pull/6377 https://t.co/diVQcuEkBK
"Metasploit 的新模块支持从 AD 域提取信息,生成企业的组织架构图: https://t.co/XriEf8DU68 https://t.co/diVQcuEkBK "
-

[ Web Security ] Git All the Payloads! A collection of web attack payloads: https://github.com/foospidy/payloads
"Web 攻击 Payloads 收集, Github Repo︰ https://t.co/Y4Jf5ulHhB"
-

[ Windows ] #MSFT releases 13 bulletins for 30 CVEs - MS16-039 under active attack. Plus a fix for a NTLM MiTM with a name. https://technet.microsoft.com/library/security/ms16-apr
"微软发布 4 月份补丁更新,本次共 13 个补丁,30 个 CVE: https://t.co/tIkShqgxWU"
-

[ Windows ] On #Badlock for Samba (CVE-2016-2118) and Windows (CVE-2016-0128): https://community.rapid7.com/community/infosec/blog/2016/04/12/on-badlock-cve-2016-2118-for-samba-and-windows via @ todb https://t.co/Wua23vJ5kG
"Rapid7 Blog 谈 Badlock 漏洞:Samba (CVE-2016-2118) 和 Windows (CVE-2016-0128): https://t.co/Wua23vJ5kG Badlock 的网站上的信息也更新了: http://badlock.org/ "