腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Android N's Network Security Config ? to API 17 https://commonsware.com/blog/2016/07/11/backporting-android-n-network-security-configuration.html Nice work @ commonsguy
" 向后移植 Android N 的网络安全配置: https://t.co/NdjF13gbBr "
-

[ Android ] Understanding and Bypassing Reset Protection http://blog.elcomsoft.com/2016/05/understanding-and-bypassing-reset-protection/
"了解和绕过几个主流手机操作系统的出厂重置保护: https://t.co/un9LZ2GKCe"
-

[ Attack ] 白象的舞步——来自南亚次大陆的网络攻击 - http://www.antiy.com/response/WhiteElephant/WhiteElephant.pdf
"白象的舞步 - 来自南亚次大陆的网络攻击,来自安天实验室: https://t.co/I0HhhtTMcr"
-

[ Browser ] A new version of http://html5test.com has been released. Finally! http://blog.html5test.com/2016/07/html5test-has-been-updated/
" 新版 html5test.com 上线了: https://t.co/z8beL6SpCK"
-

[ Browser ] Nice! Mozilla ships its first Rust code in Firefox. Media parsers have been a large attack surface for browsers. https://hacks.mozilla.org/2016/07/shipping-rust-in-firefox/
" Mozilla Firefox 48 版本起将在各桌面平台内置 Rust 组件,其中的 MP4 解析器将用 Rust 代码实现: https://t.co/WLToS14wUA"
-

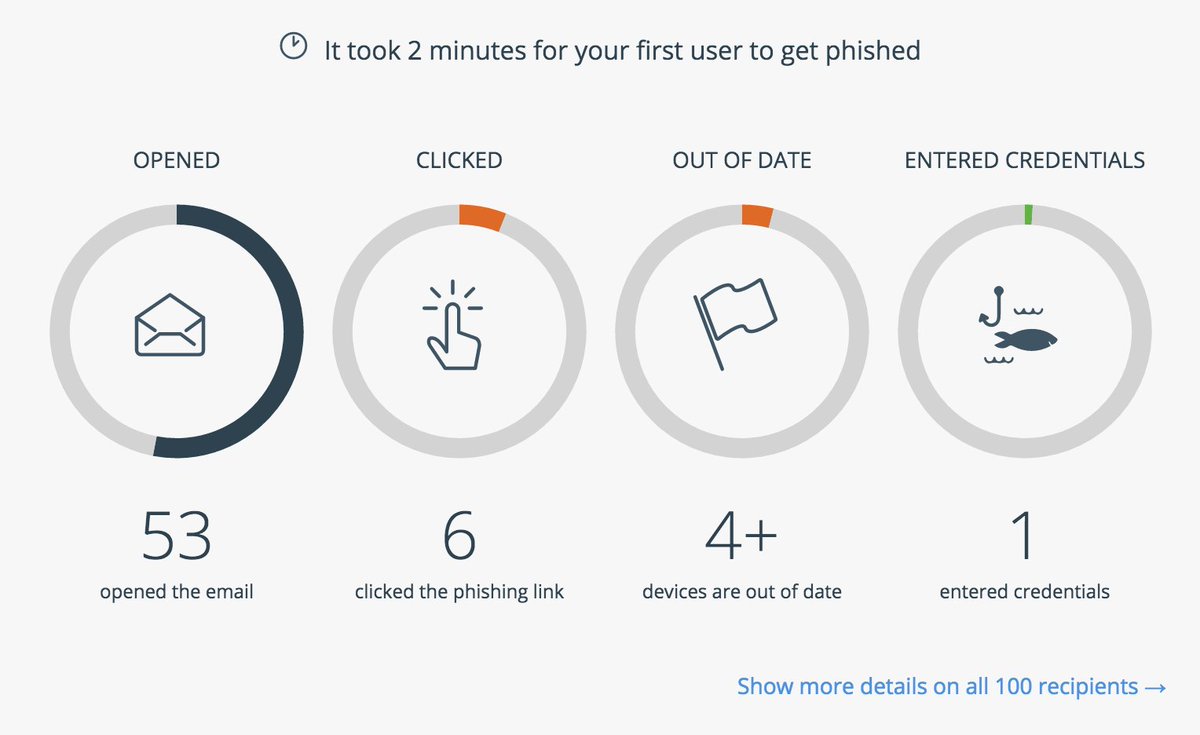
[ Detect ] Now available: Duo Insight, a tool to help organizations identify phishing risks. http://duo.sc/insight_bl https://t.co/RgjFoDl1Mq
" Duo Insight - 一个帮助企业发现钓鱼攻击的工具: https://t.co/2VUncLdEQi https://t.co/RgjFoDl1Mq"
-

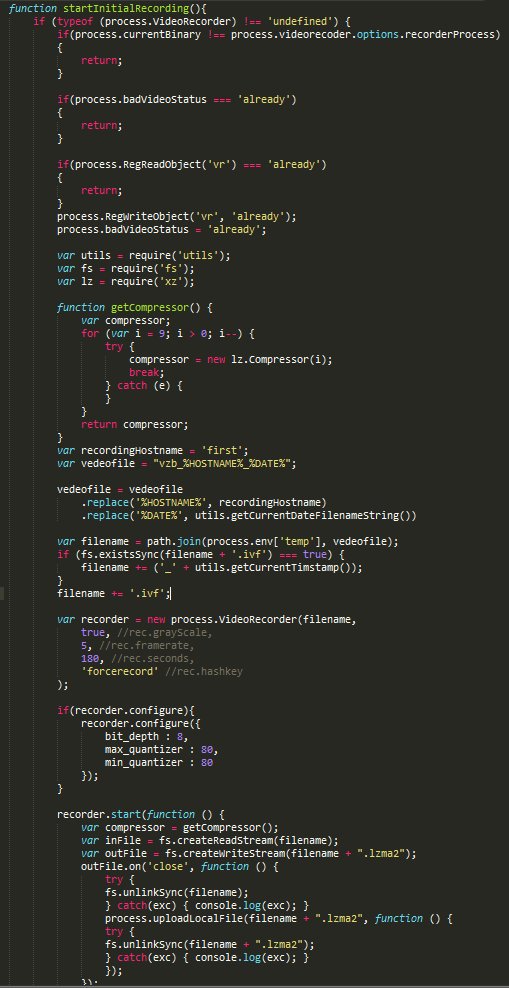
[ Detect ] How to track actors behind keyloggers using embedded credentials http://bit.ly/29NXKb3
" 通过 Keylogger 二进制文件中内嵌的凭据信息追踪背后的攻击者,来自 Palo Alto Blog: https://t.co/ES4azW5YMt "
-

[ Exploit ] New blog post: Windows user-mode exploitation trick – refreshing the main process heap. http://j00ru.vexillium.org/?p=2719
" Windows 用户态漏洞利用技巧 - 刷新主进程堆,来自 j00ru 的 Blog: https://t.co/holiCtNSq1"
-

[ Exploit ] Rat in the Shellcode - How to spawn a remote access terminal with x86 shellcode http://scottgriffy.com/blogs/rat-in-the-shellcode.html
" 在 Shellcode 中实现 RAT 功能: https://t.co/VTMOAHiJnZ"
-

[ Malware ] IBM's @ icyberfighter looks at recent changes made to the Gootkit banking trojan https://securityintelligence.com/gootkit-bobbing-and-weaving-to-avoid-prying-eyes/ https://t.co/mR5bx6GmuK
" Gootkit 银行木马最近的一些变化: https://t.co/bbgwpF1mqF https://t.co/mR5bx6GmuK "
-

[ Malware ] A look at the embedded configuration of the LuminosityLink RAT, by @ jgrunzweig http://researchcenter.paloaltonetworks.com/2016/07/unit42-investigating-the-luminositylink-remote-access-trojan-configuration/
" LuminosityLink 远控木马内嵌的配置信息分析,来自 Palo Alto Blog: https://t.co/Ldx9UebreF "
-

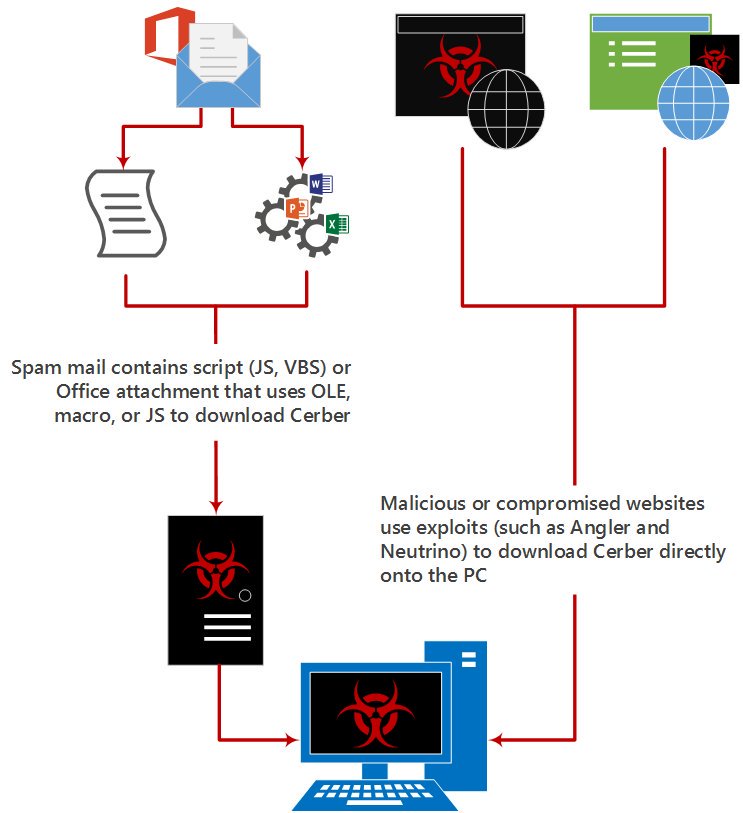
[ Malware ] MSRT July features Cerber ransomware detection: http://ow.ly/htaR302b6bv https://t.co/HetRUvl6eH
"MSRT(微软恶意软件防护中心)观测到的 Cerber 勒索软件的 7 月份数据信息︰ https://t.co/RiihOsBHLD https://t.co/HetRUvl6eH"
-

[ Network ] Gaining Control of a .int Domain Name With DNS Trickery : https://thehackerblog.com/the-international-incident-gaining-control-of-a-int-domain-name-with-dns-trickery/index.html cc @ IAmMandatory
" 通过 DNS 的技巧控制一个 .int 的域名︰ https://t.co/aur2E8eGuR "
-

[ Network ] Understanding IP Addressing : Everything You Ever Wanted To Know : https://web.archive.org/web/20080405225344/http://www.3com.com/other/pdfs/infra/corpinfo/en_US/501302.pdf (pdf)
" IP 网络寻址的过程︰ https://t.co/rXqKd08bZO "
-

[ NetworkDevice ] Belkin Router AC1200 Authentication Bypass https://packetstormsecurity.com/files/137857/Belkin-Router-AC1200-Authentication-Bypass.html
" Belkin AC1200 路由器身份验证绕过漏洞: https://t.co/3jGS1Gbws4"
-

[ Others ] My slides from @ securityfest are now online! "The Secret Life of a Bug Bounty Hunter" http://www.slideshare.net/fransrosen/the-secret-life-of-a-bug-bounty-hunter-frans-rosn-security-fest-2016
" The Secret Life of a Bug Bounty Hunter: https://t.co/5IJIFRlMYv "
-

[ Popular Software ] .@ Adobe patches 52 vulns in #FlashPlayer, many lead to RCE - http://ow.ly/Dwst302b67o
" Adobe 发布本月的 FlashPlayer 漏洞公告,共修复 52 个漏洞: https://t.co/zl06MJ6FoE 还有 Acrobat 阅读器的公告: https://helpx.adobe.com/security/products/acrobat/apsb16-26.html "
-

[ Popular Software ] Advisories and PoC for APSB16-25 and APSB16-26: https://smsecurity.net/vulnerabilities/ , https://cosig.gouv.qc.ca/en/advisory/
" COSIG 研究员发现的几个 Adobe Acrobat Reader DC 漏洞的公告和 PoC: https://t.co/HZdYbMMrjA https://t.co/iyDV99zy6O"
-

[ Tools ] Nmap Command For Network Administrator http://www.kalitut.com/2015/12/nmap-command-for-network-admins.html #Kalilinux #Linux #kali #Nmap #Network https://t.co/YFvHyC9fqs
" Nmap 扫描工具使用指南: https://t.co/6yFJIt1iNd https://t.co/YFvHyC9fqs"
-

[ Tools ] DebugView++ https://goo.gl/D2fG25 an open source viewer for Win32 OutputDebugString
" DebugViewPP - Win32 调试输出查看工具: https://t.co/nAkcehDff7 "
-

[ Tools ] PoshC2 – Powershell C2 http://www.hackwhackandsmack.com/?p=693 (Post exploitation assistance)
"PoshC2 — Powershell 版 C&C 实现: https://t.co/DArmD9zcgO "
-

[ Tools ] Automater – IP & URL OSINT Tool For Analysis http://www.darknet.org.uk/2016/07/automater-ip-url-osint-analysis/
"Automater — 一个开源的威胁情报工具,指定一个 IP/域名/文件名/Hash 值,返回从 VirusTotal 等网站获取的相关信息: https://t.co/aoupnBLOYV "
-

[ Tools ] #SoundKeylogger - Open source #keylogger based on keystroke pattern analysis - https://github.com/rodrigoalvesvieira/SoundKeylogger
"SoundKeylogger - Keylogger,通过窃听键盘敲击声音还原按键,目前还是实验版本: https://t.co/mshTHRrNL7"
-

[ Web Security ] Cross-Site Scripting vulnerability in Profile Builder WordPress Plugin http://goo.gl/fb/eqy64l #FullDisclosure
" WordPress Profile Builder 插件的 XSS 漏洞,来自 FullDisclosure 公告: https://t.co/n0QiV9VUF3 还有一个 Master Slider 插件的 XSS: http://seclists.org/fulldisclosure/2016/Jul/27 "
-

[ Windows ] Technical advisory and blog post for MS16-087 / CVE-2016-3238 is up: http://blog.vectranetworks.com/blog/microsoft-windows-printer-wateringhole-attack
" 搞定了一台打印机就搞定了整个网络(基于 MS-WPRN 协议),所涉及的漏洞为 MS16-087/CVE-2016-3238,来自 Vectra Blog︰ https://t.co/nzG6rBX6Mo"
-

[ Windows ] Patch Now: Simple Office 'Protected View' Bypass Could Have Big Impact CVE-2016-3279 https://blogs.mcafee.com/mcafee-labs/patch-now-simple-office-protected-view-bypass-could-have-big-impact/
" 一个简单的 Office 保护视图绕过漏洞可能会产生很严重的影响(CVE-2016-3279),来自 McAfee Blog: https://t.co/4MATP4Ffdr"
-

[ Windows ] Microsoft released six critical bulletins + fixed a RCE flaws in Windows print spooler components #PatchTuesday - http://ow.ly/yEqB302bggj
"微软发布 7 月份漏洞补丁公告,其中有 6 个为严重级别,来自 ThreatPost 对其中 Print Spooler RCE 漏洞的报道: https://t.co/io4nCli5z1 本月的补丁摘要: https://technet.microsoft.com/en-us/library/security/ms16-jul.aspx 本月的致谢信息: https://technet.microsoft.com/library/security/mt674627.aspx "