腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Android Studio 2.0: Now available as a *stable* release. Instant Run, faster builds, new emulator, and much more! http://android-developers.blogspot.com/2016/04/android-studio-2-0.html
"Android Studio 2.0 稳定版发布,官方 Blog: https://t.co/yhw3T1ofmF"
-

[ Android ] New Android emulator is sweet https://developer.android.com/tools/devices/emulator.html
"在 Android 模拟器中运行 APP,来自 Android 开发者 Blog: https://t.co/xMn6VCcKLG"
-

[ Attack ] Hack on Ukranian power grid highlights the urgency for accelerated threat intelligence in industrial control systems http://bit.ly/1MVboZr
"乌克兰电网攻击凸显出威胁情报在工业控制系统中的重要性和紧迫性, 来自 Palo Alto Blog: https://t.co/KBfvZu0PKd "
-

[ Browser ] Information theft attacks abusing browser's XSS filter http://www.mbsd.jp/blog/20160407.html
"滥用浏览器的 XSS 过滤器,窃取信息, 来自 MBSD Blog: https://t.co/WE6o1KzBPw"
-

[ Browser ] Putting Users in Control of Flash - Microsoft Edge now intelligently auto-pauses ancillary Flash content https://blogs.windows.com/msedgedev/2016/04/07/putting-users-in-control-of-flash/
"Edge 浏览器将会取消自动播放 Flash 动画,除非用户手动点击播放: https://t.co/WrZuOEn4RQ"
-

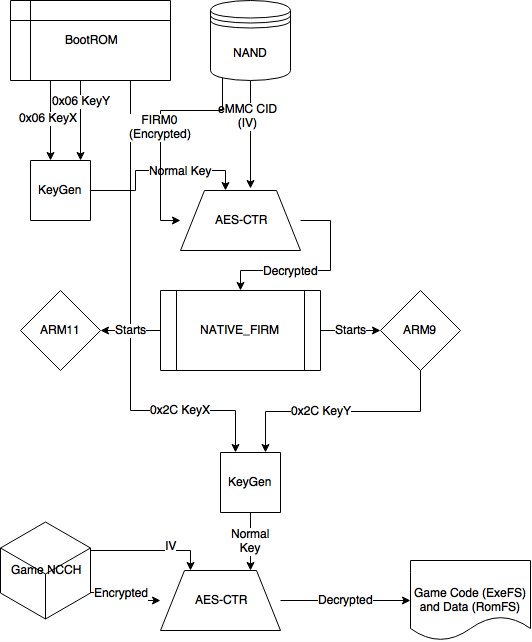
[ Crypto ] The 3DS Cryptosystem http://yifan.lu/2016/04/06/the-3ds-cryptosystem/ https://t.co/fzeO2ncTDW
"任天堂 3DS 游戏机的加密系统: https://t.co/2MXQByRi04 https://t.co/fzeO2ncTDW"
-

[ Detect ] How to Detect Ransomware with FileAudit http://www.isdecisions.com/blog/it-security/how-to-detect-ransomware-with-fileaudit/
"如何用 FileAudit 工具检测勒索软件: https://t.co/zNLHPgM5xu"
-

[ Hardware ] Hacking Tesla Model S : http://www.su-tesla.space/2016/04/hack-s.html (obtain_root script ...? ) https://t.co/K3mW8JG4hS
"Hacking Tesla Model S - 获取触摸屏的 ROOT 权限: https://t.co/MCdhQfooHz https://t.co/K3mW8JG4hS"
-

[ Hardware ] Cold-boot attacks on scrambled DDR3 memory : http://www.dfrws.org/2016eu/proceedings/DFRWS-EU-2016-7.pdf (pdf)
"针对杂乱 DDR3 内存的冷启动攻击, Paper ︰ https://t.co/ESTdpKj4PW "
-

[ Industry News ] Hacking Team In Trouble Again -- Banned From Selling Outside Of Europe @ Forbes http://www.forbes.com/sites/thomasbrewster/2016/04/06/hacking-team-in-trouble-again-banned-from-selling-outside-of-europe/
"Hacking Team 又遇到麻烦了,不能再向欧洲以外的国家销售恶意软件, 来自 Forbes Blog: https://t.co/mPKtbaedYv"
-

[ Linux ] KPlugs - a user-mode interface for plugging into the linux kernel http://www.kplugs.org/
"KPlugs - 一个内核态模块,他在用户态暴露接口,让用户态程序可以在内核态执行脚本: https://t.co/RvG3Y69049 "
-

[ Linux ] vuls : Vulnerability scanner for Linux, agentless, written in golang : https://github.com/future-architect/vuls
"Linux 漏洞扫描器,无 Agent, Golang 语言编写 ︰ https://t.co/LXUmq9ePRw"
-

[ Mac OS X ] Talos Blog: Vulnerability Deep Dive: Exploiting the Apple Graphics Driver and Bypassing KASLR http://tinyurl.com/gwtz39z
"OS X 图形驱动漏洞利用 & KASLR Bypass(CVE-2016-1743), 来自 Talos Blog: https://t.co/R4HKvtmwkc"
-

[ Malware ] Andromeda under the microscope https://blog.avast.com/andromeda-under-the-microscope
"显微镜下的仙女座(Andromeda)恶意软件家族, 来自 Avast Blog: https://t.co/gUqd5KANdF"
-

[ Malware ] Free Star木马分析与追溯 - http://bobao.360.cn/learning/detail/2828.html
"Free Star木马分析与追溯, 来自 360 安全播报: https://t.co/lmSql82Hrc"
-

[ Malware ] Petya到底是个什么鬼 - http://blogs.360.cn/360safe/2016/04/05/what_is_petya/
"Petya 到底是个什么鬼, 来自 360 Blog: https://t.co/UXkIP1hawE"
-

[ Network ] Forwarding-Loop Attacks in Content Delivery Networks. Nice idea, interesting DoS attacks: https://www.internetsociety.org/sites/default/files/blogs-media/forwarding-loop-attacks-content-delivery-networks.pdf
"CDN 网络中的转发循环(Forwarding-Loop)攻击, 来自清华大学陈建军博士的 Paper ︰ https://t.co/PRW5oAfzxt Freebuf 上的文章: http://www.freebuf.com/news/96874.html "
-

[ Others ] Secure Coding with Python : https://www.owasp.org/images/c/cb/OWASP_Romania_Branca.pdf (pdf/Slides) #b2b
"Python 安全编码,来自 OWASP 的 Slides,其中列举了大量的示例 ︰ https://t.co/4VdnBF1tBK "
-

[ Others ] Exploiting Existing Replicas of Stack Pointer in the Register File for Error Detection http://www.median-project.eu/wp-content/uploads/MEDIAN-Finale-s3-1.pdf
"利用寄存器堆(Register File)中的栈指针副本实现快速错误检测, Paper: https://t.co/nHlEh5R1gE "
-

[ Others ] Unpatchable – Living with a vulnerable implanted device https://www.insinuator.net/2016/04/unpatchable-living-with-a-vulnerable-implanted-device/
"Unpatchable — 带着一个有漏洞又无法修复的植入式医疗设备生活, 来自 Troopers 2016 会议: https://t.co/ngFO7XGUuU Slides: https://www.troopers.de/media/filer_public/7b/55/7b554af2-8462-4299-9ffc-9fe4be9ab6df/2016-03-17-troopers-til-publisering.pdf "
-

[ Others ] Exagrid fixes hardcoded, default credential exposures CVE-2016-1560 & CVE-2016-1561: https://community.rapid7.com/community/infosec/blog/2016/04/07/r7-2016-04-exagrid-backdoor-ssh-keys-and-hardcoded-credentials reported by @ egyp7 at @ rapid7
"ExaGrid 存储设备存在后门 SSH Key 和硬编码凭据信息(CVE-2016-1560 & CVE-2016-1561), 来自 Rapid7 Blog : https://t.co/8fls8OSbzO "
-

[ Others ] CFFI - C Foreign Function Interface for Python. Interact with almost any C code from Python. https://cffi.readthedocs.org/en/latest/
"CFFI - 从 Python 中直接与 C 函数交互的接口: https://t.co/0fgTOuT1kr"
-

[ Others ] PHP <= 7.0.4/5.5.33 - SNMP Format String Exploit : https://www.exploit-db.com/exploits/39645/
"PHP <= 7.0.4/5.5.33 - SNMP 格式化字符串 Exploit PoC ︰ https://t.co/7dBGZPElJc"
-

[ ThirdParty ] Oops, nice gcc bug. https://bugzilla.redhat.com/show_bug.cgi?id=1262846 #bughappens
"gcc std::random_device 随机性可预测漏洞(CVE-2015-5276): https://t.co/OaFmvzWJND"
-

[ Tools ] Vis : A Vim Like Text Editor : https://github.com/martanne/vis ; https://asciinema.org/a/41361
"Vis: 像 Vim 的一个代码编辑器 ︰ https://t.co/RwJw2ECSgK https://t.co/yHLbo3q8VX"
-

[ Tools ] WebTorrent Desktop – Open source streaming torrent client (for OS X, Windows, and Linux ) : https://webtorrent.io/desktop
"WebTorrent - 开源流式 torrent 客户端 (支持 OS X、 Windows 和 Linux) ︰ https://t.co/O88vTw2I8f"
-

[ Windows ] Bash on Ubuntu on Windows – Download Now! : https://blogs.msdn.microsoft.com/commandline/2016/04/06/bash-on-ubuntu-on-windows-download-now-3/ https://t.co/iGUBXXWKwe
"Bash on Ubuntu on Windows 现在可以下载了: https://t.co/bpOS4K4gGj https://t.co/iGUBXXWKwe"
-

[ Windows ] 异常中的异常——借助系统异常处理特例实现匪夷所思的漏洞利用 - http://xlab.tencent.com/cn/2016/04/05/exception-in-exception/ by @ tombkeeper
"异常中的异常——借助系统异常处理特例实现匪夷所思的漏洞利用, 来自玄武实验室 Blog, 作者为 tombkeeper: https://t.co/1UvSvlycEP "
-

[ WirelessSecurity ] Reverse Engineering Digital Signals : https://www.fleark.de/keyfob.pdf (Slides*)
"数字信号逆向, Slides ︰ https://t.co/kSOOlkIilZ "