腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Cool attack. Hacking smartphones via voice commands hidden in YouTube videos https://www.helpnetsecurity.com/2016/07/11/hacking-smartphones-voice-commands/
" 通过 YouTube 视频中内嵌的语言命令黑掉智能手机: https://t.co/mksBpA5FTt "
-

[ Android ] Malicious #PokémonGo App Installs Backdoor on #Android Devices: https://threatpost.com/malicious-pokemon-go-app-installs-backdoor-on-android-devices/119174/ via @ threatpost
" 一个被篡改的、带后门的 Pokémon Go 游戏应用正在 Android 设备上传播: https://t.co/VdpNWKrPbz"
-

[ Android ] Security at your Fingertips. A dive into Marshmallow’s new fingerprint and keystore APIs https://droidcon.de/sites/global.droidcon.cod.newthinking.net/files/media/documents/Talk-%20Security%20at%20your%20Fingertips._0.pdf https://t.co/YPrZZn5Ul9
" Android Keystore 以及如何生成 APP 私有的密钥: https://t.co/y1sAqVgztY https://t.co/YPrZZn5Ul9 "
-

[ Android ] TaintDroid depth analysis http://drops.wooyun.org/mobile/17417 (Chinese)
" TaintDroid 深入剖析之启动篇,来自 WooYun Drops: https://t.co/H2CeA2CGZR "
-

[ Browser ] I wrote a privacy analysis of @ w3c Vibration API. Privacy engineer's point of view, uses and abuses. https://blog.lukaszolejnik.com/privacy-of-w3c-vibration-api/
" W3C 的振动(Vibration) API 隐私问题分析: https://t.co/fan9kg8oPL"
-

[ Browser ] The Future of Browser History — https://medium.com/@ patrykadas/browserhistory-2abad38022b1#.w2jtzjcjj
"浏览器历史访问记录的未来: https://t.co/m0K7Az3D2S"
-

[ Browser ] The Scriptless Scriptlet - Or how to execute JavaScript from CSS in MSIE11 without using Scripts https://gist.github.com/cure53/521c12e249478c1c50914b3b41d8a750
" IE11 中,如何通过 CSS 执行 JavaScript 脚本: https://t.co/g3m3pa628E"
-

[ Detect ] Anti Ransom: Detect and stop ransomware via honeypot, dumping memory for key extraction http://www.security-projects.com/?Anti_Ransom
" Anti Ransom - 通过蜜罐检测和阻断勒索软件的开源工具: https://t.co/pnhsN4ioTT "
-

[ Detect ] CryptoLock (and Drop It) : Stopping Ransomware Attacks on User Data : http://www.cise.ufl.edu/~traynor/papers/scaife-icdcs16.pdf (pdf)
" CryptoDrop - 勒索软件检测和阻断工具,Paper︰ https://t.co/ddeY54HXp9 "
-

[ Hardware ] 91 percent of public-facing #ICS components are remotely exploitable - http://ow.ly/HYUs3027CvN #SCADA
"91% 的面向公众的工控组件是可被远程攻击的,来自 ThreatPost 的报道: https://t.co/9sfoG0zZqf 来自 Kaspersky 的《工控威胁现状研究报告》: https://securelist.com/analysis/publications/75343/industrial-cybersecurity-threat-landscape/ "
-

[ Malware ] Late last month, the Rig exploit kit started spreading an updated Cryptobit ransomware http://researchcenter.paloaltonetworks.com/2016/07/unit42-cryptobit-another-ransomware-family-gets-an-update/
"上个月下旬,Rig Exploit Kit 开始传播更新后的 Cryptobit 勒索软件,来自 Palo Alto Blog: https://t.co/BcyQTCrhAr"
-

[ OpenSourceProject ] 2 new programs! CSRFGuard http://bgcd.co/29CnEje & Java HTML Sanitizer Project http://bgcd.co/29CnBUE by @ owasp https://t.co/Zs6ZVERGML
" OWASP 的两个项目 CSRFGuard 和 Java Sanitizer 正在参加 Bugcrowd 的 Bug Bounty 计划: https://bugcrowd.com/owaspcrsfguard https://bugcrowd.com/owaspjavasanitizer "
-

[ Others ] Shadow of a Doubt: Testing for Divergences Between Software Versions http://srg.doc.ic.ac.uk/files/papers/shadow-icse-16.pdf
" 这篇 Paper 提出了一种技术,基于符号执行,生成只对新版本补丁引入代码覆盖的测试输入: https://t.co/etnKBVjx7e"
-

[ Popular Software ] KeeThief – A Case Study in Attacking KeePass Part 2 http://www.harmj0y.net/blog/redteaming/keethief-a-case-study-in-attacking-keepass-part-2/
"KeeThief — 针对密码管理软件 KeePass 的攻击案例研究 Part 2: https://t.co/Ly7k8GQ5vf "
-

[ Popular Software ] TeamPass @ TheTeamPass fixed critical security issues with the help of RIPS http://teampass.net/2016-05-13-release-2.1.26#security-analysis-with-rips
"团队密码管理软件 TeamPass 刚刚修复了一个任意文件下载漏洞: https://t.co/S28HHsswZ6 "
-

[ ReverseEngineering ] awesome-reversing A curated list of #awesome #reversing resources Author: @ tylerhalfpop https://github.com/tylerhalfpop/awesome-reversing
" Awesome Reversing Resources,逆向方向的学习资料: https://t.co/dLm7G75U9y"
-

[ Tools ] Frankencert - Adversarial Testing of Certificate Validation in SSL/TLS Implementations https://github.com/sumanj/frankencert
"Frankencert - SSL/TLS 证书验证对抗性测试工具,GitHub Repo: https://t.co/dQrSdDQWMw"
-

[ Tools ] Visualizing relationships between python packages https://kozikow.com/2016/07/10/visualizing-relationships-between-python-packages-2/
"可视化 Python 库的相互引用关系: https://t.co/WBxqc0XCw9 "
-

[ Tools ] https://github.com/siberas/IDA2Sym
" IDA2Sym - 在 IDA 中创建可以被 WinDbg 加载的符号文件: https://t.co/q7mRfEhU5i"
-

[ Windows ] Vulnerability Spotlight: Local Code Execution via the Intel HD Graphics Windows Kernel Driver http://blog.talosintel.com/2016/07/Intel-HD-Graphics-Vulnerability.html
" Intel 高清图形处理驱动(Windows)本地代码执行漏洞(CVE-2016-5647),来自 Talos 的公告: https://t.co/Sto7g2HtPK"
-

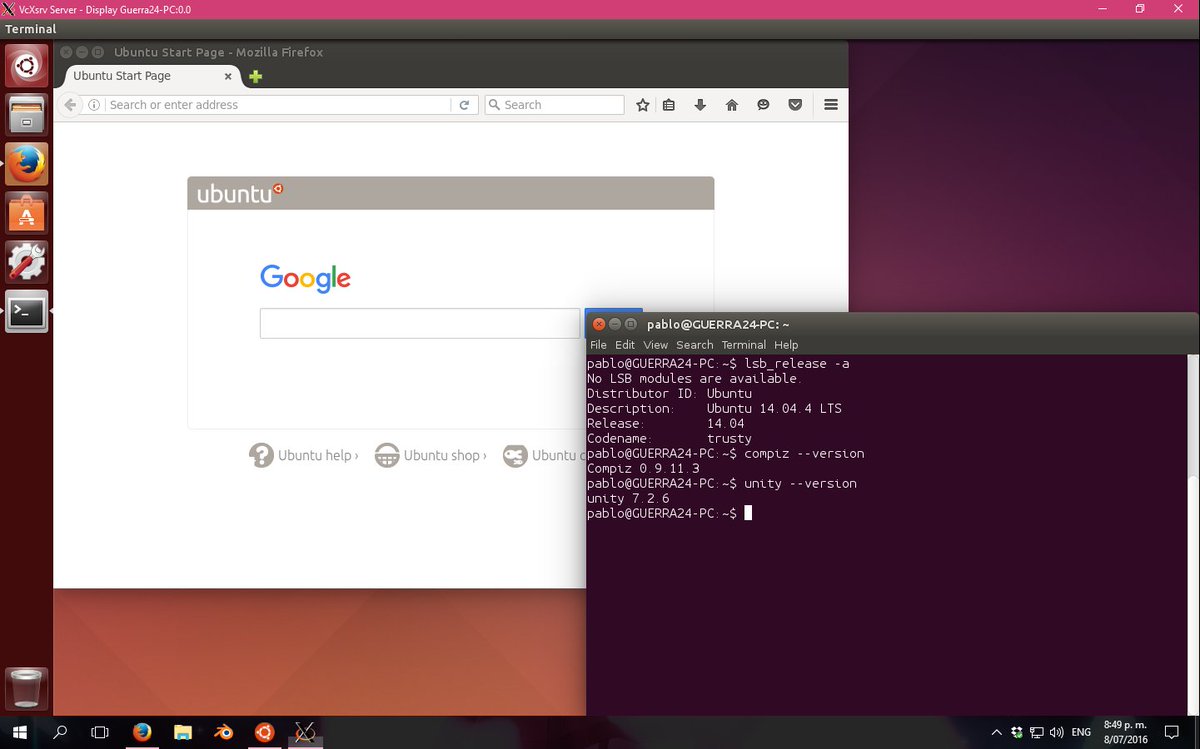
[ Windows ] Ubuntu's Unity desktop environment can run in Windows : https://github.com/Microsoft/BashOnWindows/issues/637 https://t.co/k4B0JfVvYe
"Ubuntu Unity 桌面视窗环境可以在 Windows 上运行,但还存在一些稳定性问题︰ https://t.co/WQPswrWvDm https://t.co/k4B0JfVvYe"
-

[ Windows ] Journey to HackSys Extreme Vulnerable Driver - Windows 7 x64 by my friend @ sizzop https://sizzop.github.io/ https://github.com/hacksysteam/HackSysExtremeVulnerableDriver
" HackSys Extreme Vulnerable Driver 实战(1,2,3,4): https://t.co/0Cl2FU6MXx https://t.co/6EsokCgWbu"