
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Language ] Ruby Hacking Guide : http://ruby-hacking-guide.github.io/
"Ruby Hacking 指南︰ https://t.co/PdcU1evYof"
-

[ Linux ] Android "Root" via dirtyc0w privilege escalation exploit https://gist.github.com/Arinerron/0e99d69d70a778ca13a0087fa6fdfd80 https://t.co/jJDlw383GY
" 又有研究员为 DirtyCow 漏洞写了一个 Android 版本的利用代码: https://t.co/2qk7tI3fhH https://t.co/jJDlw383GY"
-

[ macOS ] My ppt "Fuzzing and Exploit OSX Vulnerabilities for Fun and Profit" on Pacsec2016 http://www.slideshare.net/PacSecJP/moony-li-pacsec18?qid=15552f01-6655-4555-9894-597d62fd803c&v=&b=&from_search=4 Github https://t.co/rUX8bzhCAd
" OS X 系统漏洞的挖掘和利用,来自 PacSec 2016 会议, PPT: https://t.co/jDYsVanz1l 代码: https://t.co/rUX8bzhCAd"
-

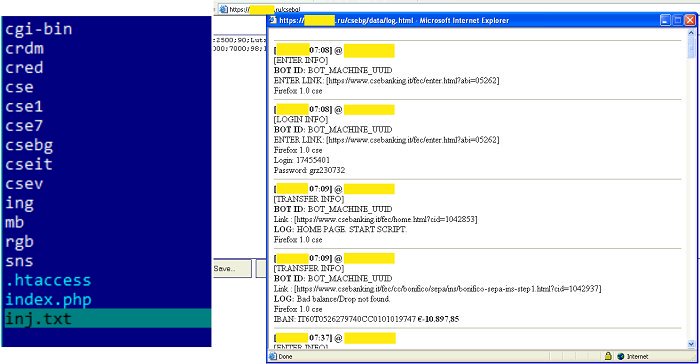
[ Malware ] CloudFanta Malware Steals Banking Information Via Cloud Storage Apps http://securityaffairs.co/wordpress/52750/malware/cloudfanta-malware.html
"CloudFanta 恶意软件通过云存储应用程序窃取银行信息: https://t.co/DWL2aUjiqC"
-

[ Malware ] Inside the Gootkit C&C server https://securelist.com/blog/research/76433/inside-the-gootkit-cc-server/ https://t.co/3MJiBq0hrw
" 剖析 Gootkit 的 C&C 服务器: https://t.co/g274I3LUXg "
-

[ Malware ] A nine-year-old vulnerability is uncovered in Linux systems. A look at other recent threats that affected the OS: http://bit.ly/2eqfZc4
" Linux 系统的恶意软件威胁,来自趋势科技︰ https://t.co/yIv4t95ipa"
-

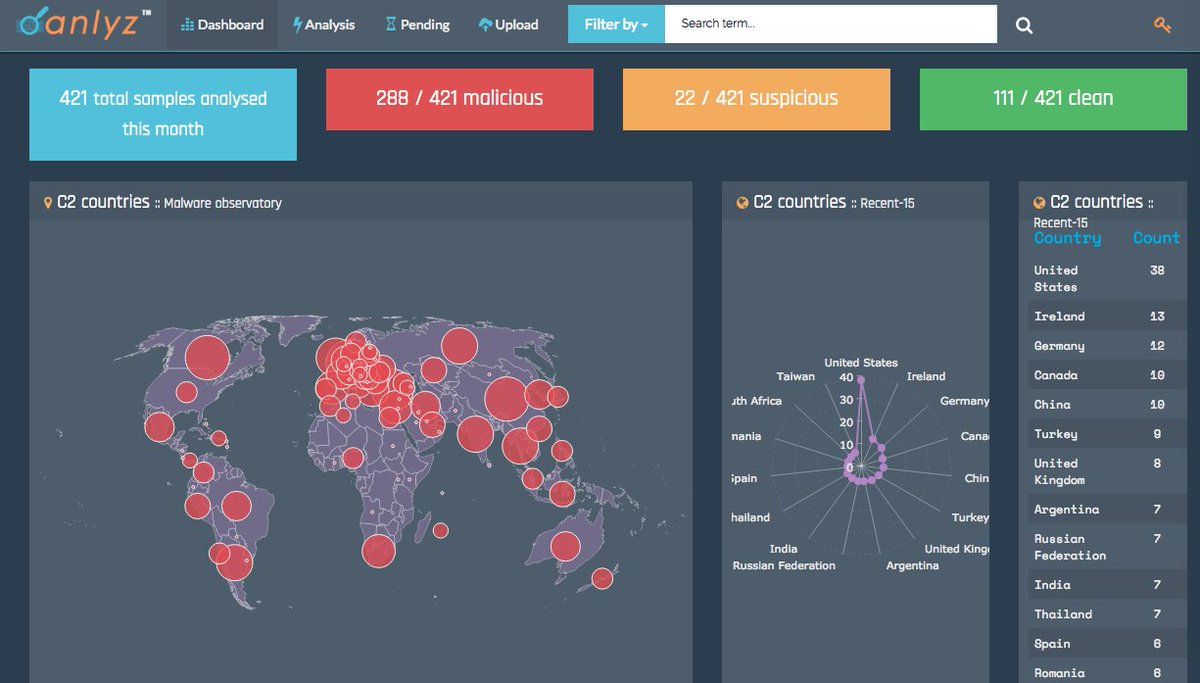
[ MalwareAnalysis ] Sandbox Analyz.io yet another malware sandbox https://sandbox.anlyz.io https://t.co/D6mSEEMraZ
" sandbox.anlyz.io - 恶意软件分析沙盒工具: https://t.co/Gs5j3jU2MS "
-

[ OpenSourceProject ] GNU tar extract pathname bypass : https://sintonen.fi/advisories/tar-extract-pathname-bypass.proper.txt
"GNU 解压缩工具 tar 存在路径名绕过漏洞︰ https://t.co/jmHl7kjZd4"
-

[ Others ] Controlled-Channel Attacks: Deterministic Side Channels for Untrusted Operating Systems - https://www.microsoft.com/en-us/research/wp-content/uploads/2016/02/ctrlchannels-oakland-2015.pdf - https://www.youtube.com/watch?v=fwUaN5ik8zE
" 来自微软公开的一篇 Paper,介绍了一种新型的侧信道攻击方式, 《Controlled-Channel Attacks: Deterministic Side Channels for Untrusted Operating Systems》: https://www.microsoft.com/en-us/research/wp-content/uploads/2016/02/ctrlchannels-oakland-2015.pdf https://www.youtube.com/watch?v=fwUaN5ik8zE "
-

[ Others ] [New Phrack Paper] Attacking JavaScript Engines: A case study of JavaScriptCore and CVE-2016-4622 http://www.phrack.org/papers/attacking_javascript_engines.html by @ 5aelo
" 攻击 JavaScript 引擎︰ JavaScriptCore 与 CVE-2016-4622 案例研究,来自 Phrack 的一篇 Paper: https://t.co/1nP1z8LU8t 作者公开的代码: https://github.com/saelo/jscpwn "
-

[ Rootkit ] NumChecker A System Approach for Kernel Rootkit Detection and Identification https://www.blackhat.com/docs/asia-16/materials/asia-16-Guo-NumChecker-A-System-Approach-For-Kernel-Rootkit-Detection-And-Identification.pdf - https://www.youtube.com/watch?v=TgMsMwsfoQ0
"NumChecker - 内核 Rootkit 检测和识别的系统性方法,来自 BlackHat Asia 2016 会议: https://www.blackhat.com/docs/asia-16/materials/asia-16-Guo-NumChecker-A-System-Approach-For-Kernel-Rootkit-Detection-And-Identification.pdf 视频: https://www.youtube.com/watch?v=TgMsMwsfoQ0 "
-

[ Tools ] Check our ROP tool used in our private PS4 jailbreak: https://github.com/chaitin/pro
" 长亭科技开源的一个 PS4 越狱相关的 ROP 辅助工具︰ https://t.co/3y15JsHJdg"
-

[ Tools ] rop-chainer : static program analysis tool that generates return-oriented exploits for ELF binaries : https://github.com/wizh/rop-chainer
"rop-chainer - 为 ELF 二进制文件生成 ROP 片段的静态分析工具︰ https://t.co/Gjkauu26iK"
-

[ Tools ] A new tool uses Capstone inside: RePEconstruct to auto unpack Windows binary & rebuild the Import Address Table. https://t.co/2cDP0GZujL
" RePEconstruct - Windows 二进制文件自动化脱壳、重建导入表的工具: https://t.co/2cDP0GZujL"
-

[ Virtualization ] [CVE-2016-5328/5329] Multiple VMWare Fusion kernel infoleaks (1 in the OS X Host and 1 in the OS X Guest) - https://marcograss.github.io/security/vmware/cve/2016/10/27/cve-2016-5328-5329-vmware-fusion-infoleaks.html
" VMWare Fusion 内核信息泄漏漏洞(CVE-2016-5328/5329): https://t.co/kPVvgQ0HgY"
-

[ Web Security ] Joomla exploit, drops PHP shell too https://github.com/XiphosResearch/exploits/tree/master/Joomraa (cc @ danielcid @ showthread )
" 近两天公开的 Joomla 3.4.4 - 3.6.4 (CVE-2016-8869/8870) 漏洞的 Exploit: https://t.co/4dzPEHTgHV "
-

[ Windows ] Windows atom tables can be abused for code injection attacks - http://bit.ly/2efdPGC #atombombing
"Windows atom tables 可被滥用实现代码注入攻击: https://t.co/tKD7CvH1yG "
-

[ Windows ] Example: Turn Msbuild.exe into a keylogger. https://gist.github.com/subTee/c51ea995dfaf919fd4bd36b3f7252486
" 把 Msbuild.exe 变成 Keylogger: https://t.co/IDABotvZrG"
-

[ Windows ] Check details how I exploit a win32k vulnerability for EoP in Pwn2Own 2016. https://twitter.com/zer0mem/status/791522523003228160
" win32k 的攻击面以及如何利用它的漏洞在 Pwn2Own 2016 绕过 Edge 的沙箱,来自科恩实验室研究员的分享《Rainbow Over the Windows: More Colors Than You Could Expect》: https://t.co/UYndiEXj0T http://www.slideshare.net/PeterHlavaty/rainbow-over-the-windows-more-colors-than-you-could-expect "
-

[ Windows ] [BlogPost] Command Line Camouflage - ODBCCONF.EXE http://subt0x10.blogspot.com/2016/10/command-line-camouflage-odbcconfexe.html cc @ NickTyrer
" 命令行伪装 - ODBCCONF.EXE,作者为 subTee: https://t.co/mToepoRU3q "
-

[ Windows ] Windows Device Guard Code Integrity Policy Reference http://www.exploit-monday.com/2016/10/code-integrity-policy-reference.html
" Windows Device Guard 代码完整性策略的细节: https://t.co/HNq9W6kbr5"

 Xuanwu Spider via 360 NetLab
Xuanwu Spider via 360 NetLab