腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] The evolution of mobile ransomware https://blog.avast.com/the-evolution-of-mobile-ransomware
"手机勒索软件的发展历程, 来自 Avast Blog: https://t.co/VvQy8DXcB7 "
-

[ Android ] Trojan found in more than 100 Android apps on Google Play Store https://www.grahamcluley.com/2016/04/advertising-trojan-100-android-apps-google-play-store/
"Google Play Store 在超过 100 款 Android Apps 中发现了 Android.Spy.277.origin 木马: https://t.co/66eP6RxJuh "
-

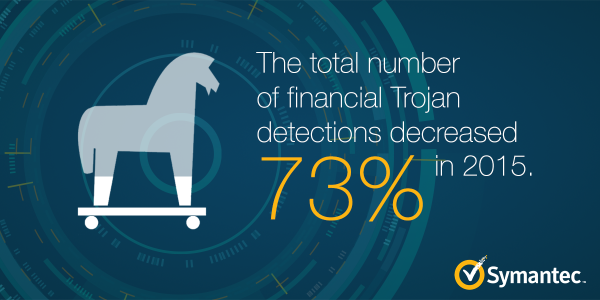
[ Attack ] Financial Trojan detection has dropped, but the #malware family upped their game. Read on: http://symc.ly/1UVKgws https://t.co/noAyR75yOI
"2015 年金融类木马感染量有 73% 的下降 ︰ https://t.co/8Lc7SeLFgC https://t.co/noAyR75yOI"
-

[ Browser ] New write-up by @ avlidienbrunn: CSP: bypassing form-action with reflected XSS http://labs.detectify.com/2016/04/04/csp-bypassing-form-action-with-reflected-xss/ https://t.co/lW4uKFgc4E
"利用反射式 XSS 绕过 CSP form-action 限制, 来自 detectify labs: https://t.co/AzKEQrEbvc https://t.co/lW4uKFgc4E"
-

[ Defend ] Security Rules for Email: https://matt.sh/security-rules-for-email
"电子邮件安全法则 - 如何评估电子邮件的安全性 ︰ https://t.co/1GmGCqMPix"
-

[ Fuzzing ] I'm doing a talk with @ 4c1d3 on Linux filesystem fuzzing using @ lcamtuf's AFL at Vault 2016: http://sched.co/68kL http://events.linuxfoundation.org/sites/events/files/slides/AFL%20filesystem%20fuzzing%2C%20Vault%202016.pdf
"基于 AFL 的 Linux 文件系统 Fuzz, 来自 Vault 2016 会议: https://t.co/Dwagx2qcWK https://t.co/Op5cYf7MMY"
-

[ iOS ] New blog post: Enabling Serial I/O on iOS Devices http://embeddedideation.com/2016/04/06/enabling-serial-io-on-ios-devices/
"在 iOS 设备上启用串行 I/O: https://t.co/mhEpmr1tyE "
-

[ Linux ] CVE-2016-3672 - Unlimiting the stack not longer disables ASLR http://goo.gl/fb/do7eI3 #FullDisclosure
"Linux 内核将 RLIMIT_STACK 资源限制设置为无限可以禁用 ASLR(CVE-2016-3672), 来自 FullDisclosure 公告: https://t.co/i8vErmHd8P 漏洞的详细分析: http://hmarco.org/bugs/CVE-2016-3672-Unlimiting-the-stack-not-longer-disables-ASLR.html "
-

[ Linux ] Ubuntu Patches Kernel Vulnerabilities https://threatpost.com/ubuntu-patches-kernel-vulnerabilities/117229/
"Ubuntu 昨天(6 号)发布补丁更新,修复了多个内核漏洞, 来自 ThreatPost 的报道: https://t.co/bWIbKsPOK2 官方的公告: http://www.ubuntu.com/usn/usn-2946-1/ "
-

[ Mac OS X ] Our 1st guest blog post: 'Analysis of an Intrusive Cross-Platform Adware; OSX/Pirrit' ->https://objective-see.com/blog.html Mahalo @ 0xAmit! #OSXAdware
"跨平台的恶意广告软件 OSX/Pirrit 分析: https://objective-see.com/blog/blog_0x0E.html "
-

[ Malware ] Samsam may signal a new trend of targeted ransomware http://www.symantec.com/connect/ko/blogs/samsam-may-signal-new-trend-targeted-ransomware
"Samsam 勒索软件标志着一个新趋势 - 定向勒索攻击到来, 来自 Symantec Blog: https://t.co/bzMJtB159H "
-

[ Malware ] Decrypting PowerWare Ransomware https://www.alienvault.com/open-threat-exchange/blog/powerware-or-poshcoder-comparison-and-decryption
"Alien Vault 对 PowerWare 勒索软件的分析: https://t.co/qIpRIbPJ0h"
-

[ Operating System ] Subgraph OS: A hardened OS that prioritizes security http://ow.ly/10jQQu
"Subgraph OS - 一个把安全性放在高优先级的操作系统: https://t.co/LRzWF2s95k "
-

[ Others ] USB key drop study is here: https://zakird.com/papers/usb.pdf
"大多数人真的会捡起他们发现的 U 盘,并且插进电脑。 这篇 Paper 讲述了一个实验: 将 297 个 U 盘扔到校园, 看到底有多少人会捡起并且插进电脑︰ https://t.co/oOL6IUHVWe"
-

[ Others ] Rupture, "A framework for BREACH and other compression-based crypto attacks" https://github.com/dionyziz/rupture from BH Asia https://www.blackhat.com/docs/asia-16/materials/asia-16-Karakostas-Practical-New-Developments-In-The-BREACH-Attack.pdf
"前几天推送过 rupture 这个工具(边信道攻击框架,可以攻击基于压缩的加密算法): https://t.co/6fd6cPadV6 这次是作者在 BlackHat Asia 2016 会议的演讲, 谈 BREACH 攻击的新方法: https://t.co/Pd74jsgpA3"
-

[ Others ] Safe Clearing of Private Data. http://www.viva64.com/en/b/0388/ (#cpp, #memset, #security, #securecoding, #vulnerability) https://t.co/Ogws4M926s
"私有数据的安全擦除, 来自 PVS-Studio Blog: https://t.co/ml9IWJZ4d2 https://t.co/Ogws4M926s"
-

[ Popular Software ] Flash CVE-2016-1019 being actively exploited, advisory: https://helpx.adobe.com/security/products/flash-player/apsa16-01.html with credits to @ kafeine and @ _clem1
"Flash CVE-2016-1019 漏洞正在野外被利用, Adobe 发布紧急更新: https://t.co/SJFDGVAR3w"
-

[ Popular Software ] New post: A Root Cause Analysis of the Recent Flash Zero-Day Vulnerability, CVE-2016-1010 http://bit.ly/22bCgX4 @ TrendMicro
"Flash 最近的 0Day CVE-2016-1010 漏洞根本原因分析, 来自 TrendMicro Blog: https://t.co/FaAn4znFx2 "
-

[ SecurityProduct ] Panda Security 2016 Home User Products - Privilege Escalation http://goo.gl/fb/Je55rf #FullDisclosure
"Panda 安全软件家庭用户版 v16.0.1 存在 SYSTEM 提取漏洞, 来自 FullDisclosure 公告: https://t.co/cKvFU300do "
-

[ ThirdParty ] new SSL test framework in OpenSSL https://github.com/openssl/openssl/commit/453dfd8d5ee0893146e0fb61a5978ab59ba95c01
"OpenSSL 官方代码库中加入了一个新的测试框架, Github Commit 日志: https://t.co/EFJcaGZCz0"
-

[ Tools ] Usercorn is a fantastic binary emulator using Unicorn engine! Try to see its magic: https://github.com/lunixbochs/usercorn https://twitter.com/lunixbochs/status/717584959565762560
"Usercorn - 基于 Unicorn 引擎的二进制模拟器,支持模拟内核、系统、用户态程序 ︰ https://t.co/pRUjdlc7Td https://t.co/8o9wPlihDd"
-

[ Tools ] New post and tool! ADOffline written by @ ukstufus, details on creating the offline SQL database from AD at https://labs.mwrinfosecurity.com/blog/offline-querying-of-active-directory
"ADOffline - Active Directory 离线 SQL 查询工具, MWR Blog: https://t.co/dU6FOAgc42 Github Repo: https://github.com/stufus/ADOffline "
-

[ Tools ] Aggressor Script’s Secret mIRC Scripting Past http://blog.cobaltstrike.com/2016/04/06/aggressor-scripts-secret-mirc-scripting-past/ https://t.co/dXEGCju8kT
"Aggressor Script 是 Cobalt Strike 的脚本引擎,这篇 Blog 谈谈 Aggressor Script 的历史: https://t.co/rHtHTRU3LZ https://t.co/dXEGCju8kT"
-

[ Tools ] My newest post! Advanced Burp Suite #cybersecurity #infosec @ Burp_Suite http://hack-ed.net/2016/04/02/advanced-burp-suite/
"Burp Suite 高级教程: https://t.co/Fm8xDvI1YU"
-

[ Tools ] Python Decoders for Common Remote Access Trojans https://github.com/kevthehermit/RATDecoders #RE #malware
"常见远控木马的 Python 解码器,可以从远控木马中提取配置文件, Github Repo: https://t.co/EiYipbbSH1 "
-

[ Tools ] Smile - Statistical Machine Intelligence and Learning Engine http://buff.ly/1S0tbAX
"Smile - 统计型机器智能和机器学习引擎: https://t.co/R7xt6NWt1i"
-

[ Web Security ] XSS Attacks through PATH https://speakerdeck.com/masatokinugawa/xss-attacks-through-path
"基于路径的 XSS 攻击: https://t.co/79tA3RHy8e"
-

[ Web Security ] Operating System Based Redirection with Apache mod_rewrite https://bluescreenofjeff.com/2016-04-05-operating-system-based-redirection-with-apache-mod_rewrite/ (post #3 of Strengthening Your Phishing with mod_rewrite)
"通过 Apache mod_rewrite 实现为不同操作系统的用户定制 Payload,这可以帮助钓鱼: https://t.co/h220IaYWmq "
-

[ Windows ] WMI Persistence http://windowsir.blogspot.com.tr/2016/04/cool-stuff-re-wmi-persistence.html #DFIR #infosec
"WMI 持久性: https://t.co/QnAb2cmddj "