腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] New in Android N: Strictly Enforced Verified Boot with Error Correction http://android-developers.blogspot.com/2016/07/strictly-enforced-verified-boot-with.html Thanks @ samitolvanen!
" Android 7.0 将启用带错误纠正的严格的启动过程验证: https://t.co/5LvbnxcHjn "
-

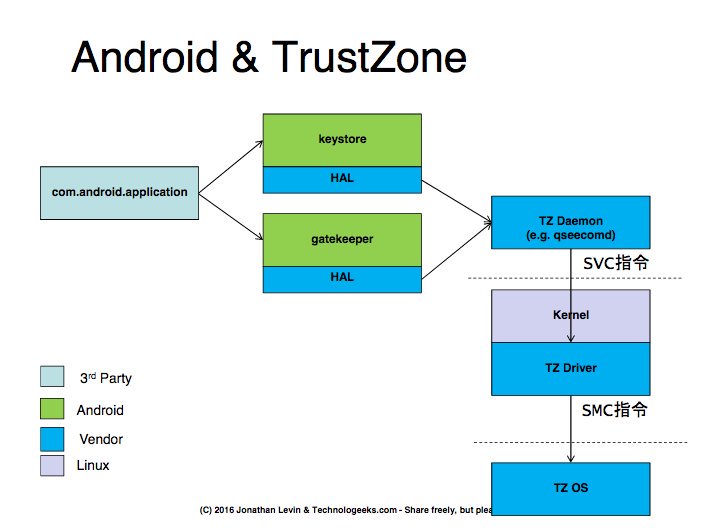
[ Android ] @ Morpheus______ 's presentation slides on #ARM #TrustZone usage in #iOS and #Android #Boot - http://technologeeks.com/files/TrustZone.pdf https://t.co/T9PTFOpcRq
" iOS 和 Android 的启动链与 TrustZone: https://t.co/eLLQ0xQlQp https://t.co/T9PTFOpcRq "
-

[ Attack ] 'Prominent' Admin of Top ISIS Forum Hacked; messages dumped online https://motherboard.vice.com/read/prominent-admin-of-top-isis-jihadi-forum-hacked https://t.co/lLyQC2q65t
" 顶级 ISIS 论坛 jihadi 的管理员被黑: https://t.co/5gdzUwuE8N https://t.co/lLyQC2q65t"
-

[ Detect ] Bypassing Gmail’s Malicious Macro Signatures https://warroom.securestate.com/bypassing-gmails-malicious-macro-signatures/
"绕过 Gmail 的恶意宏特征检测: https://t.co/cQP3OM2kFB"
-

[ Detect ] Detecting the Neutrino exploit kit based on its network behaviour http://capstarforensics.com/?p=713
" 基于网络行为检测 Neutrino EK: https://t.co/AsL8KSUwkC "
-

[ Forensics ] ssd forensics http://goo.gl/0WSn66
" SSD 硬盘取证分析: https://t.co/InBijtq2bh"
-

[ iOS ] Lots of iOS bugs fixed today. I wonder if the imageIO ones were reachable via iMessage: https://support.apple.com/en-au/HT206902
" Apple 更新 iOS 9.3.3 和 OS X 10.11.6,本次更新相关的漏洞公告: https://support.apple.com/en-us/HT201222 "
-

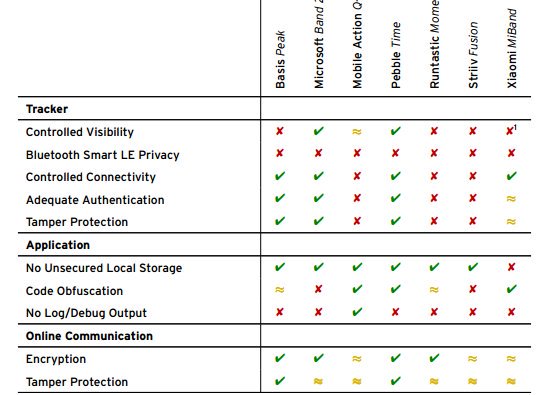
[ IoTDevice ] Internet of Things. Security Evaluation of 7 Fitness Trackers on Android and the Apple Watch https://www.av-test.org/fileadmin/pdf/avtest_2016-07_fitness_tracker_english.pdf https://t.co/ryGdCYZ6sM
" Android 和 Apple Watch 上的 7 款健身手环的安全性分析: https://t.co/24Ciomsjpt https://t.co/ryGdCYZ6sM "
-

[ macOS ] OS X 10.11.5 now available: http://opensource.apple.com/release/os-x-10115/
"OS X 10.11.5 版本的源码也发布了︰ https://t.co/Fqlqw2MHWC"
-

[ Malware ] FireEye researchers analyze the attack process of the Cerber ransomware https://www.fireeye.com/blog/threat-research/2016/07/cerber-ransomware-attack.html https://t.co/mzBP8PtWoH
"FireEye 研究者对 Cerber 勒索软件攻击过程的分析: https://t.co/PLlkL0OPKV https://t.co/mzBP8PtWoH"
-

[ Others ] Drupal 8.1.6 HTTP traffic to an arbitrary proxy server https://cxsecurity.com/issue/WLB-2016070150
"Drupal 8.1.6 因为用到了第三方 PHP 库 Guzzle,所以受 httpoxy 漏洞的影响: https://t.co/aUZQAQCzQb"
-

[ Others ] New search engine lets you search for vulnerabilities in Javascript code https://nerdydata.com/search?terms%5B%5D=(eval%5C(%5B%5E%5C)%5D%2B%5C))®ex=true
" NerdyData - 一个可以搜索 Javascript 代码的搜索引擎,比如可以搜索 eval(): https://t.co/EK0ZRVuq56 "
-

[ Others ] This is a huge bug. ASN.1 bug in objective systems implementation popular on baseband stacks https://twitter.com/4dgifts/status/755179455258226690
" Objective Systems 公司的 ASN1C 编译器生成的代码,在解析 ASN.1 时存在堆溢出漏洞(CVE-2016-5080): https://t.co/6qpjLmD1KN 公告: https://github.com/programa-stic/security-advisories/tree/master/ObjSys/CVE-2016-5080 "
-

[ Others ] SKEE: A Lightweight Secure Kernel-level Execution Environment for ARM https://www.internetsociety.org/sites/default/files/blogs-media/skee-lightweight-secure-kernel-level-execution-environment-for-arm.pdf
" SKEE – 针对 ARM 平台的轻量级 Linux 内核安全执行环境: https://t.co/4MqNZKRDuQ 网安国际有一篇相关的中文介绍: http://www.inforsec.org/wp/?p=796 上海交大 GoSSIP 有一篇对该论文的解读文章: http://www.securitygossip.com/blog/2016/04/11/2016-04-11/ "
-

[ Pentest ] Building an Active Directory Lab : https://www.psattack.com/series/building-an-active-directory-lab/ cc @ jaredhaight
" 搭建一个 Active Directory 渗透测试实验环境︰ https://t.co/OQluiC4OLF "
-

[ Popular Software ] Client-Side Redis Attack PoC https://ericrafaloff.com/client-side-redis-attack-poc/
" 客户端 Redis 攻击 PoC: https://t.co/6jDP48McCV"
-

[ Popular Software ] Multiple Cross-Site Scripting vulnerabilities in Ninja Forms WordPress Plugin http://goo.gl/fb/yd88pX #FullDisclosure
" WordPress 插件 Ninja 表单插件跨站漏洞: https://t.co/whg8TRLADJ PoC: https://sumofpwn.nl/advisory/2016/multiple_cross_site_scripting_vulnerabilities_in_ninja_forms_wordpress_plugin.html "
-

[ Popular Software ] Django CMS v3.3.0 - (Editor Snippet) Persistent Web Vulnerability (CVE-2016… http://goo.gl/fb/gsN6xo #FullDisclosure
"Django CMS v3.3.0 XSS 漏洞(CVE-2016-6186): https://t.co/YeRqqaSGsV "
-

[ Popular Software ] Use After Free Vulnerability in SNMP with GC and unserialize() https://bugs.php.net/bug.php?id=72479
" PHP 5.5.37 SNMP 包的一个 UAF 漏洞: https://t.co/R4BHBRPvoT 还有一个 Session 反序列化相关的 UAF: https://bugs.php.net/bug.php?id=72562 "
-

[ Tools ] SZpy - Z3 Symbolic Execution python. Based on z3. https://github.com/dariosharp/SZpy
"SZpy - 基于 Z3 的符号执行工具: https://t.co/mhmHxEcxhG"
-

[ Tools ] Just open-sourced gotrace. Try it, feedback is welcome. Particularly interested if README is clear enough. #golang https://github.com/divan/gotrace
" gotrace - Go 语言的一款 3D 可视化 Tracer: https://t.co/oHvj2tT0Cr"
-

[ Web Security ] Paypal bug bounty: Updating the Paypal.me profile picture without consent (CSRF attack) https://hethical.io/paypal-bug-bounty-updating-the-paypal-me-profile-picture-without-consent-csrf-attack/
" Paypal Bug Bounty 中(Paypal.me 个人资料图片)的一个 CSRF 漏洞: https://t.co/SUWqGizmCW "
-

[ Web Security ] Stealing Facebook access_tokens using CSRF in device login flow https://www.josipfranjkovic.com/blog/hacking-facebook-csrf-device-login-flow
"通过设备登录过程中的 CSRF 漏洞窃取 Facebook access_tokens: https://t.co/0bobLfyTtT "
-

[ Windows ] Captain Hook: Pirating AVs to Bypass Exploit Mitigations http://breakingmalware.com/vulnerabilities/captain-hook-pirating-avs-bypass-exploit-mitigations/
" Captain Hook - 作者在几款主流 Hook 引擎中发现了 6 个漏洞: https://t.co/9GsPr8K52H"
-

[ WirelessSecurity ] Just released tech report with results from my #LTE #security and #exploit research and @ shmoocon talk. #infosec http://arxiv.org/abs/1607.05171
" 基于低成本无线电设备的 LTE 协议漏洞利用和位置跟踪实验,Paper: https://t.co/sZqVllSG0j"