
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Attack ] Shocking, a German nuclear plant suffered a disruptive cyber attack http://securityaffairs.co/wordpress/52116/security/nuclear-plant-attack.html
" 德国一家核电站遭到网络攻击: https://t.co/71xN8kqQBc"
-

[ Browser ] #DailyBug #Firefox NULL pointer Repro: <track xmlns="..."><feImage xmlns="..." xmlns:xlink="..." xlink:href='?'>… https://twitter.com/i/web/status/785412860222603265
"Firefox NULL pointer (<track xmlns="..."><feImage xmlns="..." xmlns:xlink="..." xlink:href='?'>) : https://bugzilla.mozilla.org/show_bug.cgi?id=1308862
-

[ Conference ] #PacSec 2016 Tokyo Oct26-27 13 talks announced http://pacsec.jp/speakers.html 2days:CAD$650 1day:CAD$400 until Oct20 http://pacsec.jp/register.html
"2016年东京 PacSec 大会发布议题: https://t.co/Du2OrD5Ivn 大会具体安排: https://t.co/H6XUYARCos"
-

[ Conference ] Black Hat USA 2016 videos - https://www.youtube.com/playlist?list=PLbHqJuIbKd_6jPpl9pnXGUmUj8gtlWony
" BlackHat USA 2016 会议的所有视频: https://t.co/mL1ser6ba0"
-

[ Fuzzing ] Test suite for fuzzers: https://github.com/google/fuzzer-test-suite.
" 一组用于测试 fuzzer 效果的测试集: https://t.co/oKa5Zlc0K0 "
-

[ Linux ] Linux Kernel 3.13.1 Recvmmsg Privilege Escalation https://cxsecurity.com/issue/WLB-2016100094
"Linux 内核 3.13.1 Recvmmsg 提权 Exploit: https://t.co/5NqXq7q3TU"
-

[ Linux ] [local] - Linux kernel 4.6.2 - IP6T_SO_SET_REPLACE Privilege Escalation https://www.exploit-db.com/exploits/40489/
" Linux 内核 4.6.2 IP6T_SO_SET_REPLACE 提权 Exploit(CVE-2016-4997): https://t.co/bCinjRJrun"
-

[ Malware ] #VB2016 the slides of our talk on VB2016 is now open: https://www.virusbulletin.com/uploads/pdf/conference_slides/2016/Liu_Wang-vb-2016-TheElknotDDoSBotnetsWeWatched.pdf
" VB2016 会议的一篇关于 Botnet 的演讲《我们观察到的 Elknot DDoS Botnet》,来自 360 网络安全实验室︰ https://t.co/4ywMiWCliJ"
-

[ MalwareAnalysis ] Remsec driver analysis (Part 2) : https://artemonsecurity.blogspot.in/2016/10/remsec-driver-analysis-part-2.html , Part 1 : https://artemonsecurity.blogspot.in/2016/10/remsec-driver-analysis.html
"恶意软件 Remsec 驱动程序分析 【第 2 部分】: https://t.co/orxbYYLFMz ;【部分 1】: https://t.co/TPz2Pi73RZ"
-

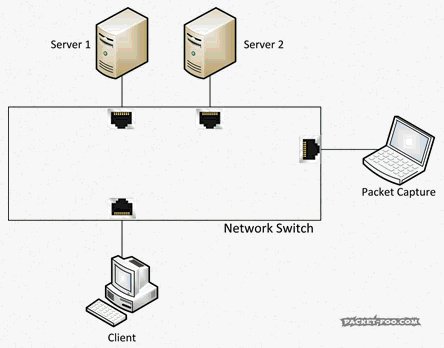
[ NetworkDevice ] The Network Capture Playbook ( Part 1 – Ethernet Basics) : https://blog.packet-foo.com/2016/10/the-network-capture-playbook-part-1-ethernet-basics/ cc @ PacketJay https://t.co/RFhGJ5IeUn
"Network Capture Playbook (第 1 部分 — — 以太网基础): https://blog.packet-foo.com/2016/10/the-network-capture-playbook-part-1-ethernet-basics/"
-

[ OpenSourceProject ] Noto : Google Releases An Open Source Font That Supports 800 Languages : https://opensource.googleblog.com/2016/10/an-open-source-font-system-for-everyone.html , Download Noto : https://www.google.com/get/noto/
" Google 开源了一套新的字体系统 Noto,涵盖 800 种语言和 11 万个符号︰ https://t.co/OjOuEvpt4Q 下载︰ https://t.co/vCbeQA5TAG"
-

[ Others ] mitmproxy – Intercepting HTTP Proxy Tool aka MITM http://www.darknet.org.uk/2016/10/mitmproxy-intercepting-http-proxy-tool-aka-mitm/
"mitmproxy — — 一个用于拦截 HTTP Proxy 的工具: https://t.co/aCMx7wKy6j"
-

[ Others ] DMA attacking over USB-C and Thunderbolt 3 : http://blog.frizk.net/2016/10/dma-attacking-over-usb-c-and.html cc @ UlfFrisk
"通过 USB-C 和 Thunderbolt 3 实现 DMA 攻击: https://t.co/grgmNYaZZ5 "
-

[ Popular Software ] Apache Tomcat (RedHat-Based Distros Pkgs) - Root Privilege Escalation Exploit (CVE-2016-5425) http://legalhackers.com/advisories/Tomcat-RedHat-Pkgs-Root-PrivEsc-Exploit-CVE-2016-5425.html
"Apache Tomcat(RedHat 发行版)修复了一个 Root 提权漏洞(CVE-2016-5425): https://t.co/ygpsczHWlw"
-

[ Rootkit ] HorsePill: a New Type of Linux Rootkit : https://github.com/r00tkillah/HORSEPILL
"HorsePill - 一种新型的 Linux Rootkit: https://t.co/Cl7Xfqm8Ez"
-

[ Tools ] tmux - A terminal multiplexer : https://tmux.github.io/ https://t.co/d0b6kca8lY
"tmux - 一个多窗口的终端工具︰ https://t.co/1c14E5SmFf "
-

[ Tools ] 4nonimizer - A bash script for anonymizing the public IP managing the connection to TOR and different VPNs providers http://www.kitploit.com/2016/10/4nonimizer-bash-script-for-anonymizing_10.html
"4nonimizer-一个 Bash 脚本可用于匿名浏览网页及连接到 TOR、Vpn https://t.co/N1Dfqs0lR3 "
-

[ Tools ] #FreeBSD 11.0-RELEASE Now Available: https://lists.freebsd.org/pipermail/freebsd-announce/2016-October/001760.html
"FreeBSD 发布 11.0 稳定版本︰ https://t.co/jgjSAC5QzG"
-

[ Virtualization ] Added significantly enhanced Xen hypercall fuzzer https://github.com/chipsec/chipsec/blob/master/source/tool/chipsec/modules/tools/vmm/xen/hypercallfuzz.py
" Xen hypercall fuzzer: https://t.co/HhzryJaeMj"
-

[ Windows ] you can use wnf kernel data to find hidden processes: http://redplait.blogspot.ru/2016/10/another-cross-process-scan.html
" 利用 EPROCESS.WnfContext 发现隐藏进程︰ https://t.co/D5F0LKP2fx"
-

[ Windows ] Keep Windows 10 secure - https://github.com/Microsoft/windows-itpro-docs/blob/master/windows/keep-secure/TOC.md - Interesting documentation from Microsoft
" Keep Windows 10 secure,来自微软官方的一份文档,几乎涵盖了 Windows 10 各个方面的安全性: https://github.com/Microsoft/windows-itpro-docs/blob/master/windows/keep-secure/TOC.md "
-

[ WirelessSecurity ] Going Deeper Into GNURadio Companion http://www.hak5.org/episodes/hak5-1601 Decoding Digital Subcarriers with a $20 SDR http://www.hak5.org/episodes/hak5-1602 #SDR
"利用神器 GNURadio 探索 RTL-SDR 【vedio】: https://t.co/HAXFzuoANd ;仅用价值20刀的 SDR 解码数字载波 【vedio】: https://t.co/wAx5Z9dzh2 "
-

[ WirelessSecurity ] Hacking the Drones ( GPS Spoofing over DJI Phantom ) [PDF] https://www.owasp.org/images/5/5e/OWASP201604_Drones.pdf
" 通过 GPS 欺骗的方式 Hacking 大疆无人机: https://t.co/FbvXV8HNU9"
-

[ WirelessSecurity ] Drones Hijacking multi - dimensional attack vectors and countermeasure https://media.defcon.org/DEF%20CON%2024/DEF%20CON%2024%20presentations/DEFCON-24-Aaron-Luo-Drones-Hijacking-Multi-Dimensional-Attack-Vectors-And-Countermeasures-UPDATED.pdf https://www.youtube.com/watch?v=bahJxY3fEI4
" Defcon 24 会议上的一篇演讲《劫持无人机》: https://t.co/LueUNR5IoH 视频: https://t.co/FDmZGBmLsH"
-
[ Browser ] CVE-2016-1707 Chrome Address Bar URL Spoofing on IOS: http://xlab.tencent.com/en/2016/10/09/CVE-2016-1707-Chrome-Address-Bar-URL-Spoofing-on-IOS/
-
[ ] 利用python进行识别相似图片: (1): https://segmentfault.com/a/1190000004467183 (2): https://segmentfault.com/a/1190000004500523?_ea=630748
-
[ Tools ] SQLMAP源码分析——第一讲:架构篇: http://v.youku.com/v_show/id_XMTc1NDI5NjA0OA==.html?refer=eco-h5-wbtb&tuid=UNTgxMDQzNzI4
 Xuanwu Spider via MottoIN
Xuanwu Spider via MottoIN