腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Introduction to debugging Android apps using AndBug http://resources.infosecinstitute.com/android-hacking-and-security-part-23-introduction-to-debugging-android-apps-using-andbug/
" 用 AndBug 逆向调试器调试 Android APP: https://t.co/kj5APC6HbE"
-

[ Android ] MADAM: Effective and Efficient Behavior-based Android Malware Detection and Prevention http://www.iet.unipi.it/g.dini/research/papers/2016-tdsc-ssdm-accepted.pdf
" MADAM - 基于行为的 Android 恶意软件检测技术,Paper: https://t.co/NZF2iFwuqB"
-

[ Browser ] Malware in the browser: how you might get hacked by a Chrome extension https://kjaer.io/extension-malware/
" 浏览器里的恶意扩展 - 没准哪天你就被 Chrome 扩展黑了: https://t.co/sJN7Iv7iEh"
-

[ Crypto ] opensshd - user enumeration http://seclists.org/fulldisclosure/2016/Jul/51
"opensshd - 一个用户名+一个超长的密码字符串,用户名正确或错误时,opensshd 会产生比较明显的时间差,通过这个方法可以枚举出用户名: https://t.co/YSRkQkBNOv"
-

[ Detect ] Detecting malicious behaviour using system calls : http://repository.tudelft.nl/islandora/object/uuid:c71c85bc-d742-449b-88e7-33e172392ec2?collection=education
" 通过监控系统调用检测 OS X 软件的恶意行为︰ https://t.co/plIxakclp1"
-

[ Industry News ] Opera browser sold to a Chinese consortium for $600 million (May be a good time to stop using Opera) : https://www.engadget.com/2016/07/18/opera-browser-sold-to-a-chinese-consortium-for-600-million/
"Opera 浏览器以 6 亿美元的价格卖给了奇虎 360︰ https://t.co/mG57kZ3OJp"
-

[ iOS ] new blogpost on Apple - [CVE-2016-1865] Some unexploitable but unsandboxable OS X/iOS Kernel NULL pointers - https://marcograss.github.io/security/apple/cve/2016/07/18/cve-2016-1865-apple-nullpointers.html
" CVE-2016-1865 - 不可利用、但是从沙箱内也能触发的空指针引用内核 Crash 漏洞: https://t.co/EhBpG3IpCL"
-

[ Malware ] A look at a malicious Word macro that detects virtual environments https://www.vmray.com/word-macro-detects-vm-environments/ https://t.co/ac3r6gyrrR
" 恶意 Word 宏对虚拟环境的探测方法: https://t.co/EgEtNlbGQI https://t.co/ac3r6gyrrR "
-

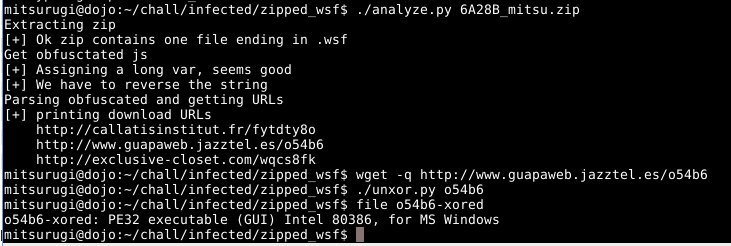
[ Malware ] Automatic analysis of zip with .wsf file inside #malware http://0x90909090.blogspot.fr/2016/07/analyzing-zip-with-wsf-file-inside.html https://github.com/0xmitsurugi/Analyzing-zip-file-with-.wsf-file-inside https://t.co/Nthwv7sc9H
" 内嵌 .wsf 文件的压缩包样本分析: https://t.co/AS9v4KrwaI GitHub Repo: https://t.co/LYEGtzhmcs "
-

[ Others ] IBM report looks at command injection attacks https://securityintelligence.com/command-injection-a-deadly-needle-in-the-haystack/
" 命令注入攻击 - 草堆里的一根针,来自 IBM 的报告: https://t.co/cwuHYQ1FFE"
-

[ Others ] CGI script vuln #httpoxy affects server-side web apps, allows for #MitM attacks on Red Hat products - http://ow.ly/m5FG302n3Ow
" httpoxy - CGI 脚本环境变量冲突漏洞,来自 ThreatPost 的报道: https://t.co/cjZdMY9MKo 该漏洞的官网: https://httpoxy.org/ 来自 360 的一篇分析文章: http://m.bobao.360.cn/learning/detail/2903.html "
-

[ Others ] w00t! I'm in the list of @PwnieAwards nominee for Best Server-Side bug for the Cisco ASA heap exploit :)
" 今年的 Pwnie Awards 奖项提名列表公布了: http://pwnies.com/nominations/ "
-

[ Others ] Have you seen our recent whitepaper: My name is Matt - My voice is my password https://www.nccgroup.trust/uk/our-research/my-name-is-matt-my-voice-is-my-password/
" 我叫马特,我的声音就是我的密码,来自 NCC Group 的研究报告: https://t.co/gLbghTD6pS"
-

[ Popular Software ] Time To Patch: RCE on Meinberg NTP Time Server https://www.securifera.com/blog/2016/07/17/time-to-patch-rce-on-meinberg-ntp-time-server/
" Meinberg NTP 时间服务器 RCE 漏洞: https://t.co/jAUhGbBlg3"
-

[ Tools ] DMitry – Deepmagic Information Gathering Tool http://www.darknet.org.uk/2016/07/dmitry-deepmagic-information-gathering-tool/
" DMitry 信息收集工具,支持端口扫描,邮件地址搜索等等: https://t.co/H4uOrwFJPo"
-

[ Web Security ] Lessons learned from an SVG flaw that used JavaScript to serve a persistent XSS https://hackerone.com/blog/Hacktivity-Highlights:-XSS-via-SVG
" 借助 SVG 实现的 XSS: https://t.co/WFeLUb2eNr "
-

[ Windows ] Running Windows 64-bit in QEMU Emulation Mode : https://www.invincealabs.com/blog/2016/07/running-windows-64bit-qemu/
"在 QEMU 仿真模式下运行 64 位 Windows︰ https://t.co/5y9O8Smbc2"
-

[ Windows ] RCE Endeavors » Runtime DirectX Hooking http://www.codereversing.com/blog/archives/282
" Runtime DirectX Hooking: https://t.co/f4bXFP94nN"