腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Android Trojan "Hellfire" modified system binaries, boot image, init.rc, SE policy rules, dm_verify, etc. http://blogs.360.cn/360mobile/2016/06/21/analysis_of_diyuhuo/ (Chinese)
" '地狱火' 手机病毒 - 源自安卓系统底层的威胁,来自 360 移动安全团队: https://t.co/b9yTqoWeXY "
-

[ Android ] New post: ‘GODLESS’ Mobile Malware Uses Multiple Exploits to Root Devices http://bit.ly/28N8Yih @ TrendMicro
" Android 恶意软件家族 Godless 利用多个 Exploits Root Android 设备,来自 TrendMicro Blog: https://t.co/Y2KYNItzvs "
-

[ Attack ] REcon slides "Visiting The Bear Den" #sednit #apt28 #reconmtl are up! http://www.welivesecurity.com/wp-content/uploads/2016/06/visiting_the_bear_den_recon_2016_calvet_campos_dupuy-1.pdf with @ __ek0 @ nyx__o
" 参观熊窝 - 追踪 APT 组织 Sednit 的间谍行动,来自 ESET 研究员在 RECon 会议的演讲: https://t.co/iOWBHcwBrf "
-

[ Attack ] GitHub Security Update: Reused password attack from attackers replayed using lists of compromised accounts https://github.com/blog/2190-github-security-update-reused-password-attack
"周二晚上,有黑客尝试通过密码撞库攻击的方式攻击 GitHub 用户账户,来自 GitHub Blog: https://t.co/UzhwpzXWX3 "
-

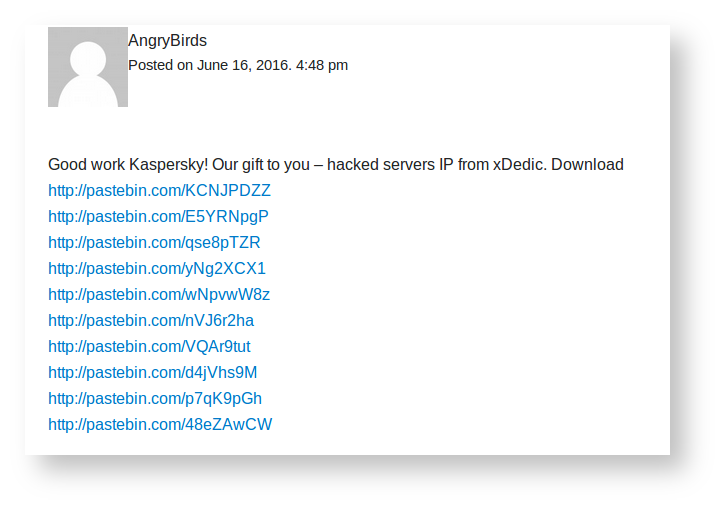
[ Attack ] Our analysis of AngryBirds' xDedic Pastebin leak: https://securelist.com/blog/research/75120/the-tip-of-the-iceberg-an-unexpected-turn-in-the-xdedic-story/ https://t.co/YcY6ll9FpV
" xDedic 故事未曾料到的逆转 ︰ https://t.co/TeYsfT8xUD https://t.co/YcY6ll9FpV"
-

[ Attack ] Red Line Drawn: China Recalculates Its Use of #CyberEspionage https://www.fireeye.com/blog/threat-research/2016/06/red-line-drawn-china-espionage.html #ThreatIntel https://t.co/IOSdXq8Liw
" 一条红线与中.国的网络间.谍攻击分析报告,来自 FireEye: https://t.co/B79MurlWRM https://t.co/IOSdXq8Liw"
-

[ Attack ] Resurrection of the Evil Miner http://www.fireeye.com/blog/threat-research/2016/06/resurrection-of-the-evil-miner.html
"邪恶矿工的复活(比特币挖矿攻击行动),来自 FireEye Blog: https://t.co/OUbzqcsW5n"
-

[ Crypto ] Slides from my talk "Secure channels - are we there yet?" now online - bonus; new attack on OpenSSH, slide 44 on: http://www.turing-gateway.cam.ac.uk/documents/tgmw35/Kenny%20Paterson.pdf
" 我们真的在使用安全的信道通信吗, Slides ︰ https://t.co/to3SKRCHsV"
-

[ Forensics ] Understanding Critical Windows Artifacts and Their Relevance During Investigation http://resources.infosecinstitute.com/understanding-critical-windows-artifacts-and-their-relevance-during-investigation/
" Windows 应急响应调查与 NTFS 时间戳,来自 InfoSec Blog: https://t.co/puRNeH4zCF"
-

[ Hardware ] BadUSB 2.0 USB-HID MiTM POC : https://github.com/withdk/badusb2-mitm-poc h/t : @ drcruft
"BadUSB 2.0 USB-HID 中间人劫持 PoC, GitHub Repo: https://t.co/5PVJRIdZUC "
-

[ Linux ] Adventures in HardenedBSD https://github.com/lattera/presentations/blob/master/NYCBUG/2016/Adventures%20in%20HardenedBSD.pdf [PDF] https://t.co/z6Kr3nmfw0
"FreeBSD 的安全加固历史: https://t.co/suNyUleE6K https://t.co/z6Kr3nmfw0 "
-

[ macOS ] DNS parsing flaw patched in @ Apple #AirPort base stations https://threatpost.com/apple-patches-airport-remote-code-execution-flaw/118787/ via @ threatpost
" 苹果刚刚修复了一个 AirPort DNS 数据解析远程代码执行漏洞,来自 ThreatPost 的报道: https://t.co/SXXxioRF4l"
-

[ Malware ] JavaScript-PHP Joint Exercise Delivers Nemucod Ransomware https://blogs.mcafee.com/mcafee-labs/javascript-php-joint-exercise-delivers-nemucod-ransomware/
" Nemucod 勒索软件利用 JavaScript 和 PHP 联合传播,来自 McAfee Blog: https://t.co/UQSIKTIj1G"
-

[ Malware ] New post: JScript-toting Ransomware Can Steal Your Passwords and Bitcoin Wallets, Too http://bit.ly/28KRWkE @ TrendMicro
" JScript 编写的勒索软件 RAA,可以盗取密码和比特币,来自 TrendMicro Blog: https://t.co/r1ivhZ01UN "
-

[ Mitigation ] Mitigating Stagefright Attacks with the ARM Performance Monitoring Unit https://www.endgame.com/blog/mitigating-stagefright-attacks-arm-performance-monitoring-unit
" ARM 性能监控单元(PMU)可以被用于监控系统调用,缓解 Stagefright 攻击: https://t.co/svlu0W7xgM 作者在 RECon 会议关于这个议题的演讲: http://pages.endgame.com/rs/627-YBU-612/images/hardware-assisted-rootkits-ARM_spisak.pdf "
-

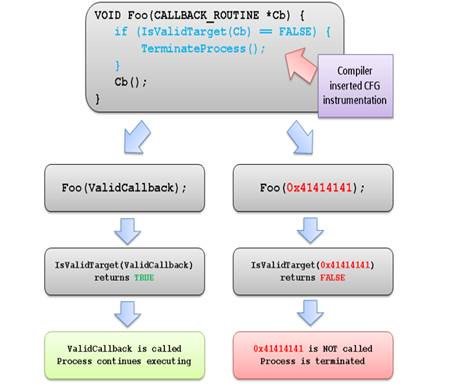
[ Mitigation ] Documenting the Undocumented: Adding Control Flow Guard Exceptions: http://breakingmalware.com/uncategorized/documenting-undocumented-adding-control-flow-guard-exceptions/ https://t.co/wfWXzJsdw7
" 通过一个未文档化的方法,在 CFG 合法 Bitmap 插入一个例外,以此绕过 CFG 的保护,来自 BreakingMalware Blog ︰ https://t.co/ipihu7Zmmu https://t.co/wfWXzJsdw7"
-

[ Network ] NCC Group Whitepaper: Local net compromise - dangers of NBNS/LLMNR spoofing attacks & how to prevent - https://www.nccgroup.trust/uk/our-research/local-network-compromise-despite-good-patching/?research=Whitepapers by @ jonmacf
" 局域网 NBNS/LLMNR 欺骗攻击与防御,来自 NCC Group 的 Paper: https://t.co/hlWqZMzXfr "
-

[ OpenSourceProject ] More compression bugs discovered by @ _Icewall http://blog.talosintel.com/2016/06/the-poisoned-archives.html ! Test them on your favorite security device today!
" Talos 团队发现了 libarchive 库的多个漏洞: https://t.co/sv3FSvbzd8 "
-

[ Others ] CPU RSB based side-channel analysis as applied to detecting VMM. Slides: http://www.c7zero.info/stuff/hyper-channel_toorcon_seattle.ppt [ppt]: https://m.youtube.com/watch?v=UN8iXdMZP2s
" 基于 CPU RSB 的边信道攻击,可以被用于检测 VMM,来自 2008 年的一篇演讲︰ https://t.co/xteJoQOOzE Youtube 视频: https://t.co/LJ8OcnbmDh"
-

[ Others ] Visualising the .NET Garbage Collector http://mattwarren.org/2016/06/20/Visualising-the-dotNET-Garbage-Collector/
" 可视化 .NET 的垃圾回收器(GC): https://t.co/Uq3XCI74z9"
-

[ Others ] Dell 2410U monitor exploitation, PoC assisted by the USB armory https://twitter.com/jatinkataria/status/744599163795611649
" Dell 2410U 显示器代码执行 PoC: https://t.co/g8VV5JuLcu GitHub Repo: https://github.com/RedBalloonShenanigans/MonitorDarkly "
-

[ Pentest ] Penetration testing tools cheat sheet quick reference high level overview 4 typical penetration testing engagements https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/
" 渗透测试工具清单(包括详细的工具使用步骤、命令行参数): https://t.co/ajMrwGGKwf"
-

[ Tools ] Using nmap? Here's a great cheat sheet ~ https://highon.coffee/blog/nmap-cheat-sheet/
" Nmap 扫描器使用手册: https://t.co/AwyHPl2fLw"
-

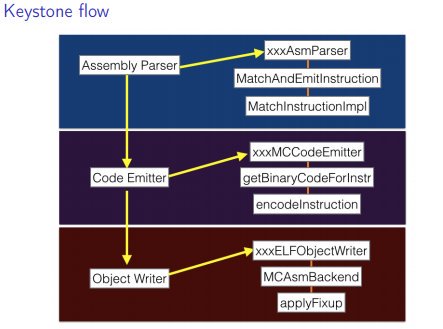
[ Tools ] KEYSTONE : The last missing framework for Reverse Engineering : http://www.keystone-engine.org/docs/RECON2016-keystone.pdf (pdf) https://t.co/uoQh9mJMAc
" Keystone - 逆向欠缺的最后一个框架,来自 Keystone 作者在 RECon 会议的演讲︰ https://t.co/swFT2DxVd5 https://t.co/uoQh9mJMAc"
-

[ Windows ] #DailyBug magic values in 32-bit processes on 64-bit OS-es and how to exploit them at http://blog.skylined.nl (with details on two bugs)
" 64 位操作系统 32 位进程中的一些 Magic Number: https://t.co/38aqyWaEYd "
-

[ Windows ] Malware Disabling UAC http://neonprimetime.blogspot.com/2016/06/malware-disabling-uac.html
"恶意软件释放的一段禁用 UAC 的 VBS 脚本: https://t.co/KgpNtUMcFe"
-

[ Windows ] New on the blog: Getting Physical: Extreme abuse of Intel based Paging Systems – Part 2 – Windows http://hubs.ly/H03nm2c0
" 英特尔分页系统的极端滥用 Part 2 - Windows 内存分页机制的实现: https://t.co/qwRQmAbBgb"