
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] The #StrongPity APT targets Italian and Belgian TrueCrypt users: https://securelist.com/blog/research/76147/on-the-strongpity-waterhole-attacks-targeting-italian-and-belgian-encryption-users/
"StrongPity APT 将目标锁定到意大利和比利时的 TrueCrypt 用户︰ https://t.co/4hcGLDZovV"
-

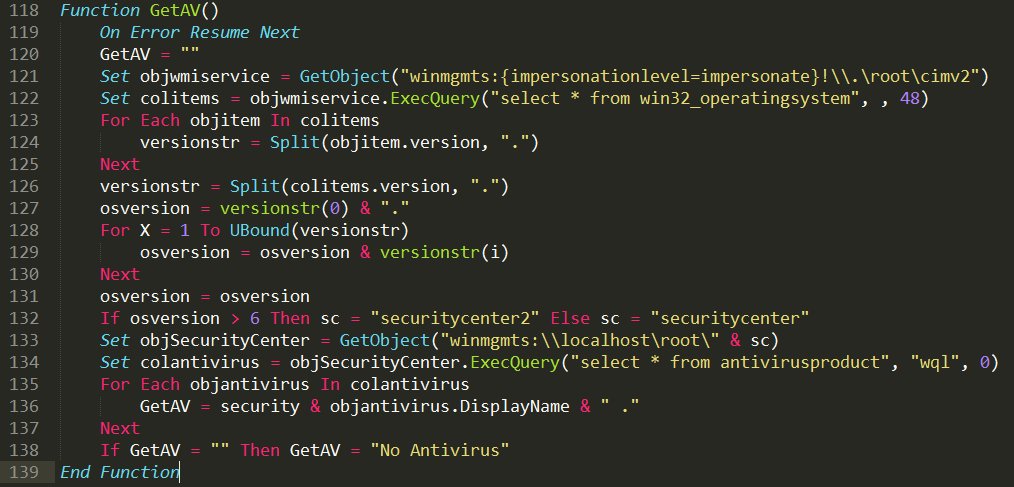
[ Detect ] [Blog] Increased use of WMI for environment detection & evasion http://bddy.me/2dtmhBG #infosec https://t.co/Ze8DJyPKJG
"恶意软件在环境检测和逃逸方面更多的开始使用 WMI : https://t.co/gl6YdDPUvo "
-

[ IoTDevice ] IoT Botnet Uses HTTP Traffic to DDoS Targets: https://threatpost.com/iot-botnet-uses-http-traffic-to-ddos-targets/121199/ via @ threatpost
"物联网僵尸网络使用 HTTP 流量 DDoS 的目标︰ https://t.co/42KIEh4VjP"
-

[ Linux ] Linux learning for Novices (from scratch) : https://linuxjourney.com/
" 从头开始学 Linux︰ https://t.co/mP7ZJ0kAQY"
-

[ Malware ] Nymaim : Deep Technical Dive - Adventures in Evasive Malware : http://www.seculert.com/blogs/nymaim-deep-technical-dive-adventures-in-evasive-malware https://t.co/fI4OeZocEn
"针对恶意软件 Nymaim 的深度技术分析: http://www.seculert.com/blogs/nymaim-deep-technical-dive-adventures-in-evasive-malware"
-

[ Network ] Say Cheese : A snapshot of the massive DDoS attacks coming from IoT cameras : https://blog.cloudflare.com/say-cheese-a-snapshot-of-the-massive-ddos-attacks-coming-from-iot-cameras/
"DDos攻击新趋势:来自IoT设备的DDoS攻击︰ https://t.co/eu4VHWL5ll"
-

[ OpenSourceProject ] New OpenSSL double-free and invalid free vulnerabilities in X509 parsing https://github.com/guidovranken/openssl-x509-vulnerabilities
"openssl-x509-vulnerabilities(double-free and invalid free vulnerabilities ) https://t.co/y5KCNik5eJ"
-

[ Popular Software ] New advisory and poc for Adobe Flash Player vulnerability. https://cosig.gouv.qc.ca/en/cosig-2016-35-en/
"Adobe Flash Player 远程执行代码漏洞(PoC): https://t.co/d0v3ogiilO"
-

[ Popular Software ] #PatchTuesday - #Security updates available for #Adobe #Flash Player: http://adobe.ly/2ellxCO
" Adobe Flash 本月的补丁更新公告︰ https://t.co/LOJT8kiinM Acrobat Reader 的补丁公告: https://helpx.adobe.com/security/products/acrobat/apsb16-33.html "
-

[ Sandbox ] Slides from our presentation at #VB2016: https://www.virusbulletin.com/uploads/pdf/conference_slides/2016/Skuratovich_Chailytko-vb-2016-defating-sandbox-evasion.pdf
"VB2016 上关于对抗虚拟机逃逸的演讲PPT︰ https://t.co/FNJDQKqY7S"
-

[ Tools ] IDA Pro 6.8 magnet:?xt=urn:btih:9d3a25dd5f9be78750b75b64c257574bd878be1f&dn=ida_pro_6.8&tr=udp%3a%2f%2fglotorrents.pw%3a6969%2fannounce
"IDA Pro 6.8 以及反汇编插件泄漏了"
-

[ Windows ] Microsoft Patches Five Zero Days Under Attack: https://threatpost.com/microsoft-patches-five-zero-days-under-attack/121211/ via @ threatpost
"微软发布本月的补丁更新,其中修复了 5 个 0Day: https://t.co/nlb9qniE0t ; 补丁摘要: https://technet.microsoft.com/en-us/library/security/MS16-OCT ; "
-

[ Windows ] MS16-030 (previous PT) analysis - http://blog.vectranetworks.com/blog/triggering-ms16-030-via-targeted-fuzzing
" 通过定向 Fuzz 触发 MS16-030 漏洞: https://t.co/FGUyRjjDs6"
-

[ Windows ] @Laughing_Mantis Also MS16-125 is a incorrect fix for a #pwn2own exploit found originally by lokihardt /cc @thezdi
" MS16-125 当初并没有正确的修复 lokihardt 在 Pwn2Own 所用的漏洞"
-
[ Linux ] linux exploit development tutorial: https://github.com/hardenedlinux/linux-exploit-development-tutorial
-
[ Detect ] Code Relatives: Detecting Similarly Behaving Software(相似行为软件的检测): https://loccs.sjtu.edu.cn//gossip/blog/2016/10/11/2016-10-11/
-
[ Tools ] ShinoBOT – Malware Attack Simulator Framework: http://www.sectechno.com/shinobot-malware-attack-simulator-framework/
-
[ Android ] Android 系统新权限模型剖析与预警:http://blogs.360.cn/360mobile/2016/10/11/android_new_permission_model/
 Xuanwu Spider via GitHub
Xuanwu Spider via GitHub