腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] All of the presentation materials for the Android browser @ InfiltrateCon talk can be found here - https://github.com/LifeForm-Labs/all_your_browsers_belong_to_us
"All Your Browsers Belong To Us, 来自 rotlogix 在 Infiltrate 会议的演讲,谈 Android 浏览器漏洞利用: https://t.co/8Vg9NkRwB3"
-

[ Android ] Release a PoC for CVE-2016-0846, IMemory bug leak to arbitrary memory read/write, first reported by @ tiraniddo https://github.com/secmob/CVE-2016-0846
"Android IMemory 接口 OOB 漏洞导致的内存读写 PoC (CVE-2016-0846), 来自 oldfresher 的 Github Repo: https://t.co/DhS81nyTsN 该漏洞最早由 James Forshaw 发现: https://bugs.chromium.org/p/project-zero/issues/detail?id=706 "
-

[ Android ] New advisory released: A Bluetooth pairing authentication bypass in Android discovered by @ bouuntyyy https://labs.mwrinfosecurity.com/advisories/bluetooth-pairing-authentication-bypass/
" Android 蓝牙配对身份认证绕过漏洞(CVE-2016-0850), 来自 MWR Labs 的公告: https://t.co/ONiflSSGLQ "
-

[ Attack ] New Blog Post - PHP Files in CMS, Targeted for Alteration ^AF http://blog.jpcert.or.jp/2016/04/php-files-in-cms-targeted-for-alteration.html
"JPCERT 最近监测到一些网站的 PHP 文件遭到篡改并且注入了恶意代码: https://t.co/VHa2y1W3gC"
-

[ Browser ] ZDI-16-224: Google Chrome libANGLE glGetUniformfv Buffer Overflow Remote Code Execution Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-224/
"ZDI-16-224 ︰ Google Chrome 浏览器 libANGLE glGetUniformfv 缓冲区溢出 RCE,今年 Pwn2Own 韩国选手 lokihardt 用该漏洞打的 Chrome: https://t.co/FxMnkgJWro"
-

[ Browser ] Here are my "On the Security of Browser Extensions" slides: http://stuff.iceqll.eu/slides/2016-on-the-security-of-browser-exts/
"浏览器扩展的安全研究, 在线 Slides ︰ https://t.co/wW55X89xwp"
-

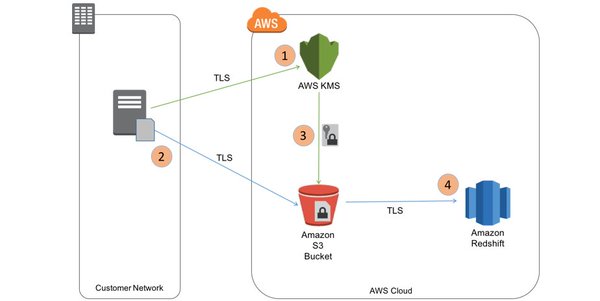
[ Cloud ] New on our AWS #BigData Blog: "Encrypt Your Amazon Redshift Loads with Amazon S3 & AWS KMS" http://amzn.to/1YhZPwj https://t.co/RqbEN1CAqU
"用 Amazon S3 和 AWS KMS 加密 Redshift: https://t.co/z1dMRzKJxD Redshift 是 Amazon 推出的一种快速、完全托管的 PB 级数据仓库"
-

[ Crypto ] TLSkex : Harnessing virtual machine introspection for decrypting TLS communication : http://www.dfrws.org/2016eu/proceedings/DFRWS-EU-2016-12.pdf (pdf)
"TLSkex ︰ 利用虚拟机自省技术解密 TLS 加密通信, 来自 DFRWS 2016 会议 ︰ https://t.co/Bc2PStgGDC "
-

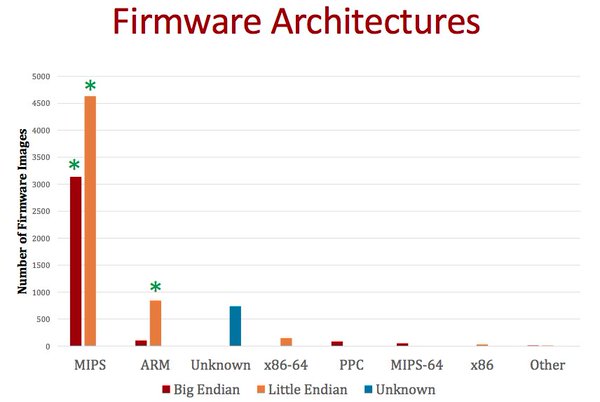
[ Firmware ] #NDSS2016 FIRMADYNE: Dynamic analysis of 23k embedded firmware https://www.internetsociety.org/sites/default/files/07_1-ndss2016-slides.pdf [git https://github.com/firmadyne https://t.co/kI07YRDPIZ
"Firmadyne - 嵌入式固件自动化分析框架,之前推送过这个工具,这次是在 NDSS 2016 会议的演讲: https://t.co/hyvbbQV2Xs Github Repo: https://t.co/9ovJLvYoM7 https://t.co/kI07YRDPIZ "
-

[ Forensics ] Automatic profile generation for live Linux Memory analysis : http://www.dfrws.org/2016eu/proceedings/DFRWS-EU-2016-2.pdf (pdf)
"自动生成用于实时 Linux 内存分析的 Profile 文件, 来自 DFRWS 2016 会议 ︰ https://t.co/7B4ScbL6fm "
-

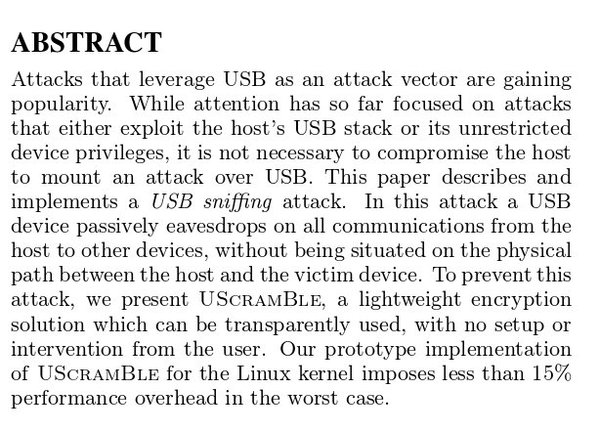
[ Hardware ] Turns out you can run a USB device in "promiscuous" mode. Check out our new work http://static.securegoose.org/papers/uscramble_cr.pdf @ sictune https://t.co/B2mCpZDNnV
"USB 窃听攻击的透明防御技术: https://t.co/79uK58I85i https://t.co/B2mCpZDNnV"
-

[ Hardware ] Neat find @ dklinedinst http://www.kb.cert.org/vuls/id/615456
"车辆监控设备 Lemur BlueDriver 在建立蓝牙连接时没有认证用户身份,汽车售后经常使用这种设备获取车辆信息,而这个漏洞可以允许周围人直接连上蓝牙,接入汽车 CAN Bus: https://t.co/7cKgEdgMxx"
-

[ Industry News ] Govt Bug Bounty program - Peter Cook http://www.defense.gov/News/News-Releases/News-Release-View/Article/709818/statement-by-pentagon-press-secretary-peter-cook-on-dods-partnership-with-hacke#.VwdUVG-c3gU.twitter
"美国国防部(DOD) 与 HackerOne 合作举办 Bug Bounty 项目: https://t.co/XI134OAdqO"
-

[ Malware ] Cylance Quick Brief: TeslaCrypt 4.0 https://blog.cylance.com/cylance-quick-brief-teslacrypt-4.0
"TeslaCrypt 4.0 快速概览, 来自 Cylance Blog: https://t.co/fnIG2IXMo2"
-

[ Malware ] ModPOS: A Framework Lurking in Point-of-Sale System Kernels http://labs.lastline.com/modpos-a-framework-lurking-in-point-of-sale-system-kernels
"ModPOS - 潜伏在 PoS 系统内核中的框架: https://t.co/N6xVXRVjuR"
-

[ Network ] "El flagelo del ID numérico" Slides de la presentación en PROTOSEC 2016 [PDF en inglés] http://www.fundacionsadosky.org.ar/pub/2016-03-30-Protosec2016-iarce.pdf
"网络协议中数字标识符的诅咒, 来自 Protosec 2016 会议: https://t.co/90epWuSb9X"
-

[ NetworkDevice ] Juniper removes Dual_EC from ScreenOS. https://threatpost.com/juniper-completes-removal-of-dual_ec/117297/ via @ threatpost
"Juniper 将从 ScreenOS 中移除 DUAL_EC_DRBG 和 ANSI X9.31 PRNG 两个有争议的随机数发生器组件, 来自 ThreatPost 的报道: https://t.co/VbsPcq7ZVi"
-

[ Others ] Attacks on Biometric Systems : A Case Study in Fingerprints : http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.10.7168&rep=rep1&type=pdf (pdf)
"攻击生物特征识别系统 ︰ 指纹案例,来自密歇根州立大学的 Paper︰ https://t.co/t1UyI0tSkw "
-

[ Others ] The #DeepLearning textbook is now complete! Check it out. #MachineLearning http://www.deeplearningbook.org/ https://t.co/25tkmfTcwP
"深度学习(Deep Learning)(书籍): https://t.co/vwjgRC8YhD https://t.co/25tkmfTcwP"
-

[ Others ] Breaking Semantic Image CAPTCHAs - Schneier on Security https://www.schneier.com/blog/archives/2016/04/breaking_semant.html
"基于深度学习技术,打败语义图片验证码, Paper: http://www.cs.columbia.edu/~polakis/papers/sivakorn_eurosp16.pdf "
-

[ Others ] #Unit42 finds #Locky #ransomware, #TeslaCrypt, & other #malware families use new tool to evade detection http://bit.ly/1qcp3RI
"Palo Alto 最近发现 Locky、TeslaCrypt 等恶意软件正在使用一种新工具逃逸检测: https://t.co/GxdSnUZk47"
-

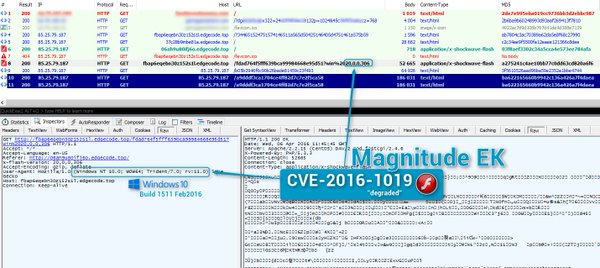
[ Popular Software ] Killing a zero-day in the egg: Adobe CVE-2016-1019 - https://www.proofpoint.com/us/threat-insight/post/killing-zero-day-in-the-egg https://t.co/QWLR0NVM6j
"Killing a Zero-Day in the Egg: Adobe CVE-2016-1019: https://t.co/6e9dayfVuo https://t.co/QWLR0NVM6j FireEye 对这个漏洞的分析: https://www.fireeye.com/blog/threat-research/2016/04/cve-2016-1019_a_new.html "
-

[ Popular Software ] #Adobe #Flash Player #security updates available (APSB16-10) - details @ http://adobe.ly/1VbLVh1
"Adobe Flash 发布补丁更新公告(APSB16-10),本次修复 24 个漏洞,包括一个野外被利用的漏洞: https://t.co/bqVsqQo5li "
-

[ Popular Software ] ZDI-16-228: (Pwn2Own) Adobe Flash JPEG-XR Parsing Stack Buffer Overflow Remote Code Execution Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-228/
"ZDI-16-228: Adobe Flash JPEG-XR 解析栈缓冲区溢出 RCE,腾讯电脑管家团队用该漏洞打的 Pwn2Own 比赛: https://t.co/SYRuZfsDp8"
-

[ Tools ] .@ _fel1x shared a cool tool for efficient, high-speed memory tracing: http://simutrace.org/
"Simutrace 项目 - 高效的内存 Trace︰ https://t.co/8aw0EGJDj2 "
-

[ Tools ] Pazuzu: reflective DLL to run binaries from memory http://www.shelliscoming.com/2016/04/pazuzu-reflective-dll-to-run-binaries.html
"Pazuzu︰ 利用反射式 DLL 注入技术,在内存中执行二进制: https://t.co/IVupjvjDAv "
-

[ Tools ] I wrote a simple IOCTL decoder to demonstrate how to parse binary data using bit math in #PowerShell. https://gist.github.com/mattifestation/844d01bd5c378f9b1f52d76219deaf0f
"在 PowerShell 中解析 IO Control Code: https://t.co/5hhpyEJYjP"
-

[ Tools ] We're releasing our tools for collecting kernel logs from our servers, check it out here: https://github.com/facebook/fbkutils
"Facebook 开源了一个内核扩展工具 fbkutils,Facebook 用这个工具从所有的 Linux 服务器中收集内核日志, Github Repo ︰ https://t.co/SXfvw5YDhg"
-

[ Tools ] WAFW00F allows one to identify and fingerprint Web Application Firewall (WAF) products protecting a website https://github.com/sandrogauci/wafw00f
"WAFW00F - 用于检测和识别 WAF 产品的工具,可以识别出 30 多种 WAF: https://t.co/YYAhYsEOsq"
-

[ Tools ] Hack all the IPV6 things... (H/T @ DaveMarcus) https://goo.gl/y1dfm7
"ipv6tools - 用于对启用 IPv6 的网络做健壮性测试的工具: https://t.co/0PlfOaAIJ9"