腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Backdoor ] ExaTrack 对 Uroburos 驱动级后门的分析报告: https://exatrack.com/public/Uroburos_EN.pdf
-

[ Browser ] Google 表示将在 2018 年 7 月发布的 Chrome 68 会把所有 HTTP 网站标记为“不安全”: https://security.googleblog.com/2018/02/a-secure-web-is-here-to-stay.html
-

[ Data Breach ] 瑞士电信(Swisscom)数据泄露,80万用户受影响: http://www.zdnet.com/article/swisscom-data-breach-800000-customers-affected/
-

[ Industry News ] Apache HTTPD 在源码中增加对 HonggFuzz 的支持: https://github.com/apache/httpd/commit/3bf3cbb9d4a8e142774d25cbad5cee5181fbbed4
-

[ iOS ] 苹果设备(iOS) Boot Loader 组件 iBoot 的源码泄露了: https://threatpost.com/apple-downplays-impact-of-iboot-source-code-leak/129852/https://github.com/m57/iBoot
-

[ IoTDevice ] 多款 IoT 设备的多个漏洞披露,包含硬编码凭证和远程命令注入漏洞: https://blogs.securiteam.com/index.php/archives/3661
-

[ macOS ] 由于 AppleEmbeddedOSSupportHostClient::registerNotificationPort 方法缺少锁操作导致 MacOS 内核 UAF 漏洞(CVE-2018-4083): https://bugs.chromium.org/p/project-zero/issues/detail?id=1430
-

[ MalwareAnalysis ] LokiBot 变种使用 Windows 安装器 msiexec.exe 安装后门: https://blog.trendmicro.com/trendlabs-security-intelligence/attack-using-windows-installer-msiexec-exe-leads-lokibot/
-

[ MalwareAnalysis ] Fortinet 对多款 JavaScript 挖矿代码的分析: https://blog.fortinet.com/2018/02/07/the-growing-trend-of-coin-miner-javascript-infection
-

[ Others ] In-Memory Evasion - 内存中 DLL 注入与发现的猫鼠游戏: https://blog.cobaltstrike.com/2018/02/08/in-memory-evasion/
-

[ Others ] 联邦法律官员最近表示,以后设备生产厂商需要自己有能力解密自己生产的设备,这个被称为 "Responsible Encryption",这篇 Paper 分析这带来的风险: https://cyberlaw.stanford.edu/files/publication/files/2018-02-05%20Technical%20Response%20to%20Rosenstein-Wray%20FINAL.pdf
-

[ Others ] 在 XNU 的源码中搜索 __ARM_KERNEL_PROTECT__ 宏定义可以了解针对 ARM64 架构的保护机制: https://twitter.com/i/web/status/961645139008552960
-

[ Others ] UDPOS - 偷磁条卡信息并用基于 UDP 的 DNS 数据包向外渗出的恶意软件: https://blogs.forcepoint.com/security-labs/udpos-exfiltrating-credit-card-data-dns
-

[ Popular Software ] 针对 CVE-2018-4878 的技术分析: https://blog.morphisec.com/cve-2018-4878-an-analysis-of-the-flash-player-hack
-

[ Popular Software ] Shimo VPN Client for MacOS 本地提权漏洞披露(CVE-2018-6823): https://github.com/VerSprite/research/blob/master/advisories/VS-2018-001.md
-

[ Popular Software ] Weblogic wls-wsat 组件反序列化漏洞(CVE-2017-10271)的利用脚本: https://github.com/kkirsche/CVE-2017-10271
-

[ Popular Software ] Adobe Coldfusion 11.0.03.292866 BlazeDS Java 对象反序列化远程代码执行漏洞POC: https://cxsecurity.com/issue/WLB-2018020117
-
-

[ Tools ] Stacer - Linux 系统优化与监控工具: https://github.com/oguzhaninan/Stacer
-

[ Tools ] StaCoAn - 跨平台的移动端应用静态代码分析工具: https://github.com/vincentcox/StaCoAn
-

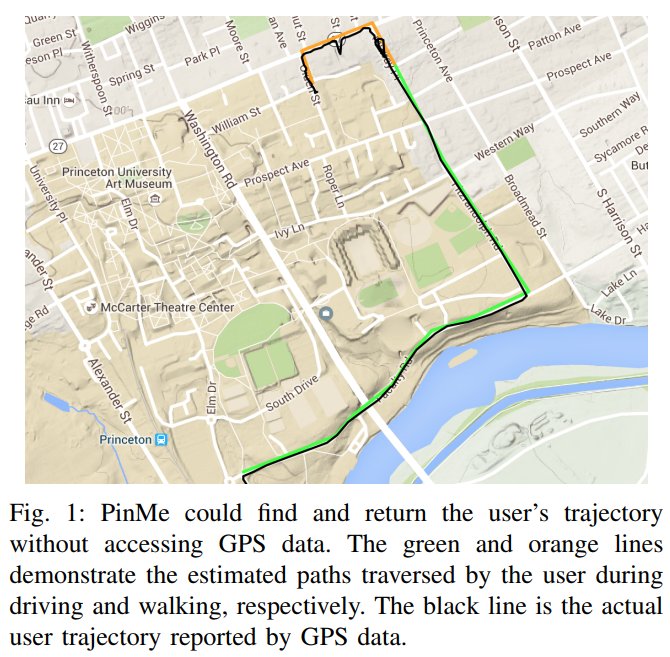
[ Tools ] PinMe - 智能手机用户的定位之前需要 GPS 或者网络相关的信息。这篇 Paper 提到的 PinMe 方法可以在 GPS 相关服务关闭的情况通过气压、时区等信息追踪用户位置: https://arxiv.org/pdf/1802.01468.pdf
-

[ Tools ] pcileech-fpga - 针对 FPGA 设备的 PCILeech DMA 攻击套件: https://github.com/ufrisk/pcileech-fpga
-

[ Tools ] NtObjectManager 更新至 v1.1.8: https://www.powershellgallery.com/packages/NtObjectManager/1.1.8
-

[ Tools ] Bellingcat 总结的数字取证相关的工具和方法: https://docs.google.com/document/d/1BfLPJpRtyq4RFtHJoNpvWQjmGnyVkfE2HYoICKOGguA/edit#
-

[ Tools ] TheFatRat and BeEF – Pre and Post Exploitation Method,TheFatRat 与 BeEF 工具的综合使用示例: https://www.drchaos.com/thefatrat-and-beef-pre-and-post-exploitation-method/
-

[ Tools ] 二进制漏洞利用开发教程: https://0x00sec.org/t/getting-cozy-with-exploit-development/5311
-

[ Vulnerability ] 游戏公司的 BANDAI NAMCO 驱动 bandainamcoonline.sys 被发现本地提权漏洞: https://securelist.com/elevation-of-privileges-in-namco-driver/83707/
-

[ Windows ] Windows 10 Insider Preview Build 17093 发布,并详细介绍了该版本的诸多更新内容: https://blogs.windows.com/windowsexperience/2018/02/07/announcing-windows-10-insider-preview-build-17093-pc/