腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Bandicoot - An Open-source Python Toolbox To Analyze Mobile Phone Metadata http://buff.ly/28L0W7f #metadata #phone https://t.co/RzkdirMoqT
" Bandicoot - 可视化分析手机应用元数据的一个开源工具套件: https://t.co/UYbsHOIPle https://t.co/RzkdirMoqT"
-

[ Android ] Online analysis system for packed Android malware https://github.com/CvvT/AppTroy
" AppTroy - 加壳后的 Android 恶意软件在线分析工具,可以实现脱壳、反混淆、监控 API 调用: https://t.co/cZ4FQHxqZk "
-

[ Attack ] Fraudsters are Buying IPv4 Addresses https://www.schneier.com/blog/archives/2016/06/fraudsters_are_.html
" IPv4 地址买卖中的诈骗: https://t.co/aMiS4HKOmB"
-

[ Attack ] Hewlett Packard Enterprise (HPE) Cyber Risk Report 2016 http://techbeacon.com/resources/2016-cyber-risk-report-hpe-security
" 惠普 HPE 团队发布 2016 安全风险研究报告: https://t.co/U3ZGkrudoo"
-

[ Attack ] Carbonite online backup accounts under password reuse attack, Stop passwork-reuse abuse ! ~ http://www.theregister.co.uk/2016/06/22/carbonite_accounts_password_reuse_attack/ via @ theregister
" 在线备份服务厂商 Carbonite 遭到密码重用攻击,来自 TheRegister 的报道: https://t.co/VHVSAmImld"
-

[ Attack ] The number of corporate devices attacked with crypto-ransomware increased almost 6 times in the past year. https://securelist.com/analysis/publications/75145/pc-ransomware-in-2014-2016/
"2014~2016 勒索软件发展趋势报告,来自 Kaspersky: https://t.co/6tSrQyaFBg"
-

[ Attack ] T-Mobile Czech Employee Steals and Sells 1.5 Million Users Data ~ http://thehackernews.com/2016/06/t-mobile-hacked.html #Security
"T-Mobile 捷克员工窃取并售卖 150 万用户数据: https://t.co/bJ80bJShi1 "
-

[ Browser ] Microsoft Edge CBaseScriptable PrivateQueryInterface Uninitialized Memory Remote Code Execution Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-371/
" Edge 浏览器 CBaseScriptable PrivateQueryInterface 未初始化内存 RCE,来自 ZDI 的公告: https://t.co/gc61VfkjPX"
-

[ Browser ] Proof-of-Concept for spraying high addresses in Chrome & Firefox on 64-bit Windows: http://blog.skylined.nl/20160622001.html (+ details on CVE-2014-1736)
" 64 位 Windows,Chrome/Firefox 浏览器高地址 HeapSpray PoC ︰ https://t.co/v73TfTLreG Blog 后面还分析了 Chrome createImageData 任意地址读写漏洞(CVE-2014-1736)"
-

[ Browser ] Leaner, smarter, faster: JavaScript performance updates in Edge & Chakra https://blogs.windows.com/msedgedev/2016/06/22/javascript-performance-updates-anniversary-update/#cAhDyQOe2o8FfeYh.99
" Edge 浏览器 Chakra 引擎 JavaScript 处理性能提升,来自微软 Blog: https://t.co/Brk0lhapdY"
-

[ Crypto ] NCC Group Whitepaper: How to Backdoor Diffie-Hellman - https://www.nccgroup.trust/globalassets/our-research/us/whitepapers/2016/june/how-to-backdoor-diffie-hellmanpdf by @ lyon01_david - learn what to look for!
" 如何在 Diffie-Hellman 加密算法中植入后门,来自 NCC Group 的 Paper: https://t.co/kuebudw6OS "
-

[ iOS ] Apple Releases unobfuscated iOS 10 kernel https://www.technologyreview.com/s/601748/apple-opens-up-iphone-code-in-what-could-be-savvy-strategy-or-security-screwup/
" 之前版本的 iOS 内核,苹果都会混淆或加密,而最近的 iOS 10 预览版中,苹果放了一个未混淆的版本: https://t.co/UfAFMafxlH"
-

[ Linux ] Linux Kernel ROP part 2 is out on the #SpiderLabs blog https://www.trustwave.com/Resources/SpiderLabs-Blog/Linux-Kernel-ROP---Ropping-your-way-to---(Part-2)/
" Linux 内核 ROP Part 2 - 通往 ROOT 的 ROP 之路: https://t.co/N7dxBT9xpY"
-

[ Malware ] New post: After Angler: Shift in Exploit Kit Landscape and New Crytpo-Ransomware Activity http://bit.ly/28PCzrp @ TrendMicro
" Angler EK 消失之后,市场的新变化,来自 TrendMicro Blog: https://t.co/6DQT8dm6cL "
-

[ Malware ] Macro Malware Adds Tricks, Uses MaxMind to Avoid Detection https://blogs.mcafee.com/mcafee-labs/macro-malware-adds-tricks-uses-maxmind-to-avoid-detection/
"宏恶意软件通过 MaxMind 服务获取 IP 地址信息,躲避检测,来自 McAfee Blog: https://t.co/sKzeh6CVuV"
-

[ Malware ] Analyzing the New Locky Javascript Downloader https://malcat.moe/?p=53
" Locky 勒索软件新的 JavaScript 下载器分析: https://t.co/DMLi8jyX4a"
-

[ OpenSourceProject ] VULNERABILITY SPOTLIGHT: PIDGIN VULNERABILITIES -http://blog.talosintel.com/2016/06/vulnerability-spotlight-pidgin.html by @ TalosSecurity
" Talos 团队研究员发现了 Pidgin 聊天客户端的 16 个漏洞: https://t.co/qd5so363ES"
-

[ Sandbox ] TIL about AppContainers on Windows from looking into the Chromium sandbox: https://github.com/MalwareTech/AppContainerSandbox
" 基于 Windows AppContainers 的沙箱实现示例代码, GitHub Repo︰ https://t.co/GUO4mk7CuS"
-

[ Tools ] Added the ability to search Shodan for websites that are using certain technologies, ex: jQuery - https://www.shodan.io/search?query=http.component%3Ajquery
" Shodan 搜索引擎支持以网站组件为条件搜索了,如: jQuery: https://t.co/FVzQoSNC5r"
-

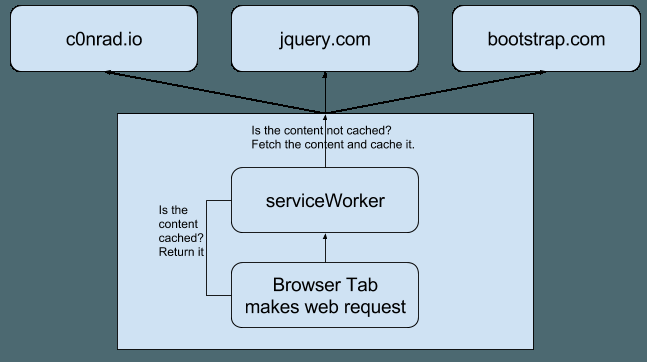
[ Web Security ] XSS persistence using JSONP and serviceWorkers https://c0nradsc0rner.wordpress.com/2016/06/17/xss-persistence-using-jsonp-and-serviceworkers https://t.co/ruuXhkUtWC
" 基于 JSONP 和 serviceWorkers 的 XSS 持久攻击技术: https://t.co/hzMN47Zus0 https://t.co/ruuXhkUtWC"
-

[ Windows ] Rekall and the windows PFN database http://rekall-forensic.blogspot.ch/2016/05/rekall-and-windows-pfn-database.html
"Rekall 内存取证框架与 Windows PFN 数据库: https://t.co/kgloNg1Nrd"
-

[ Windows ] Microsoft Windows Diagnostics Hub Standard Collector Directory Traversal Privilege Escalation Vulnerability http://www.zerodayinitiative.com/advisories/ZDI-16-372/
"微软 Windows 诊断中心采集器目录穿越提权漏洞(CVE-2016-3231),来自 ZDI 的公告: https://t.co/6BuIzpFlGv"