腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

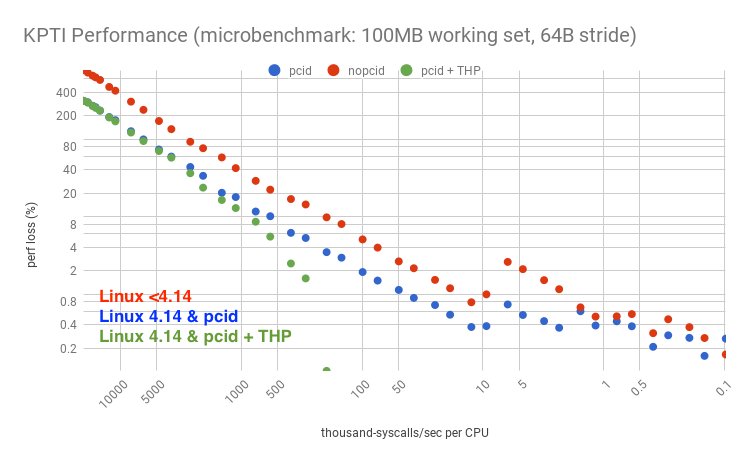
[ Hardware ] 对 Linux 系统 CPU Meltdown 补丁(KPTI/KAISER)的性能的分析: http://www.brendangregg.com/blog/2018-02-09/kpti-kaiser-meltdown-performance.html
-

[ Industry News ] 研究人员发现多款 Netgear 路由器存在远程认证绕过漏洞: http://securityaffairs.co/wordpress/68883/hacking/netgear-router-flaws.html
-

[ Industry News ] 联想警告其顾客数十种 ThinkPad 产品存在严重的 WiFi 漏洞: https://threatpost.com/lenovo-warns-critical-wifi-vulnerability-impacts-dozens-of-thinkpad-models/129860/
-

[ macOS ] macOS 系统 Installer Plugins 从 /tmp 文件夹加载 .pkg 代码执行的特性可以被用来劫持签名应用(Signed APP): https://posts.specterops.io/malicious-installer-plugins-6e30991bb529
-

[ MalwareAnalysis ] 利用 concolic execution 进行恶意软件的静态分析: https://int0xcc.svbtle.com/using-concolic-execution-for-static-analysis-of-malware
-

[ Others ] .NET handles – Part 1 – Dependent handles : https://blogs.msdn.microsoft.com/yizhang/2018/02/08/top-secret-net-handles-part-1-dependent-handles/
-

[ Popular Software ] Joomla 二次注入漏洞分析 (CVE -2018-6376): https://www.notsosecure.com/analyzing-cve-2018-6376/
-

[ Popular Software ] Adobe Flash Exploitation, Then and Now: From CVE-2015-5119 to CVE-2018-4878,Adobe Flash 多个漏洞利用方式回顾: https://www.mdsec.co.uk/2018/02/adobe-flash-exploitation-then-and-now-from-cve-2015-5119-to-cve-2018-4878/
-
-
-

[ Tools ] Meterpreter_Paranoid_Mode-SSL - 自定义 Meterpreter SSL 证书验证的工具: https://github.com/r00t-3xp10it/Meterpreter_Paranoid_Mode-SSL
-

[ Vulnerability ] 趋势科技 IMSVA Management Portal 身份认证绕过漏洞披露: http://seclists.org/fulldisclosure/2018/Feb/30
-

[ Vulnerability ] HDR 图像格式的开源实现 OpenEXR 被发现越界写漏洞(Imf_2_2::copyIntoFrameBuffer): https://github.com/openexr/openexr/issues/262
-

[ Web Security ] Snapchat 存储型 XSS 漏洞挖掘: https://medium.com/@mrityunjoy/stored-xss-on-snapchat-5d704131d8fd
-

[ Windows ] Hacked? Pray that the Attacker used PowerShell, PowerShell 红与蓝: https://www.slideshare.net/nikhil_mittal/hacked-pray-that-the-attacker-used-powershell
-

[ Windows ] 滥用计算机账户在活动目录环境下获取控制权限: http://www.bluehatil.com/files/Computers%20Gone%20Rogue.pdf