
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Forensic Analysis of the ChatSecure Instant Messaging Application on Android Smartphones : https://arxiv.org/pdf/1610.06721v1.pdf (pdf)
"Android ChatSecure 即时通信应用的取证分析︰ https://t.co/nRHq375Chr "
-

[ Attack ] Moonlight – Targeted attacks in the Middle East http://blog.vectranetworks.com/blog/moonlight-middle-east-targeted-attacks
" Moonlight - 中东地区的定向攻击跟踪: https://t.co/8WH5K006nY"
-

[ Backdoor ] Pork Explosion: A Foxconn Bootloader Root/SELinux Backdoor http://bbqand0days.com/Pork-Explosion-Unleashed/ Many thanks to @ nextbitsys for promptly fixing this!
" 富士康 Bootloader Root/SELinux 后门: https://t.co/Xw2CN85QeR "
-

[ Browser ] A BrowserStack vulnerability disclosure http://bloggerbust.ca/2016/10/26/browsersmack-a-browser-stack-proxy-vulnerability/
" BrowserSmack - BrowserStack 的代理漏洞,BrowserStack 是一种跨浏览器测试的解决方案: https://t.co/YUPrcOUW2b"
-

[ Challenges ] Final entry: @ keen_lab used a UAF in the renderer & mem corruption in sandbox to steal pics from an iPhone. They wi… https://twitter.com/i/web/status/791191679134932992
" 昨天的 Mobile Pwn2Own 比赛上,科恩实验室团队成功攻破了搭载 Android 7 版本的 Nexus 6P 以及 iOS 10: https://twitter.com/i/web/status/791191679134932992 团队最终赢得了 21.5 万美元的奖金: https://twitter.com/i/web/status/791197929264472064 比赛的最终结果的细节: http://blog.trendmicro.com/results-mobile-pwn2own-2016/ "
-

[ Firmware ] Pixhawk Firmware Hooking - https://www.invincealabs.com/blog/2016/10/pixhawk-firmware-hooking/
" Pixhawk Firmware Hooking: https://t.co/pcDwq6kuX8"
-

[ Hardware ] Towards a hardware-assisted information ow tracking ecosystem for ARM processors https://hal.archives-ouvertes.fr/hal-01337579/document
" ARM 处理器硬件辅助的信息流跟踪系统: https://t.co/5MFO0Tsq7T"
-

[ Hardware ] Researchers @ Percent_X & @ tatanus discovered #vulns in multiple bluetooth device trackers. Read this: http://r-7.co/2eE8v0T
" 多款蓝牙低功耗跟踪器被发现漏洞,来自 Rapid7 Blog︰ https://t.co/r0iYuztCfI"
-

[ Linux ] Using scumjr's vDSO Dirty COW POC to escape Docker containers. Video, docker config, and instructions to play along: https://t.co/vOEQ9KNTPG
" 利用脏牛漏洞(Dirty Cow)的 vDSO Exploit 实现 Docker 容器的逃逸︰ https://t.co/vOEQ9KNTPG"
-

[ Network ] We analyzed the Mirai IoT botnet, arguably one of the largest distributed denial of service attacks (DDoS) to date https://t.co/QgRmE6hUc3
" 来自 Incapsula 团队对 Mirai IoT Botnet DDoS 的分析: https://t.co/QgRmE6hUc3"
-

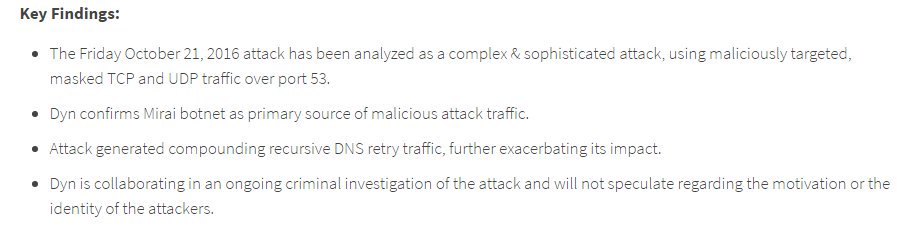
[ Network ] .@ Dyn posts update on Friday's massive DDoS attack --> http://dyn.com/blog/dyn-analysis-summary-of-friday-october-21-attack/ https://t.co/YDj2j1SfZO
" DNS 提供商 Dyn 昨天发布了一篇文章总结上周五针对它的 DDoS 攻击事件: https://t.co/AMQMAOF7St https://t.co/YDj2j1SfZO"
-

[ Others ] Techniques for surveillance evasion. Worth reading https://protectioncircle.org/2016/06/14/surveillance-evasion/
" 如何实现逃避敌人的监视: https://t.co/pQrkKwHt3m"
-

[ Others ] Trading Off a Vulnerability: Does Software Obfuscation Increase the Risk of ROP Attacks http://riverpublishers.com/journal/journal_articles/RP_Journal_2245-1439_444.pdf
" 软件混淆技术一定程度上可以增加逆向分析的难度,这篇 Paper 换一个角度,谈引入混淆可能使软件更加容易被 ROP 攻击: https://t.co/ySrHjGDmRk"
-

[ Popular Software ] Apache Tomcat DebPkg - Root PrivEsc Video PoC Exploit (CVE-2016-1240) http://legalhackers.com/videos/Apache-Tomcat-DebPkg-Root-PrivEsc-Exploit.html
"Apache Tomcat Debian 发行版存在一个 Root 提权漏洞(CVE-2016-1240),视频演示: https://t.co/WrN1tTZX9h 公告细节: http://legalhackers.com/advisories/Tomcat-DebPkgs-Root-Privilege-Escalation-Exploit-CVE-2016-1240.html "
-

[ Popular Software ] #Security updates available for #Adobe #Flash Player: http://adobe.ly/2dHqG3t
" Adobe Flash 昨天发布补丁更新,修复了一个 UAF 漏洞(CVE-2016-7855)︰ https://t.co/4ZZwweHGEc"
-

[ Vulnerability ] CODE BLUE 2016 - Method of Detecting Vulnerability in Web Apps http://www.slideshare.net/babaroa/code-blue-2016-method-of-detecting-vulnerability-in-web-apps
"日本信息安全大会 CODE BLUE 2016 议题之一:在 Web 应用程序中检测漏洞的方法: https://t.co/B42DS7VLjr "
-

[ Web Security ] Joomla Vuls analysis by p0wd3r of Knownsec 404 Security Team CVE-2016-8869 http://paper.seebug.org/88/ CVE-2016-8870 https://t.co/aUKS3nX1NH
" Joomla 未授权创建特权用户漏洞(CVE-2016-8869)分析: https://t.co/Gka9xorm2q Joomla 未授权创建用户漏洞(CVE-2016-8870)分析: https://t.co/aUKS3nX1NH "
-

[ Web Security ] Google Spreadsheet Vuln - CSRF and JSON Hijacking allows data theft : https://www.rodneybeede.com/Google_Spreadsheet_Vuln_-_CSRF_and_JSON_Hijacking_allows_data_theft.html
"Google 的在线电子表格存在 CSRF 和 JSON 劫持漏洞,利用该漏洞可以窃取数据︰ https://t.co/GrjLHLG64G"
-

[ Windows ] Our ETW library exposes C++ and C# APIs. Here’s a C# example: https://github.com/Microsoft/krabsetw/blob/master/examples/user_trace_002.cs
" KrabsETW - 微软开源的一个库,是对底层事件跟踪做的一个 C++ 的封装︰ https://github.com/Microsoft/krabsetw https://t.co/6s0fFGVioc"
-

[ Windows ] Microsoft Windows (x86) - 'NDISTAPI' Privilege Escalation (MS11-062) : https://www.exploit-db.com/exploits/40627/
"Microsoft Windows (x86) 'NDISTAPI' 提权漏洞 Exploit,比较早了,2011 年的漏洞,漏洞编号为:MS11-062/CVE-2011-1974: https://t.co/NDvRi888wP"
-

[ WirelessSecurity ] GNU Radio Tutorials [pdf] http://files.ettus.com/tutorials/labs/Lab_1-5.pdf video https://www.youtube.com/playlist?list=PL618122BD66C8B3C4&feature=view_all
"GNU Radio 教程 [pdf]: https://t.co/XibPzi6WlE 视频: https://t.co/Qk2ttLq9YV"
-
[ Popular Software ] Oracle JRE java.awt.Menu Use-After-Free 远程代码执行漏洞分析与利用: http://mp.weixin.qq.com/s?__biz=MzA4MzgzNTU0Mg==&mid=2669132104&idx=1&sn=40b3a7f6d5125db976096ea084fb288a&chksm=851376b1b264ffa7dc284a1168e86e2e1d331bc15d373bf03f54813576b89020771c9b2fa3ea&mpshare=1&scene=1&srcid=1027YnoAvWftKRl95x1LWMAw#rd
 Xuanwu Spider via Seebug
Xuanwu Spider via Seebug