腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] New post: Mobile Devices Used to Execute DNS Malware Against Home Routers http://bit.ly/1VMsgn3 @ TrendMicro
"TrendMicro 最近发现有 IoT 攻击借助手机来完成,当手机访问恶意站点时,触发恶意 JavaScript 的下载,下载的 JavaScript 修改家用路由器的 DNS 配置。 TrendMicro 将其命名为 JS_JITON: https://t.co/dvJuPm5dwn "
-

[ Android ] Samsung exposes modem over USB which can be abused to enable ADB, make calls, send texts, and bypass lockscreen: https://github.com/ud2/advisories/tree/master/android/samsung/nocve-2016-0004
"三星手机通过 USB 可以访问 Modem 接口,攻击者可以滥用该接口,实现启用 ADB、打电话、发短信、绕过锁屏 ︰ https://t.co/ZubJtUIf0W 受影响的型号包括: Galaxy S6、Galaxy Note 3,Galaxy S4 系列"
-

[ Browser ] My birthday blog post on the difficulties of using SVG images with Content Security Policy: https://pokeinthe.io/2016/04/09/black-icons-with-svg-and-csp/
"SVG + CSP: 一碗索然无味的字母汤 ︰ https://t.co/zlia2raiHs"
-

[ IoTDevice ] New blog post: Discover the Unknown: Analyzing an IoT Device https://www.insinuator.net/2016/04/discover-the-unknown-analyzing-an-iot-device/
"发现未知︰ IoT 设备分析, 这篇 Blog 介绍 IoT 安全评估过程中所用的方法和工具: https://t.co/yTQUrRoGrg"
-

[ Malware ] Tool Released to Decrypt Petya Ransomware Infected Disks, (Mon, Apr 11th) https://isc.sans.edu/diary.html?storyid=20929&rss
"Petya 勒索软件的文件解密还原工具发布: https://t.co/X8H1GNggeC 密钥生成网站: https://petya-pay-no-ransom.herokuapp.com/ Github Repo: https://github.com/leo-stone/hack-petya "
-

[ Malware ] #Unit42 & @ Dell @ SecureWorks CTU find click-fraud #Ramdo #malware family continues to plague users http://bit.ly/23x57HJ
"点击欺诈恶意软件家族 Ramdo 分析,来自 Palo Alto Blog: https://t.co/qIwJQi5bv6"
-

[ Malware ] CryptoHost Decrypted: Locks files in a password protected RAR File http://www.bleepingcomputer.com/news/security/cryptohost-decrypted-locks-files-in-a-password-protected-rar-file/
"CryptoHost 勒索软件将文件锁定在一个密码保护的 RAR 文件中, 这篇 Blog 介绍如何解密: https://t.co/p0IpN8Wtqj"
-

[ Malware ] New post: Learning from Bait and Switch Mobile Ransomware http://bit.ly/1SaSVL0 @ TrendMicro
"以诱导转向法的方式了解手机勒索软件,伪装成成人网站的勒索软件,不仅加密设备,还会打开前置摄像头: https://t.co/u3UdlHRPrc "
-

[ Network ] The curious case of slow downloads http://blog.cloudflare.com/the-curious-case-of-slow-downloads/
"一桩下载速度缓慢的离奇案例, 来自 CloudFlare Blog: https://t.co/LD2eJOBLcc "
-

[ Others ] Uncovering a ransomware distribution operation – Part 1 https://reaqta.com/2016/04/uncovering-a-ransomware-distribution-operation/
"Crypt0L0cker 勒索软件传播行动调查报告,来自 Reaqta Blog,Part 1: https://t.co/8XgIfrFWUV"
-

[ Others ] MongoDB Injection - How To Hack MongoDB http://www.technopy.com/mongodb-injection---how-to-hack-mongodb.html
"MongoDB 注入 - How To Hack MongoDB: https://t.co/XLu8gusc8v"
-

[ Others ] Great ransomware analysis http://blog.talosintel.com/2016/04/ransomware.html
"勒索软件的过去、现在和将来, 来自 Talos Blog: https://t.co/Sh5BvUyHU8"
-

[ Others ] Hardening Measures in Android N Cripple System Utility and Security Applications https://code.google.com/p/android/issues/detail?id=205565
"过度限制的 Android N 权限控制, 来自 Android Issues: https://t.co/Hdf7lSqLpQ "
-

[ Others ] Mapping the Dark Web searching for illegal content http://securityaffairs.co/wordpress/46202/deep-web/dark-web-mapping.html
"Intelliagg 最近对 Dark Web 的调查报告 《Dark Web 里点一盏灯》, 来自 SecurityAffairs 的报道: https://t.co/gH62kUEETB 报告: http://deeplight.intelliagg.com/deeplight.pdf "
-

[ Others ] We just published the collection of gadgets used to bypass defensive #javadeser as shown in our RSA talk https://github.com/pwntester/SerialKillerBypassGadgetCollection
"能够绕过 Java 反序列化漏洞 "Look-Ahead" 保护方法的代码片段收集,来自作者在 RSA 会议的演讲: https://t.co/zgj81OZRtg "
-

[ Others ] Moxa Won’t Patch Publicly Disclosed Flaws Until August: https://threatpost.com/moxa-wont-patch-publicly-disclosed-flaws-until-august/117311/ via @ threatpost
"Moxa 公司表示 8 月份之前将不会修复 NPort 6110 工控设备的漏洞, 来自 ThreatPost 的报道: https://t.co/uw1hdkldIc"
-

[ Others ] Distributed ledgers - blockchain from Intel using Software Guard Extensions (SGX) - https://intelledger.github.io/introduction.html - source https://github.com/intelledger
"Intel 的 Sawtooth Lake 项目: https://t.co/r7ozAlhAoT Github Repo: https://t.co/YlaN2A870j "
-

[ ReverseEngineering ] Reverse engineering Blizzard's Warden : https://hackmag.com/uncategorized/deceiving-blizzard-warden/
"逆向暴雪的游戏反作弊工具 Warden ︰ https://t.co/iZjPaWjAsy"
-

[ ReverseEngineering ] Important Code Constructs in Assembly Language-Part 1 http://resources.infosecinstitute.com/important-code-constructs-in-assembly-language-part-1/
"恶意软件逆向分析系列文章 - 在汇编语言中识别重要的代码结构(循环、Switch、变量作用域), 来自 InfoSec Blog: https://t.co/X4SY1QTa4i "
-

[ ThirdParty ] CVE Request: Qemu: net: buffer overflow in MIPSnet emulator: Hello, Qemu emulator built with the MIPSnet c... http://bit.ly/1qKBSDw
"CVE 申请: Qemu MIPSnet 模拟器缓冲器溢出: https://t.co/XKTyoN8wjz Patch: https://lists.gnu.org/archive/html/qemu-devel/2016-04/msg01131.html RedHat 的 Bug 追踪: https://bugzilla.redhat.com/show_bug.cgi?id=1326082 "
-

[ ThreatIntelligence ] Automated Reverse Image Search Part 2: Vimeo | Automating OSINT Blog http://bit.ly/1UVfsM4 #osint #python
"自动化地图像反向搜索 Part 2 ︰ 自动化地处理 Vimeo 的视频预览图片: https://t.co/0NCscno5Tp Part 1: 自动化地处理 Youtube 的视频预览图片: http://www.automatingosint.com/blog/2015/11/osint-youtube-tineye-reverse-image-search/ 关于图片反向搜索技术: http://www.automatingosint.com/blog/2015/05/osint-reverse-image-search/ "
-

[ Tools ] INURLBR – Advanced Search Engine Tool http://www.darknet.org.uk/2016/04/inurlbr-advanced-search-engine-tool/
"INURLBR — 面向安全研究人员、基于 PHP 的高级搜索引擎工具: https://t.co/EZAbVI5QJH"
-

[ Tools ] go-debug: A Go Debugger for the Atom Editor - https://github.com/lloiser/go-debug https://t.co/ByNQgp3iaX
"Atom 编辑器的 Go 语言调试器: https://t.co/vZx5BWZb97 https://t.co/ByNQgp3iaX"
-

[ Tools ] W0w, finally an IDA emulator plugin based on Unicorn! This is what we are all longing for \O/ cc @ sk3wl @ timstrazz https://github.com/36hours/idaemu
"idaemu - IDA 的一个模拟器插件,基于 Unicorn 引擎,目前仅支持 x86 系列指令集,ARM 支持正在开发中: https://t.co/nQL1zlrIZM"
-

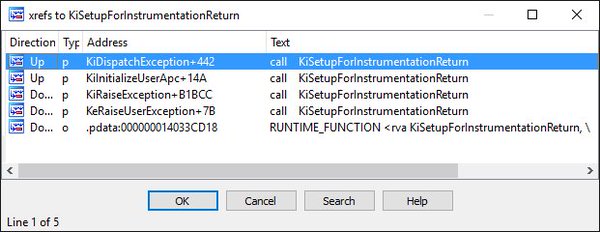
[ Windows ] Windows 10 Hooking Nirvana explained http://sww-it.ru/?p=1332 https://t.co/EVtm9gsvy6
"Windows 10 Hooking Nirvana 是一种隐蔽的插桩技术, 之前 Alex Ionescu 在 Recon 2015 会议也谈过。 这篇 Blog 作者分析 Hooking Nirvana 是如何工作的: https://t.co/SpJeaebZfE https://t.co/EVtm9gsvy6"
-

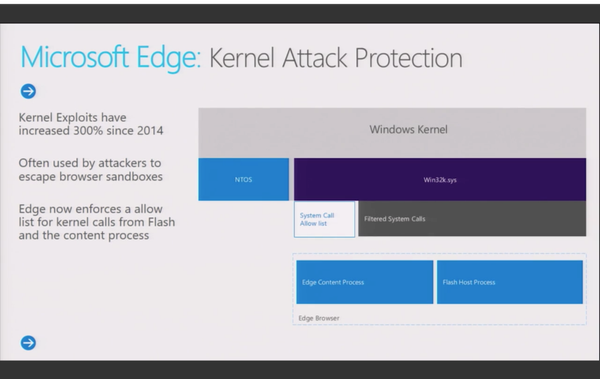
[ Windows ] Win10 getting a syscall filter! Shame only for win32k, no matter what Dave said in the talk to imply otherwise :-( https://t.co/8BgJBAFBz0
"Win10 有一个 syscall filter! 可惜只针对 win32k: https://t.co/8BgJBAFBz0"