腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ MalwareAnalysis ] Latest #Unit42 research on #SamSa ransomware with details on updated toolsets http://oak.ctx.ly/r/5at7r
"Unit42 对 SamSa 勒索软件过去一年的回顾与分析: https://t.co/SCqVtjQUIF "
-

[ MalwareAnalysis ] Analysis of Zeus Variant 'Floki Bot' targeting PoS Data : http://blog.talosintel.com/2016/12/flokibot-collab.html#more , Flokibot Tools :… https://twitter.com/i/web/status/807254823598833665
"针对恶意软件 Zeus 变种 Floki Bot 的分析 ︰ https://t.co/0w9wPOqQFp,Flokibot Tools: https://t.co/JF6JIGpYlh"
-

[ MalwareAnalysis ] The Domain Generation Algorithm (DGA) used in #Mirai 's new variant: http://blog.netlab.360.com/new-mirai-variant-with-dga/
"Mirai 的新变种开始使用域生成算法 (DGA): https://t.co/nOtQIFi7Ka"
-

[ MalwareAnalysis ] Banking trojan, Gmail webinject, SMS message and malicious APK – all in one attack scenario https://badcyber.com/banking-trojan-gmail-webinject-sms-message-and-malicious-apk-all-in-one-attack-scenario/
"银行木马新攻击场景:冒充波兰财务部邮件,诱使用户打开恶意附件: https://t.co/jH8WK0Jb4k"
-

[ MalwareAnalysis ] Camouflage - http://blog.avlsec.com/2016/12/4179/camouflage/ (Chinese)
"当攻击者熟读兵法,Camouflage病毒实战演示暗度陈仓之计: https://t.co/TJ6KjqH7Br"
-

[ Others ] Stego in TCP/IP made easy (part-1) : https://www.exploit-db.com/docs/40891.pdf (pdf)
"TCP/IP 中的隐写术 (part 1): https://t.co/f2mnvDqOJb (part 2): https://www.exploit-db.com/docs/40897.pdf"
-

[ Others ] Hackers targeted the heavy industry ThyssenKrupp and stole industrial secrets http://securityaffairs.co/wordpress/54218/hacking/hackers-targeted-thyssenkrupp.html
"德国重工业巨头 ThyssenKrupp 遭东南亚黑客袭击,商业机密被窃走 : https://t.co/iKyxai6RuY"
-

[ Popular Software ] Yahoo Mail stored XSS and how it was found https://klikki.fi/adv/yahoo2.html #bugbounty
"Yahoo 邮箱存储型 XSS 漏洞在哪里: https://t.co/6wnNKBAvdo"
-

[ Popular Software ] Splunk Enterprise Server-Side Request Forgery https://goo.gl/fb/nBbmNq #FullDisclosure
"Splunk Enterprise <= 6.4.3 服务器端请求伪造漏洞: https://t.co/SAc6M3Uqc2 "
-

[ Popular Software ] Microsoft Remote Desktop Client For Mac 8.0.36 Remote Code Execution https://cxsecurity.com/issue/WLB-2016120050
"Mac 版 Microsoft 远程桌面客户端存在远程代码执行漏洞: https://t.co/SxDsshZwhM ; Demo Video: https://www.youtube.com/watch?v=6HeSiXYRpNY&;feature=youtu.be"
-

[ Tools ] avclass - AVClass malware labeling tool https://github.com/malicialab/avclass
"AVClass -- 一个恶意软件标记工具: https://t.co/3XlCn0GNmw"
-

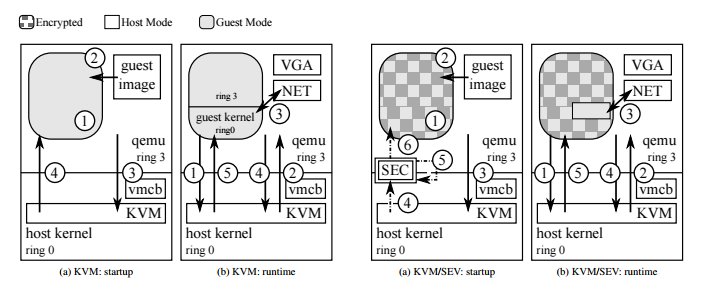
[ Virtualization ] Security Analysis of Encrypted Virtual Machines : https://arxiv.org/pdf/1612.01119v1.pdf (pdf) https://t.co/OZfPDNJpfL
"加密的虚拟机安全性分析(PDF)︰ https://t.co/m28ZJ7UpgV"
-

[ Windows ] Windows x64 - Bind Shell TCP Shellcode (508 bytes) : https://www.exploit-db.com/exploits/40890/
Windows x64 - Bind Shell TCP Shellcode: https://www.exploit-db.com/exploits/40890/
-

[ WirelessSecurity ] GSM Hacking:The application of Silent SMS in technical investigation https://cn0xroot.wordpress.com/2016/12/09/gsm-hacking%ef%bc%9athe-application-of-silent-sms-in-technical-investigation/ from @ xdzou #SDR… https://twitter.com/i/web/status/807249268083859457
"GSM Hacking:静默短信(Silent SMS)在技术侦查中的应用: https://t.co/Fi3lIAvMcr "
-

[ WirelessSecurity ] My wireless mouse hijacking NES controller is now open source. Build guide + firmware are on GitHub. Happy hacking! https://t.co/3jtagz7ZVs
"无线鼠标劫持 NES controller 开源: https://t.co/3jtagz7ZVs"