
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] Rise of the Machines: The Dyn Attack Was Just a Practice Run (Mirai 'is just the tip of the iceberg') : http://icitech.org/wp-content/uploads/2016/12/ICIT-Brief-Rise-of-the-Machines.pdf (pdf)
"机器的崛起︰ Dyn 攻击只是实践 (Mirai 也只是冰山一角)︰ https://t.co/hnrKWDr8if "
-

[ Browser ] RCE in JXBrowser JavaScript/Java bridge : http://blog.portswigger.net/2016/12/rce-in-jxbrowser-javascriptjava-bridge.html
"RCE in JXBrowser JavaScript/Java bridge ︰ https://t.co/K0KbulRxWD"
-

[ Browser ] Here is basically how Firefox chrome code execution works http://pastebin.com/raw/EsBErDZ3/ #TheMoreYouKnow
" 如何在 Firefox/Chrome 浏览器 about:newtab 特权页面的 Console 中弹计算器: https://t.co/V6YB7TJHhx "
-

[ Browser ] ROP & Heap Spray for a Reverse Shell in IE8 : https://woumn.wordpress.com/2016/12/07/rop-heap-spray-for-a-reverse-shell-in-ie8/ https://t.co/NTri6b0JDk
"在 IE8 中利用 ROP和堆喷射来反弹 shell︰ https://t.co/gWwIxNFw6U"
-

[ Browser ] #DailyBug #MSIE 9 MSHTML CDispNode::InsertSiblingNode use-after-free http://blog.skylined.nl/20161208001.html
"MSIE 9 MSHTML CDispNode::InsertSiblingNode UAF 细节(CVE-2013-1306): https://t.co/Ne5uhZdRHq"
-

[ Fuzzing ] Applied high-speed in-process fuzzing: the case of Foxit Reader http://www.hdwsec.fr/en/blog/inprocessfuzzing.html
" Fuzz 过程中,性能是一个关键指标。这篇 Blog 以 Fuzz 福昕阅读器的 ConvertToPDF 插件为例,介绍如何通过注入代码不重启进程的方式 Fuzz 指定 API,实现高性能 Fuzz: https://t.co/6MwdamAHJ4 "
-

[ iOS ] If you add https://jbme.qwertyoruiop.com to Cydia, a tweak that patches the Pegasus bug is available.
" qwertyoruiop 基于前段时间的三叉戟(Pegasus)漏洞利用代码,结合盘古的越狱代码,写了针对 iOS 9.3.x 版本的一个远程越狱工具: https://t.co/0mXYb3vPMA 另外,他说将 jbme.qwertyoruiop.com 添加到 Cydia 中,就可以修复 Pegasus 的一个 Bug,这个 Patch 的源码: https://ghostbin.com/paste/pfqv6"
-

[ IoTDevice ] An Anatomy of IoT Security : https://github.com/mdsecresearch/Publications/blob/master/presentations/An%20Anatomy%20of%20IoT%20Security_OWASPMCR_Nov2016.pdf (Slides) cc @ domchell || @ OwaspMcr
"物联网安全剖析(slides)︰ https://t.co/kaEi5JT4bn "
-

[ MalwareAnalysis ] PowerShell threats are on the rise: 95.4% of the scripts we analyzed were malicious Learn more:… https://t.co/TxuOYwsJGG
"PowerShell 威胁呈上升趋势︰ 被分析的脚本中的 95.4% 均为恶意代码: https://t.co/TxuOYwsJGG"
-

[ Mobile ] New post: Mobile Ransomware: Pocket-Sized Badness http://bit.ly/2hn2p4Q @ TrendMicro
"TrendMicro 对手机勒索软件的研究: https://t.co/74pwNrsy3X "
-

[ OpenSourceProject ] FreeBSD/Apple libc link_ntoa() buffer overflow https://cxsecurity.com/issue/WLB-2016120046
"FreeBSD/Apple libc link_ntoa() 缓冲区溢出漏洞(CVE-2016-6559): https://t.co/6ASBNDMdfA"
-

[ Others ] Eventvwr File-less UAC Bypass implemented in Cobalt Strike https://www.mdsec.co.uk/2016/12/cna-eventvwr-uac-bypass/ #windows #UAC #bypass https://t.co/MS2F5SGPm6
"Eventvwr 无文件绕过 UAC 限制的 CNA 利用脚本: https://www.mdsec.co.uk/2016/12/cna-eventvwr-uac-bypass/ "
-

[ Others ] North Korea's Linux-based Red Star OS can be Hacked Remotely with just a Link http://thehackernews.com/2016/12/redstar-north-korea.html #linux #Security
"只需一个链接即可黑掉朝鲜 Red Star OS: https://t.co/yXDuf0WLdv "
-

[ Others ] Tracking Down a Freaky Python Memory Leak : https://benbernardblog.com/tracking-down-a-freaky-python-memory-leak/
"Python 内存泄漏追踪︰ https://t.co/JVRmRqgnXq"
-

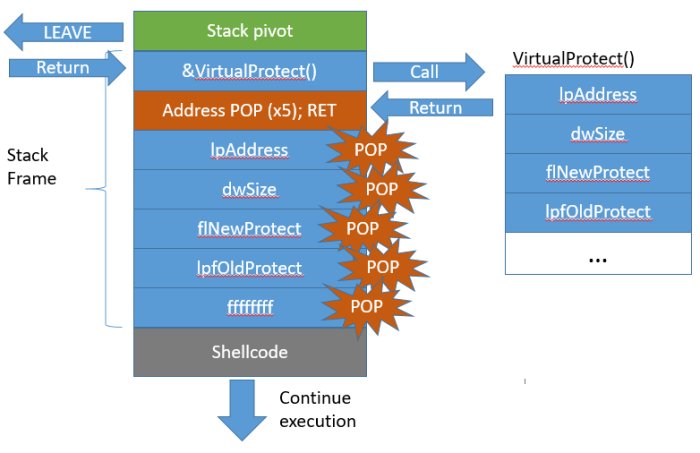
[ Others ] Smashing the Stack into a Reverse Shell : https://woumn.wordpress.com/2016/09/24/smashing-the-stack-into-a-reverse-shell/ ; Bypassing ASLR on Windows into a Reverse Shell : https://woumn.wordpress.com/2016/10/12/bypassing-aslr-on-windows-into-a-reverse-shell/
"利用栈溢出来反弹 shell︰ https://t.co/Twx17MiaX9 在 Windows 上绕过 ASLR 来反弹 shell︰ https://t.co/YT5wZQSvG0"
-

[ Tools ] Best IDA Plugins https://n0where.net/best-ida-plugins/ #InfoSec #CyberSecurity
"最佳 IDA 插件推荐: https://t.co/2J1Dg336d1 "
-

[ Tools ] Neat IDA Python editor. https://github.com/techbliss/Python_editor
" IDA Pro 的自带脚本编辑器不是非常好用,于是有研究员自己写了一个。支持 Python 代码的自动补全和高亮等功能,界面也看起来友好多了: https://t.co/FzX3lsYS2j"
-

[ Tools ] ATrace is a tool for tracing execution of binaries on Windows. https://shrtm.nu/iJRR by @ ktwo_K2
"ATrace -- 一个 Windows 上的二进制文件跟踪工具: https://t.co/93BDWC6QSY"
-

[ Tools ] EPEx: Error Path Exploration for Finding Error Handling Bugs https://github.com/yujokang/epex
" EPEx - 基于 Clang 编译器实现的一个工具,用于检测 C 代码中错误处理代码缺失的情况: https://t.co/rPmec8cig6 "
-

[ Tools ] Cobalt Strike 3.6 – A Path for Privilege Escalation http://blog.cobaltstrike.com/2016/12/08/cobalt-strike-3-6-a-path-for-privilege-escalation https://t.co/rxGReyjWHO
"Cobalt Strike 3.6 发布: https://t.co/9qA6OpkGJn "
-

[ Tools ] xrdp : A rudimentary remote desktop tool for the X11 protocol exploiting unauthenticated x11 sessions : https://github.com/sensepost/xrdp
"xrdp -- 一个可用于 X Windows 未授权会话利用的远程桌面工具︰ https://t.co/AMq90tPHZa"
-

[ Windows ] Windows Kernel Exploitation - Uninitialized Heap Variable Assignment http://dokydoky.tistory.com/445
"Windows 内核利用之未初始化的堆变量: https://t.co/8jyf93rw7D"
-

[ Windows ] CSS Custom Properties (variables to non-Spec heads) in Edge \o/ https://twitter.com/msedgedev/status/806641150186528768
"Windows Edge build 14986 已发布: https://t.co/tvJgltI4PM"
-
[ OpenSourceProject ] (CVE-2016-1247)Nginx Local Privilege Escalation Vulnerability Technical Analysis and Solution: http://blog.nsfocus.net/nginx-local-privilege-escalation-vulnerability-technical-analysis-solution/
-
[ Popular Software ] War3 地图“漏洞”分析介绍: https://3gstudent.github.io/3gstudent.github.io/War3%E5%9C%B0%E5%9B%BE-%E6%BC%8F%E6%B4%9E-%E5%88%86%E6%9E%90%E4%BB%8B%E7%BB%8D/
-
[ Malware ] 来自卡巴斯基的《2016 年勒索软件发展研究报告》: https://securelist.com/analysis/kaspersky-security-bulletin/76757/kaspersky-security-bulletin-2016-story-of-the-year/
 Xuanwu Spider via 绿盟科技
Xuanwu Spider via 绿盟科技